How to build a cybersecurity asset management solution on the Elastic Stack

In the world of cybersecurity, you can’t secure something if you don't know it exists. That's why asset management is a critical foundational component of any cybersecurity program.
Cybersecurity asset management is an important and ongoing topic for practitioners tasked with creating and maintaining an Information Security Management System (ISMS). While often discussed, the challenge is not quite solved.
Many organizations face the same challenges as we do at Elastic — a myriad of assets and security solutions, but imperfect visibility and control. Sound familiar? On the Elastic InfoSec team, we decided not to accept the status quo, and built a cybersecurity asset management solution on the Elastic Stack as one of the building blocks of a proactive and end-to-end security strategy.
Here's how we did it.
First, asset classification
For us, it all started with asset classification.
When we talk about assets, most people think about things like laptops and servers. For us, an asset is anything of value to the business. This can take the form of a device, data or information, software systems, cloud instances, or even people.
Some challenges we've faced (and how you can overcome them)
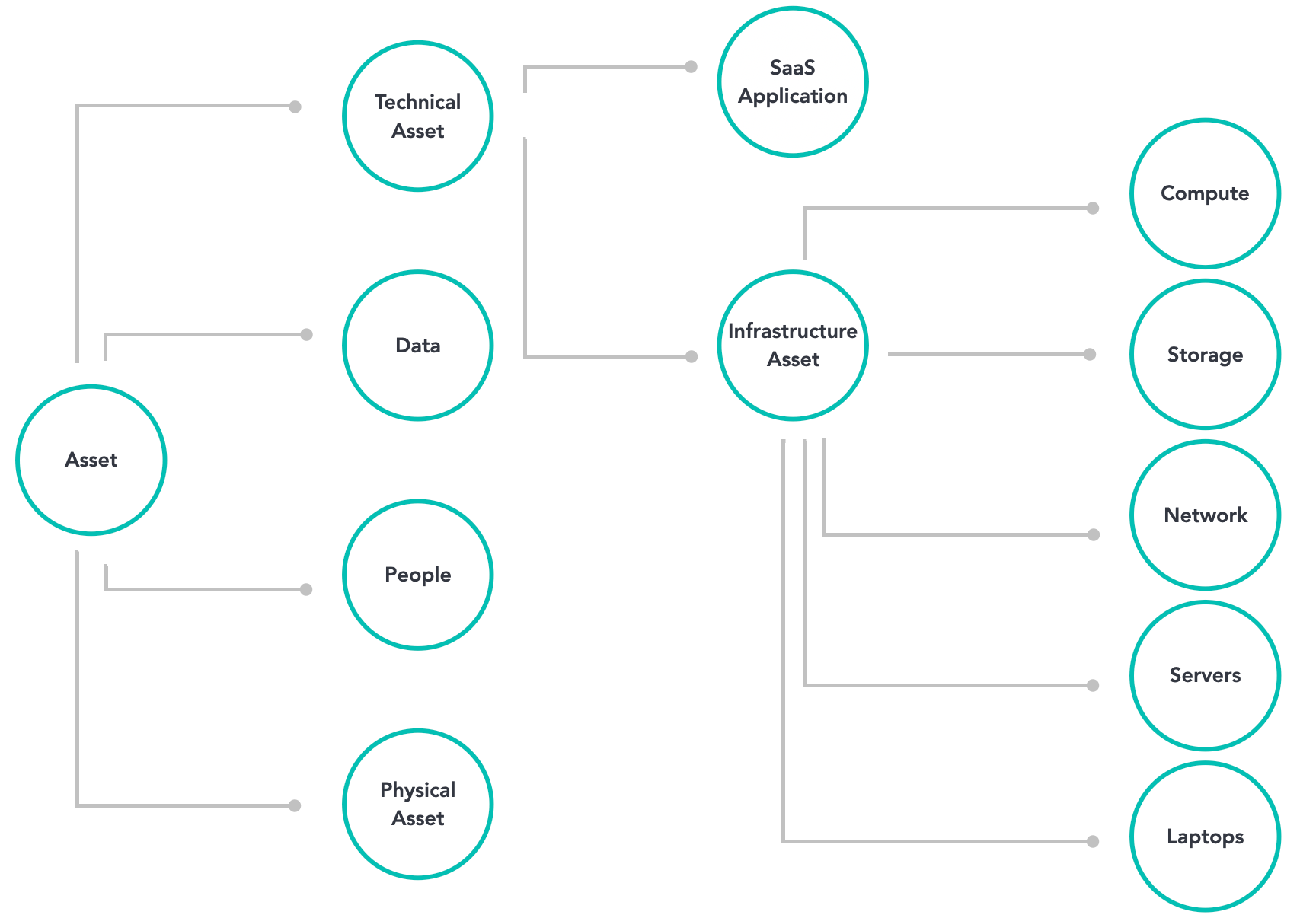
Overall, the process of creating an asset inventory can be cumbersome and time-consuming. First, there's the process of defining the taxonomy of assets that are most important and the schema for assigning different assets into relevant categories.
