Suchen, analysieren und agieren Sie auf Basis von Log-Analytics
Logs sind überall, zeichnen alles auf und sind die reichhaltigste Quelle für Kontext. Elastic filtert mit agentenbasierter KI die Informationsflut heraus – und wandelt unübersichtliche, unstrukturierte Logs in einsatzfähige Antworten um.
ANGELEITETE DEMO
Von Rohprotokollen zu echten Antworten
Logs informieren Sie darüber, was geschehen ist. Elastic hilft Ihnen, den Grund zu verstehen.
FUNKTIONEN
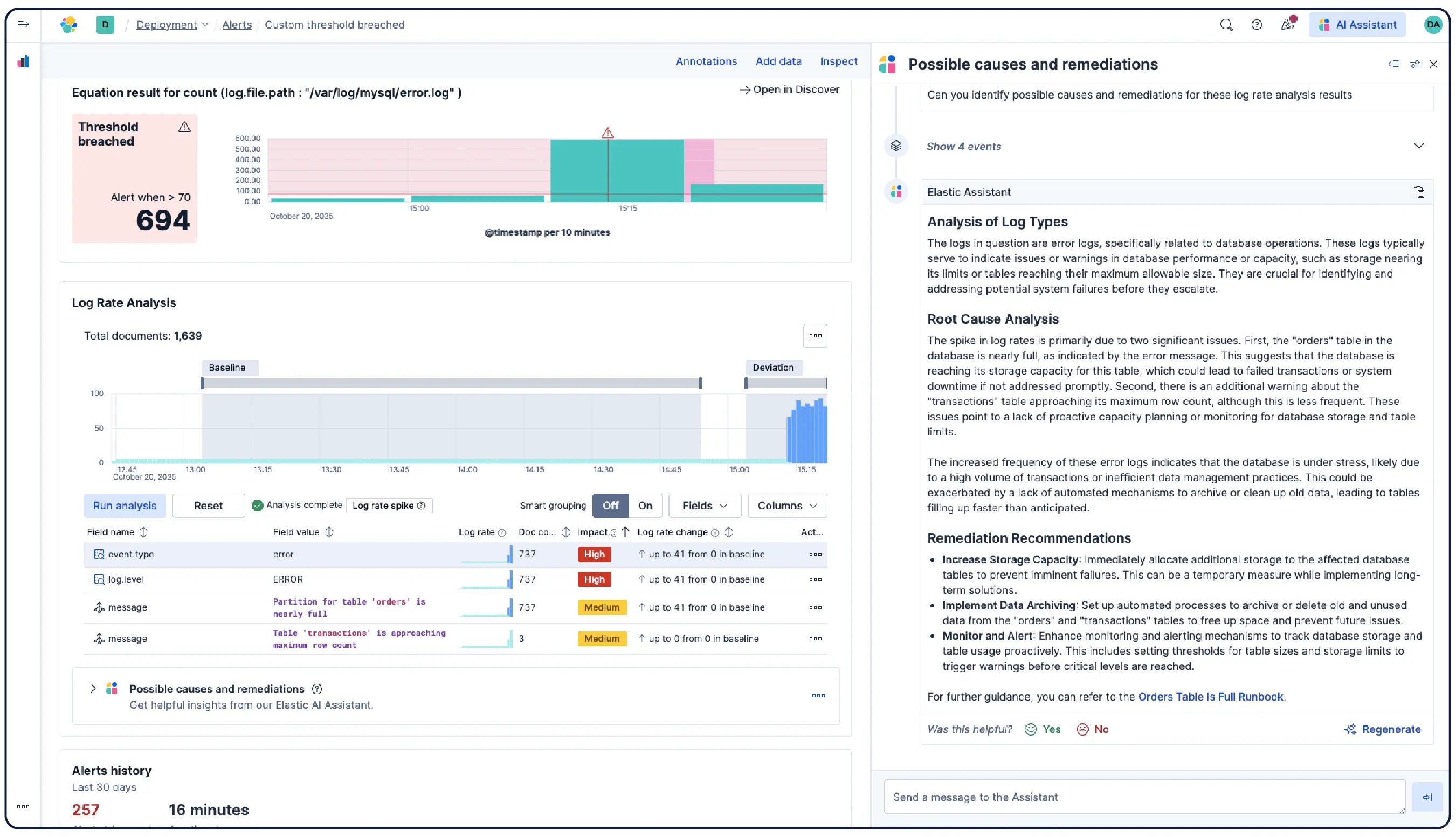
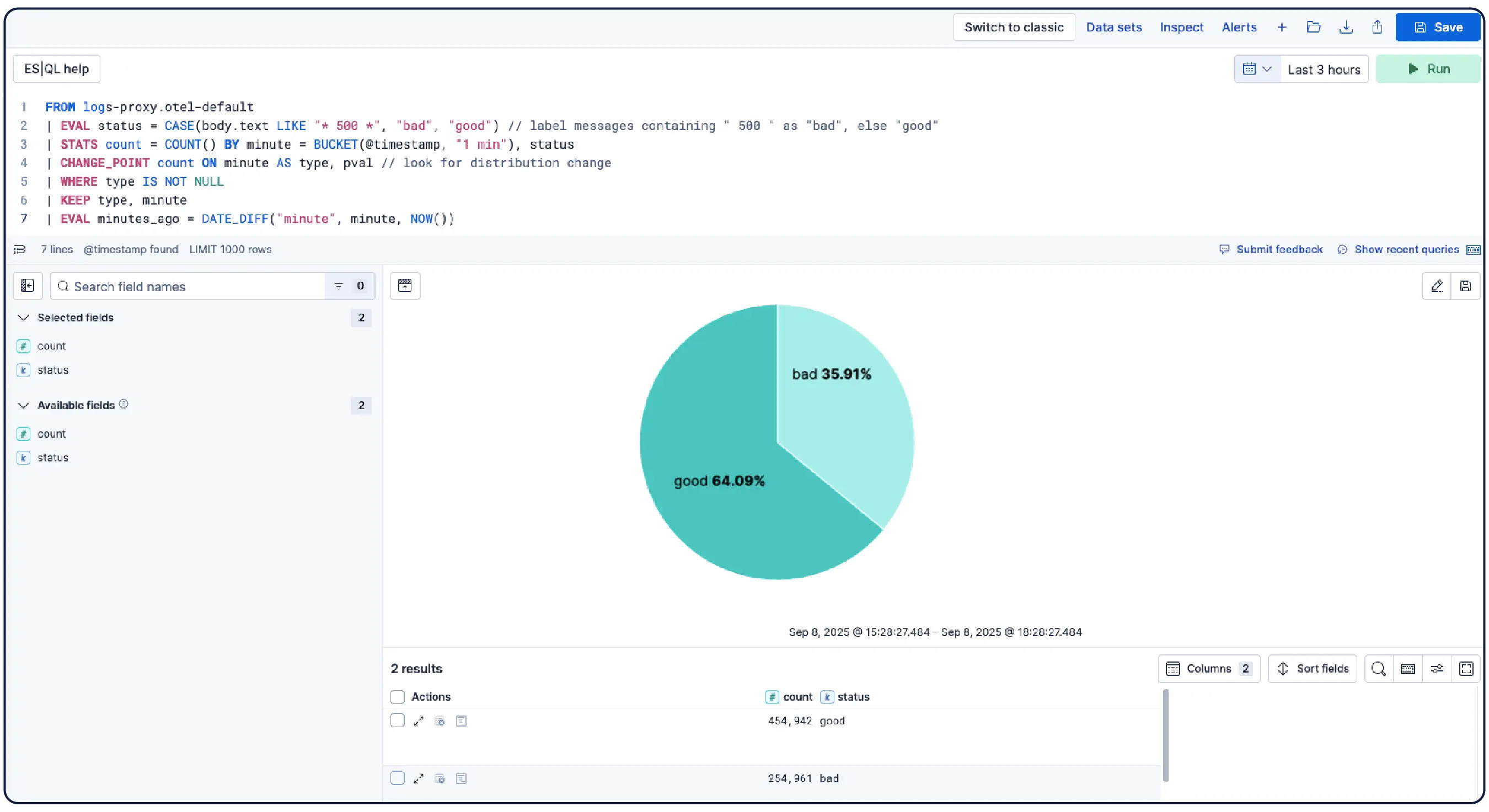
