What is cybersecurity?
Cybersecurity definition
Cybersecurity is the practice of protecting networks, systems, devices, and other sensitive information from deliberate attacks and unauthorized use. It is a holistic endeavor that requires alignment across your people, processes, and technologies. In order to protect an organization's assets, employees, customers, and users, today's cybersecurity experts use a variety of strategies to protect their data. In an increasingly digital world, protecting cybersecurity is of paramount importance, to ensure:
- Personal privacy and safety: Cybersecurity protects personal privacy and safety by preventing hackers from exploiting identifying information or, directly or indirectly, threatening physical safety.
- Protection of financial assets and intellectual property: Poor cybersecurity can enable cyber criminals to steal confidential business information, such as trade secrets, product designs, and other proprietary information.
- Preservation of business operations: Cyber attacks can disrupt the normal functioning of an organization, disrupting services and causing wide-ranging losses.
- Reputational integrity: A data breach or other cybersecurity incident can damage an organization's reputation, making it difficult to attract and retain customers, investors, and employees.
- Resilience and reliability of critical infrastructure: Cyber attacks on critical infrastructure systems, such as energy, transportation, and water systems, can impact the safety of individuals and the functioning of society.
- Legal and compliance assurance: Poor cybersecurity can result in non-compliance with data privacy regulations, such as GDPR and HIPAA, resulting in regulatory issues, financial penalties, and other consequences.
- National security: Cybersecurity is essential for maintaining national security as it can protect government and military networks from cyber espionage and cyber attacks that can compromise sensitive information.
Why is cybersecurity important?
Cybersecurity is important to mitigate the risk of cyber-attacks and ensure the integrity, confidentiality and availability of the data, systems, and networks at the foundation of the modern world. According to Cybersecurity Ventures1, cybercrime is expected to cost $10.5 trillion each year by 2025. From the perspective of an enterprise, cybersecurity is important because it can protect organizations from threats that might otherwise cause substantial harm.
Data breaches are one of the most common sources of negative impacts to an organization. The effects of such data breaches have a lasting financial impact for the culpable organization due to immediate regulatory fines and long-term reputational damage. Without proper cybersecurity protections, organizations risk the loss of sensitive information, including intellectual property, financial information, and personally identifiable information (PII) such as employee and customer contact information, social security numbers, and healthcare information.
Data breaches are unfortunately common.
When attacks occur, they are expensive, can hurt employees and customers, and can cost an organization its good standing with consumers. That's why it's important for every organization to prioritize the mitigation of cybersecurity risks.
Types of cybersecurity
The term "cybersecurity" encapsulates a number of different efforts and strategies, all with the aim of protecting organizations from vulnerabilities. Here are some of the most common types of cybersecurity areas that today’s organizations focus on.
-
Security information and event management (SIEM)
Security information and event management (SIEM) is a cybersecurity solution used to detect and respond to threats within an organization. At its core, a SIEM (pronunciation rhymes with "him") collects logs and events, normalizing this data for further analysis that can manifest as visualizations, alerts, searches, reports, and more. Security analysts can use SIEM solutions to take on advanced cybersecurity use cases such as continuous monitoring, threat hunting, and incident investigation and response.
-
Endpoint security
Endpoint security is the practice of protecting the devices that connect to a network, such as laptops, servers, and mobile devices. The ideal endpoint security solution prevents ransomware and malware, detects advanced threats, and arms responders with vital investigative context.
-
Cloud security
Cloud security is the practice of protecting cloud technologies from misconfigurations and breaches. The right cloud security solution will protect cloud deployments by providing rich visibility into cloud posture. It will protect cloud workloads with prevention, detection, and response capabilities — all in one integrated solution.
-
Security orchestration, automation, and response (SOAR)
Security orchestration, automation, and response (SOAR) enables security teams to standardize and streamline their organization’s response to cyber attacks and incidents. SOAR optimizes workflows within and beyond the security operations center (SOC) — enabling analysts to focus their efforts on securing their organization's ecosystem.
-
Application security
Application security is the practice of protecting applications, whether running in the cloud, on on-prem servers, or on client devices. This includes creating, developing, adding, and testing security features within applications to make sure they are functional. Proper application security ensures that data within applications is secure and won’t be stolen.
