Cloud security from Elastic
Detect, investigate, and respond to cloud-native threats efficiently with AI-driven security analytics. Gain deep visibility, advanced insights, and proactive threat mitigation across cloud and container environments — all built on Elastic's Search AI Platform.

Choose the right protection for your needs
Elastic Security offers a comprehensive solution for securing cloud environments. Utilize AI-driven security analytics to swiftly detect, investigate, and respond to threats. Choose between extended protection or native protection to suit your specific needs.
Protect your cloud from threats, deployment risks, and runtime attacks
Cloud security from Elastic packages cloud visibility, benchmark assessment, protections, and response with a host of integrations. The result? An end-to-end cloud security solution.
Enforce cloud security compliance
Assess the configuration of multi-cloud assets against industry benchmarks like CIS Controls, continuously uncovering and maintaining security posture across AWS, Azure, and GCP — in a single view. This is supported by turnkey dashboards and step-by-step remediation guides, ensuring the confidentiality, integrity, and availability of your data in the cloud by shrinking your attack surface and advancing your security posture.

Protect cloud and container workloads
Stop runtime threats targeting cloud workloads and applications. Gain real-time visibility into runtime process activity from a terminal-like view with a lightweight agent powered by eBPF.
Automate the detection and identification of cloud and Linux workload threats. Achieve rapid time-to-value with MITRE ATT&CK®-aligned protections honed by Elastic Security Labs. Customize prebuilt content to secure your organization.

Cloud detection and response
Enhance SIEM capabilities with context from the cloud with cloud detection and response (CDR). Ingest logs and alerts from various multi-cloud provider sources (like AWS CloudTrail, Audit Manager, and VPC Flow Logs) and cloud security tools (like Wiz, Palo Alto Networks, and Google Security Command Center).
Leverage hundreds of out-of-the-box and anomaly detection rules for all cloud sources, and gain end-to-end visibility into cloud-specific attacks triggered by our powerful detection engine.
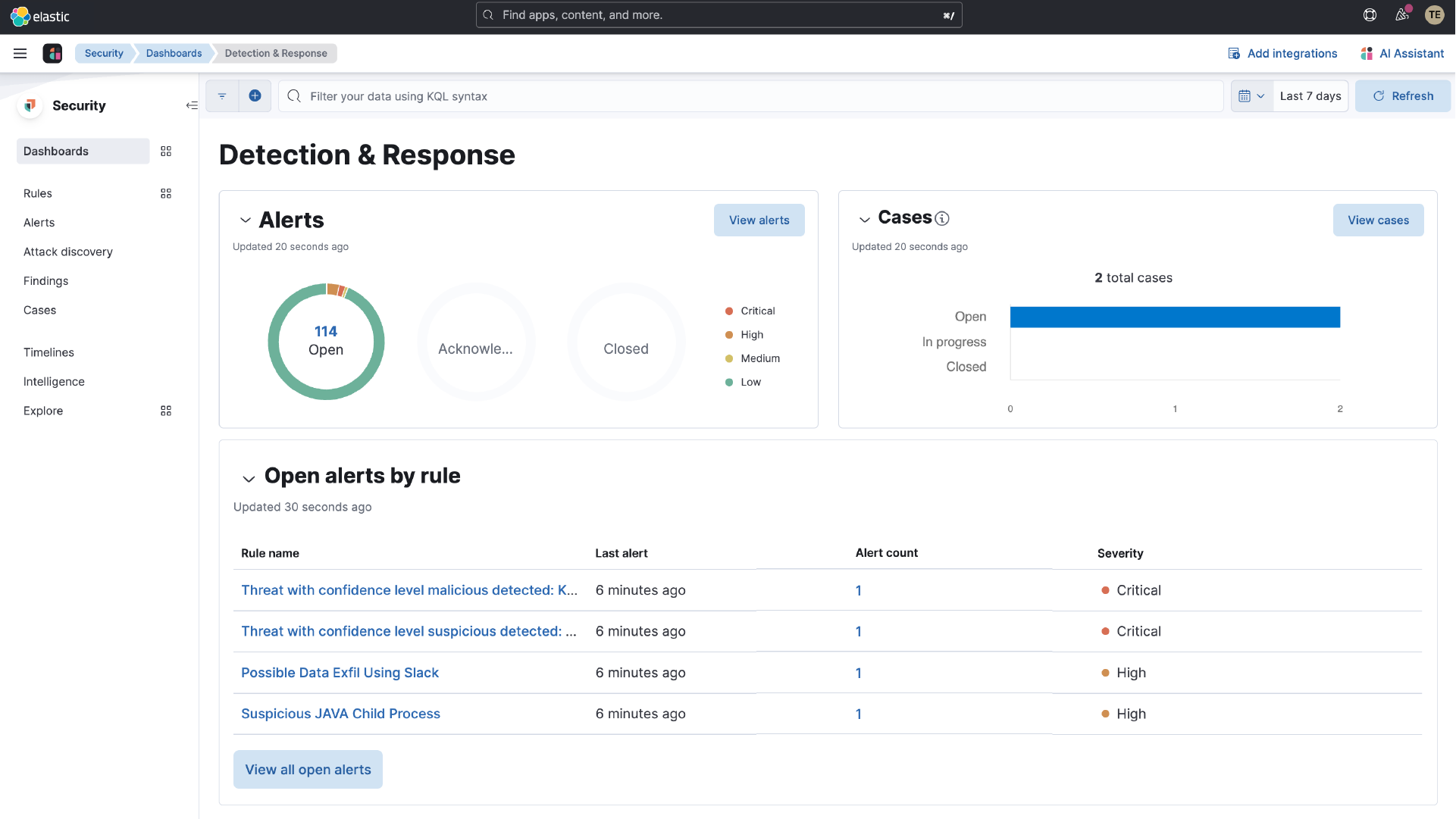
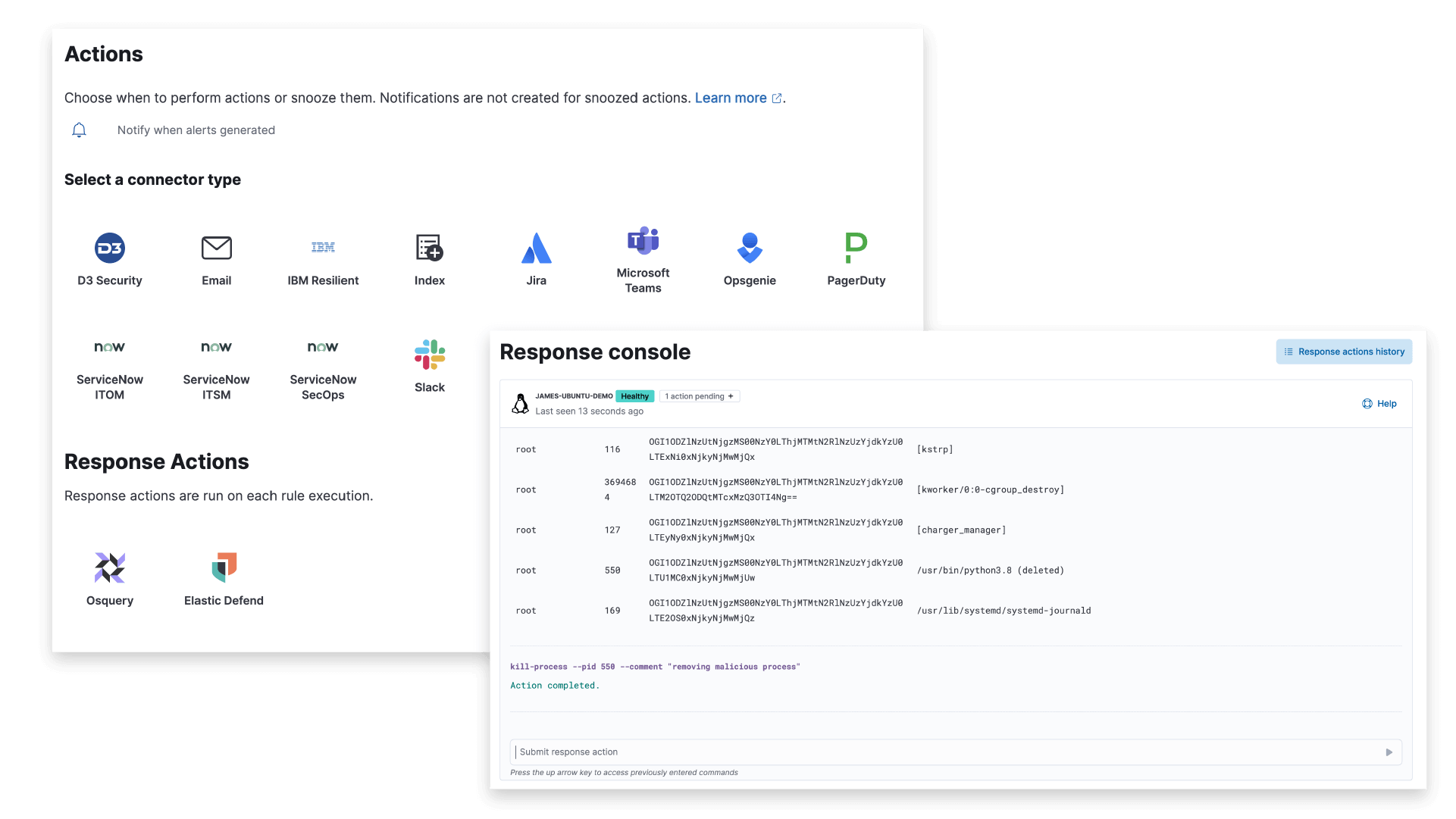
Respond faster, minimize damage
Detect, investigate, and respond to threats with lightning speed. Elastic AI-driven security analytics empowers analysts with decisive action to minimize damage and keep your cloud secure. With Elastic Security's robust response workflows, you can automate your responses — be it a simple Slack message or even live remediations like killing a process or file.
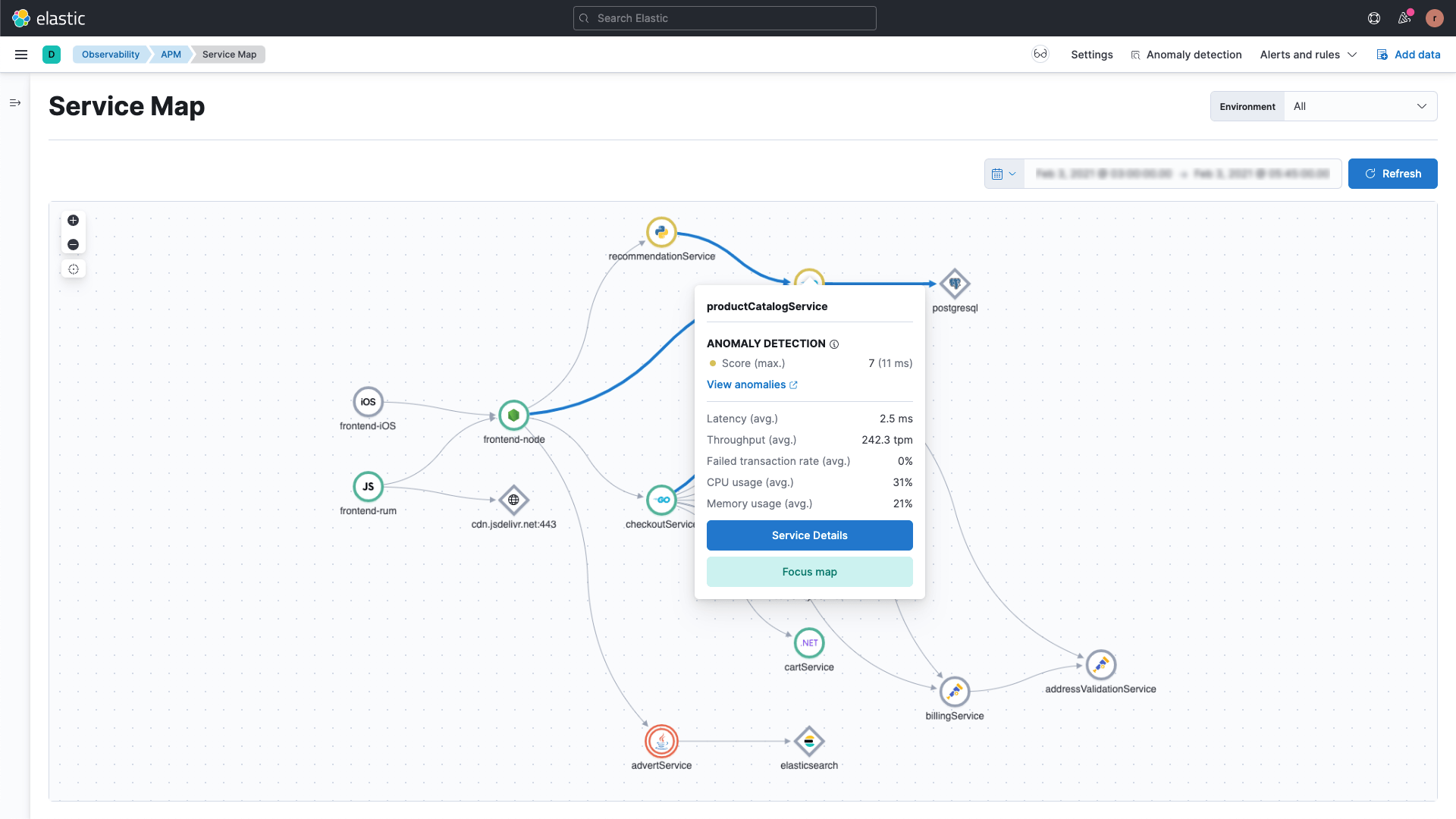
Protect while you observe
Cloud security and observability are business-critical. Gain visibility into cloud availability, application performance, metrics, and traces while you protect workloads and monitor for compliance.
