

Elastic Security
Modernize SecOps with AI-driven security analytics
Address complex threats with Elastic Security, built on the Elastic Search AI Platform, to streamline SecOps.

CAPABILITIES
Security for the AI era
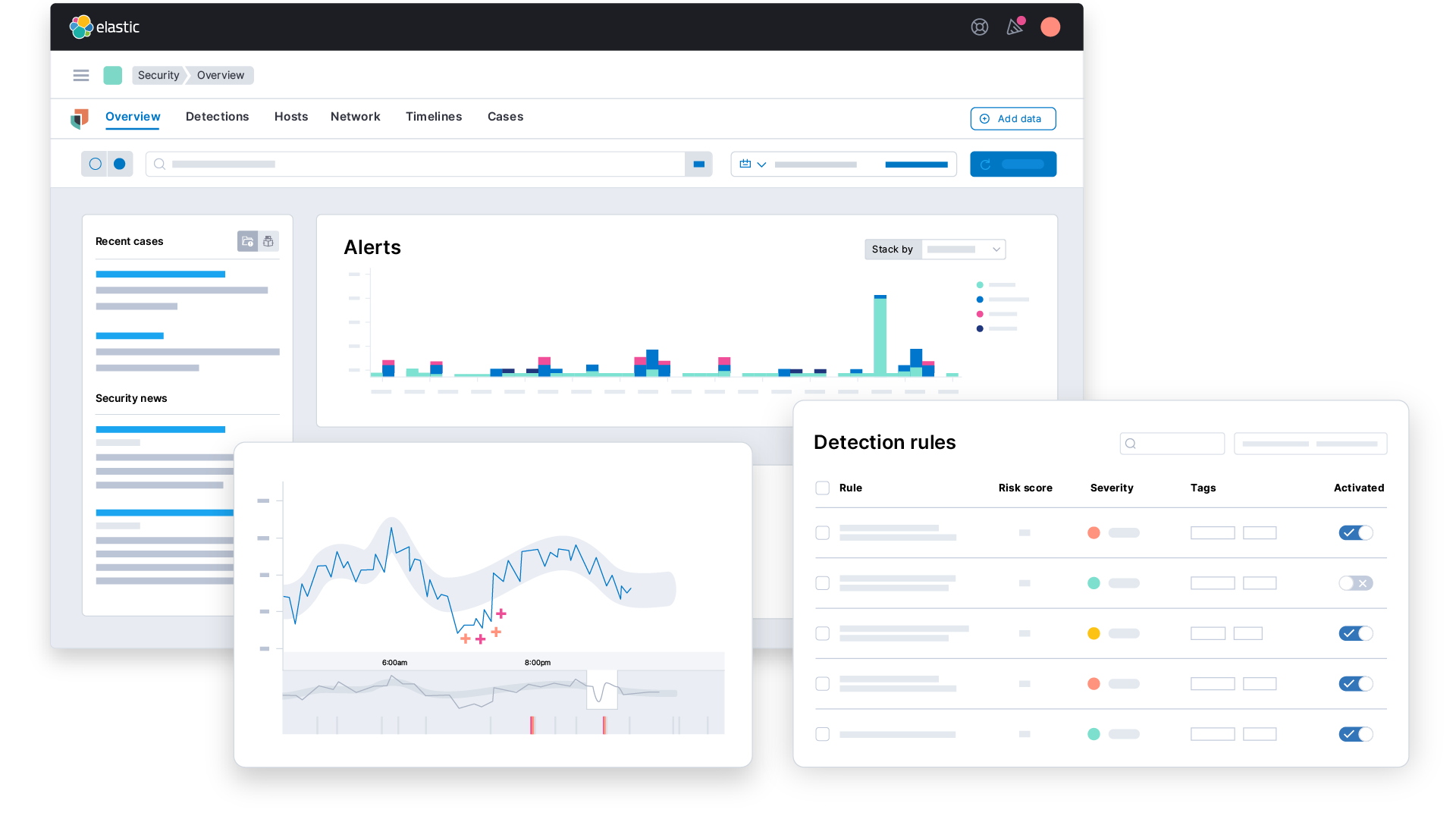
SIEM
Empower your SOC
SIEM, simplifiedResist advancing threats with AI-driven security analytics, the future of SIEM.
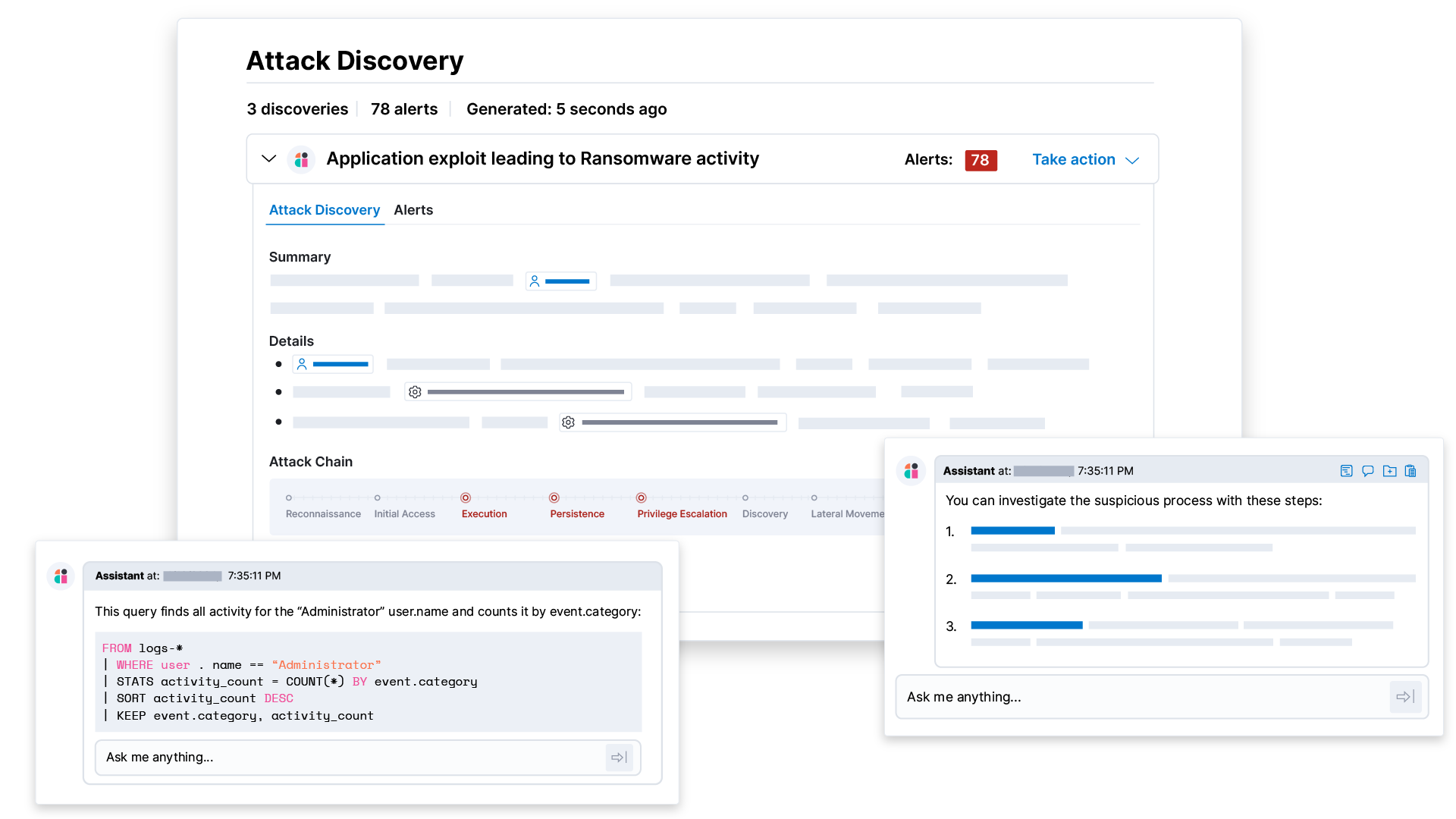
AI for Security Operations
Work smarter with AI
AI for SecOpsDetect sooner, investigate faster, and respond before threats have a chance, with the Elastic Search AI platform.
Threat research
Fueled by Elastic Security Labs
Explore threat researchApply novel research on threats, malware, and protections from our expert security researchers.



