Maximizing security insights: A deep dive into the Amazon Security Lake and Elastic Security integration

Elastic is actively working on updating our current integration with Amazon Security Lake to support its newly available adoption of the Open Cybersecurity Schema Framework (OCSF) version 1.1 and version 1.2. Elastic is committed, in close partnership with AWS, to keeping up to date with the OCSF schema as it evolves and ensuring all security data is actionable within Elastic Security through our Amazon Security Lake integration. We’re focused on ensuring that customers utilizing Elastic Security will continue to have industry leading protection for their critical digital infrastructure.
In the ever-evolving landscape of cybersecurity, having a robust and efficient security information and event management (SIEM) system is crucial. One powerful solution that has gained significant traction is the Elastic® integration with Amazon Security Lake. This integration not only facilitates the collection of security-related log and event data, but also empowers organizations to analyze and understand their security posture comprehensively.
In this blog post, we will delve into the intricacies of this integration and explore how it can enhance the protection of workloads, applications, and data across the entire organization.
About Amazon Security Lake
Amazon Security Lake serves as a centralized repository for security-related data, automating the collection process from both AWS services and third-party sources. Amazon Security Lake is not a SIEM tool itself, but it plays a pivotal role in transforming security operations by centralizing logs and finding data in a unified data lake.
This centralized approach yields a comprehensive overview of security data, simplifying the handling of diverse security monitoring use cases and contributing to an enhanced overall security posture. The tool not only streamlines security operations but also normalizes logs, ensuring swift and accurate information feeding to external SIEM solutions like Elastic with minimal operational overhead.
This adoption has resulted in a substantial reduction in the time and effort required by security engineers for collecting findings and logs. Users leverage Security Lake beyond mere storage, employing it to investigate incidents and automate responses across the entire platform.
About Elastic Security
Elastic Security extends the capabilities of Elastic into the realm of cybersecurity, addressing the critical need for threat detection and response. This security-focused iteration incorporates a powerful SIEM system, leveraging machine learning and threat intelligence to fortify an organization's defenses.
