A game of nations — How nation-states prepare for cyber threats with Locked Shields

This blog is the first post of a two-part series. Part 1 talks about the concept of a nation-state and then provides a high-level overview of Locked Shields — the world's largest cybersecurity exercise — and its increasingly important role in promoting cyber warfare readiness for NATO member states and partners. Part 1 also outlines the steps taken by nations to prepare for a cyber warfare exercise. Part 2 will go in depth into the Locked Shields cybersecurity exercise and how Elastic Security can be leveraged to help protect, detect, and respond to threats in a cyber warfare exercise.
What is a nation-state?
A nation-state is a sovereign state inhabited by a group of people who share a sense of national identity and usually embody a common culture, language, and history. This commonality contributes to a sense of belonging and identification with the state, so the state represents the interests and aspirations of a nation. This definition is not strict, though, since many nations consist of diverse ethnic, cultural, and linguistic groups within their borders, yet are still considered nation-states for aspects that unify them.
Nation-states and hostility
A commonly exhibited trait by nation-states is the desire to assert dominance or achieve strategic objectives. This is attempted through acts such as aggression, cyber attacks, espionage, and disinformation, among others. A nation-state that commits such acts is referred to as a hostile nation.
Hostile nation-states are a high risk due to their ability to effectively employ technology and tools against the most difficult targets. These targets include, for example, classified networks and critical infrastructure (CI) like electricity grids, transport systems, and gas control valves. Hostile actions can target government institutions, private organizations, or even individuals.
Nation-state cyber threats
Nation-state cyber threats are methodically planned and executed cyber attacks that are usually carried out by state-sponsored actors on behalf of their government. These threats often involve the use of sophisticated techniques and advanced capabilities and are backed by significant resources and expertise.
These nation-state cyber threats typically involve Advanced Persistent Threat (APT) groups that operate over a long period, with a focus on stealth, persistence, and intelligence gathering. The attacks are advanced due to their use of sophisticated intrusion capability as well as malware. This also includes the development of custom malware and tools when needed.
The persistence aspect focuses on a committed execution of attempted attacks over a long period of time with the aim of being successful in breaking into the target. The attacks are usually progressive and of a variety, often stealthy in nature. Threats are the proactive discovery and exploitation of the target's technical and non-technical vulnerabilities.
Nation-state cyber threat actors
The actors behind nation-state threats are usually state sponsored agencies or organizations whose aim is to gather intelligence and information of national interest. This interest is usually focused on critical infrastructure of other nations and organizations of interest. Nation-state actors have advanced capability in cyberwarfare for the purposes of espionage, among others.
There are two ways a nation can employ nation-state threat actors. Firstly, a nation may engage its own intelligence agencies and specialized cyber experts. Or, some nations work with organizations that specialize in cyber crime. It is also common to have a nation use nation-state actors in both categories. In either case, there is a lot of espionage associated with nation-state actors. These actors can attack other nations or other outside organizations, including private companies and non-governmental organizations.
The goal of nation-state actors is to use their technology skills to:
- Steal sensitive information
- Disrupt critical infrastructure
- Gain an advantage over state adversaries
- Facilitate hacking
- Sabotage
- Commit theft
- Spread misinformation
Achieving these goals tends to be seen as an enhancement of a nation-state’s counterintelligence strategy.
Enter Locked Shields — One of the world's largest cybersecurity exercises
So, what is Locked Shields? It is one of the world's largest and most realistic cybersecurity exercises, aimed at testing the defense capabilities of member nations in a simulated cyber attack. Elastic participates by supporting some of the member nations that take part in Locked Shields. Locked Shields is an annual exercise hosted by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE), designed to test and improve the preparedness of member nations and partner states against large-scale cyber attacks.

As described on the CCDCOE website, Locked Shields focuses on testing and improving the skills, capabilities, and coordination of participating member nations in defending against sophisticated cyber attacks. The exercise simulates a realistic and complex cyber threat scenario where each member nation must work together to protect a fictional computer network from various cyber threats.
The exercise provides a platform for participants to enhance their cyber defense capabilities, assess their readiness, and identify areas for improvement. It also facilitates international cooperation, knowledge sharing, and the development of best practices in the field of cybersecurity. Participants in the roles of cybersecurity professionals engage in defensive operations, incident response platform, and testing the decision-making processes.
Berylia and Crimsonia: The two nation-states that set the context
The Locked Shields exercise focuses on two fictitious nations, Crimsonia and Berylia. These have been used as part of the exercise scenarios since inception of the exercise.
Berylia is typically depicted as the victim of aggressive actions from Crimsonia. Berylia is defended by the blue teams. The Locked Shields exercise challenges teams from various member nations to defend the network and systems of Berylia while continuing the operation of assorted services. The teams must handle and respond to a wide variety of cyber threats while maintaining the confidentiality, integrity, and availability of the systems.
Crimsonia, on the other hand, represents the attacking side. In these scenarios, Crimsonia often depicts a sophisticated cyber threat actor. It uses a range of tactics, techniques, and procedures (TTPs) aimed at disrupting, degrading, or destroying Berylia's critical infrastructure and information systems. This could include attacks on networks, data breaches, distributed denial of service (DDoS) attacks, and other types of cyber espionage and warfare.

