What is vulnerability management?
Vulnerability management defined
Vulnerability management is the proactive, ongoing process of identifying, assessing, categorizing, reporting on, and mitigating vulnerabilities within an organization’s systems and software. The systematic approach allows cybersecurity teams to prioritize potential threats while minimizing exposure and reducing the attack surface.
Implementing strong vulnerability management involves adopting tools and strategies that allow organizations to monitor their digital environment for an up-to-date view of their overall security status and any weaknesses that pose a risk.
What is cloud vulnerability management?
Cloud vulnerability management is vulnerability management specific to cloud environments, platforms, and cloud-native applications. It is a continuous process of identifying, reporting, managing, and remediating security vulnerabilities unique to the cloud ecosystem.
As more organizations implement cloud technologies, proper cloud vulnerability management is critical. It represents the evolution of vulnerability management to meet the rapidly expanding threat landscape ushered in by dynamic cloud architectures. The strategy requires assessing the security of cloud-based assets, discovering weaknesses specific to cloud deployments, bolstering workload security (without undue strain on resources), and implementing appropriate countermeasures to mitigate those risks.
To protect server workloads in hybrid, multi-cloud data center environments, cloud workload protection platforms (CWPPs) are an emerging category of workload-centric security solutions. These platforms can even protect public cloud infrastructure-as-a-service (IaaS) environments. As one facet of cloud vulnerability management, CWPPs provide consistent visibility and control for containers and serverless workloads, regardless of location. They secure workloads with a combination of system integrity protection, application control, behavioral monitoring, intrusion prevention, and anti-malware protection. They also proactively scan for workload risk.
Common types of vulnerabilities
A cybersecurity vulnerability is any weakness that can be exploited to gain unauthorized access to a system or network. It can allow attackers to install malware, run code, or steal and destroy data, among many other unwelcome outcomes. Effective vulnerability management strategies hinge on detecting and understanding these vulnerabilities.
Common Vulnerabilities and Exposures (CVE) is a public database of known cybersecurity vulnerabilities and exposures. This resource is maintained by the National Cybersecurity FFRDC (Federally Funded Research and Development Center). Each unique CVE number corresponds to a known threat, providing organizations with a reliable way to stay on top of the ever-growing list of cybersecurity issues to address. So far, the database has identified over 200,000 vulnerabilities open to exploitation from attackers.
Common types of cybersecurity vulnerabilities include:
- Weak passwords
- Inadequate access controls, including insufficient authentication and authorization policies, such as a lack of two-factor and multi-factor authorization
- Unsecured networks and communications
- Malware and viruses
- Malicious insiders who obtain unauthorized access to resources
- Phishing scams, buffer overflow attacks, cross-site scripting (XSS) attacks
- Lack of visibility into cloud infrastructure
- Unpatched software, hardware, and systems
- Vulnerable or outdated APIs ( which are more common targets as API use increases)
- Weak or improper access management related to cloud data
- Internal and external misconfigurations (currently, cloud misconfigurations are among the most common vulnerabilities)
Why is vulnerability management important?
Vulnerability management is critically important, as Elastic's Dan Courcy puts it, "because every year cybercriminals find and take advantage of system vulnerabilities. They feast on open communication protocols and exposed databases that show no sign of regular security maintenance or prevention techniques."
Modern cyber ecosystems are constantly evolving in both breadth and complexity — and so too are the thousands of new threat vectors discovered each year. More applications, users, and systems spanning vast cloud infrastructures and services create an expanding attack surface. And with more users, mistakes proliferate in growing systems, creating even more opportunities for cybercriminals.
For most modern enterprises, vulnerability management is critical for a robust security posture. It helps organizations stay ahead of threats by proactively seeking out weaknesses and neutralizing them. By conducting continuous vulnerability assessments, organizations can find their weak spots before malicious actors can exploit them. Proactive management reduces the risk of costly data breaches, compromised systems, and potential reputational damage or loss of user trust.
How vulnerability management works
Vulnerability management works by using a variety of tools and solutions. Together, these enable the key phases of risk identification, security assessment, prioritization, remediation, and confirmation.