By seamlessly integrating with the broader Elastic Stack, Elastic Security not only monitors and analyzes security events but also facilitates a holistic approach to managing and mitigating potential threats.
As organizations grapple with the ever-evolving landscape of cyber risks, Elastic Security emerges as an indispensable tool, empowering them to proactively safeguard their data and infrastructure.
How to implement the Elastic Security and Amazon Security Lake integration
As Elastic and Amazon Security Lake embark on this groundbreaking integration, we're poised to redefine security data management and bolster the capabilities of security teams worldwide. Together, we're propelling security into a new era, where data integration meets actionable insights.
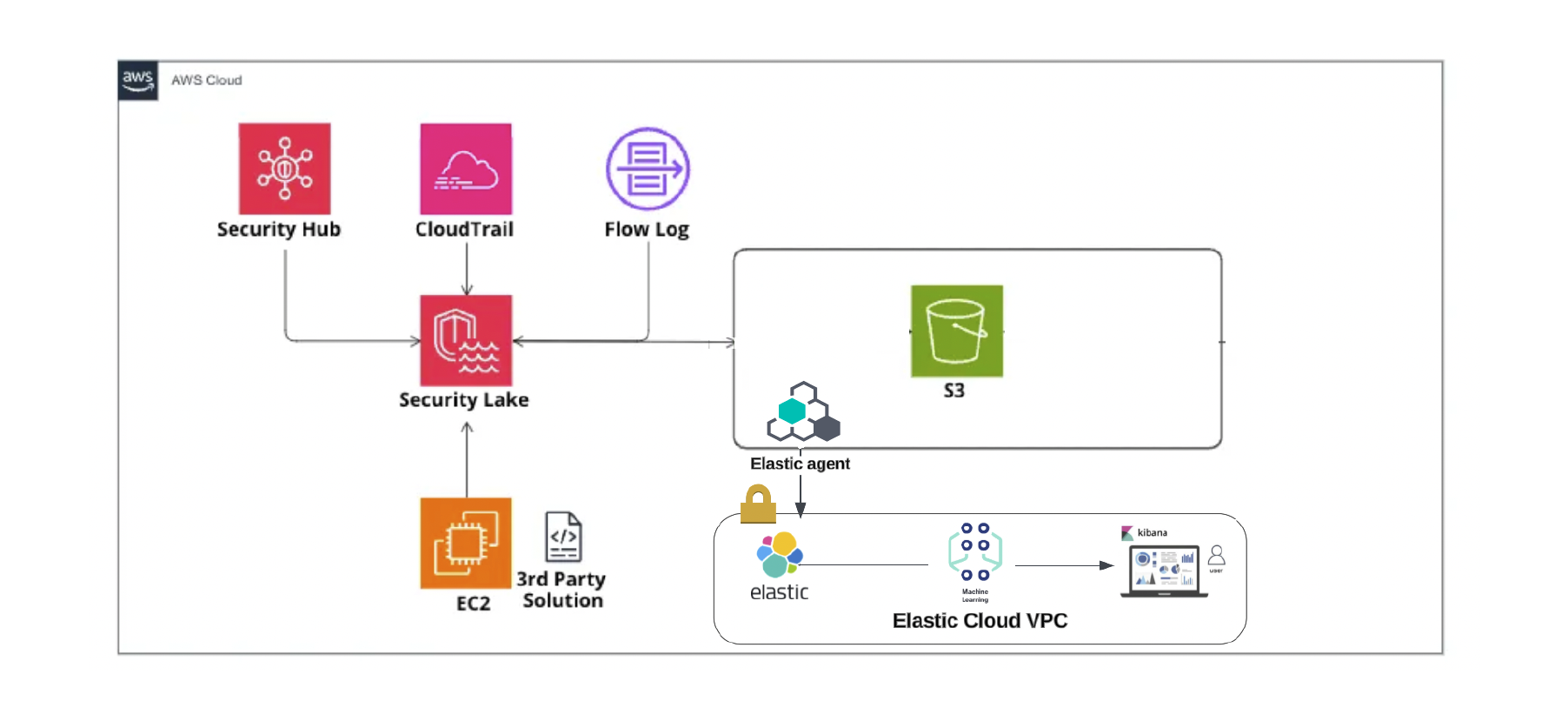
Elastic ensures a seamless transition by converting Open Cybersecurity Schema Framework (OCSF) to the Elastic Common Schema (ECS) format before integrating with Elastic, thus making sure to preserve those default dashboards for a smooth experience.
Steps to integrate Elastic with Amazon Security Lake
Elastic latest Agent must be installed.
Elastic Agent is required to stream data from the Amazon Security Lake subscriber account to ship the data to Elastic, where the events will then be processed via the integration's ingest pipelines.
The correct permissions must be in place to set up an Amazon Security Lake subscriber.
Setup
-
To enable and start Amazon Security Lake, follow the Getting Started instructions.
-
After creating a data lake, follow the steps below to create data subscribers to consume data.
-
Open the Security Lake console.
-
By using the AWS Region selector in the upper-right corner of the page, select the Region where you want to create the subscriber.
-
In the navigation pane, choose Subscribers.
-
On the Subscribers page, choose Create subscriber.
-
For Subscriber details, enter Subscriber name and an optional Description.
-
For Log and event sources, choose which sources the subscriber is authorized to consume.
-
For the Data access method, choose S3 to set up data access for the subscriber.
-
For Subscriber credentials, provide the subscriber's AWS account ID and external ID.
-
For Notification details, select SQS queue.
-
Choose Create.
-
-
The above-mentioned steps will create and provide required details such as IAM roles/AWS role ID, external id, and queue url to configure the AWS Security Lake integration.
