Elastic Security 7.9 adds anti-malware, prebuilt cloud protections, and more
Security teams frequently use Elastic Security to collect and analyze endpoint data, and the need to enhance visibility as the virtual workforce grows is making this use case even more common. The solution excels with use cases requiring data at scale — delivered in any format, at nearly any volume and velocity. Just deploy Beats across your endpoints, and voilà, you’re collecting far and wide.
This leads us to ask: if you’ve deployed an agent to collect endpoint data, why not use that same agent to prevent malware?
Elastic Security 7.9 delivers the first major milestone toward comprehensive endpoint security integrated directly into the Elastic Stack by introducing signatureless malware prevention and kernel-level data collection on the new Elastic Agent, our “one Beat to rule them all.” The Elastic Agent also brings together logging, metric collection, and more. These capabilities are available now in our free distribution tier, with additional endpoint protection features planned for later releases.
Elastic Security 7.9 has even more in store. With data, applications, and users quickly moving to the cloud, SecOps teams must still maintain visibility across their hybrid environment. To address this, 7.9 introduces new detections that enable SecOps to preserve situational awareness without hindering the speed or agility of IT and dev teams performing migration. Community-driven workflow refinements streamline prevention, detection, and response. And a trove of newly supported data sources equip practitioners to stop threats, wherever they’re revealed.
Let’s dig in.
Free malware prevention and deep endpoint visibility
Anti-malware in one click (beta)
Malware prevention is now built into Elastic Agent, adding an important layer of protection to endpoint data collection. This new capability is available in our free tier to users and organizations everywhere. This advances our goal of building threat prevention directly into Elastic Agent, with many more advanced endpoint security capabilities to come.
Signatureless malware prevention puts an immediate stop to malicious executables on Windows and macOS endpoints. In its latest round of testing, AV-Comparatives found that the Elastic Security machine learning model stops 99.6% of malware and triggers zero false positives on common business software. Activating anti-malware takes just one click in Kibana.
Kernel-level data collection (beta)
Elastic Security facilitates high-fidelity alerting by collecting endpoint data for centralized analysis. MITRE ATT&CK©-aligned detections from the Elastic Security Research Team leverage information all the way down to the kernel, powering detection rules and machine learning jobs, while minimizing false positives. The solution offers broad support, enabling collection of essential data, whatever the underlying OS:
- Windows datasets: Process, Network, File, DNS, Registry, DLL and Driver Loads, Security
- macOS datasets: Process, File, Network
- Linux datasets: Process, File, Network
Centralizing endpoint data from across your environment and adding further context enables organizations to accelerate threat hunting, alert triage, and incident response. With the speed and scale of Elastic Security, you can quickly analyze detailed endpoint data, examine and contextualize information with interactive visualizations, and integrate response workflows with external orchestration and ticketing tools, like SOAR platforms.
Prebuilt cloud protections and expanded detection options
Cloud security posture monitoring protections (rules beta / ML jobs GA)
Verizon’s 2020 DBIR estimates that configuration errors are causal events in 22% of data breaches. The stakes grow as organizations transition to the cloud, but 99% of configuration errors are still being missed. The security content shared in our latest release reduces risk by enabling security teams to keep a continuous eye on misconfigured assets, permissions, and user activity.
