Elastic provides the foundation for the DoD's pillars of Zero Trust Networking

The whole point of IT systems, whether deployed via traditional methods or via modern practices (such as Agile methodologies, DevSecOps, and orchestration platforms like Kubernetes) is to make data available for business operations — those operations could be making business decisions, identifying or troubleshooting system performance and efficiency issues, detecting bad actors, or protecting organizational assets. Unfortunately, the result is a large array of disparate data silos that were never designed to interact with each other.
What's needed is the ability to collect and ingest data from multiple disparate sources and bring them together within a common access layer, in a format that allows cross-correlation and analysis, at scale and in near real-time. Elastic provides a uniquely powerful data collection, monitoring, and analytics platform that enables observability and security spanning all layers of the organization's data operations.
Support for all the pillars
There are many definitions of Zero Trust, and several different combinations of the core “pillars” that cover the concepts that would enable the application ZTN to be used in a real-world way. In the end, Zero Trust Networking (ZTN) is a set of principles that spans the entire breadth of enterprise operations, while also redefining access patterns and controls on those systems.
As an example of how confusing this can be, just within the US Public Sector there are several competing reference documents, each outlining their own take on what the core principles/pillars are:
- The Cybersecurity and Infrastructure Security Agency (CISA) breaks down 5 pillars in its “Zero Trust Maturity Model”
- The National Institute of Standards and Technology (NIST) supports 6 pillars in its “Zero Trust Architecture”
- The U.S. Department of Defense (DoD) offers 7 pillars of Zero Trust in its “Zero Trust Reference Architecture”