Enabling the integration in Elastic
1. In Kibana®, go to Management > Integrations.
2. In the "Search for integrations" search bar, type Amazon Security Lake.
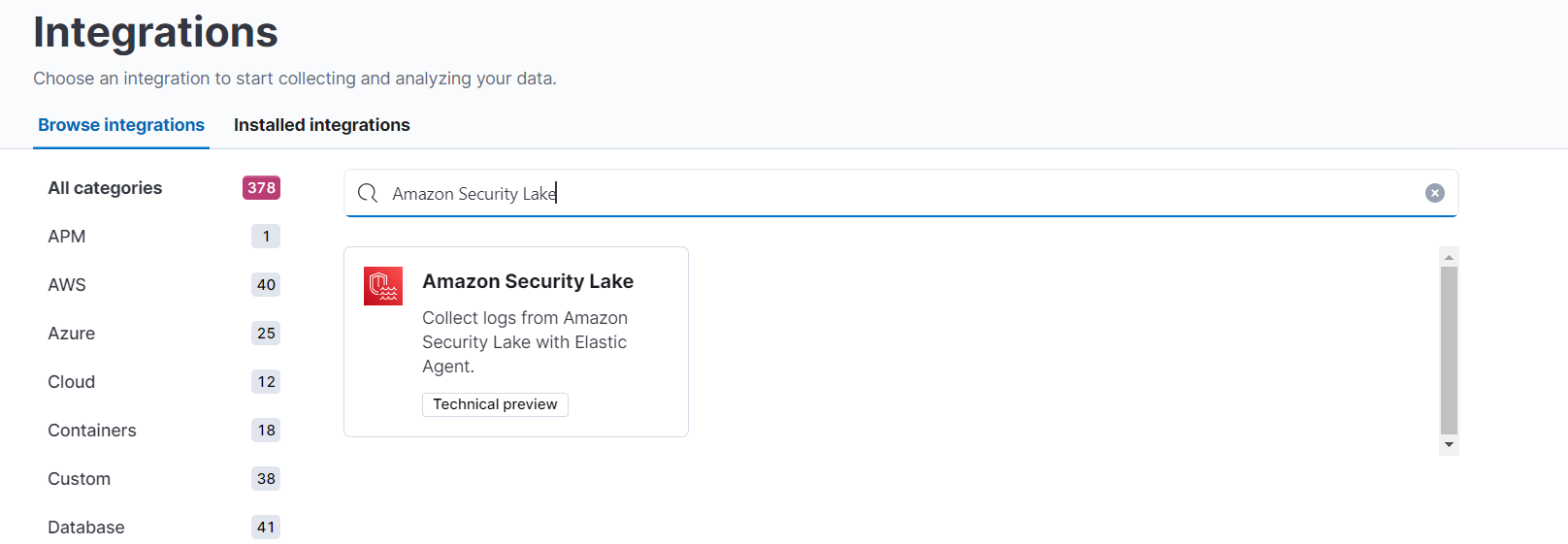
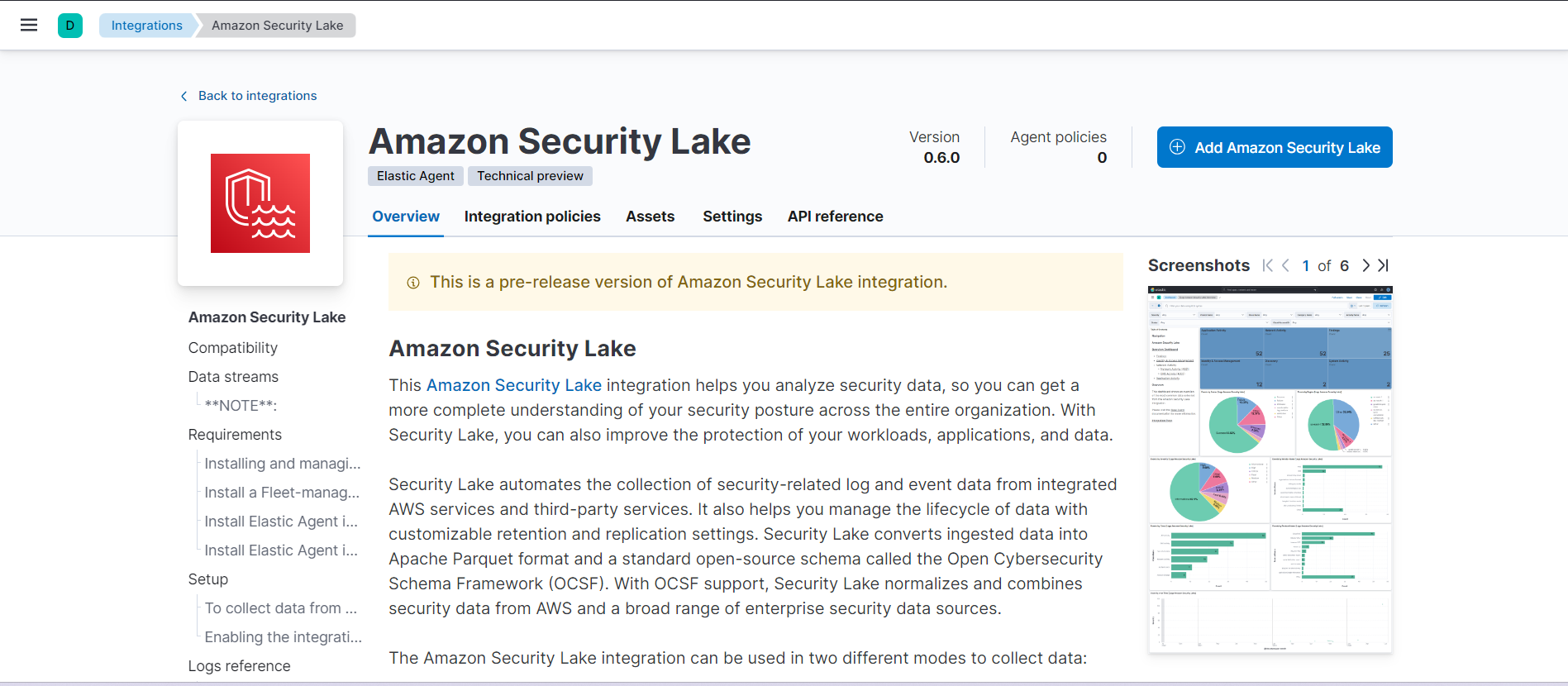
3. Click on the Amazon Security Lake integration from the search results.
4. Click on the Add Amazon Security Lake button to add the integration.
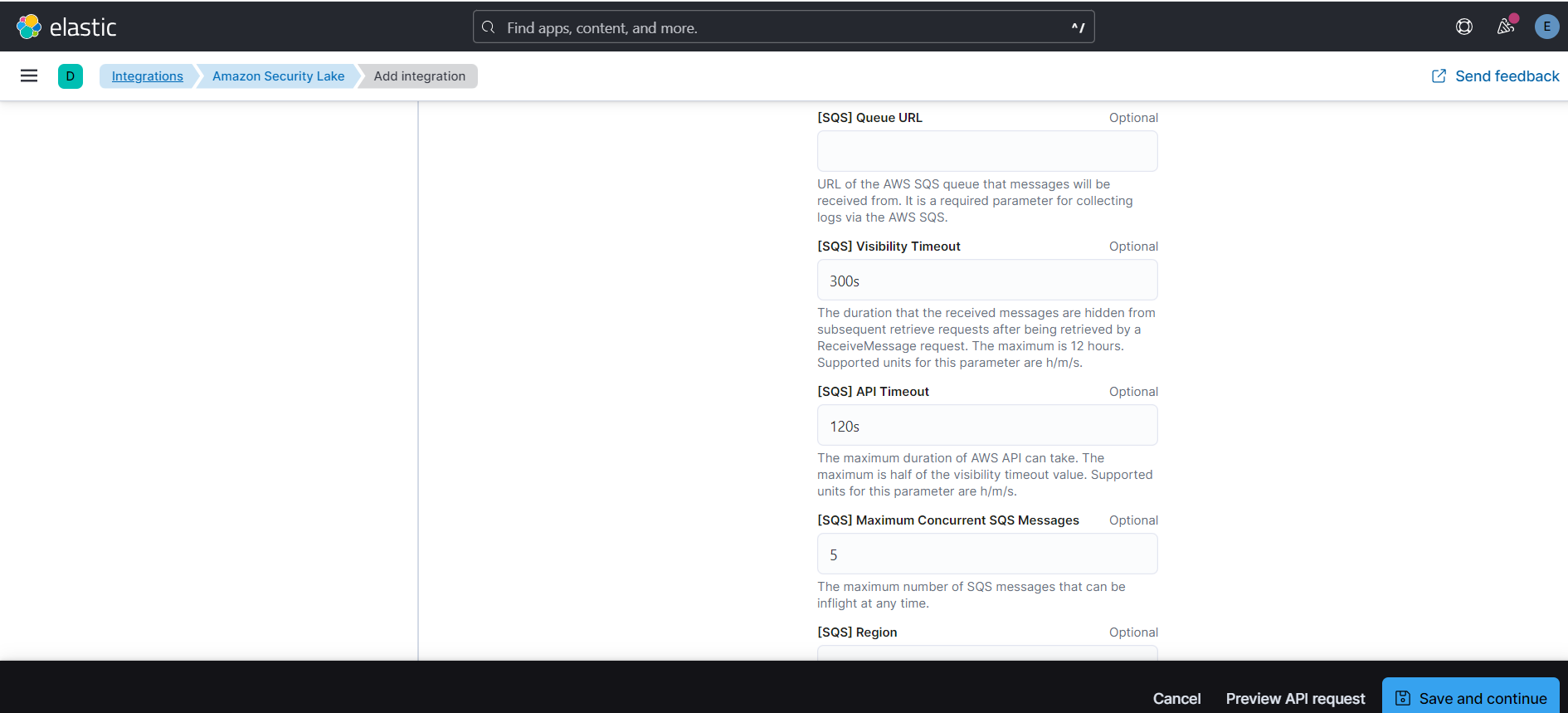
5. By default collect logs via S3 Bucket toggle will be off and collect logs for AWS SQS.