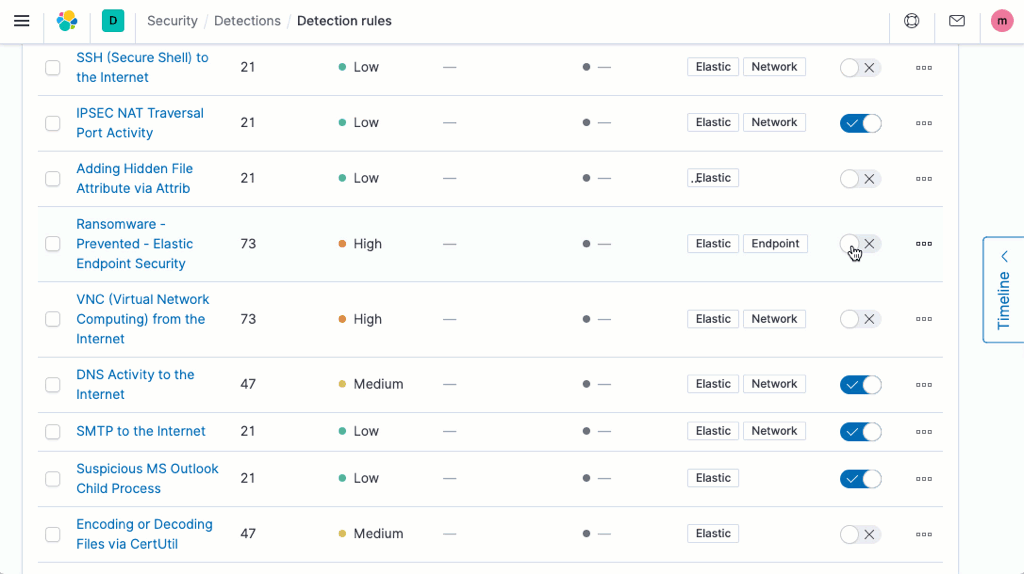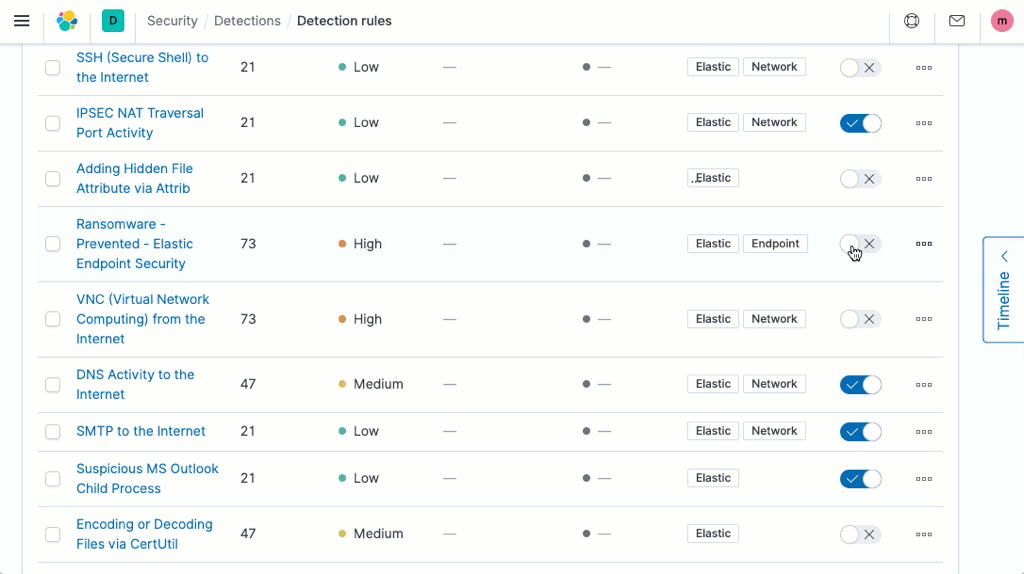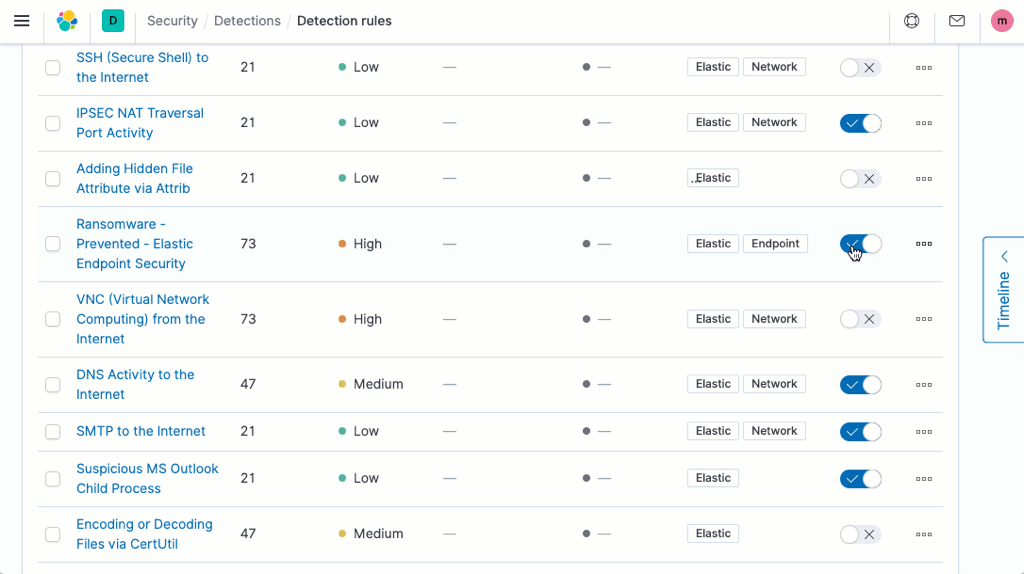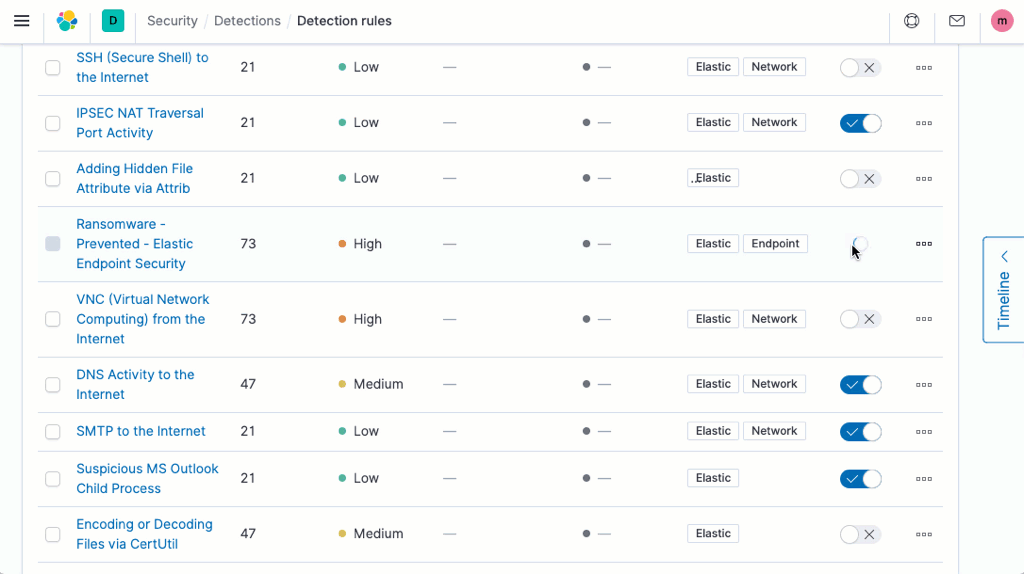 Elastic Security 7.9 safeguards cloud infrastructure and applications with new machine learning jobs and threat detection rules, helping prevent damage and loss. Like other Elastic-developed material, this new security content is aligned with the MITRE ATT&CK framework. It enables continuous analysis of data from both AWS CloudTrail and Okta to support cloud infrastructure monitoring and identity and access monitoring.
Elastic Security 7.9 safeguards cloud infrastructure and applications with new machine learning jobs and threat detection rules, helping prevent damage and loss. Like other Elastic-developed material, this new security content is aligned with the MITRE ATT&CK framework. It enables continuous analysis of data from both AWS CloudTrail and Okta to support cloud infrastructure monitoring and identity and access monitoring.
Have other use cases in mind? Explore the Detection Rules repo, which we recently opened to facilitate collaboration between the Elastic Security Research Team and community members.