- The Government Services Administration (GSA) names 8 pillars in its “Zero Trust Architecture” design
Regardless of which reference you follow, the success of ZTN depends on more than any one tool or layer; it requires them all to work in conjunction with each other at speed and scale, with a holistic comprehension of events and activity at all layers that can drive the policy decisions and enforcement. The Elastic Stack can perform the vital role of bringing together the data streams generated at the edge, through the perimeter defenses, and correlate those with the activity in and around the applications and services being accessed.
Zero Trust principles are especially powerful when used in conjunction with other approaches, such as continuous monitoring, chaos engineering, and real-time situational awareness, which is based on leveraging all available data as a strategic asset.
Let's dive in on one of these standards and map the Elastic Stack's capabilities to the "Zero Trust Pillars" to show how Elastic's technology supports and enables the practical application of Zero Trust principles across the entire enterprise.
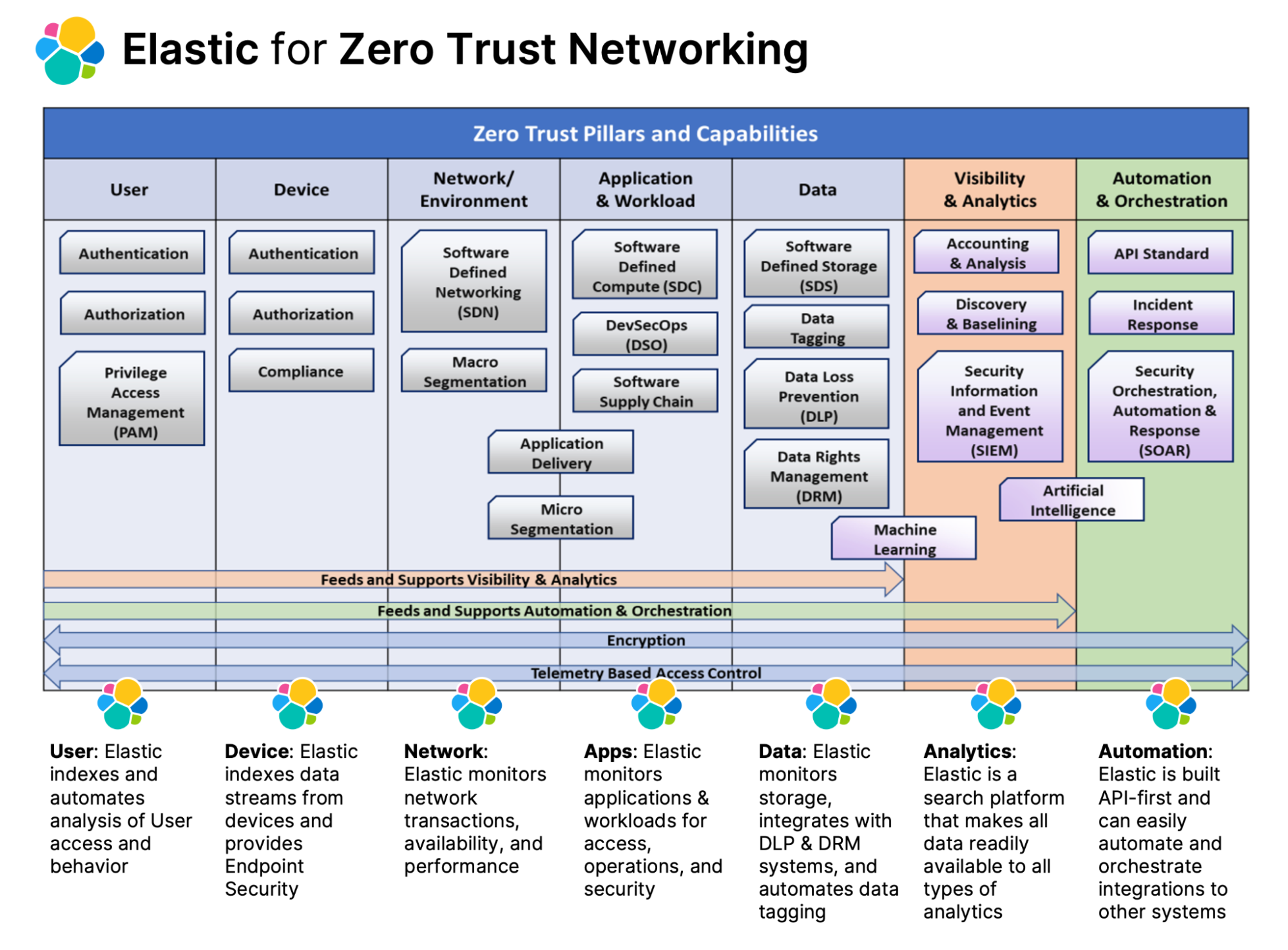
The DoD CIO's pillars of Zero Trust
The following section describes in further detail how Elastic can be used to support and enable each of the DoD CIO's pillars of Zero Trust, taken from the DoD Zero Trust Reference Architecture document.
The offset portions below are quoted directly from that document:
2.3 Pillars
Zero Trust Pillars are identified in the ZT Strategy and are in alignment with the common industry identification of ZT Pillars. A Pillar is a key focus area for implementation of Zero Trust controls. ZT is depicted as interlocking puzzle pieces that symbolize a data Pillar surrounded by Pillars of protection. All protection Pillars work together to effectively secure the Data Pillar.