-
Network security
Network security focuses on network infrastructure from misuse. It traditionally combines a number of different tactics and strategies including (but not limited to) firewalls, intrusion prevention/detection systems, network segmentation, VPNs, and other solutions.
-
IoT security
Malicious actors sometimes target specific physical devices that are connected to the network. These devices include WiFi-enabled devices such as cars, security cameras, and smart refrigerators. Internet of Things (IoT) security is the practice of cybersecurity that ensures these devices do not introduce threats or vulnerabilities into the network.
-
Threat intelligence
Threat intelligence helps security teams protect against cyber attacks by analyzing collected data that provides insight into attackers’ tactics and targets. Through threat intelligence, teams can identify patterns of attacker activity and institute appropriate defense strategies for their organization.
-
Identity and access management
Identity and access management (often known as IAM) are the frameworks and technologies that manage digital identities and user access. IAM includes things like two-factor or multifactor authentication, privileged access management, and assigning levels of access within a system or platform. By practicing healthy IAM, organizations can ensure that sign-ons are secure and that only the right people have access to sensitive information.
-
Zero trust
Zero trust is a cybersecurity framework that requires all users — no matter who they are — to be authenticated before they can have access to data, applications, and other systems. Zero trust rose into favor because of today’s distributed workforce. It accounts for remote workers who may be working from their smartphones, laptops, and other devices.
-
Mobile security
Mobile security is a branch of cybersecurity that concerns itself with securing mobile devices such as laptops, smartphones, and tablets. With the rise of mobile use in the workplace, mobile security has become increasingly important.
How do you measure the effectiveness of cybersecurity?
Measuring the success of a cybersecurity program can be challenging, as it can be difficult to quantify the effectiveness of security measures in preventing cyber attacks or data breaches. However, there are several metrics that organizations can use to assess the performance of their cybersecurity program, such as:
- Compliance: Evaluating the organization's compliance with relevant frameworks and regulations aligns a cybersecurity program with an initial set of worthwhile best practices.
- Threat detection and response time: Measuring how quickly the organization is able to detect and respond to a cyber threat can give an indication of the effectiveness of its security tools and processes.
- Risk reduction: It can be helpful to assess how successful the organization has been in reducing the overall risk to its sensitive information and systems. This can be measured by comparing the likelihood and impact of a cyber attack before and after the implementation of new security measures.
- Penetration testing: Regularly performing internal and external security audits and penetration tests can help organizations identify vulnerabilities and gaps in their security programs and improve them accordingly.
- Return on Investment (ROI): Measuring the cost-effectiveness of the program by analyzing the ratio of cost of security measures against the benefits they yield can help to show how well the cybersecurity budget is being used.
No cybersecurity program can guarantee 100% protection, so aim for results that work for the organization's budget, resources, and risk tolerance.
What is a cyberattack?
A cyberattack is an unwelcome attempt to steal, damage, alter, or disrupt data and its underlying systems. If successful, cyberattacks can damage organizations in the form of financial loss, system downtime, sensitive data exposure, and system disablement.
Cyberattackers have varied motivations, though motivation is usually financial, personal, or political. Sometimes, cyberattackers are looking for monetary gains through money and data theft. Other times, they are engaging in cyber warfare or cyberterrorism on behalf of a nation state. Some attackers may launch attacks to spy on competitors to gain an advantage.
Types of cybersecurity threats
There are a number of different types of cybersecurity threats in today’s landscape. Bad actors target networks, applications, and physical devices in their efforts. Here are some of the most common types of cybersecurity threats that organizations work to avoid:
- Malware: Short for “malicious software,” this threat category includes viruses, Trojan horses, and other malicious software that can damage or disrupt computer systems, steal sensitive information, or enable unauthorized access to a network.
- Ransomware: Ransomware is a type of advanced malware that is designed to hold a user’s information or prevent use of a system until the user pays funds to unlock it. Usually this is accomplished by encrypting certain file types, then forcing users to pay ransom to obtain a decryption key.