Threshold-based alerting (beta)
Threshold-based rules, a new detection type, provides a new way to detect threats with Elastic Security, firing when more than a user-specified number of events for a given entity (e.g., an endpoint or user) meet a particular set of criteria. This enables environment-specific tuning of rules for use cases like detecting brute force attacks and spotting log sources that have stopped reporting.
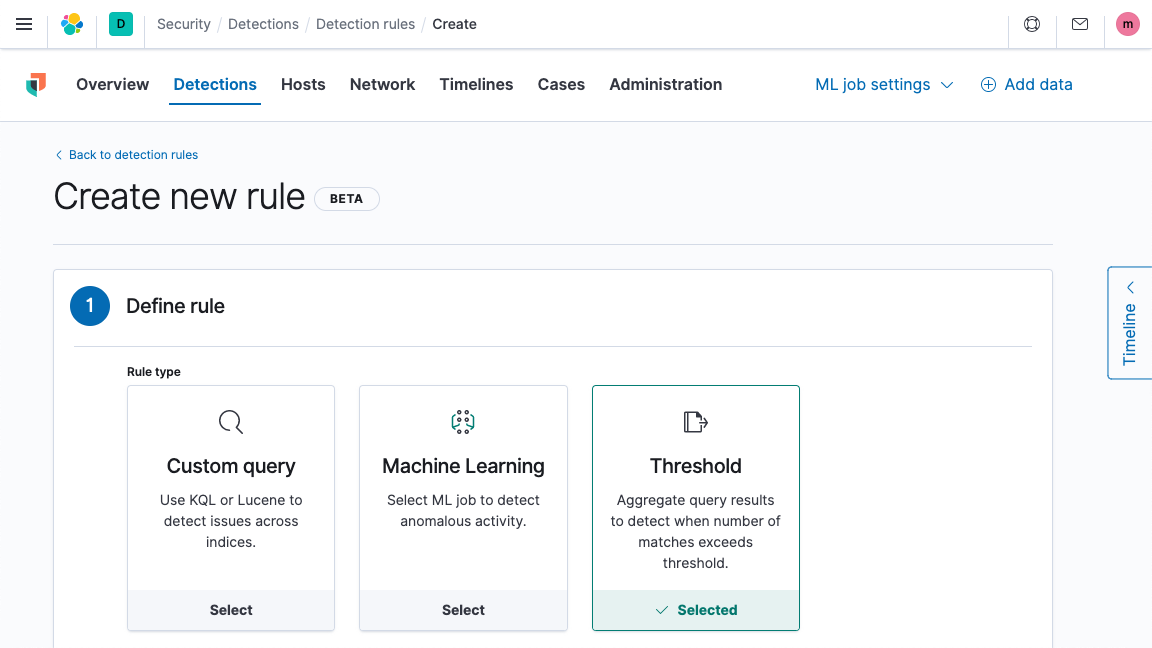
Building block rule designation (beta)
Rules specified as “building blocks” remove generated alerts from analyst workflows, allowing the creation of inputs to trigger high-fidelity alerts without causing increased noise for analysts. You could, for example, use two building block rules — one configured to alert on abnormally high web server logins and the other configured to spot out-of-schedule maintenance activity on a database server — as inputs for a rule generating alerts that are more likely to merit analyst attention.
Streamline analyst workflows with community-driven refinements
Elastic strives to deliver the intuitive, efficient, and delightful user experiences that security practitioners deserve. This takes rigor, but it’s worth it, because security teams spend countless hours in front of screens in pursuit of their mission to protect their customers, colleagues, and organizations.
Our UX team works hard to meet a lofty goal: finding the balance between simplicity for new users and flexibility for advanced users. They transform community feedback into operational efficiency, so thank you for your direct input into many of these enhancements to Elastic Security.
Interactive process tree visualization (beta)
A new interactive visualization of endpoint-based activity in Elastic Security 7.9 streamlines analyst triage, hunt, investigation, and response workflows. It equips analysts to spot potential adversary behaviors and attack progression (e.g., XLS file opened, process spawns, new outbound connection established). An option to attach a visualization (and associated data) to a new or existing case further streamlines workflows.