Milliarden von Logs, ein klares Bild
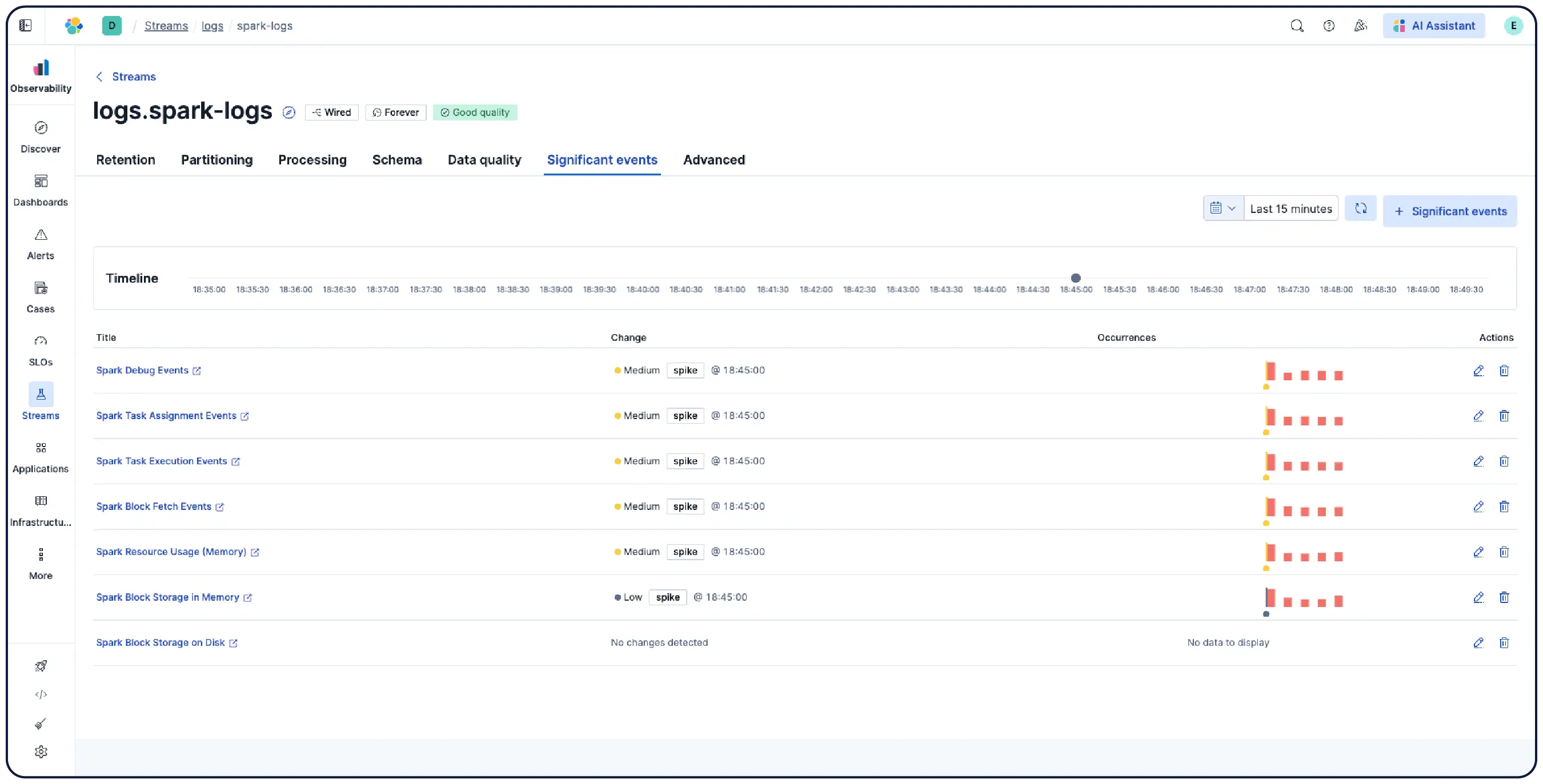
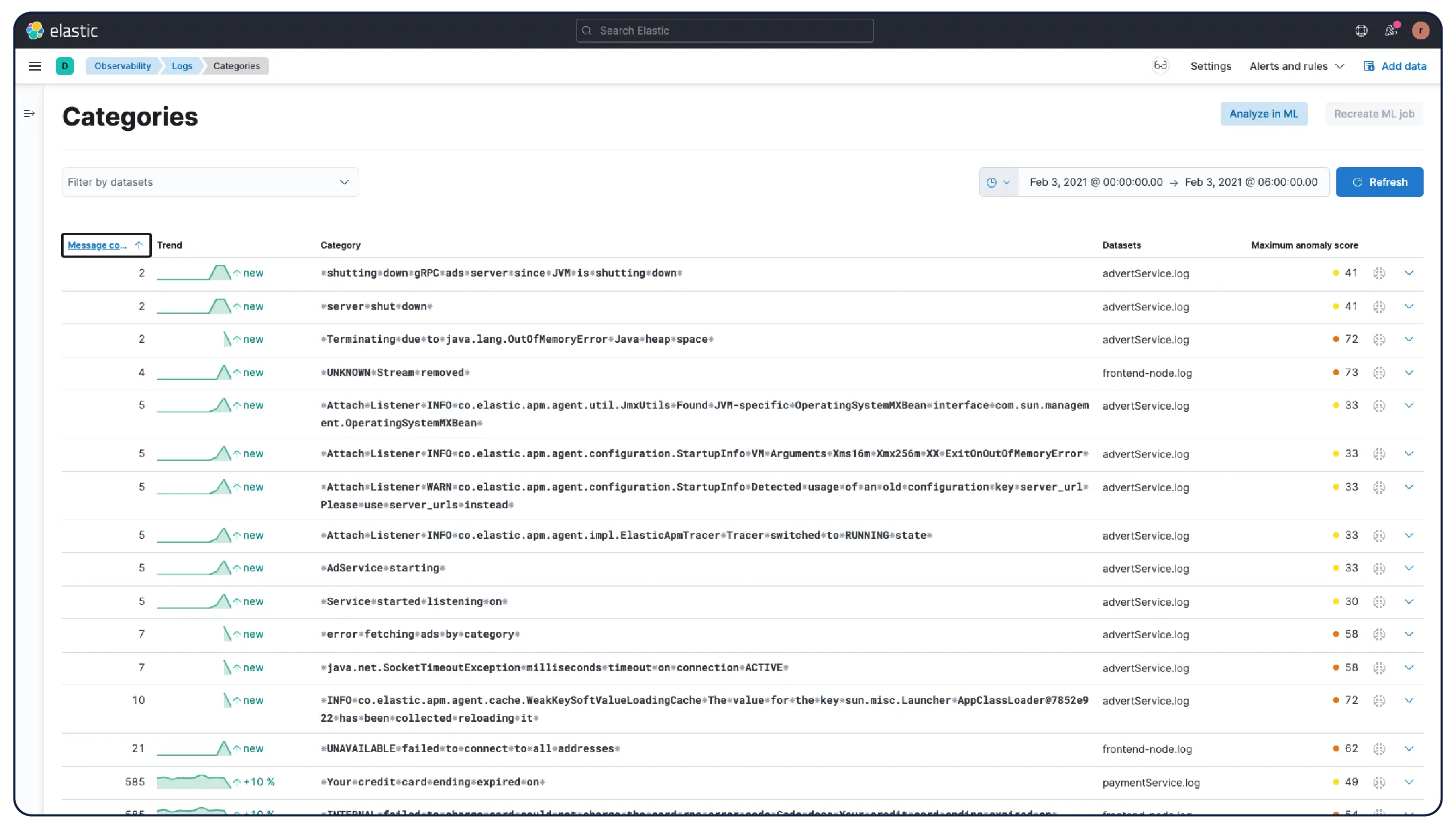
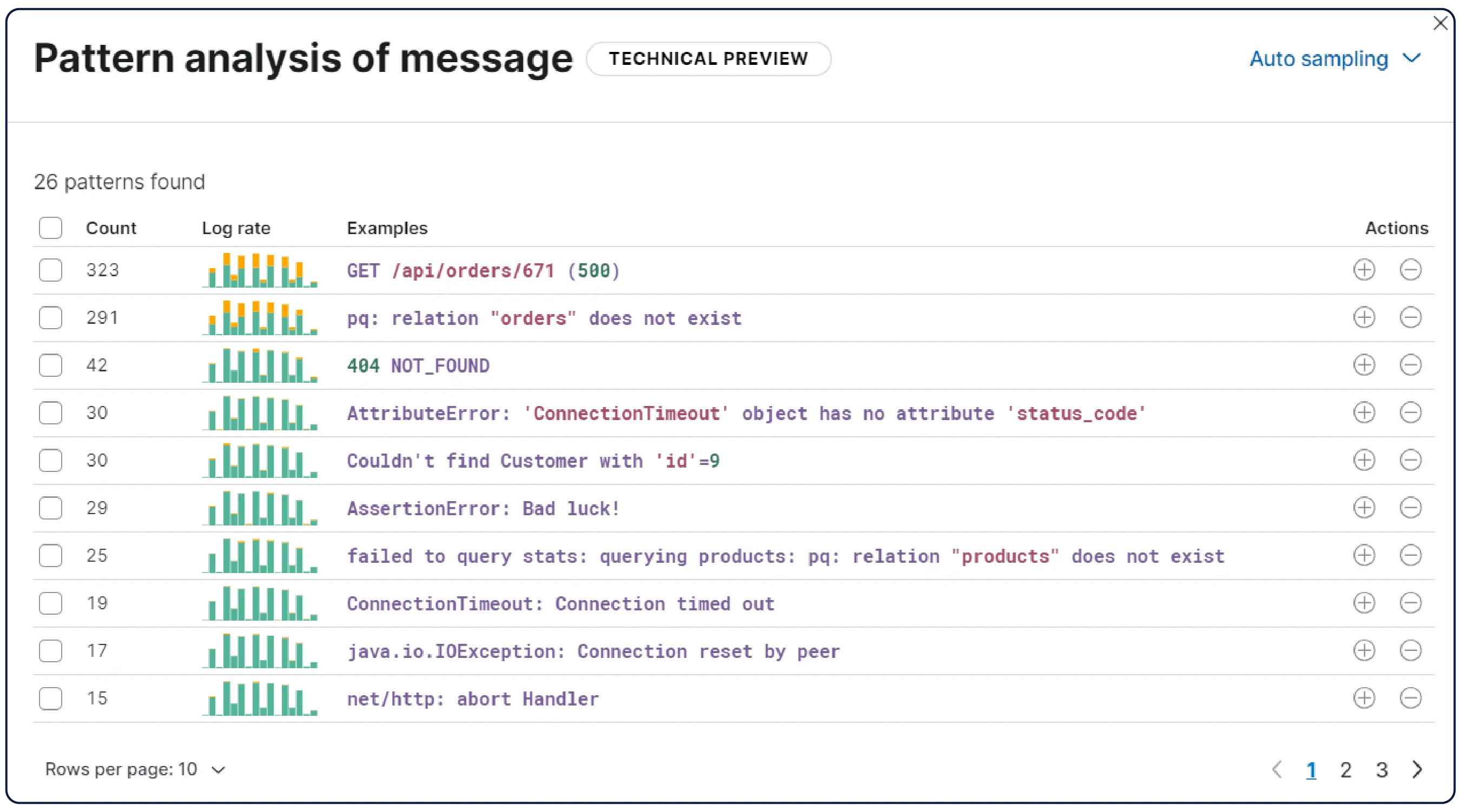
Elastic nimmt Logs von überall her auf und gruppiert sie automatisch zu Mustern, hebt Anomalien hervor und zeigt Spitzen auf – so erhalten Sie Antworten und vermeiden Überlastung.