At the center of most approaches is a vulnerability scanner that automatically assesses and analyses risk across an organization's entire infrastructure, including systems, networks, and applications. Scanners compare what they see to known vulnerabilities, helping teams prioritize the most urgent vulnerabilities. Multiple scanning tools are typically required to cover the range of software across applications, operating systems, and cloud services. Proper vulnerability management also requires regularly scheduled vulnerability assessments.
Before scanning, vulnerability management starts with achieving complete visibility into assets and inventory. Most solutions also include patch management software, security configuration management (SCM) software, real-time security information and event management (SIEM), penetration testing, and threat intelligence.
Vulnerability management lifecycle process
The vulnerability management lifecycle process is a continuous process that follows a well-defined lifecycle to ensure the systematic and comprehensive handling of vulnerabilities. It is not a single scan or assessment; it's a constant cycle. By instituting this lifecycle process, organizations can establish a structured approach to mitigating vulnerabilities. Though the specific steps can vary depending on the individual organization, excellent vulnerability management generally follows six key lifecycle phases, which are continually repeated.
- Discovery
Before the process can truly begin, teams need to identify and document the systems, applications, and assets within the scope of the program. This includes creating an accurate inventory of hardware, software, and network components across the digital environment. Discovery activities may involve network scanning, asset and inventory management tools, and collaborations with system owners and stakeholders to ensure complete coverage. - Vulnerability scanning
With assets identified, automated vulnerability scanning tools are used to scan systems and applications to detect vulnerabilities. These tools compare and correlate the software and configurations against a database of known vulnerabilities, providing a list of potential weaknesses. Authenticated scans (with valid credentials) conduct deeper assessments. Unauthenticated scans identify vulnerabilities visible from an external perspective. Scanners can also identify open ports and services running. They can scan the full range of accessible systems, from laptops and desktops to virtual and physical servers, databases, firewalls, switches, printers, and more. The resulting insights can be presented in reports, metrics, and dashboards. - Vulnerability assessment
Once you've identified the vulnerabilities across your environment, the next step is to evaluate them to determine the level of risk they pose. Many programs start with the Common Vulnerability Scoring System (CVSS) to rank the potential impact and severity of each vulnerability. Prioritizing the most critical threats helps organizations focus their resources more effectively to promptly address the most significant vulnerabilities. - Treatment and remediation
With vulnerabilities identified and prioritized, the most crucial phase in the process is taking action to address them. This can involve applying patches, reconfiguring systems, updating software versions, changing access controls, or implementing other measures. It is essential to have a well-defined and coordinated process for remediation, which may include collaboration with system owners, IT teams, and vendors to ensure the timely implementation of necessary changes. While remediation is often preferred, the next best option is mitigation, where a threat is temporarily reduced. There will also be instances when no action is taken. This occurs when a threat is particularly low-risk or too costly to be remediated. - Verification
After applying remediation measures, it is crucial to verify their effectiveness. This requires rescanning systems to confirm that known threats have been successfully mitigated or eliminated, followed by audits. Additional tests are often conducted, including penetration testing, to ensure that remediation efforts have addressed vulnerabilities sufficiently. Regular verification is essential to validate the security controls and ensure the ongoing effectiveness of vulnerability management efforts. - Ongoing monitoring
Vulnerability management is not a one-off; it's an ongoing process. Organizations should continuously monitor for new vulnerabilities, emerging cyber threats, and changes in the IT landscape. That means staying updated with security advisories, subscribing to vulnerability feeds, and actively participating in security communities. Organizations should also constantly report their discoveries to appropriate databases. By maintaining a proactive approach, organizations can more effectively detect and address vulnerabilities and reduce the risk or potential exploits — while also increasing the speed and efficiency of their overall program.

Benefits of vulnerability management
Reactive, ad hoc security measures do not amount to a viable cybersecurity strategy. Establishing a robust vulnerability management program helps businesses detect and fix potentially devastating and costly issues before they can cause harm. Vulnerability management delivers significant benefits, including:
- Proactive risk mitigation: By detecting and fixing vulnerabilities promptly, organizations minimize the risk of potential exploits. Vulnerability management makes it significantly harder for bad actors to gain access to systems.