Endpoint context is critical to SecOps visibility, but too often, performance limitations or unmanageable costs prevent the centralized analysis of this data. This integration between the SIEM and endpoint security capabilities of Elastic Security enhances environmental visibility, reduces analyst guesswork, and increases team efficiency.
Investigation guides for prebuilt detection rules (beta)
All detection rules introduced in version 7.9 feature richly formatted investigation guides that suggest questions, actions, and next steps for analysts to consider when investigating a detection alert. Customizing an investigation guide for your environment or implementing one for a new rule is as simple as updating a markdown field.
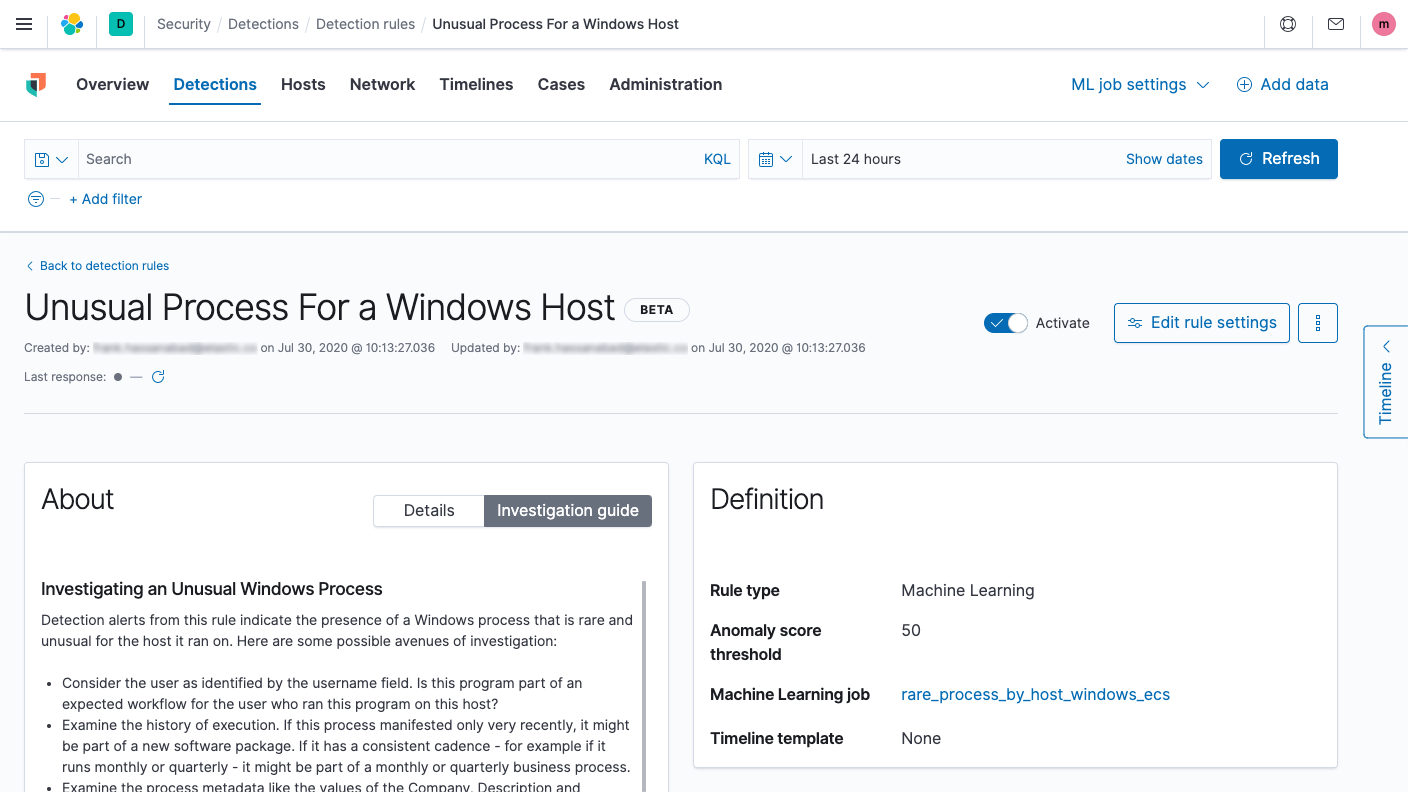
Customizable investigation timeline templates (beta)
Elastic Security 7.9 enables users to customize how data is filtered and presented on the investigation timeline through “timeline templates” associated with individual detection rules. Users can duplicate, customize, create, and share new timeline templates, which specify both the filter and columns (which fields and in what order). These curated views enable analysts to proceed directly from initial review of a detection alert to investigation, without pausing to re-configure the filter or viewable fields. Elastic security researchers align timeline templates with the investigation guides presented on new detection alerts, accelerating threat hunting and investigation.