- Phishing: Phishing refers to attacks that attempt to gain access to sensitive information such as credit card numbers, social security numbers, or other information that can be used for nefarious purposes. Phishing attackers use emails, text messages, phone calls, or social media in attempts to trick users into sharing information through legitimate-looking correspondence.
- Insider threats: This involves an individual or group that has authorized access to an organization's network or systems, who then uses that access to harm the organization.
- Social engineering: This encompasses tactics used to deceive individuals or organizations in order to gain access to sensitive information, sensitive network resources, and financial information by taking advantage of human psychology.
- Advanced Persistent Threats (APTs): These are coordinated, sustained, and stealthy cyber attacks, typically carried out by nation-state or criminal groups, that aim at stealing sensitive information from a specific organization or individual.
- IoT exploits: Cybercriminals are increasingly targeting IoT devices as a way to access an organization’s network and sensitive data.
- Distributed Denial of Service (DDoS) attacks: This is a type of cyberattack that seeks to make a website or network resource unavailable by overwhelming it with traffic from multiple sources.
Cybersecurity challenges
Even though most enterprises invest a substantial amount of time and resources into cybersecurity, preventing cyberattacks remains a challenge. As the digital landscape increases in complexity, it becomes more difficult to keep everything secure. Couple that with malicious actors who become increasingly sophisticated and the challenges abound.
Here are some of the most common cybersecurity challenges enterprises face today:
Overall increase in cyberattacks
Over the past several years, organizations have seen increases in cyberattacks. According to the 2022 Cyber Security Insights Report by S-RM2, 75% of organizations experienced a serious attack in the last three years, which is a 60% increase from the previous year. These attacks were not only on the rise but also expensive, costing businesses an average of $3.4M.
Rise of cloud services and complexity in computing and networking
Enterprises no longer store all of their data locally. Instead, they use cloud computing for an increasingly remote workforce. Although this offers substantial improvements in data storage, workflow, and a number of other areas, it introduces complexity into networks and systems that introduce more vulnerability and risk.
Dependence on digital properties
More than ever before, organizations are dependent on digital properties for completing tasks, storing sensitive information, and managing users and customers. According to a report from McKinsey3, the COVID-19 pandemic pushed companies to rapidly increase their adoption of digital technology. In July 2020, 58% of customer interactions were digital, up from 36% in 2019 and a mere 20% in 2018. Although this offers a positive experience for employees, customers, and users, relying on digital technology introduces a variety of cybersecurity challenges.
Ever-evolving strategies from cyber criminals
As technology advances, so do the strategies of cyber criminals. Many are now creating information-stealing malware specifically built for cloud technologies. With so many enterprises depending on cloud services, the risks loom large. Cyber criminals continually evolve to bypass security measures, so broad protective measures as well as a granular view into systems are important.
The human factor
Individuals are often the first line of defense against cyber attacks. It includes the end-users, system administrators, security analysts, and other employees or contractors who are responsible for implementing and maintaining cybersecurity measures. Organizations should foster a culture of security awareness, training employees on how to identify and avoid cyber threats, and take steps to protect the organization's assets and data.
