Configure access to cases in Elastic Observability
To access and send cases to external systems, you need the appropriate license, and your role must have the Cases Kibana privilege as a user for the Observability feature.
If you are using an on-premises Kibana deployment and want your email notifications and external incident management systems to contain links back to Kibana, configure the server.publicBaseUrl setting.
For more details, refer to feature access based on user privileges.
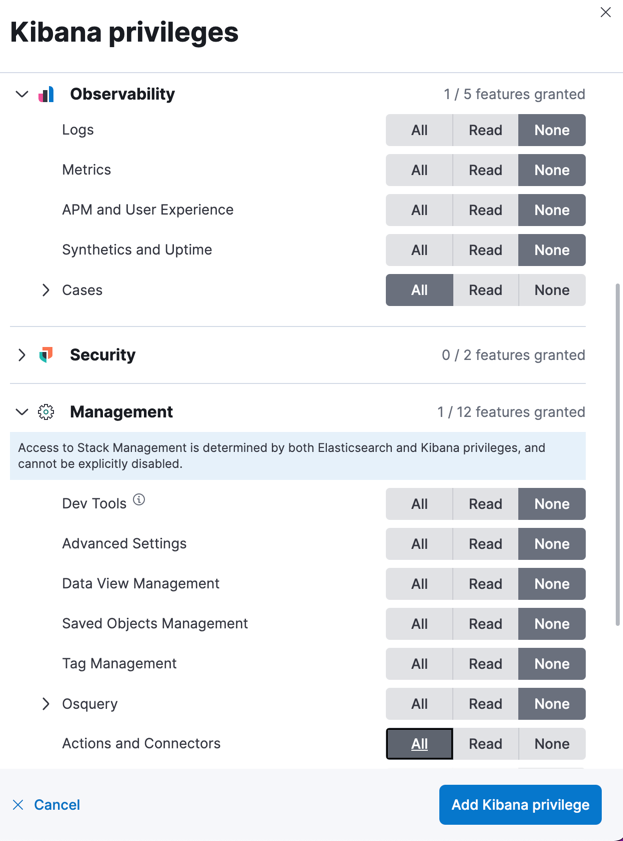
Below are the minimum required privileges for some common use cases.
Allfor the Cases feature under Observability.Allfor the Actions and Connectors feature under Management.NoteRoles without
AllActions and Connectors feature privileges cannot create, add, delete, or modify case connectors.By default,
Allfor the Cases feature allows you to have full control over cases, including deleting them, editing case settings, and more. You can customize the sub-feature privileges to limit feature access.
Allfor the Cases feature under Observability.NoteBefore a user can be assigned to a case, they must log into Kibana at least once, which creates a user profile.
Readfor the Cases feature under Observability.NoteYou can customize sub-feature privileges for deleting cases, deleting alerts and comments from cases, editing case settings, adding case comments and attachements, and re-opening cases.
Allfor the Cases feature under Observability.Readfor an Observability feature that has alerts.
Nonefor the Cases feature under Observability.