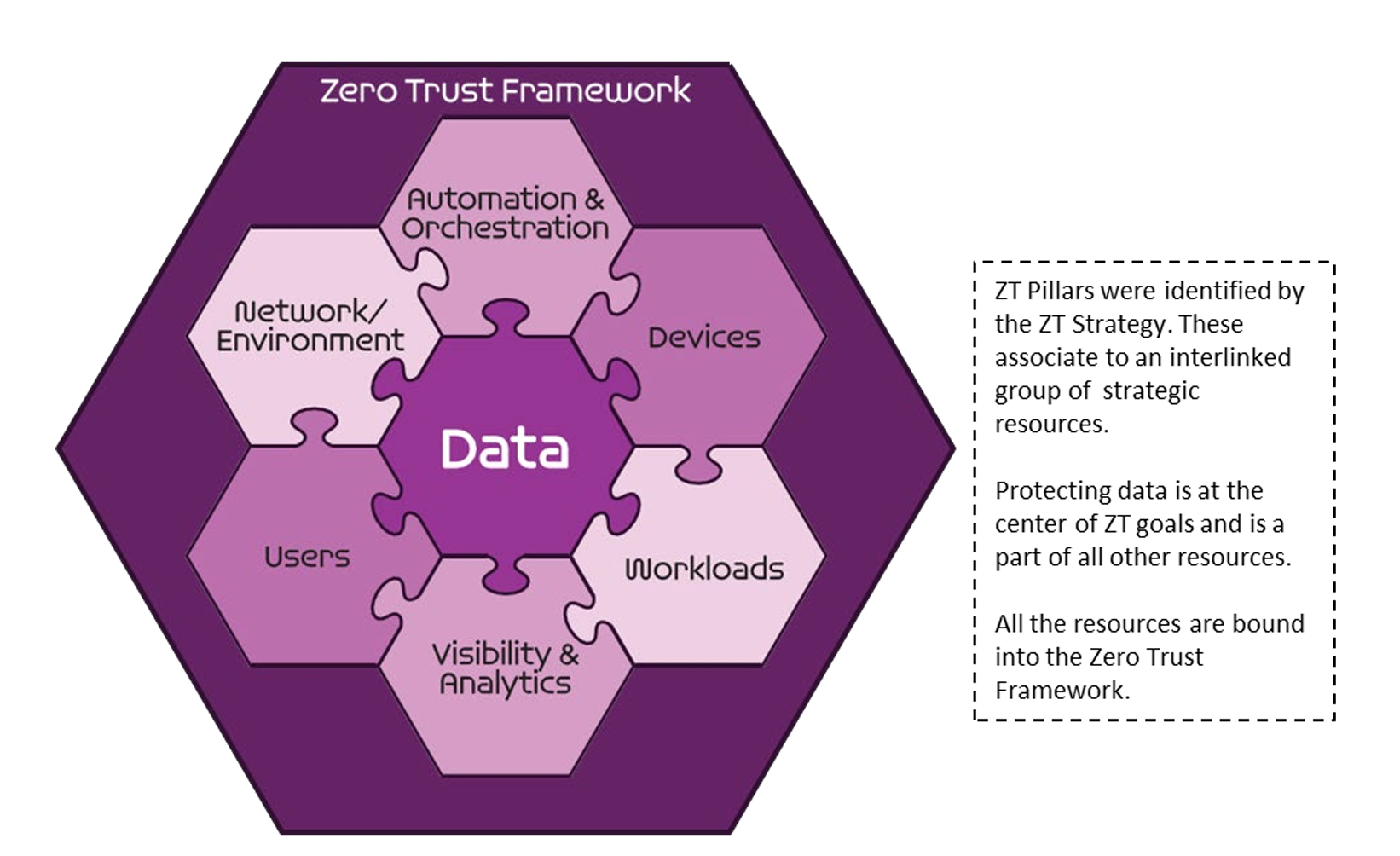
The DoD CIO has aligned the principles of Zero Trust Networking across seven pillars that span the core capabilities of data operations in the DoD enterprise. Many of the capability areas blend, overlap, and reach across several logical, functional, and technical boundaries. The depiction of interlocking puzzle pieces is an apt visualization of how interdependent these various streams really are in a ZTN deployment. Zero Trust Networking presents a wholly new paradigm for how access controls are applied to enterprise network resources and data systems.
Regardless of current or future toolsets implemented in the service of Zero Trust, a common data operating layer that can provide near real-time query and analytics of all relevant data streams is a foundational capability. What's needed is a data platform that can be the “glue” between all systems and make them all more integrated, accurate, and trustable; it requires a system that can scale as needed in a cost-effective way, and yet remain flexible enough for changing mission needs in the future.
