Elastic Security evolves into the first and only AI-driven security analytics solution

In our previous installation, we discussed the history of security information and event management (SIEM) solutions — from collection to organizational detections and finally to response and orchestration. Now, we are firmly in the SIEM 3.0 revolution and focused on applying generative AI to every applicable process in the security operations center with tremendous success. Elastic Security is leading the charge in this revolution by delivering the first and only security analytics solution with generative AI accelerating every core analyst workflow — optimizing your existing team and empowering newer members to get up and running faster and with more accuracy and efficacy.
Introducing AI-driven security analytics
The rapid acceleration of Elastic Security
Elastic Security is the first and only AI-driven security analytics solution poised to meet the challenges of the modern security team. It is built on the Elasticsearch AI platform, which includes retrieval-augmentation generation (RAG). RAG is the ultimate means of ensuring that large language models (LLMs) have all the appropriate context they need to answer a given question, allowing for bespoke and tailored responses to be presented back. Without the correct context — or an efficient, fast, and powerful way to search and retrieve that context — LLMs are only as good as the public data they were trained on. RAG also eliminates the need to constantly retrain an LLM, which is a time consuming and expensive task — especially on data found within a security analytics platform, which changes every minute.
Our solution is defined by three fundamental tenets that separate Elastic Security from all others in the market.
Tenet 1: Distributed data mesh architecture
The problem: Analyzing all of the data
Before detection engineers can craft content, analysts can triage alerts, or incident responders can remediate an incident, the security team needs visibility into their environment. There is a reason why the CIS Top 18 has led with visibility as their top priorities for decades: you cannot protect what you can’t see.
Unfortunately, the need for complete visibility has been challenged with the exponential increase in data volumes — especially with the transition to the cloud. Security teams have been forced to make decisions based on budgetary and technical limitations, not based on the value of the data they need to protect. Many have adopted a data lake approach, where information is quickly moved from an active system to inexpensive data storage. It is then accessed if and when it is needed.
Although such data lakes can address the economic challenge of storing the information, they fail to solve the operational problems of accessing the information fast enough to stop damage and loss to an organization. Remembering the Log4j attack, many companies struggled to determine if their organizations were affected. For teams whose data was in frozen storage, they had to guess and check timeframes, “thawing” a portion of frozen data, searching, and then repeating this process. Teams didn’t know for sure until they thawed and checked all of their stored data, which was far too time consuming to accomplish. Data lakes need to not only be affordable, but they also need to be searchable.
The modern SOC is distributed
Data has gravity.
It is expensive to move data around a distributed network, especially when it’s moving through regions in the cloud or through cloud providers and paying additional data transmission service (DTS) fees. This doesn’t even account for the expense of building a monolithic copy of information, which requires a massive amount of hardware and engineers, or the fact that it isn’t possible in certain areas due to data privacy regulations.
Elastic allows you to keep your data near where it is generated or collected. Our distributed data mesh architecture allows users to keep systems in any major cloud provider and/or on-premises, and then designate one system as the main SIEM where security operations take place. This solution appears to an analyst as one centralized SIEM, simplifying searches across the connected systems. The security analyst never needs to leave the main system to run detections, machine learning models, threat hunting, alert triage, incident response, or other use cases across any number of distributed security clusters.
Searching frozen data — fast
With Elastic’s distributed data mesh architecture making it affordable to store years of data, the next question is about the speed of accessing this information. Elastic leads the market here, too. Elastic Security makes the previously impossible both possible and simple. With a track record of powering millisecond search at organizations like Randstad Netherlands and Texas A&M, Elastic Security routinely wows new users with the speed and scale. Using a proprietary feature called searchable snapshots, Elastic can search frozen data like S3 in seconds without rehydrating all of the information. This makes security analytics extremely fast and affordable, even over months and years of data.
Instead of a slow, difficult data lake, operationalize your security team with Elastic’s distributed data mesh. Next time you are asked “did this occur?”, you can answer with complete assurance.
Tenet 2: Our open and transparent approach to security
Elastic Security has long been committed to openness and transparency, which are critical for organizations to assess and reduce their cybersecurity risk. When adopting a technology, you are putting your trust in the organization behind the offering — and trust is not earned with secrecy.
We previously stated that “[Open Security] means security vendors do their work out in the open, share code, detection rules, and artifacts to further the understanding of how to truly protect systems from intrusions and exploits. It’s a joint effort to improve security software so that all may benefit.” This openness is both altruistic and self-serving because a rising tide lifts all boats. Cybersecurity should not only be for those with the enterprise budgets to afford it. Anyone in the world could be a victim of a cyber attack; therefore, everyone in the world should have access to enterprise-grade cybersecurity. We must democratize security in order to stem the rising tide of attacks.
An open data schema is part of the foundation of Elastic Security. Your data is yours to use however you want, whether it’s with our standardized open source schema — Elastic Common Schema (ECS) — or one of our other schema integrations. ECS enables “write once, run everywhere” detection rules, giving teams the flexibility to easily onboard new data sources without changing detection logic. ECS has continuously evolved to support new types of security data, such as vulnerability, threat intelligence, and email logs, and has been adopted by countless vendors and organizations. To add further momentum, we recently contributed ECS to the OTel Semantic Convention.
Elastic also remains supportive of emerging and long-established schemas to ensure that organizations using them can leverage Elastic Security’s powerful analytics. For example, if you’re storing data mapped to OCSF in Amazon Security Lake, we provide a prebuilt OCSF integration to translate it to ECS. Similarly, if you’ve invested heavily in Common Event Format (CEF), we have a CEF to ECS integration, too. We were founded on this idea of openness, and it’s something we will continue to pursue.
