Threat Hunting
Elastic Security for threat hunting
Initiate hunts with insights gleaned from advanced analytics. Leverage petabytes of data, enriched with threat intel. Uncover threats you expected — and others you didn’t.
Validated by security experts
Security teams around the world perform proactive threat hunting with Elastic Security, including our very own in-house security research group.
Customer spotlight
A European police force stops attackers from sabotaging criminal investigations.
Customer spotlight

SNC's managed security services team discovers threats faster than ever.
Customer spotlight

Walmart leverages vast data sets to stop global syndicates from defrauding consumers.
Give hunters the edge
Elastic Security arms practitioners with the information they need to reveal advanced threats.
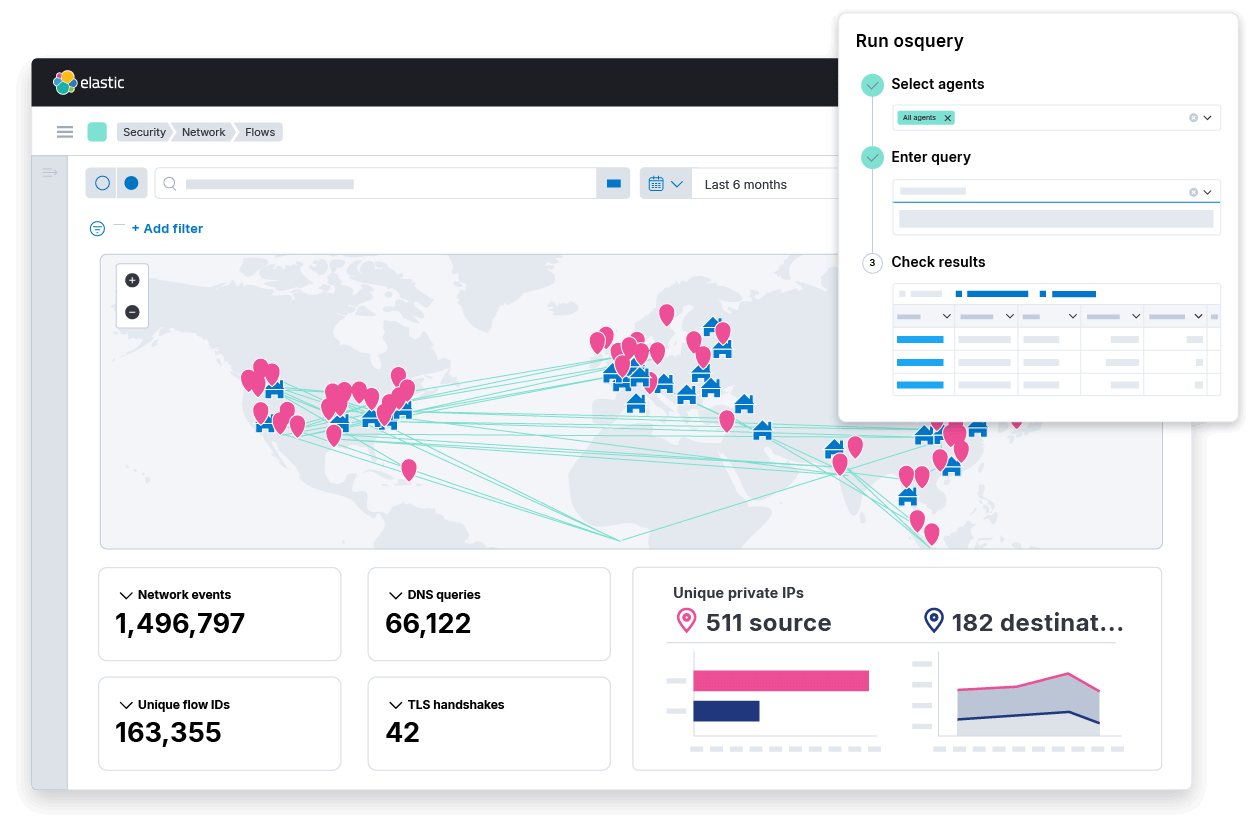
Uncover previously hidden threats
Elastic equips practitioners to track down hidden threats with curated visualizations and context. The solution integrates with a vast ecosystem of security and IT technologies, helping organizations eliminate blind spots and data silos.