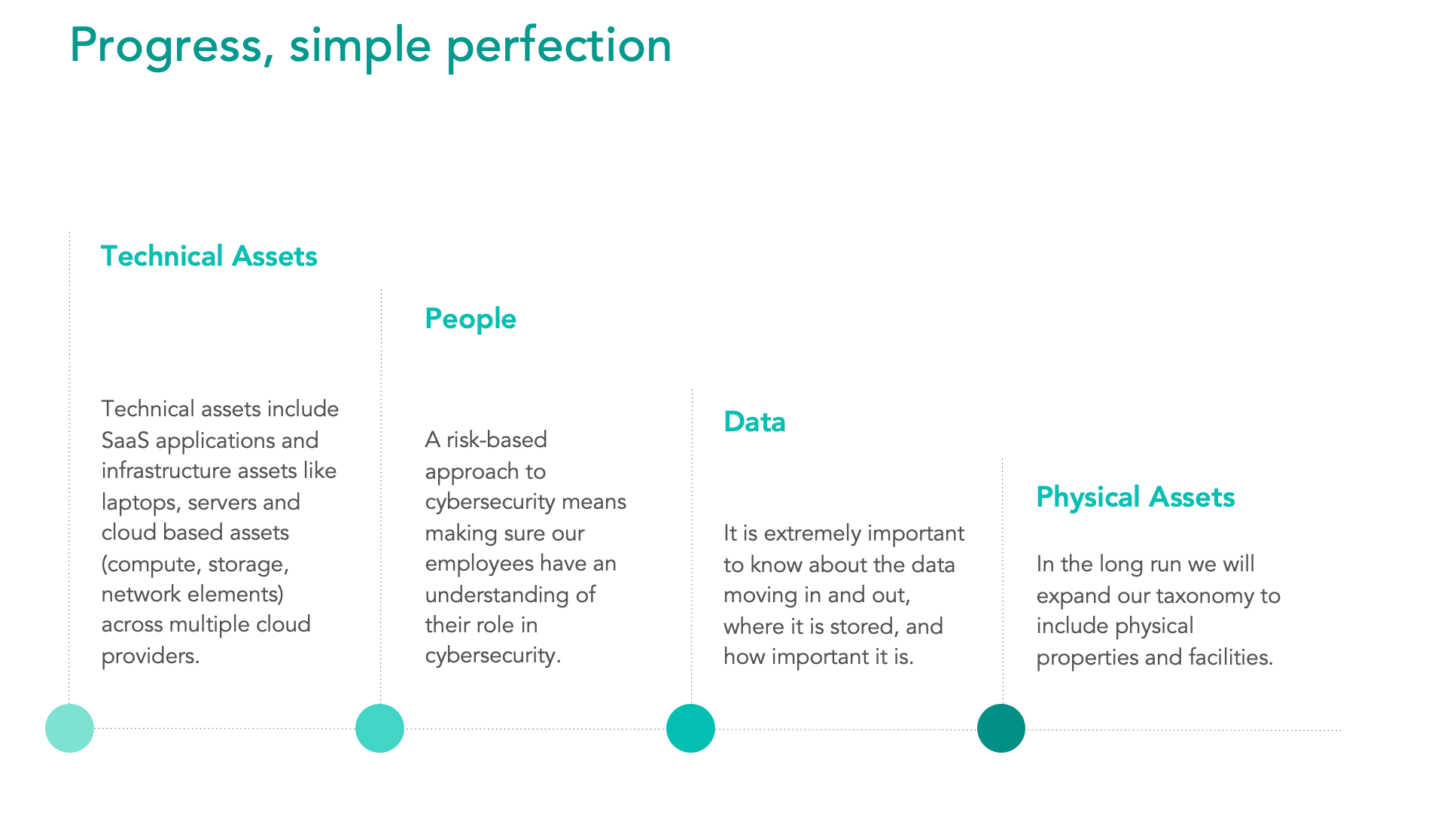
We’re defining an asset as anything that is useful or valuable to Elastic. If this definition feels all-encompassing, you're not wrong. This is why we decided to concentrate our efforts on the following asset categories:
- Technical assets - Technical assets include SaaS applications and infrastructure assets like laptops, servers and cloud-based assets (compute, storage, network elements) across multiple cloud providers. While many organizations would classify workstations as physical assets, Elastic is a company that is distributed by design. Our employees work from around the globe (often from untrusted networks) and we have no physical controls or a traditional corporate network that our laptops connect to.
- People - When it comes to asset management, we often think about hardware and software, but forget about people. A risk-based approach to cybersecurity means making sure our employees have an understanding of the crucial role they play.
- Data - It is crucial to know all the data moving in and out, where it is stored, and how important it is.
- Physical Assets - Our taxonomy includes physical properties and facilities, which is part of developing a comprehensive cybersecurity program.
Then, there's the challenge of collecting data from multiple sources, especially in an environment that is distributed by design. This is where working with the Elastic Stack and shifting to Infrastructure as a Service is a huge advantage.