Use Cases
AI-driven security analytics for SOC teams
Tackle your security use cases with the Elastic Search AI platform.
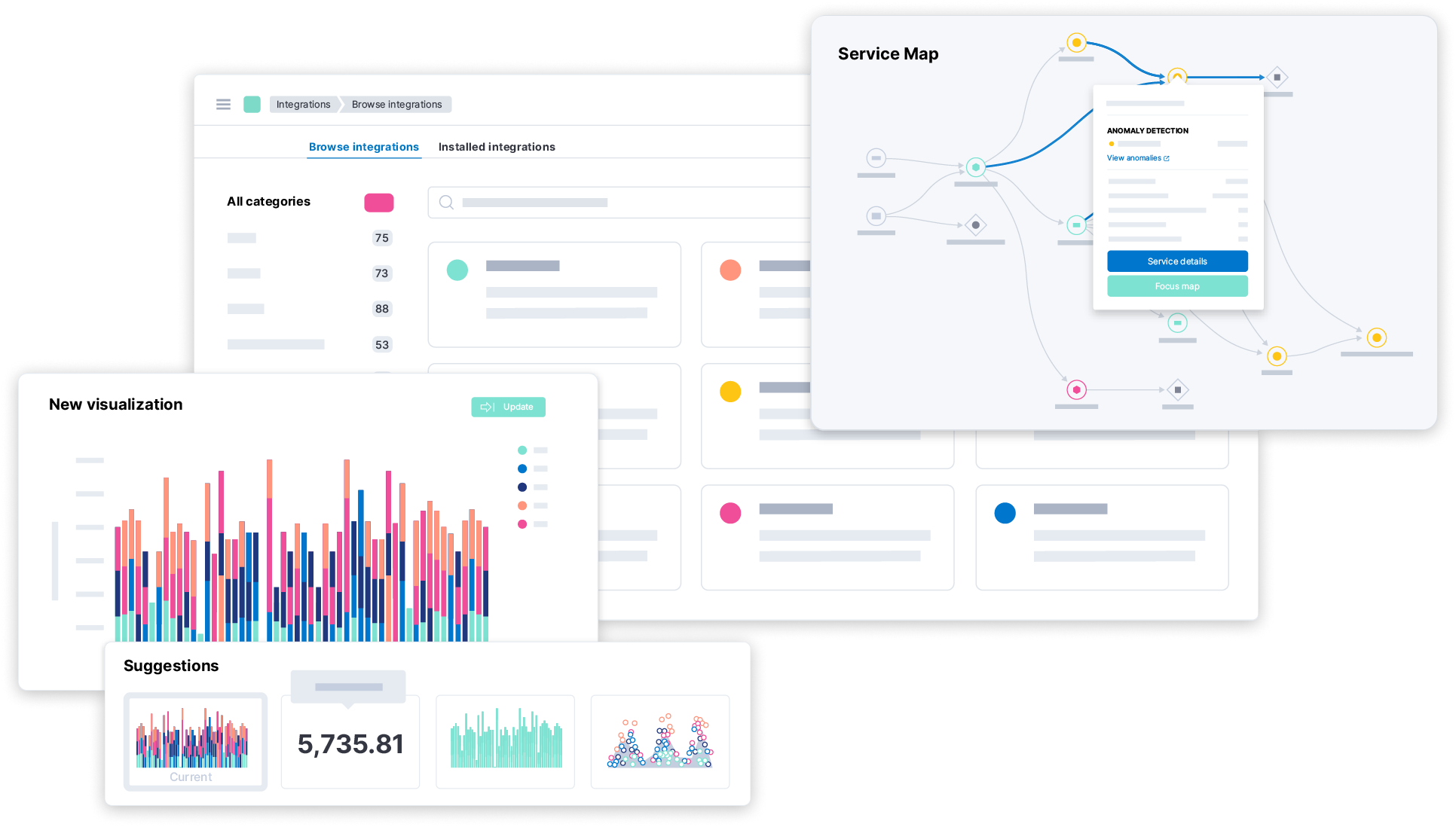
Continuous monitoring
Gain visibility across your attack surface
Discover continuous monitoringCollect and normalize data of any kind — cloud, user, network, you name it. Explore data from on-prem and cloud-based infrastructure, all in one place.
Automated threat protection
Stop complex attacks with advanced analytics
Explore automated threat protectionDetect threats across the MITRE ATT&CK® framework. Reveal hidden threats with anomaly detection. Mature SecOps practices to stop threats at unprecedented scale.