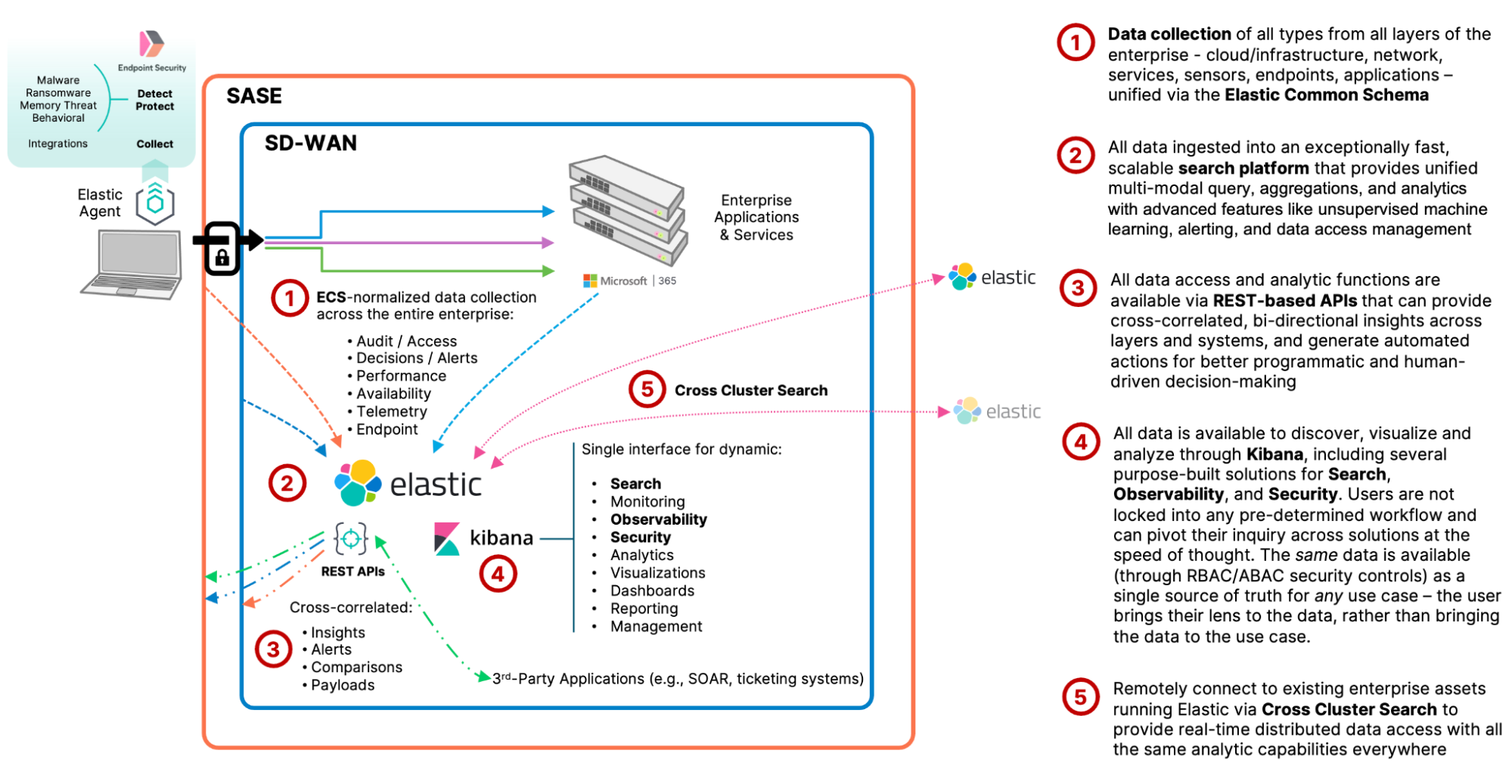
The Elastic search platform provides a distributed data access layer that connects and operationalizes data from disparate systems and exponentially enhances operations on any kind of data. Elastic can be the foundational data platform that supports and truly enables each of the DoD CIO's pillars of ZTN:
User - Securing, limiting, and enforcing person and non-person entities' access to DAAS encompasses the use of identity capabilities such as multi-factor authentication (MFA) and Privileged Access Management (PAM) for privileged functions. Organizations need the ability to continuously authenticate, authorize, and monitor activity patterns to govern users' access and privileges while protecting and securing all interactions.