- Compliance and regulatory requirements: Many industry regulations mandate regular vulnerability assessments, making vulnerability management essential for improved compliance with various security standards and regulations.
- Improved incident response: Effective vulnerability management enhances incident response times and capabilities by reducing the attack surface and providing actionable information to neutralize threats.
- Better visibility and reporting: Vulnerability management delivers current, centralized, accurate reporting on the status of an organization’s overall security posture. This gives IT teams essential visibility into potential problems and a better understanding of where improvements need to be made.
- Enhanced reputation and customer trust: Demonstrating a commitment to security through iron-clad vulnerability management helps foster trust among customers and build brand value.
- Greater efficiency: Vulnerability management helps minimize system downtime, secure valuable data, and decrease the amount of time required to recover from incidents, freeing up teams to focus on operations and revenue.
Vulnerability management limitations & challenges
While comprehensive vulnerability management is always worth the effort, the process can come with certain limitations and challenges.
- Time and resource constraints: Conducting thorough vulnerability assessments requires time, expertise, and resources, which can pose challenges for organizations with limited budgets and personnel.
- Complexity and scalability: As systems and networks grow in complexity, managing vulnerabilities across a wide range of assets can become increasingly challenging, requiring specialized tools and skills.
- False positives and negatives: Vulnerability scanning tools may produce false positives (identifying vulnerabilities that don't exist) and false negatives (failing to identify actual vulnerabilities) — often requiring manual verification and validation.
- Patch management complexities: Applying patches to remediate vulnerabilities can be a complex task, sometimes requiring meticulous planning and testing to avoid disruptions to critical systems.
- Cloud risks: Adopting cloud-native capabilities like containers, orchestrators, microservices, APIs, and declarative infrastructure comes with a unique set of security challenges when it comes to vulnerability management, including a lack of visibility into cloud infrastructure, configuration risk posture issues, and runtime concerns.
Best practices for vulnerability management
To ensure your vulnerability management efforts are as successful as they can be, consider implementing the following best practices in addition to adhering closely to the vulnerability management lifecycle process:
- Maintain an up-to-date and thorough inventory of all systems, applications, and network assets.
- Perform continuous, automated vulnerability scans.
- Establish a comprehensive, integrated, automated patch remediation policy to rapidly apply security updates and patches.
- Define roles within your organization: effective vulnerability management can only be achieved when all stakeholders are fully committed, with clearly defined roles and responsibilities, particularly when it comes to monitoring, evaluating, and resolving issues.
- Educate employees about security best practices with awareness training to minimize the risk of human error and insider threats.
- Develop and regularly test incident response plans to ensure timely and effective resolutions to potential security threats.
- Organizations should adopt unified cloud vulnerability management solutions that come with automated workflows for assessments, remediations, and reporting for a holistic view of their overall security posture.
Cloud vulnerability management with Elastic
With Elastic's cloud vulnerability management features, organizations can continuously uncover vulnerabilities across all of their cloud workloads with near-zero resource utilization. Elastic Security is the only search-powered security analytics solution that unifies SIEM, endpoint security, and cloud security on a single platform — empowering organizations with a comprehensive suite of cloud security capabilities for AWS.
Elastic's cloud-native vulnerability management capability continuously uncovers vulnerabilities in AWS EC2 and EKS workloads with zero resource utilization on workloads. It also identifies, reports, and guides remediation to help organizations respond promptly to potential risks.