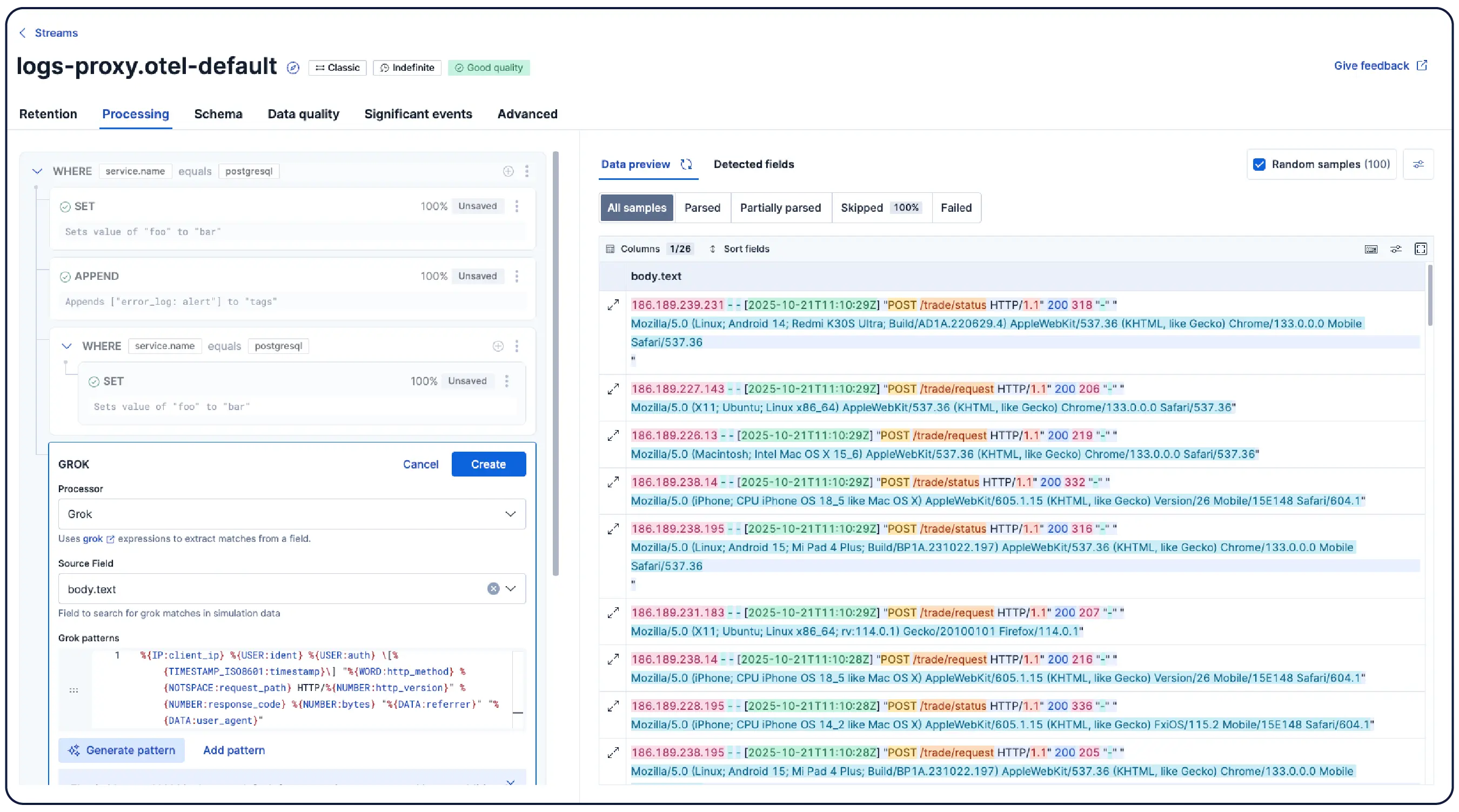
Organisieren Sie Daten automatisch in logische Streams, indem Sie Parsing-, Partitionierungs-, Feldextraktions- und Lebenszyklusrichtlinien mit minimalem manuellem Aufwand anwenden.

Erfahren Sie, warum sich Unternehmen wie Ihres für Elastic Observability entscheiden
Nutzen Sie die Log-Analyse im großen Maßstab, um unübersichtliche Logs in operative Antworten zu verwandeln.
Kunden-Spotlight

Comcast erfasst mit Elastic täglich 400 Terabyte an Daten, um Dienste zu überwachen und die Ursachenanalyse zu beschleunigen und so ein erstklassiges Kundenerlebnis zu gewährleisten.
Kunden-Spotlight

Entdecken Sie, wie die Speicherkosten um 50 % gesenkt und die Datenabrufzeiten verbessert werden konnten, indem eine zentralisierte Logging-Plattform mit Elastic implementiert wurde.
Kunden-Spotlight

Informatica senkte die Kosten und reduzierte die MTTR, indem es seinen gesamten Logging-Aufwand für mehr als 100 Anwendungen und mehr als 300 Kubernetes-Cluster auf Elastic migrierte.
Am Chat teilnehmen
Verbinden Sie sich mit der globalen Community von Elastic und nehmen Sie an offenen Gesprächen und an der Zusammenarbeit teil.
Stellen Sie Fragen, erhalten Sie Antworten und verschaffen Sie sich Gehör in unserem offenen Forum.
Tauchen Sie in Elastic ein. Lernen Sie, erkunden Sie und treten Sie mit Gleichgesinnten in Kontakt.














.jpg)
