What’s new in Elastic Security 7.14: Protect your company with Limitless XDR
Elastic Security 7.14 introduces the industry’s first free and open Limitless XDR solution, unifying the capabilities of SIEM and endpoint security. It is made possible by the general availability of Elastic Agent, which helps equip it to prevent, detect, and respond to threats before adversaries can steal sensitive information or sabotage operations. Let’s dig into the best of what it brings.
Quickly quarantine and inspect endpoints
Elastic Security 7.14 accelerates response by enabling analysts to invoke response actions with Elastic Agent. With the first native response action for Elastic Agent, host isolation, analysts can address malicious activity by quarantining a host from a network, containing the attack and preventing lateral movement to other hosts. Try it out with the Endpoint Security integration for Elastic Agent.
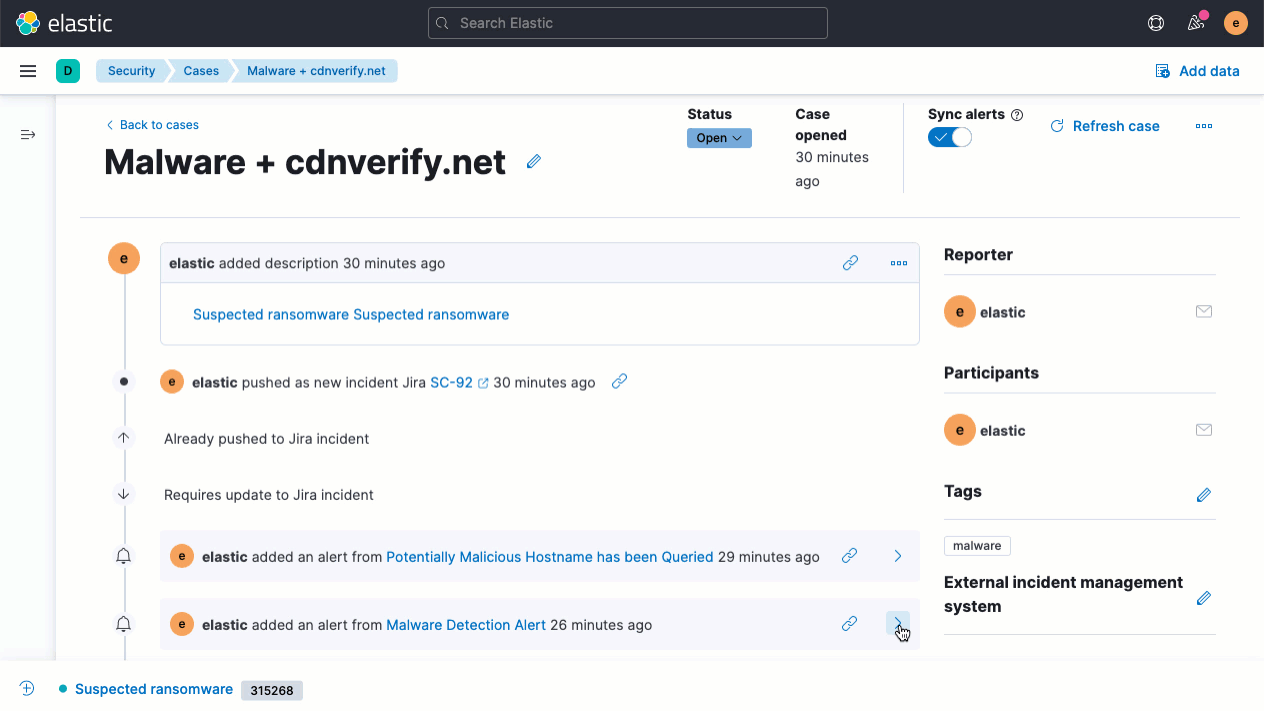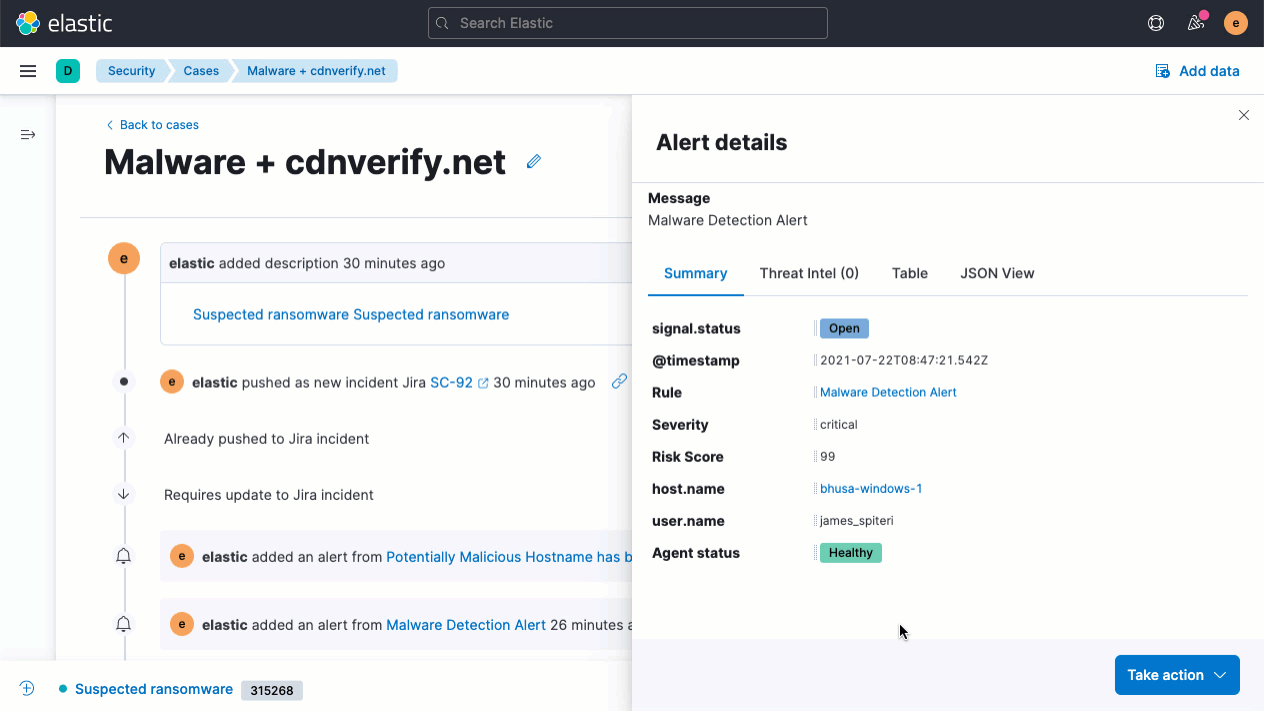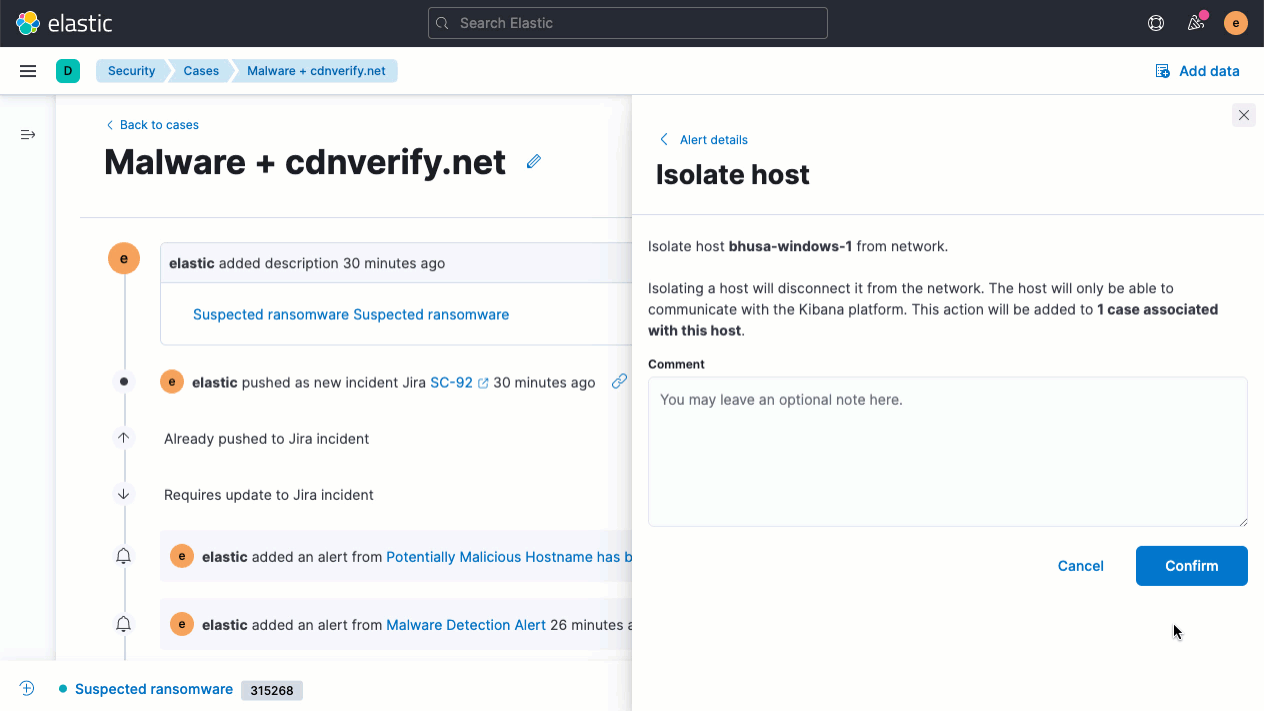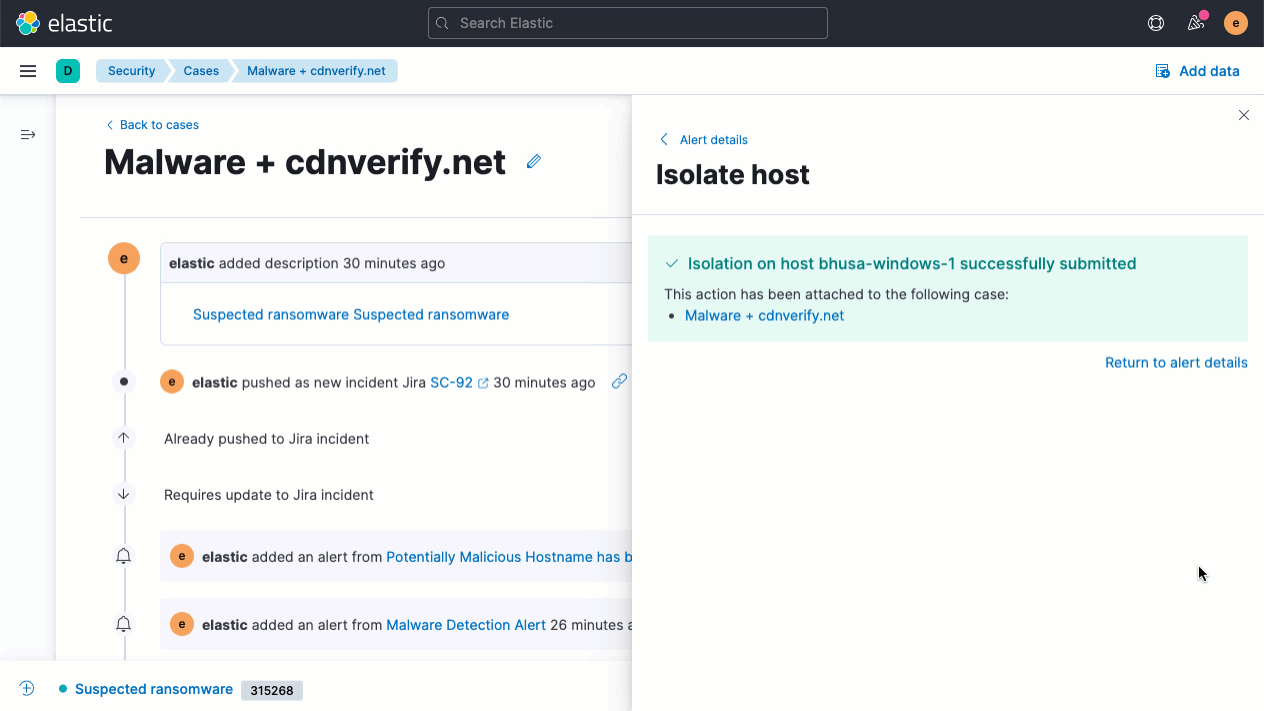
The release also streamlines the host inspection capabilities recently introduced for Elastic Agent. An update to the Osquery Manager integration for Elastic Agent enables analysts to build a library of useful host queries, because running a well-honed saved query is far faster than rewriting it from scratch. Analysts can also leverage searches developed by others in the osquery user community.