Practice makes perfect: Preparing for nation-state threats
Organizations and countries alike can prepare for nation-state attacks in various ways. The preparatory steps highlighted in this section are ones taken by some of the successful member nations during Locked Shields. The steps are similar to those stipulated by recognized standards such as the NIST computer security incident handling guide, and others alike. They mimic steps a nation-state would take for cyber warfare readiness in reality.
Stakeholder engagement
Member states are expected to have strategic decision planning for solving legal, media, and communication challenges. Internal and external stakeholder engagement is very important. Cyber defenders need to collaborate among themselves and act as rapid reaction teams and advisors to the high-level crisis management team. Actions must meet national and international regulatory standards, such as EU, NATO, and UN regulations.
Locked Shields, in addition to technical submissions, scores on how well teams collaborate and how they share information. For example, there are scenarios where certain threat reports need to be communicated to the legal team by incident responders. Sharing this type of information in a manner that can easily be understood by another audience, in the middle of cyber warfare, requires well-established communication and cooperation among stakeholders — a subtle yet very important point.
The best teams tend to have a well-defined list of stakeholders, including:
- Team managers
- IT experts
- Legal
- Public affairs and media relations
- Resiliency teams for business continuity planning (BCP) purposes, among others
Cybersecurity is a collective effort, and all stakeholders should be prepared with best practices for how to respond to and communicate in times of warfare. Communication and cooperation must be swift because a large cyber attack can quickly escalate into a large-scale security crisis. This aspect of Locked Shields prepares organizations and nations to handle this better.
The rules of engagement must be clear for all stakeholders during cyberwarfare. Well-articulated processes are effective in ensuring successful cyber defense operations.
Asset management
In addition to stakeholder management, member nations have to understand the various critical infrastructure for the fictional island state Berylia. As the mantra goes, “you can’t protect what you do not understand.” The member nations have to inventory all assets: endpoints, network segments, applications, and users. The next step is to identify the assets that have critical data on them for each CI. Asset management is a critical foundational component of any cybersecurity program.
The state of Berylia has CI encompassing military and civilian IT systems. This includes networks, communication facilities, water purification systems, the electric power grid, and even a central bank.
Member nations using Elastic take inventory in a similar way to how the internal Elastic InfoSec team does asset management. The Elastic InfoSec team sees asset management as one of the building blocks of a proactive, end-to-end security strategy. The figure below is a summary of this approach. You can read this blog for more details.
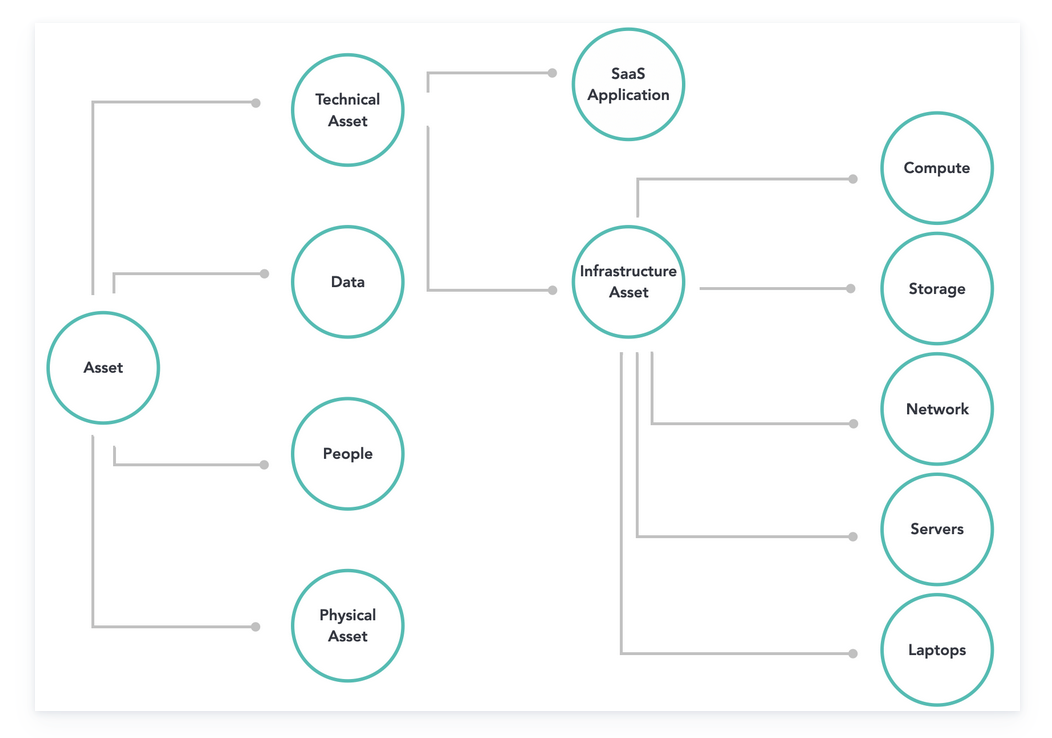
As can be seen in the figure, the Elastic platform can be used for asset management by utilizing its prebuilt capabilities as well as custom enhancements. Assets discovered from vulnerability management tools and configuration management databases (CMDB) are also valuable input for inventory. The output of this phase helps member nations have well-documented assets for identified critical infrastructure, including technical assets, people, and data. Having this relevant context is useful when detecting, investigating, and responding to threats.
The importance of preparation
This blog gave an overview of nation-states and the related concept of hostile nation-states. It has also highlighted steps nation-states take in preparing for Locked Shields, an exercise that promotes cyber warfare preparedness. Even though there is a gamification aspect to Locked Shields, there are many ways this exercise prepares nation-states for realistic cyber warfare.
In part 2, we will go in depth into Locked Shields and the live-fire activities of the exercise. We will look at how Elastic Security is used in the exercise, particularly the prevent, detect, and response capabilities, and how they enable security analysts and responders to have relevant insights and subsequently take relevant steps in the presence of cyber warfare.
Get started
Elastic Security protects organizations and their data from attack. The solution can thwart complex attacks with advanced analytics, blocking threats such as malware and ransomware on critical systems. Elastic Security enables the advancement of security operations maturity to stop threats at scale. It is simple and easy to get started with Elastic Security.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.