User - With Elastic as the common data access and analytics layer that connects all data streams from endpoints, through perimeters/boundaries, to applications, entity activities and behaviors are easily collected and monitored. Within Elastic's unified data plane, events from the various ZTN tools can be validated and cross-correlated, which helps to ensure ZTN principles are continually applied and enables complex behavioral detections, automated alerts, and actions to be generated. Behavioral detections can be based on any activity that can be found using any of the Elastic search platform's wide array of search modalities — including advanced geospatial, vector similarity (kNN/ANN), thresholds, machine learning (ML) anomaly detections, aggregated signals, and several others.
Device - Continuous real-time authentication, inspection, assessment, and patching of devices in an enterprise are critical functions. Solutions such as Mobile Device Managers, Comply to Connect programs, or Trusted Platform Modules (TPM) provide data that can be useful for device confidence assessments, authorization determination, and limiting access. Other assessments should be conducted for every access request (e.g., examinations of compromise state, software versions, protection status, encryption enablement, and proper configuration, etc.). Having the ability to identify, authenticate, inventory, authorize, isolate, secure, remediate, and control all devices is essential in a ZT approach.
Device - Generally speaking, regardless of the type of device it will emit some sort of data and indicators that can be correlated with other systems and validated against ZTN policies. Elastic provides several flexible collection and data processing tools as part of the platform, including a single endpoint Agent that allows not only collection of nearly any system or application data streams from the device, but also the protection of that device from malware, memory, ransomware attacks, and automatically detected behavioral abnormalities (detected via ML algorithms). This signatureless approach lets devices remain protected even in disconnected or intermittent connectivity environments. Compromised endpoints can be isolated from the rest of the network, while still allowing it to be interrogated by the Elastic Security solution (SIEM). One of the many endpoint Agent integrations Elastic provides is OSQuery, which allows direct querying of nearly any device attribute in real-time as well as on a scheduled basis (this integration also works when the device is isolated). Whether the Elastic Agent is the endpoint collection/protection tool or not, all data streams collected across the enterprise can be used to verify ZTN processes are functioning properly and that compliance is being maintained, thus boosting confidence and reducing risk.
Network/Environment - Segment (both logically and physically), isolate, and control the network/environment (on-premises and off-premises) with granular access and policy restrictions. As the perimeter becomes more granular through macro-segmentation, microsegmentation provides greater protections and controls over DAAS. It is critical to control privileged access, manage internal and external data flows, and prevent lateral movement.
Network/Environment - Elastic can unify network traffic activities with user, perimeter, and application logs to validate network segmentation is properly applied and alert on potential violations. The Elastic platform is built to be API-first and easily integrated with other systems, so alerts can do more than notify admins — they can automate actions on other ZTN enforcement tools. Elastic can be the common data layer that enables ZTN and network point solutions to function in an orchestrated way, whether through direct API integrations, or ticketing systems, or SOAR applications.
Applications and Workload - Applications and workloads include tasks on systems or services on-premises, as well as applications or services running in a cloud environment. ZT workloads span the complete application stack from application layer to hypervisor. Securing and properly managing the application layer as well as compute containers and virtual machines is central to ZT adoption. Application delivery methods such as proxy technologies enable additional protections to include ZT decision and enforcement points. Developed Source Code and common libraries are vetted through DevSecOps development practices to secure applications from inception.
