Winlogbeat
Lightweight shipper for Windows event logs
Keep a pulse on what's happening across your Windows-based infrastructure. Stream Windows event logs to Elasticsearch and Logstash with Winlogbeat.
Read from any Windows event log channel
There's a lot to learn from your Windows event logs. Interested in security events like logon successes (4624) and failures (4625)? How about when a storage device is attached (4663) or a new service is installed (4798)? Winlogbeat can be configured to read from any event log channel, giving you access to the Windows data you need most.
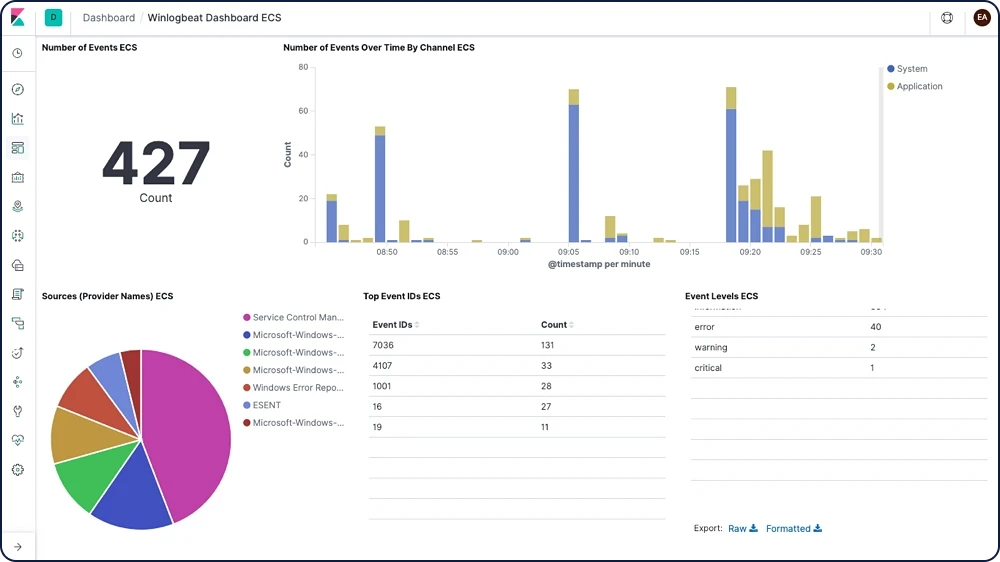
Ship to Elasticsearch or Logstash. Visualize in Kibana.
Winlogbeat supports Elastic Common Schema (ECS) and is part of the Elastic Stack, meaning it works seamlessly with Logstash, Elasticsearch, and Kibana. Whether you want to apply a bit more transformation muscle to Windows event logs with Logstash, fiddle with some analytics in Elasticsearch, or review data in Kibana on a dashboard or in the SIEM app, Winlogbeat makes it easy.
It doesn't miss a beat
Spool your Windows event logs to disk so your pipeline doesn’t skip a data point — even when interruptions such as network issues occur. Winlogbeat holds onto your events and then ships 'em to Elasticsearch or Logstash when things are back online.