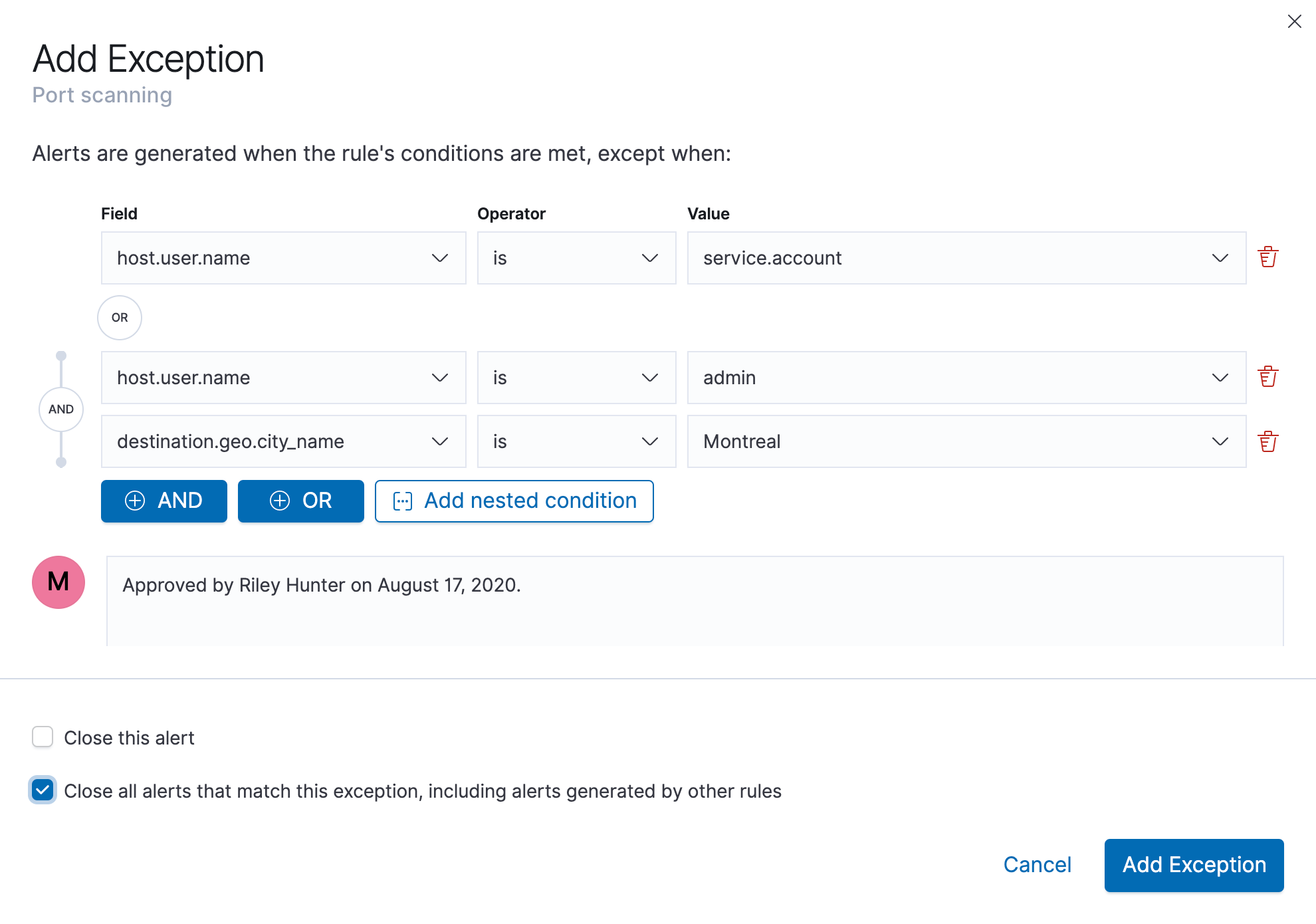
Unified alert exceptions workflow (beta)
Elastic Security 7.9 helps analysts reduce false positives, a significant and longstanding analyst frustration with common security technologies. The release makes it easy to create rule exceptions that prevent an alert from being triggered when specific conditions are met. Exceptions can be added individually or with a list, and detection rules and agent configurations can be updated in parallel, reducing the overhead associated with minimizing false positives.