Applications and Workload - Elastic provides hundreds of data ingestion integrations that enable automatic collection and indexing of all layers of the operations stack — from the infrastructure, the compute resources, network operations, to the orchestration platforms, service mesh, VMs/containers, and operating systems, to the applications and transactions interacting with those services. Elastic brings it all together into an actionable data speed layer that provides several solutions targeting monitoring, observability, and security use cases, while still also providing ultimate flexibility in how you choose to leverage your data for your mission.
Data - A clear understanding of an organization's DAAS is critical for a successful implementation of a ZT architecture. Organizations need to categorize their DAAS in terms of mission criticality and use this information to develop a comprehensive data management strategy as part of their overall ZT approach. This can be achieved through the ingestion of consistent valid data, categorization of data, developing schemas, and encrypting data at rest and in transit. Solutions such as DRM, DLP, Software Defined Environments, and granular data-tagging support the protecting of critical DAAS.
Data - Elastic can easily integrate with or augment existing data management solutions and approaches such as data normalization, tagging, and categorization, but it can also actually go several steps further to become the single unified data layer that all data operations (including data governance, records management, audit, and compliance) are performed at speed and scale. Elastic can be the common API-driven data service spanning all systems, the speed layer that also acts as a single source of truth. Elastic's built-in data security RBAC and ABAC capabilities control access at multiple layers, and are flexible enough to be easily mapped to your organizational security mechanisms.
Visibility and Analytics - Contextual details provide greater understanding of performance, behavior, and activity baseline across other ZT Pillars. This visibility improves detection of anomalous behavior and provides the ability to make dynamic changes to security policy and real-time access decisions. Additionally, other monitoring systems, such as sensor data in addition to telemetry will be used, will help fill out the picture of what is happening with the environment, and will aid in the triggering of alerts use for response. A ZT enterprise will capture and inspect traffic, looking beyond network telemetry and into the packets themselves to accurately discover traffic on the network and observe threats that are present and orient defenses more intelligently.
Visibility and Analytics - The Elastic search platform not only provides high speed and scale access to all organizational data streams, it also provides a wide array of visualization tools and dashboards. Many of the out-of-the-box data integrations include pre-built visualizations that let analysts understand and explore their data immediately upon ingestion, but these are all fully customizable and flexible enough to adapt to changing analytical needs. Dashboards allow for dynamic analysis of many different data streams at once, with the ability to overlay graphs with annotations, visualize geospatial data in context, or immediately filter or pivot to other dashboards or purpose-built solutions. The real key to these capabilities is the underlying engine that provides a normalized, rationalized, unified high-speed access layer that can support dynamic data interrogation and cross-correlations.
Automation and Orchestration - Automate manual security processes to take policy-based actions across the enterprise with speed and at scale. SOAR improves security and decreases response times. Security orchestration integrates Security Information and Event Management (SIEM) and other automated security tools and assists in managing disparate security systems. Automated security response requires defined processes and consistent security policy enforcement across all environments in a ZT enterprise to provide proactive command and control.
Automation and Orchestration - Simplicity is an underrated factor in the success of large-scale data integration efforts. Elastic provides the unique combination of high-speed and huge-scale data ingestion and management, with state-of-the-art data query, exploration, aggregation, and visualization methods, with an extremely powerful and flexible detection engine, and an alerting framework that can integrate with any other systems. This allows organizations to standardize on a single data platform that functions as a monitoring and investigative tool (for both operations and security/SIEM), and also automate the insights derived either directly to other enterprise tools or through other systems such as ticketing systems or SOARs. Orchestration and automation is only possible when the data engine behind it has the built-in analytical, filtering, query, and integrated security that allows the data feeding the automation to operate on relevant information and reduce noise.
Conclusion
Elastic provides the scalable data platform to bring together all layers of the organization's IT infrastructure and applications, and the speed to help make better business and Zero Trust Networking decisions.
To learn more about how Elastic helps the public sector meet their missions, visit our website.
Read this next: Elastic Security: Guide to high-volume data sources for SIEM
Originally published September 13, 2022; updated February 28, 2023.