Collect and store data once; apply it in multiple ways. Integrating security and observability in a single platform simplifies deployment, training, and operations. Streamline workflows to optimize CloudOps and raise ROI.
Secure your cloud with or without an agent
Elastic Security empowers your choice. Deploy a lightweight agent for deep workload protection, or enjoy frictionless, agentless monitoring for quick visibility and compliance. Either way, gain powerful threat detection and response — no matter your preference.
Frequently asked questions
Cloud security from Elastic is a cloud security solution that offers visibility, cloud-specific detections, investigation tools, and rapid response capabilities that secure cloud environments comprehensively and holistically. It provides continuous posture insights and runtime protection for workloads and containers empowering your team to prioritize threats based on rich context from multiple data sources. Protect, investigate, and respond — all within a unified view from your SIEM.
Elastic Security offers two comprehensive options to meet your needs:
Extended protection: Seamlessly integrate Elastic Security with your current cloud security tools — no vendor lock-in. Enhance visibility and respond to threats swiftly with added context. Maximize your existing security investments.
Native protection: Simplify security with built-in features for comprehensive cloud protection at no extra cost. Enjoy seamless security without complex setups. Identify and respond to threats quickly with actionable insights. Focus on your cloud, not your security stack.
Cloud Security from Elastic is a comprehensive solution that helps you protect your cloud workloads from threats and vulnerabilities. Our powerful cloud security solution allows you to:
- Monitor your cloud environment with real-time visibility and alerts
- Detect and respond to attacks with automated analysis and remediation
- Prevent breaches with advanced threat prevention and endpoint protection
- Secure your cloud data with encryption, backup, and recovery
Cloud security from Elastic is compatible with major cloud platforms, including AWS, Azure, and Google Cloud, and it supports hybrid and multi-cloud deployments.
Cloud security from Elastic helps organizations modernize their cloud security operations by providing a unified platform for threat detection, investigation, and response. Cloud security from Elastic leverages the power of the Search AI Platform, a scalable and flexible data platform that can ingest, analyze, and visualize any type of data from any source. Cloud security from Elastic enables security teams to gain visibility into their cloud environments, detect and prevent attacks, and automate workflows to respond faster and more efficiently.
Start your free trial today! Our comprehensive getting started guide will walk you through every step.
Elastic Security's agentless integration offers a quick, hassle-free setup without installing software, ideal for gaining visibility and ensuring compliance across your cloud environments. For advanced monitoring and control, Elastic also supports agent-based integration, enhancing threat detection and response capabilities.