6. While adding the integration, to collect logs via AWS SQS requires the following details:
- queue url
- collect logs via S3 Bucket toggled off
- role ARN
- external id
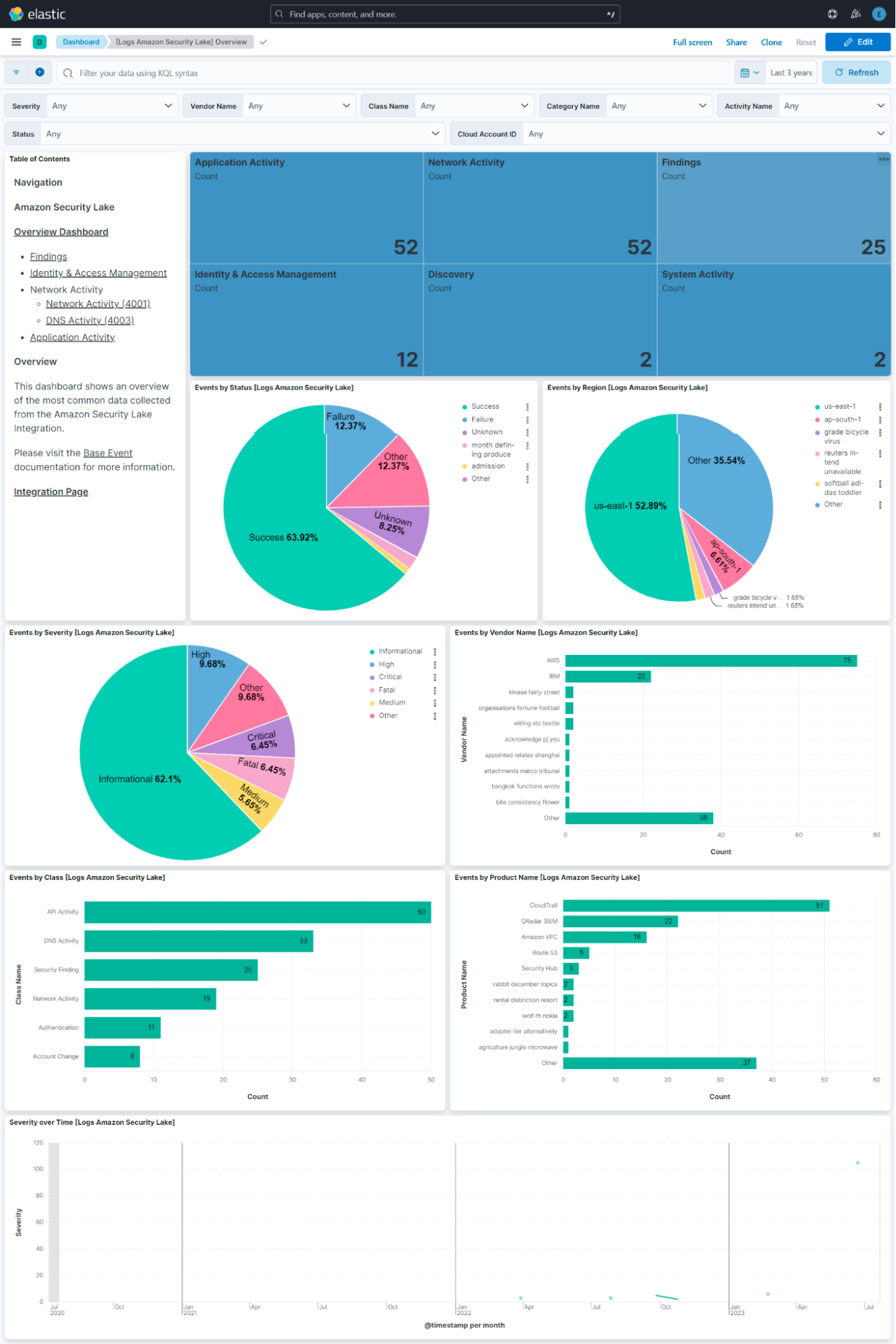
Dashboards
Elastic offers a pre-configured dashboard that displays the status, severity, and classification of Application, Network, System, and Identity & Access Management events. This baseline dashboard can be further enriched by incorporating visualizations from Kibana.
Amazon Security Lake offers a robust solution for consolidating and optimizing logs into a single rollup region while maintaining a standard log format for cost efficient storage. However, it’s important to note that Amazon Security Lake is not a SIEM or endpoint or cloud security service. Instead, it primarily focuses on storing logs in Amazon S3 with some basic analysis capabilities using Athena.
If your organization requires a comprehensive security solution like SIEM, endpoint security, and cloud security features, including advanced capabilities such as Security AI assistants for threat detection and analysis, Elastic Cloud Security has you covered. It’s essential to understand the specific needs of your organization and the capabilities you require to make an informed decision regarding your organization's security.
Start a free trial today
Start your own 7-day free trial by signing up via AWS Marketplace and quickly spin up a deployment in minutes on any of the Elastic Cloud regions on AWS around the world. Your AWS Marketplace purchase of Elastic will be included in your monthly consolidated billing statement and will draw against your committed spend with AWS.