Streamlined case workflows with IBM Security Resilient integration (beta)
Our new IBM Security Resilient integration enables security teams to readily integrate their security operations with the widely-deployed security incident response platform. Perform an investigation with Elastic Security, add investigation timelines and comments, and easily escalate by opening or updating a case within IBM Security Resilient — with just a click.
Further analyst interface enhancements (GA)
Elastic Security 7.9 delivers numerous other big and small UI enhancements that we expect to prove indispensable: full-screen mode, infinite scroll, custom IP reputation lookup links, and more. Many of these enhancements began as community requests, and together in version 7.9, they contribute to a more refined user experience.
Simplify data ingestion with expanded out-of-the-box data collection and preparation
New data integrations (GA, except where noted)
Elastic Security provides a curated experience for onboarding data, enabling SecOps, SecDevOps, and other teams to focus on the task at hand and not worry about wrangling data or chasing down data sources needed to support additional use cases. Version 7.9 adds integrations with new sources of endpoint and cloud data, including Microsoft Defender ATP, Windows PowerShell, Sophos XG firewalls, and beta support for Google G Suite (e.g., logins, admin activity, Drive activity).
Experimental data integrations
The release also introduces experimental support for 15+ common network and application security technologies via an OSS project from one of Elastic’s own, through your choice of Elastic Agent integrations and Filebeat modules:
| Source | Description | |------------------------------------|--------------------------| | Apache TomCat | Web server | | Barracuda Web Application Firewall | Web application firewall | | Blue Coat Director | Configuration management | | Cisco Nexus | Switches | | Cylance Protect | Antivirus | | F5 BIG-IP Access Policy Manager | Access control | | FortiClient Endpoint Protection | Antivirus | | Imperva SecureSphere | Web application firewall | | Infoblox Network Identity OS | IP address management | | Juniper Junos OS | Network security | | Microsoft DHCP Server | DHCP | | NetScout Arbor Sightline | DDoS security | | Radware DefensePro | IDS | | SonicWall Firewalls | Firewall | | Squid Proxy Server | Proxies | | Zscaler Nanolog Streaming Service | Firewall |
ECS 1.5 support (GA)
Finally, version 7.9 updates all Beats to support Elastic Common Schema (ECS) 1.5, ensuring consistency in how security teams execute tasks, including defining automations and performing investigations and analysis.
Give Elastic Security 7.9 a spin
Elastic Security 7.9 is a major milestone in accelerating our development of the foundation for your security teams. We’re excited to continue collaborating with our user community to enable security teams to operate more effectively and evolve more quickly. And if you haven’t joined our community yet, we welcome you to join us.
Want to get started today? Experience all that 7.9 has to offer on Elastic Cloud, or check out an Elastic Security demo. Already have ECS-formatted data in Elasticsearch? Just upgrade to 7.9 of the Elastic Stack to start preventing malware and detecting and responding to threats.
Want to see it in action? Join an upcoming ElasticON Security virtual event.