Cybersecurity use cases
In today’s threat landscape, businesses require security technology to solve several use cases. Here we’ll explore the most critical cybersecurity use cases for your organization:
Continuous monitoring
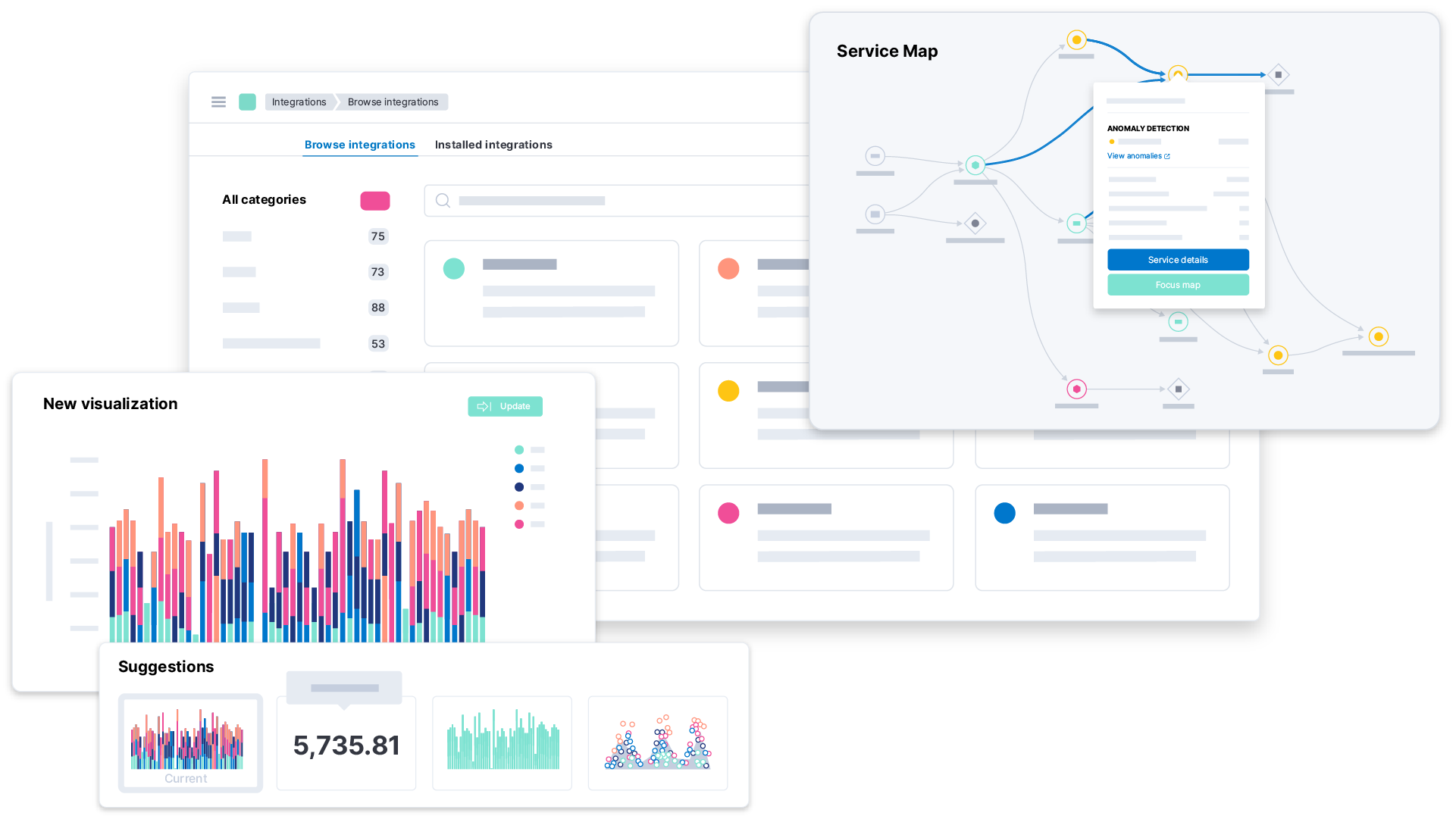
Continuous monitoring delivers powerful operational awareness, streamlined security analysis, and ongoing visual feedback. Achieving visibility across your environment is among the first — and most essential — steps to securing your organization.
To achieve continuous monitoring for your security operations program, choose a massively scalable platform with a powerful data schema and prebuilt data integrations supporting the most innovative technologies in your enterprise stack.