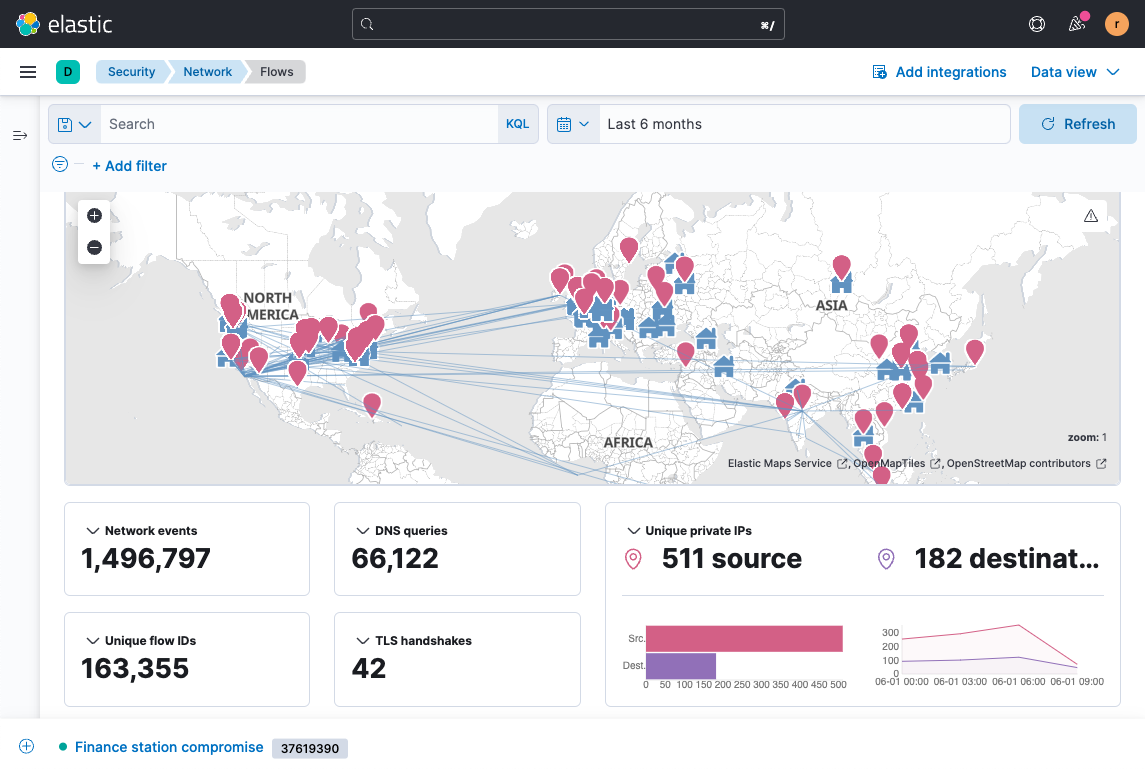
Respond faster with rich context
Elastic helps hunters determine what merits scrutiny — and what to do about it. The solution surfaces rich context on the fly, arming analysts with the confidence to take rapid action. Threat hunters can query petabytes of logs in just seconds and quickly match fresh IoCs against years of historical data.
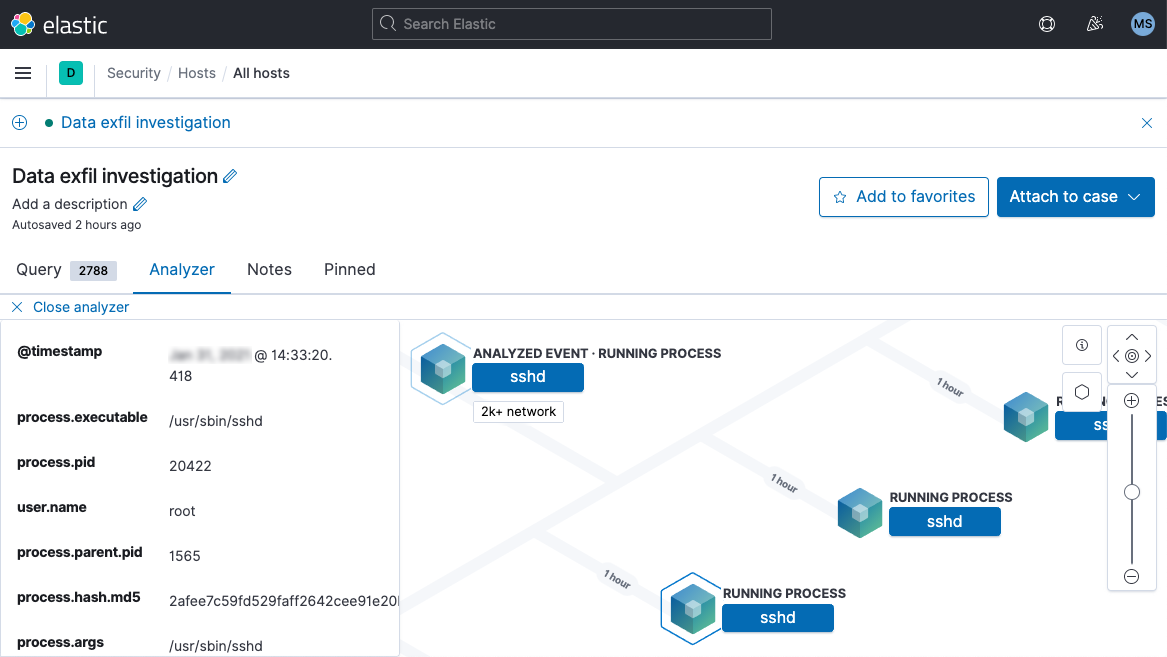
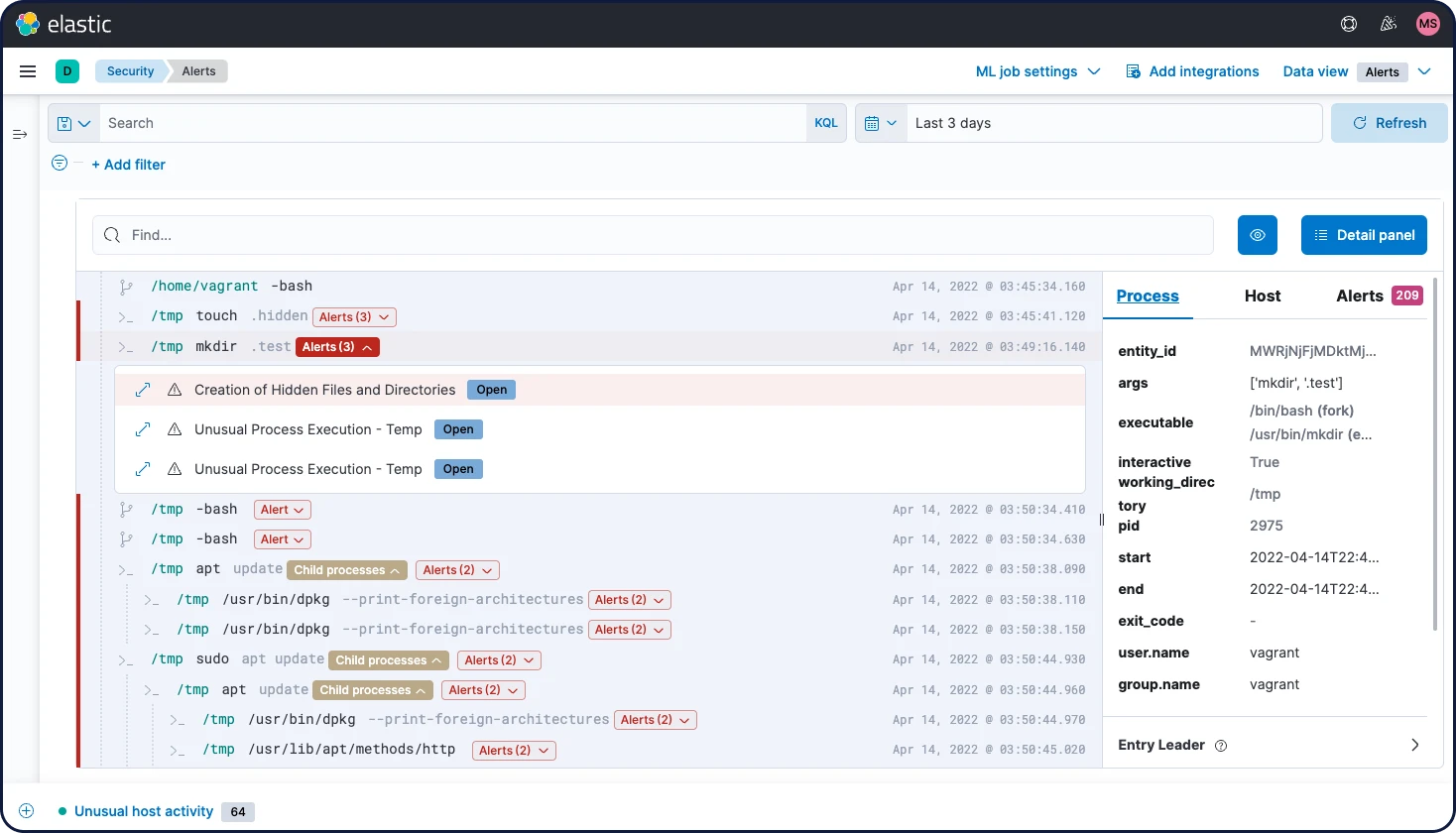
Reduce dwell time & minimize damage
Waiting for frozen data to thaw wastes precious time. Elastic provides quick access to frozen data, enabling practitioners to dig into archives without a long wait.
Do more with Elastic
Bring the speed, scale, relevance, and simplicity of Elastic to teams of all types.
Security
Prevent, detect, and respond to threats — quickly and at scale.
Observability
Analyze logs, metrics, and APM traces in a single stack.
Enterprise Search
Power search experiences for your workplace, website, or apps.