See Elastic Security in action
Security teams around the world succeed with Elastic.
Customer spotlight

KPN enhances its security posture and enables business modernization
Customer spotlight
Booking.com secures operations worldwide, protecting travelers
Customer spotlight
Texas A&M reduces response time by 99%
Frequently asked questions
What is the Elastic Security solution?
The Elastic Security solution helps teams protect, investigate, and respond to threats before damage is done. On the Search AI platform — and fueled by advanced analytics with years of data from across your attack surface — it eliminates data silos, automates prevention and detection, and streamlines investigation and response. Learn how the Elastic Security solution can modernize SecOps at your organization.
Is Elastic Security free?
Elastic Security is part of the Elastic Stack, the free and open platform powered by Elasticsearch. Organizations can get started — and even support core security operations workflows — at no cost. Learn the power of open security. If you want to try it for yourself, experience a security-focused solution with a free trial of Elastic Cloud.
Why are businesses switching from Splunk to Elastic?
If your organization needs a modern SIEM, you may be considering Elastic versus Splunk. Consider your goals: Do you need to achieve visibility across your global environment? Power advanced analytics? Support the hybrid cloud? Retiring Splunk and moving to an open and flexible solution like Elastic can help you transform your security program. Consider 5 signs you need to replace your SIEM.
What is Search AI Lake?
Search AI Lake enhances our new serverless offering, helping users accelerate insights to combat threats and minimize downtime. All data is standardized and indexed in the Search AI Lake, ensuring secure governance for your proprietary data. The fully managed cloud offering requires zero configuration, allowing you to effortlessly scale and streamline operations. Discover how you can protect, investigate, and respond to threats.