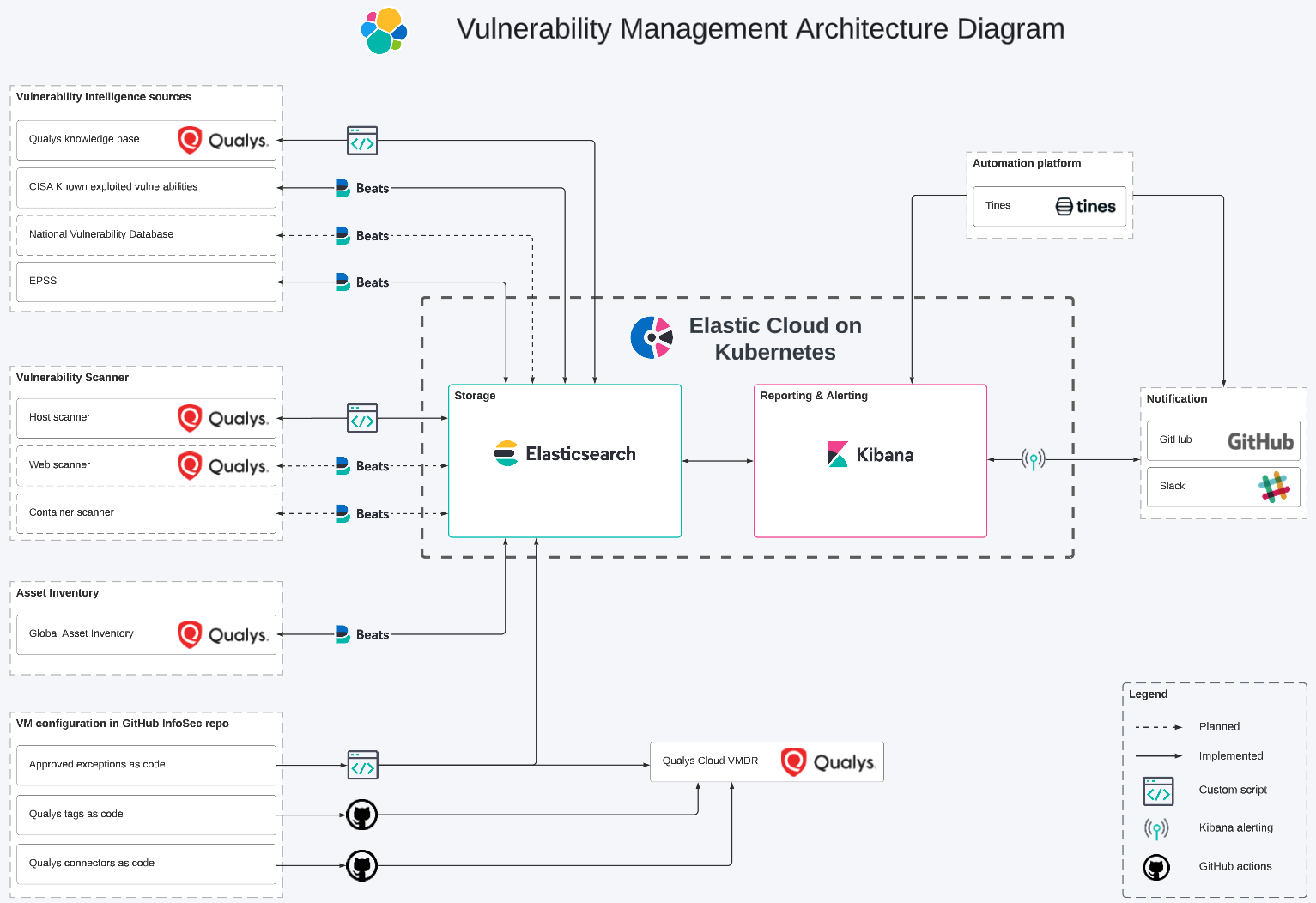
Elastic provides critical unified visibility across all cloud resources and on-premises systems. And Elastic Security delivers better attack surface visibility, reduces vendor complexity, and accelerates remediation, helping you deliver the very best cyber threat protection and management possible.
Vulnerability management FAQ
What's the difference between a vulnerability, a threat, and a risk?
A vulnerability is a weakness or flaw in a system or network, a threat refers to a potential event or action that could exploit that vulnerability, anf risk represents the potential impact or harm resulting from a successful exploit.
How do you mitigate cloud vulnerabilities?
Mitigating cloud vulnerabilities involves implementing security controls specific to cloud environments, including strong identity and access management, encryption, regular auditing and monitoring, correcting misconfigurations, and adopting a risk-based approach.
What's the difference between vulnerability management and vulnerability assessment?
Vulnerability assessment is a component of vulnerability management. An assessment is a one-time evaluation that aims to identify and classify vulnerabilities, while vulnerability management encompasses the entire process, including assessment, prioritization, and remediation.