Tenet 3: Unified approach to security operations
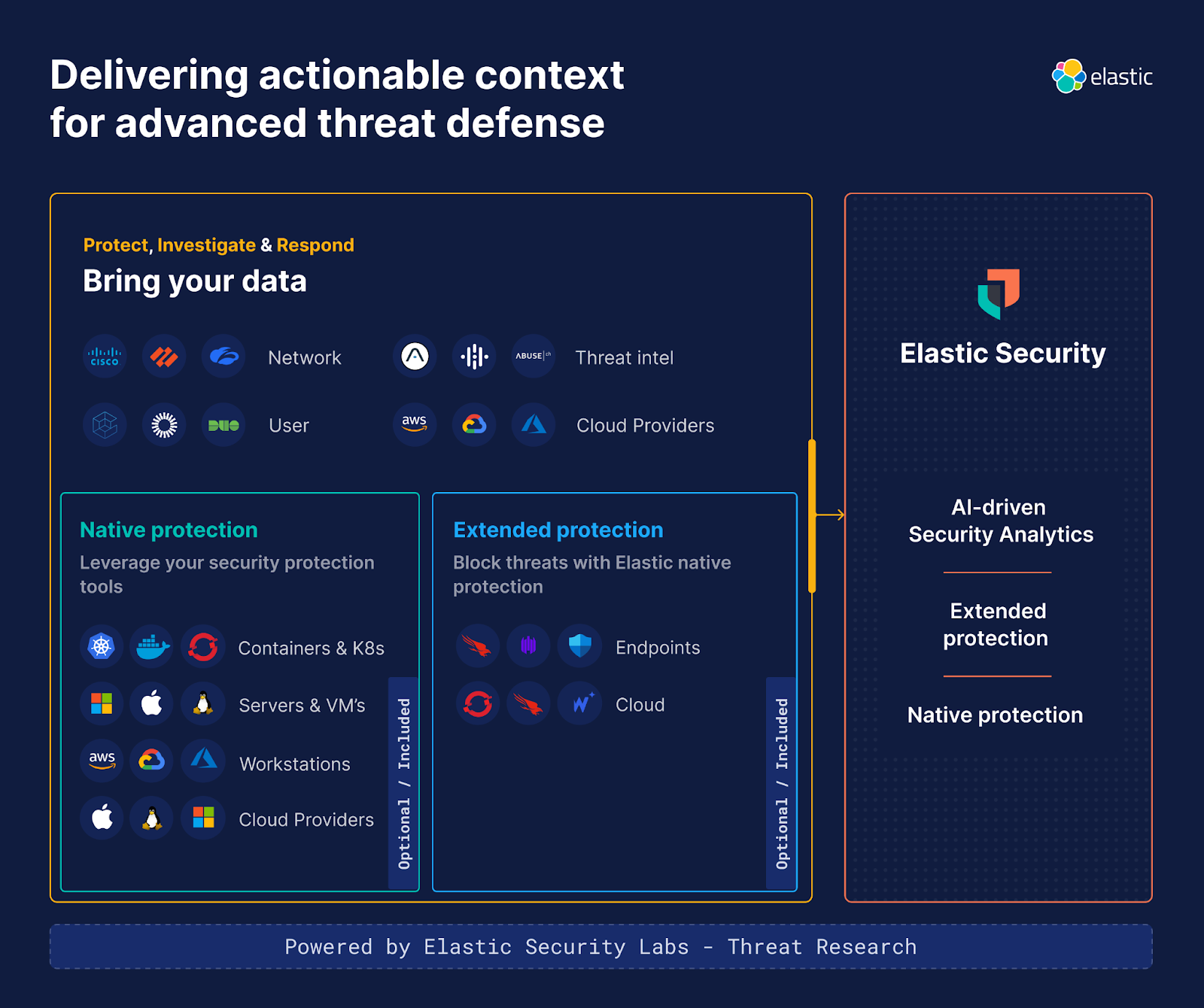
Elastic Security has one mission: to protect the world’s data from attack with democratized, enterprise-grade security. This mission includes empowering end-to-end workflows into your existing security ecosystem or providing those capabilities natively for those that cannot afford or access a deep bench of security tooling. We build, deliver, and sell only one solution: Elastic Security, which offers a wealth of optional and included capabilities. A typical customer grows with us in the following ways:
Start with analytics: Replacing a legacy SIEM with our AI-driven security analytics solution implements faster versions of proven SOC workflows and empowering new processes in the security organization
Expand to extended protection: Instantly get extended detection and response by adding the raw events from CrowdStrike, SentinelOne, Microsoft Defender, Wiz, and more into Elastic.
- Augment and/or replace with native protection: Augment or replace with a legacy point solution with Elastic’s native protection.
Elastic Security continues forward
This blog covered the tenets that we build with and how we’re driving towards a generative AI future. Our solution is built to make security teams as efficient as possible, and we’re excited to provide that with a boundary pushing security solution.
Our team is ecstatic to be leading the charge towards AI-driven security analytics. We’ve explored what drives us forward as a solution, and we’re excited to get into the weeds with our next post. The tenets explained in this blog will be expanded upon in our final installment, which explores our core capabilities at a glance and exactly how we streamline security operations. In the meantime, you can register for our upcoming webinar Fight Smarter: Accelerate Your SOC with AI. Stay tuned!
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, ESRE, Elasticsearch Relevance Engine and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.