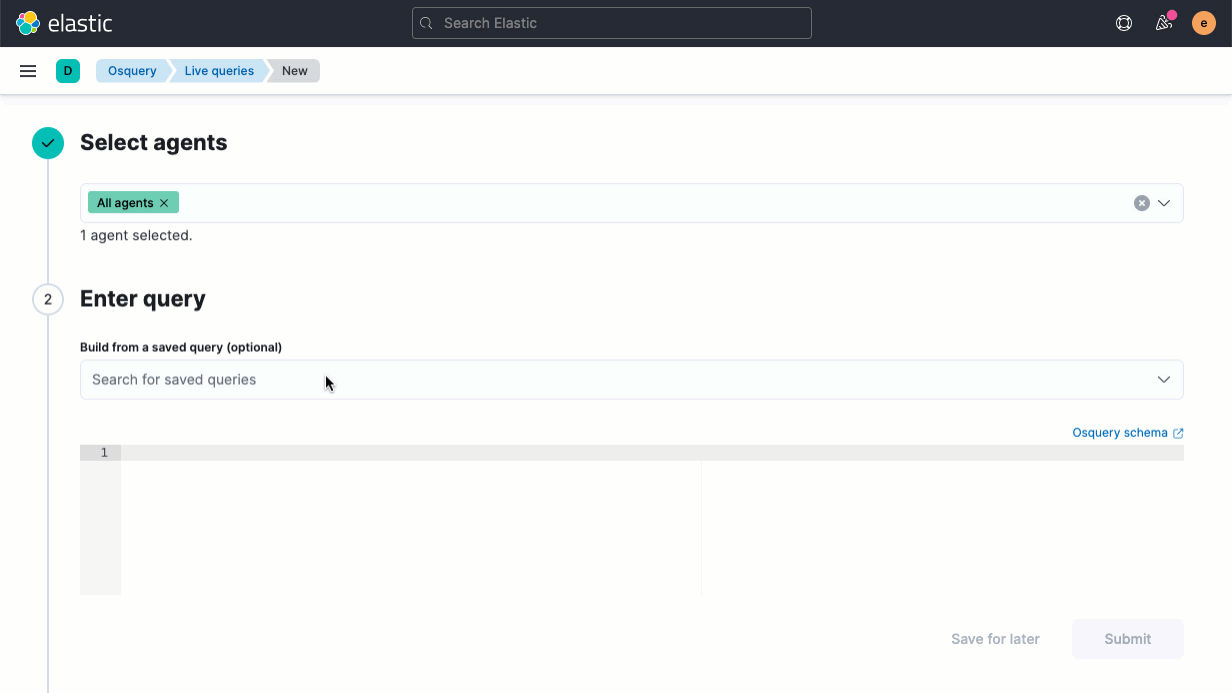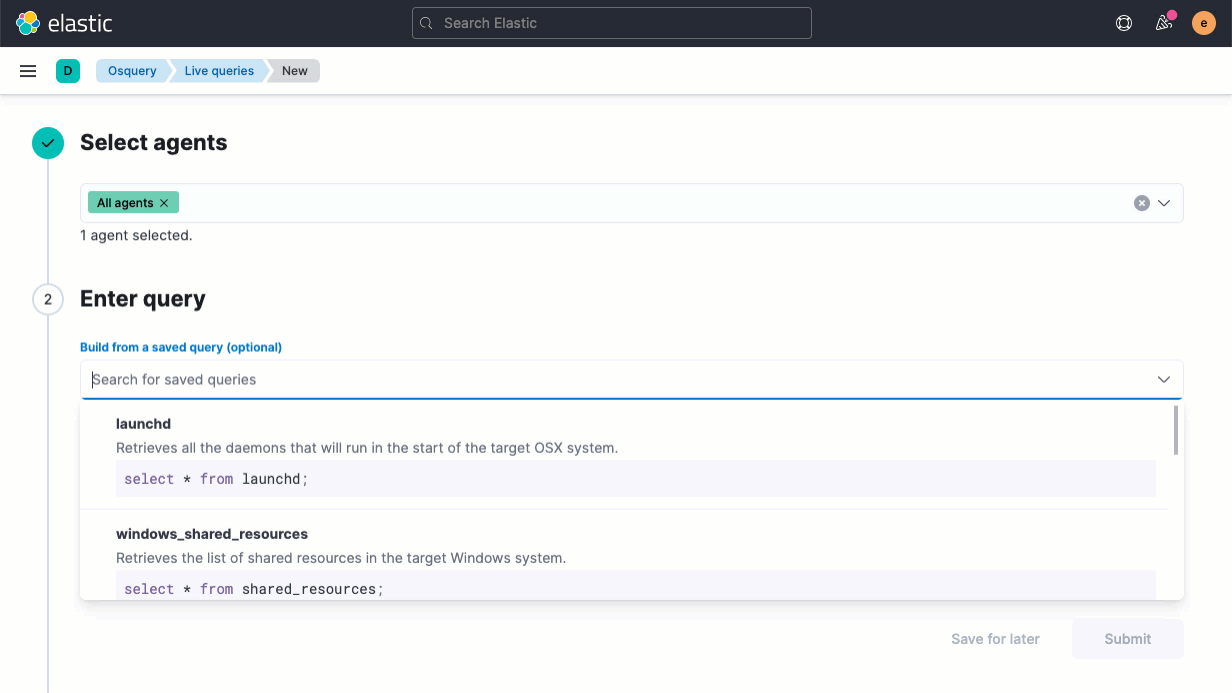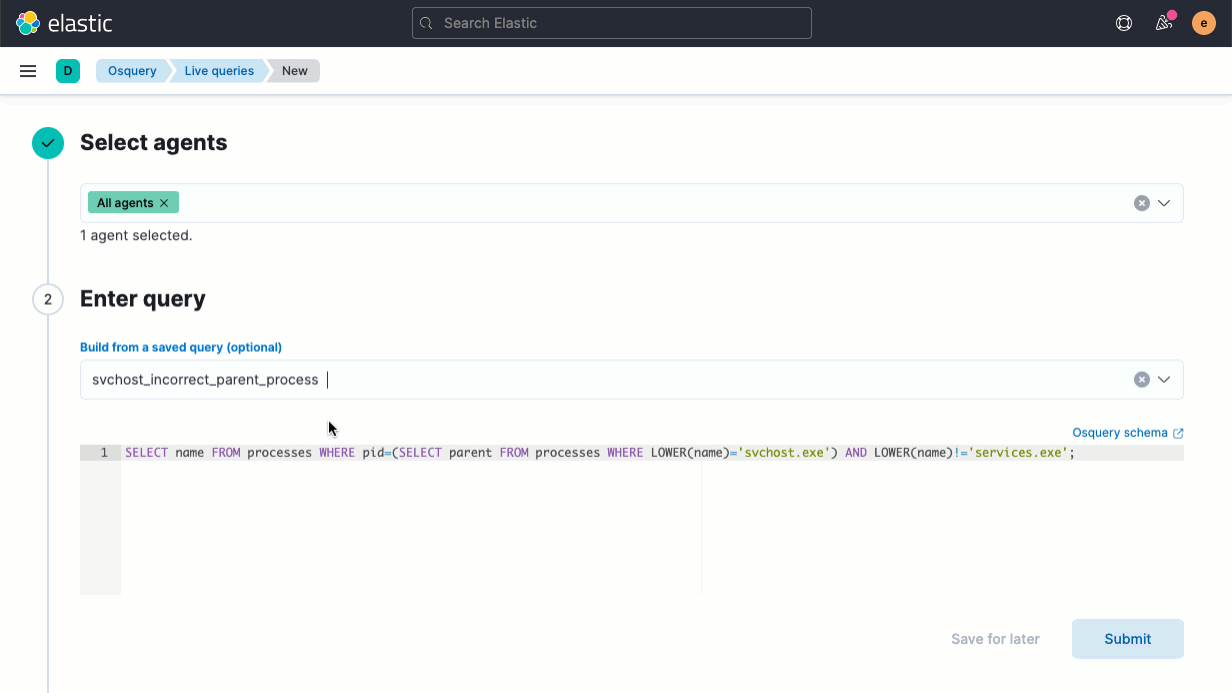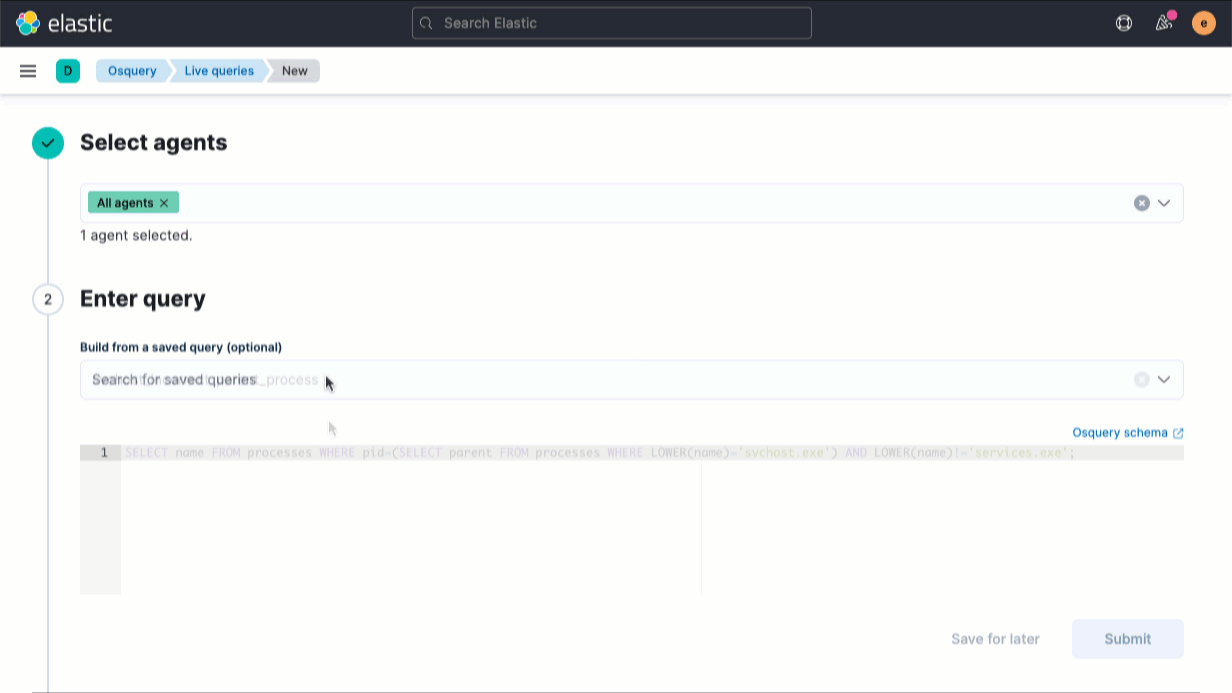
We’ve also made several other improvements to the osquery integration:
- Scheduled queries can now be constrained to particular Operating Systems or osquery versions.
- An audit trail enables users to see who ran or scheduled a query.
- Usability improvements provide a more polished practitioner experience.
Stop fast-evolving ransomware and malware
Elastic Security 7.14 strengthens the ransomware and malware stopping power of Elastic Agent. Ransomware attacks are growing more advanced and frequent, so this release adds an extra layer of ransomware protection for Windows systems and data. With its advanced techniques for stopping ransomware on Windows and macOS, Elastic Agent defends organizations from opportunistic adversaries like DarkSide and REvil. The release also adds full production support for stopping malware attacks against Windows, macOS, and Linux systems. With one click, practitioners can activate malware prevention across every endpoint covered by Elastic Agent, stopping trojans, cryptominers, rootkits, and exploits.