Threat protection
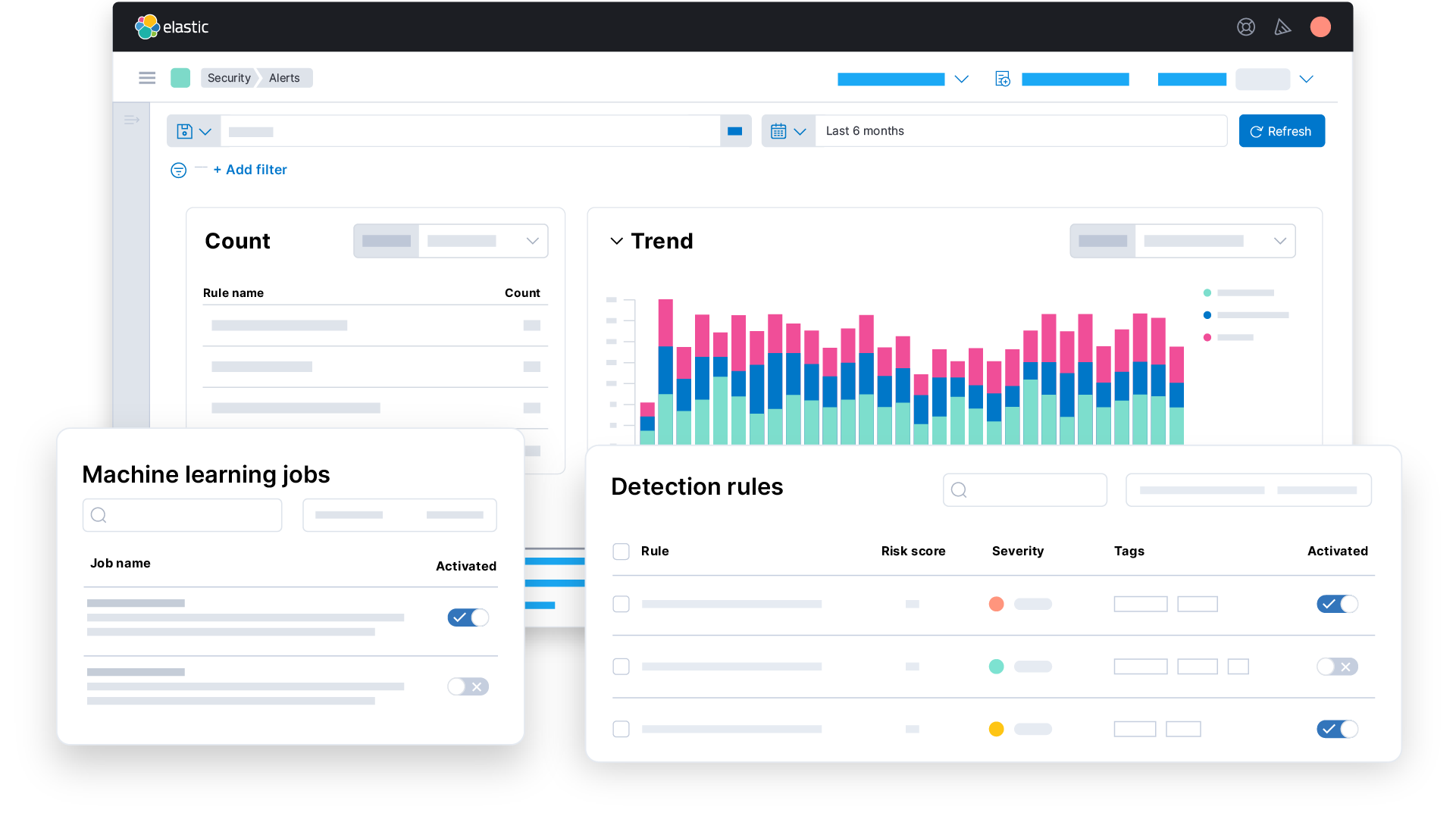
Threat protection refers to technologies, applications, and other security solutions that protect an organization from common cyber threats such as malware, ransomware, and other viruses. The idea behind threat protection is that an organization can block specific threats before damage can occur.
There are a number of different types of threat protection that organizations can employ. Traditional firewalls can offer protection, as can network access control, Advanced Malware Protection (AMP), and Application Visibility and Control (AVC).