The shift to Infrastructure as a Service means that the cloud provider(s) know exactly what assets you have in the environment — otherwise, they couldn't send that huge bill every month. This means real-time inventory information is available without the need to rely on manual documentation or ping sweeps to understand what is on the network.
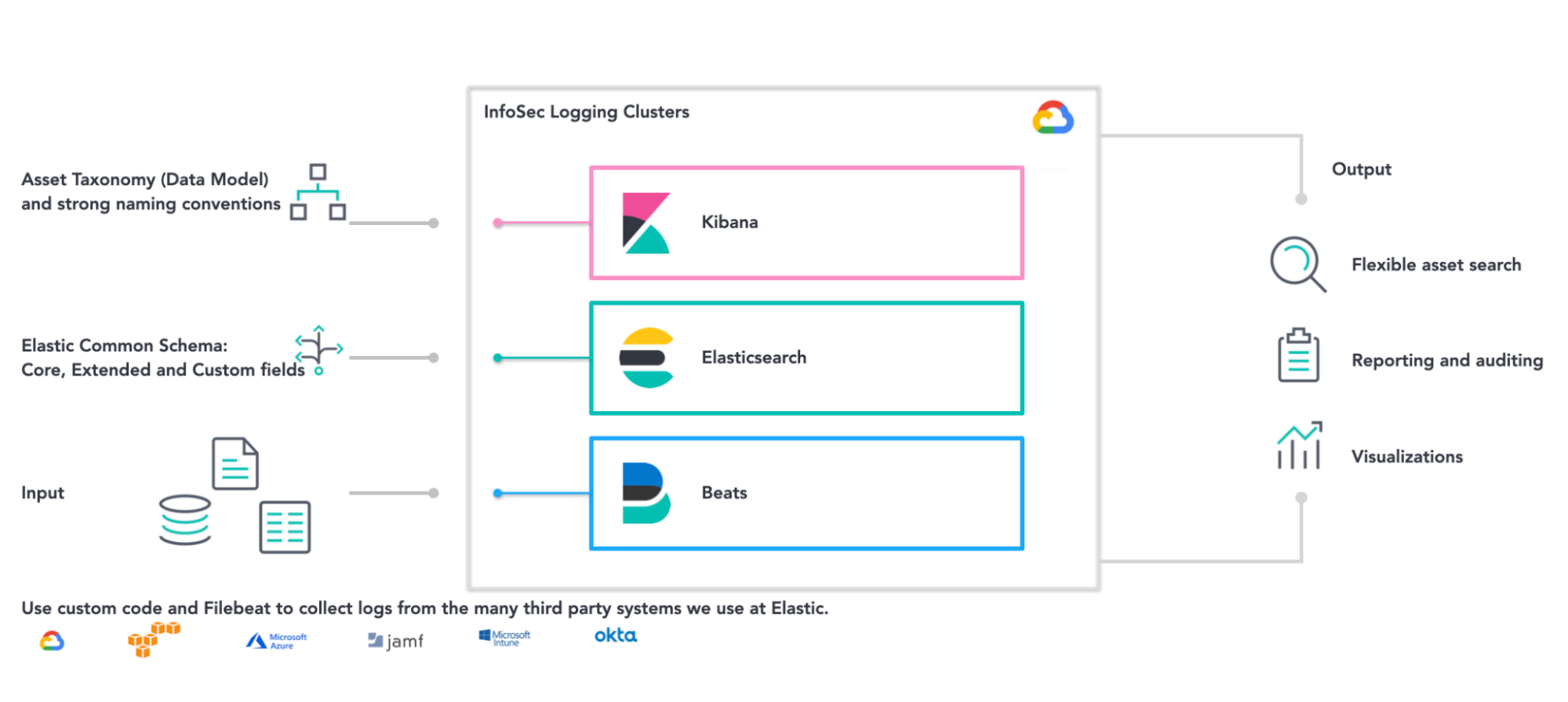
Of course, the reality is more complex. We are multi-cloud and have hundreds of separate accounts across GCP, Azure, AWS, and IBM. And of course, each provider does it a little differently, but all of them make inventory data available via an API and we are pulling that into a consolidated asset inventory built on the Elastic Stack and deployed on Google Cloud's Kubernetes Engine.
Our information security asset management does not exist as a standalone, but takes advantage of the existing Elastic Stack capabilities including search, visualizations, dashboards, machine learning features, or Beats — which are great for gathering data. For simple calls, we use Filebeat to retrieve assets from provider APIs directly. Whenever we encounter multi-step API calls like ETL, we use custom code to collect the information.
Last but not least, more and more compliance / best practices frameworks are moving towards a risk-based or maturity-focused goal. This requires us to know where we stand concerning control objectives, not “at some point in time” but rather “at any point in time.” Without a comprehensive and almost real-time inventory of all assets, it is nearly impossible to validate compliance in a programmatic fashion. For this reason, we treat the data in the asset inventory as time-series data to be able to track the configuration of an asset over time.
Wrapping up
The totality of that data, when combined and correlated, provides a powerful overall picture. But it will also allow us in the future to query how any and every asset either adheres to, or deviates from, their security policies and controls. The journey doesn’t end here:
- With lots and lots of data, our initial standardization, simplification and automation efforts are only the beginning. Our short- to mid-term efforts will focus on detecting non-conformities and policy violations in (near) real-time.
- Mid- to long-term efforts: Big data and advanced analytics to process and interpret massive volumes of asset data to identify trends in non-conformities or subtle policy violations.
- Long-term vision: Going into the direction of adaptive governance, we should be able to have enough data to evaluate the impact of relaxing or strengthening some controls. As an example, we should be able to evaluate the impact of changing some of our controls to be more (or less) restrictive — how many assets would be affected, what type of assets would be affected, etc.
You can get started with the Elastic Stack to solve asset management, too. Try Elastic for free as a 14-day trial of Elastic Cloud.