Contextually enrich alerts with threat intelligence
Elastic Security 7.14 enriches detection alerts with threat intelligence, enabling analysts to triage and investigate alerts without needing to pursue this context separately. Upon opening the alert summary panel, they can access 30 days of contextually relevant threat intelligence for ten common data fields, like IP addresses, file hashes, URL, and registry path.
Spot unusual authentications
Elastic Security 7.14 delivers six machine learning jobs that analyze authentication events to detect suspicious activity within your environment, including:
Rare user name, a smart way to detect the continued use of accounts by departed usersRare source IP for a known user, which can reveal account takeoverSpike in authentication events, to spot an unusual volume of authentication behavior or change in the ratio of failed vs. successful log-ins or the rate of failed log-ins
Detect spoofed URLs
Building on our successful introduction of monitoring DGA domains, we are enabling organizations to proactively monitor for spoofed URLs within their environment. With the introduction of the ‘Detect Spoofed URLs’ capability, an alert is generated whenever a potentially malicious URL is detected within the environment. The alerts surface potentially malicious DNS activities that might otherwise not be surfaced promptly. Once enabled, users receive alerts within their triaging workflow. The alerts associate underlying events, and surface the malicious artifacts leading to the detection. In its experimental state, the capability monitors for malformed URLs, known phishing activities, and potentially malicious domains to generate the alert.
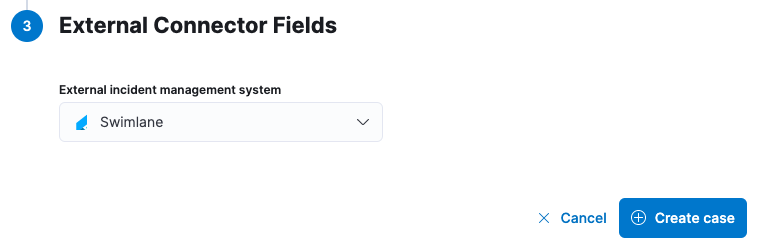
Connect workflows by integrating with Swimlane’s SOAR platform
New integrations with the Swimlane SOAR platform streamline the workflows of security teams leveraging both solutions. We partnered with Swimlane to build the integration, which enables organizations to sync alerts and cases from Elastic Security, enhancing response workflow management. The integration includes a field mapping function to assist with forwarding Elastic alert and case information to the user’s respective Swimlane field types.
Streamline administration
Faster out-of-cycle rule updates: Utilizing the out-of-cycle rule update workflow introduced in 7.13 now requires less manual interaction. Upon installation of the prebuilt rules update integration for Fleet, the Security app checks for updates whenever opened.
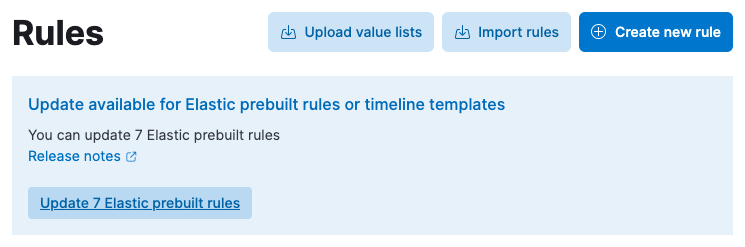
Rule management improvements: We’ve improved the performance of the rule management interface and streamlined bulk actions. Detection engineering just got faster.
Event filtering: Administrators can now create event filters to exclude unwanted endpoint events, allowing them to better utilize storage in Elasticsearch.
Role-based access control (RBAC) for cases: Investigations often uncover sensitive business and organization information, so Admins can now assign All, Read, or None access for cases to user roles.
Try it out
Want to experience all that Elastic Security 7.14 has to offer? Try it out on Elastic Cloud or upgrade your environment to try its latest features.
If you’re new to Elastic Cloud, take a look at the Elastic Security Quick Start guide (bite-sized training videos to get you started quickly) or our free fundamentals training courses. You can always get started with a free 14-day trial of Elastic Security. Or download the self-managed version of the Elastic Stack for free.
Read about these capabilities and more in the Elastic Security 7.14 release notes.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.