Investigation & response
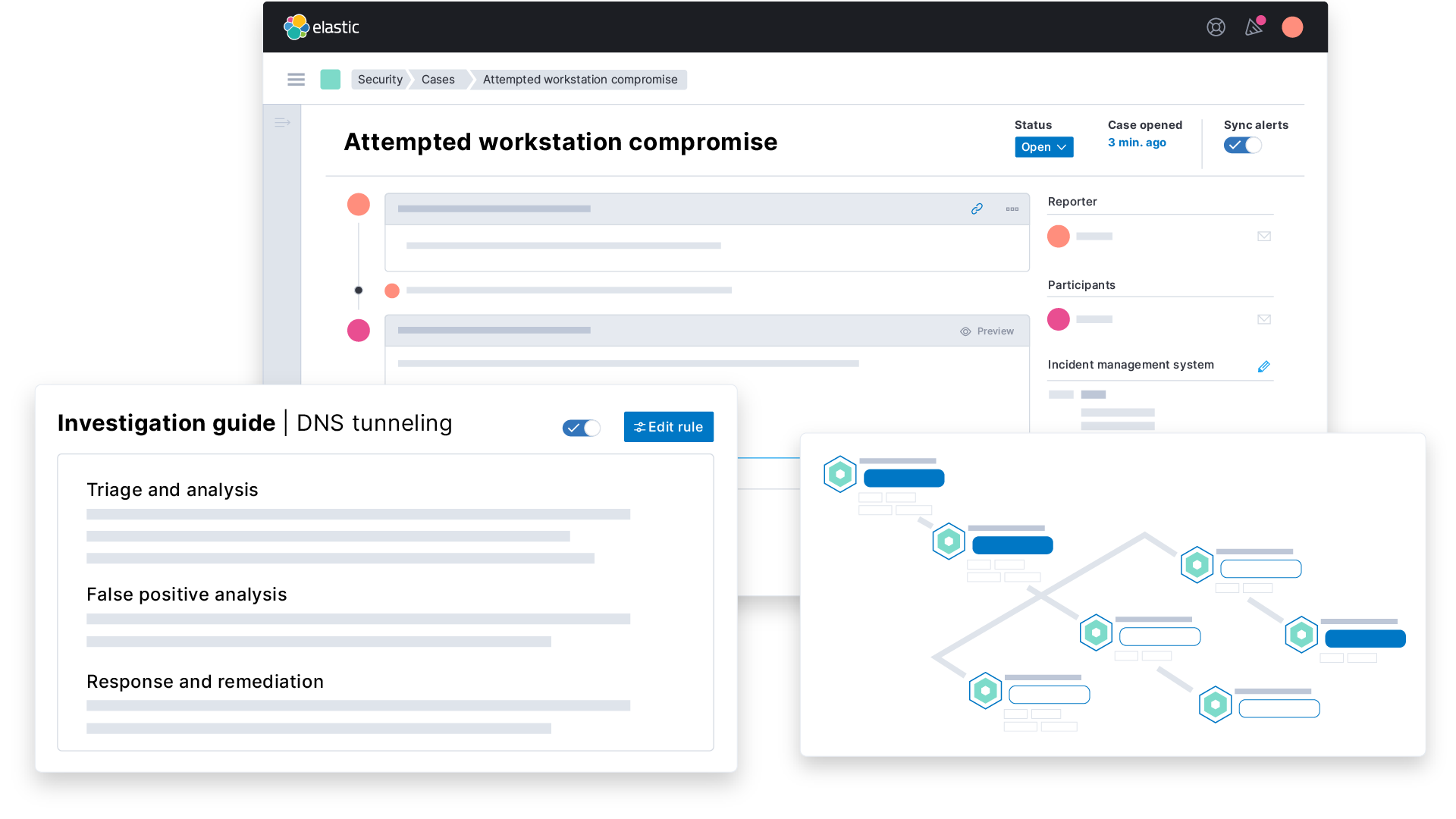
When an incident or threat occurs, it’s essential that an enterprise investigates and responds as quickly as possible. A fast response is essential so that the impact of an attack is minimized.
To achieve investigation and incident response for a security operations program, enterprises must choose a massively scalable platform with a powerful data schema and prebuilt data integrations supporting the technologies already in your stack.
Threat hunting
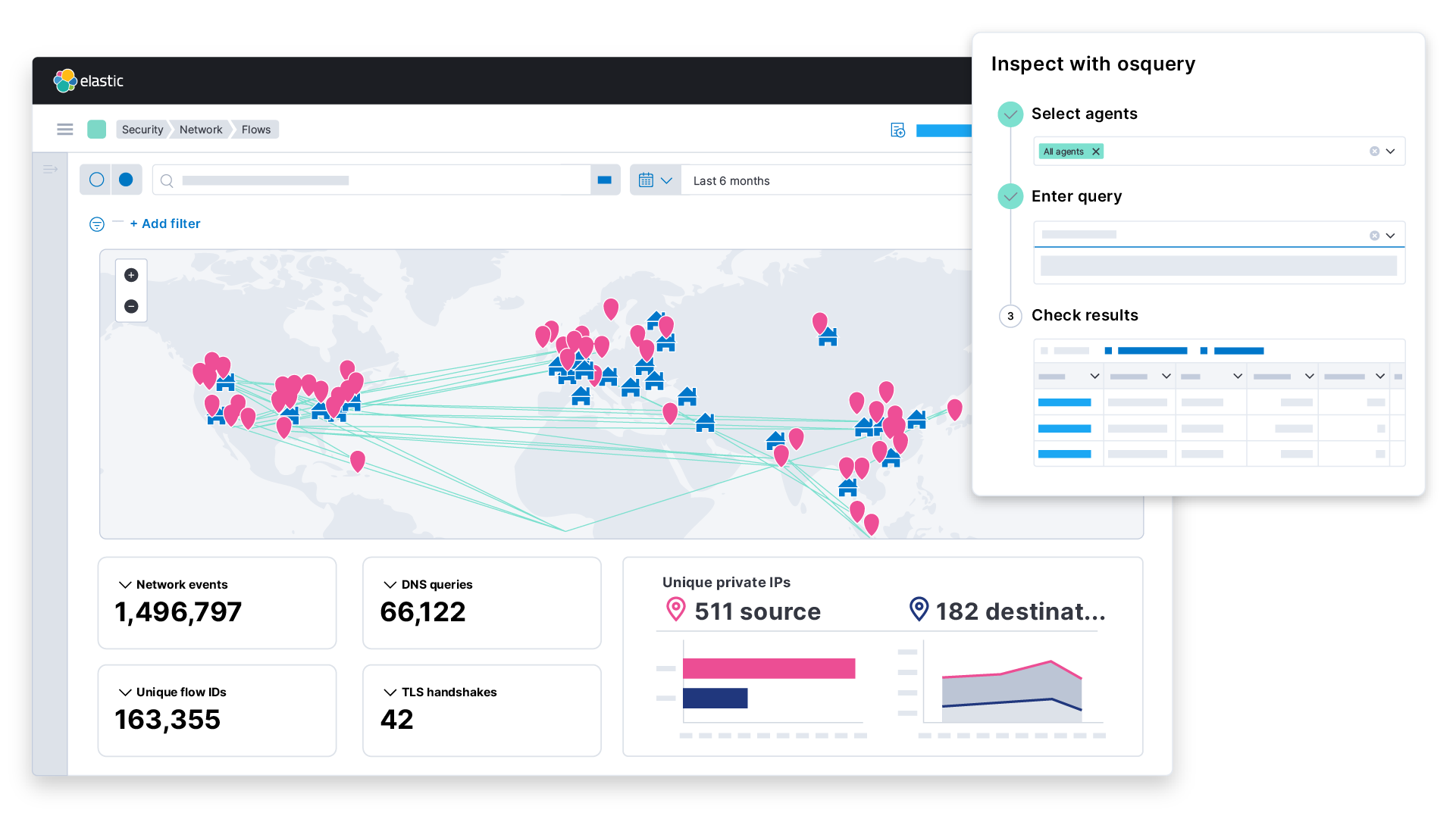
Threat hunting is a proactive approach to finding, detecting, and ultimately minimizing vulnerabilities and cyber attacks. With threat hunting, IT departments will proactively look into any anomalies, investigate them, and ensure that there are no malicious activities that could lead to a large-scale breach. Threat hunting is particularly helpful for combating advanced persistent threats, as these can linger undetected in a network environment for months while collecting sensitive information.
Can you get by without cybersecurity?
Here are some common misconceptions or optimistic thinking that can get some organizations into trouble:
"A data breach is something that only happen to other companies, not to us…"
Many companies think that it will never happen to them, but data breaches are a common occurrence. It is better to be ready for it, by having an incident response plan, a way to detect and contain breaches, and recovery plans. By accepting that a data-breach can happen, companies can take proactive steps to mitigate the risk and minimize the impact.
"Our network is secure because we have a strong perimeter…"
While firewalls can provide a basic level of security, they are not sufficient to protect against all types of cyber threats. Cybercriminals can exploit vulnerabilities in your network infrastructure, use sophisticated malware to bypass firewalls, and gain access to your sensitive data.
"We don’t need to integrate our security technologies to secure our enterprise…"
Basic security measures, such as antivirus software and firewalls, are important, but they are not sufficient to protect against today's advanced cyber threats. To detect and respond to cyber threats quickly, organizations need a comprehensive security strategy that marries integrations between key security tools with clear policies, procedures, and guidelines for handling security-related issues.
"We don't need to worry about cyber attacks originating from vendors…"
Many organizations rely on third-party vendors for various services, such as cloud storage, software development, and IT support. While these vendors may have their own security measures in place, it's important for organizations to independently verify their security protocols and ensure that they meet industry standards.
How important is speed in cybersecurity?
Attackers can do a lot of damage in a short amount of time. In the amount of time it takes you to download a file, that same interval could be all an attacker needs to offload sensitive information or deploy malicious malware. Speed is critical for security teams to respond to incidents — in real time — before they have the potential to cause damage.
Who is responsible for cybersecurity?
Truthfully, every individual at a company has some responsibility for managing cybersecurity. However, enterprises today employ Chief Information Security Officers (CISOs) to lead and direct cybersecurity initiatives within an organization. CISOs are C-level executives who work to assess risk and find solutions.
Here are other personnel responsible for managing cybersecurity:
Cybersecurity analysts
Cybersecurity analysts protect their employer from cyberattacks and/or unauthorized access of company property — including networks, hosts, servers, and apps. In this role, analysts work directly to proactively protect against cyber threats, and respond to any breaches if/when they do occur. See what a day in the life of an analyst looks like.
Security engineers/architects
In this role, engineers/architects lead the collaboration between developers, engineers, administrators, business leaders, and others within the organization to implement and improve upon the security infrastructure. The architect must balance a sound foundational cybersecurity policy, encryption methodology for sensitive data, and outline necessary or desired security features.
Security operations centers (SOC) managers
A SOC manager leads an organization’s security operations team, establishes processes, oversees hiring and training, and relays high-level insights to the chief information security officer (CISO).
Cybersecurity consultants
A cybersecurity consultant can serve one or more organizations in an advisory role, providing insight on anything from basic system infrastructure to advanced security technology implementation. Their ultimate goal is determined upon their contracting, but all will share the same mission of protecting a company’s data.
Vulnerability analysts/penetration testers
Vulnerability analysts and penetration testers are hired or contracted to identify and assess potential vulnerabilities of an organization’s systems, networks, or broader ecosystem. Penetration (pen) testers serve as "white hat" hackers who find system weakness using a variety of tools that may also be used by nefarious, "black hat" hackers.
Network engineers/architects
From network design to initial configuration to monitoring, a network engineer/architect’s role handles all things network to ensure optimal performance. Handling much more than just firewalls, this role manages the policies attached to how network traffic flows in and out of an organization.
System engineers/administrators
Oftentimes known as SysAdmin, a systems administrator or engineer manages the organization’s broader IT infrastructure — servers, applications, operating systems, etc. This role is critical to the success and uptime of the business.
Modernize SecOps with Elastic Security
Elastic Security delivers unlimited visibility into threats, reduces investigation times, and protects your enterprise from the ever-evolving threat landscape. With Elastic, users enjoy an open and integrated approach to security with out-of-the-box protections, customizable analyst workflows, deep contextual insights, and a pay-as-you-grow adoption model.
Try Elastic Security free to discover how you can stay ahead of cyber threats.
Footnotes
- 1 Cybercrime magazine - https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/
- 2 Cyber Security Insights Report 2022 - 2022 Cyber Security Insights Report by S-RM
- 3 McKinsey & Company: How COVID-19 has pushed companies over the technology tipping point—and transformed business forever - https://www.mckinsey.com/capabilities/strategy-and-corporate-finance/our-insights/how-covid-19-has-pushed-companies-over-the-technology-tipping-point-and-transformed-business-forever