Elastic Security 8.9: Streamline the analyst experience with GAI and advanced analytics

Elastic 8.9 introduces the generative AI sidekick, enhanced rule tuning, new lateral detection capabilities, and more! These new features provide security practitioners with advanced detection and analytics, easy to access information, more ways to customize your security investigations, and additional deployment options.
Elastic AI Assistant provides generative AI to the modern SOC
Security professionals have been stretched thin for years, and that’s why Elastic Security has released the Elastic AI Assistant, a generative AI sidekick for the modern SOC. Leaning on large language models (LLMs), the AI Assistant provides a wealth of knowledge on security operations topics and supplies answers to any questions about the Elastic® platform. Analysts can also leverage the AI Assistant for help with basic tasks, such as:
- Alert triage and investigation
- Query generation for specific use cases
- Data ingestion and extraction
- And much more!
Teams can read the initial announcement and watch the included demo for a deeper dive into the base capabilities.
In 8.9, we’ve added several features to the AI Assistant to further improve security and privacy, while enhancing user experience and administration. Users can now select which model to use with the AI Assistant. If they’re using OpenAI, both quick prompts and system prompts are now customizable, with the option to set defaults for both. In addition to those, we’ve implemented changes for both privacy and quality of life.
What else is new in Elastic 8.9? Check out the 8.9 announcement post to learn more >>
Embrace generative AI in your SOC through robust data controls and anonymization
When working with an alert context, you can now selectively decide what data to send and what fields you would like to anonymize. This granular control is an excellent way to ensure you’re not potentially sending extra, unnecessary data to any third parties.
When analysts are working with anonymized entities, they do not have to keep track of the original values. The AI Assistant takes care of the translation of all values to allow for a consistent experience and workflow during alert investigations. Users can also set default behavior for both data selection and anonymization.
Anonymization and field selection for the alert context within the Elastic AI Assistant:

Avoid surprise generative AI bills with token usage tracking
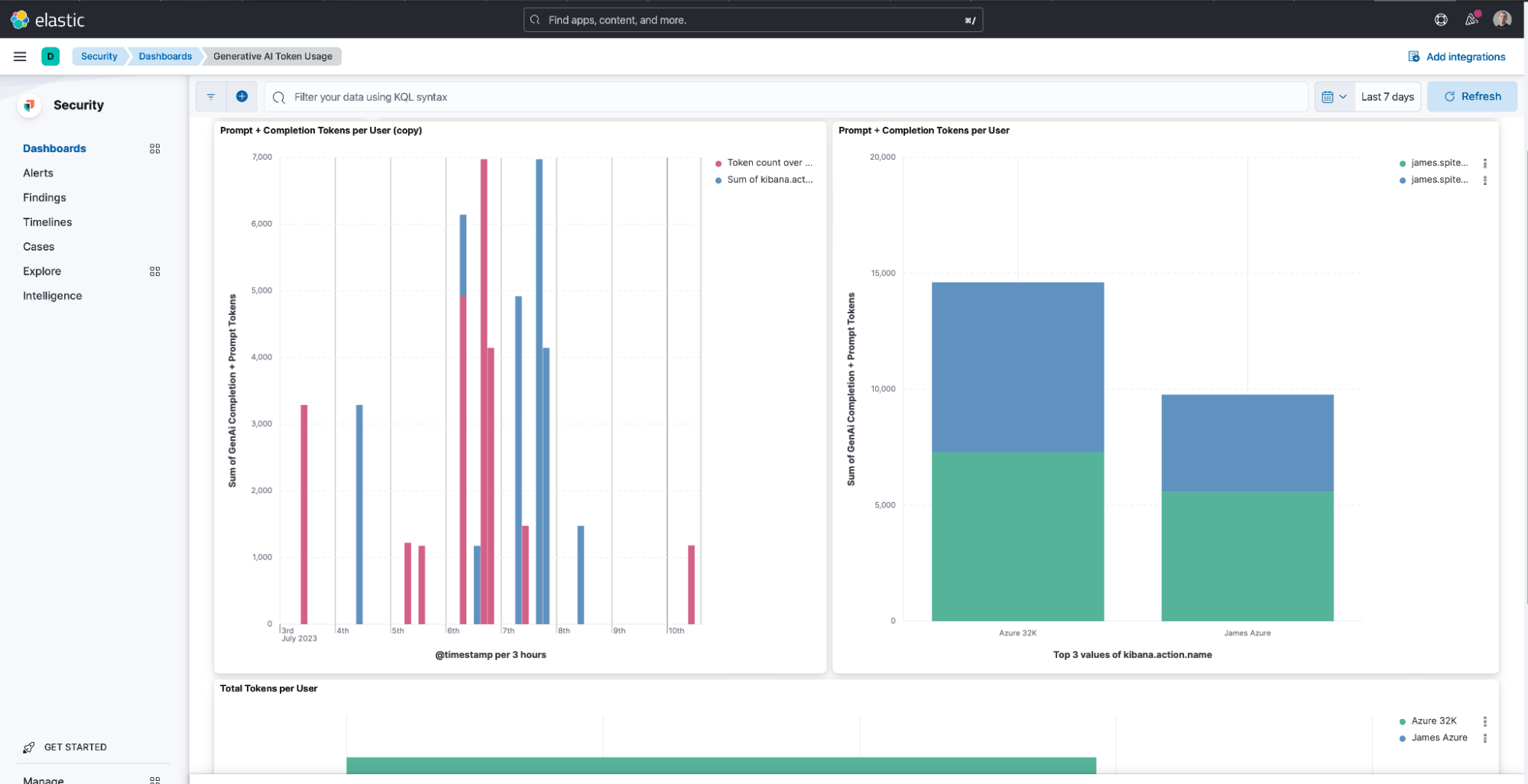
With this release, it’s now even easier to ask the AI Assistant questions. We’ve added a dashboard to track questions asked, also called token usage, per Kibana® user. This visibility allows your team to manage third-party LLM billing based on token count, ensuring there are no surprises when using the power of GAI. This helps you track the upcoming service charges and manage budgets internally.
In addition to token usage per user, the new dashboard also breaks down token usage per connector. This allows you to keep track of usage and any budgets you may have set for these services. The dashboard is also fully customizable for any additional visualizations pertinent to your organization.
These changes to the Elastic AI Assistant will make generative AI even more accessible to every SOC and can help prevent the rise of Shadow AI. The AI Assistant is available to all users — for more information, including how to integrate it with your model of choice, read our documentation.
Manage the effectiveness of your security program with enhanced rule and alert management
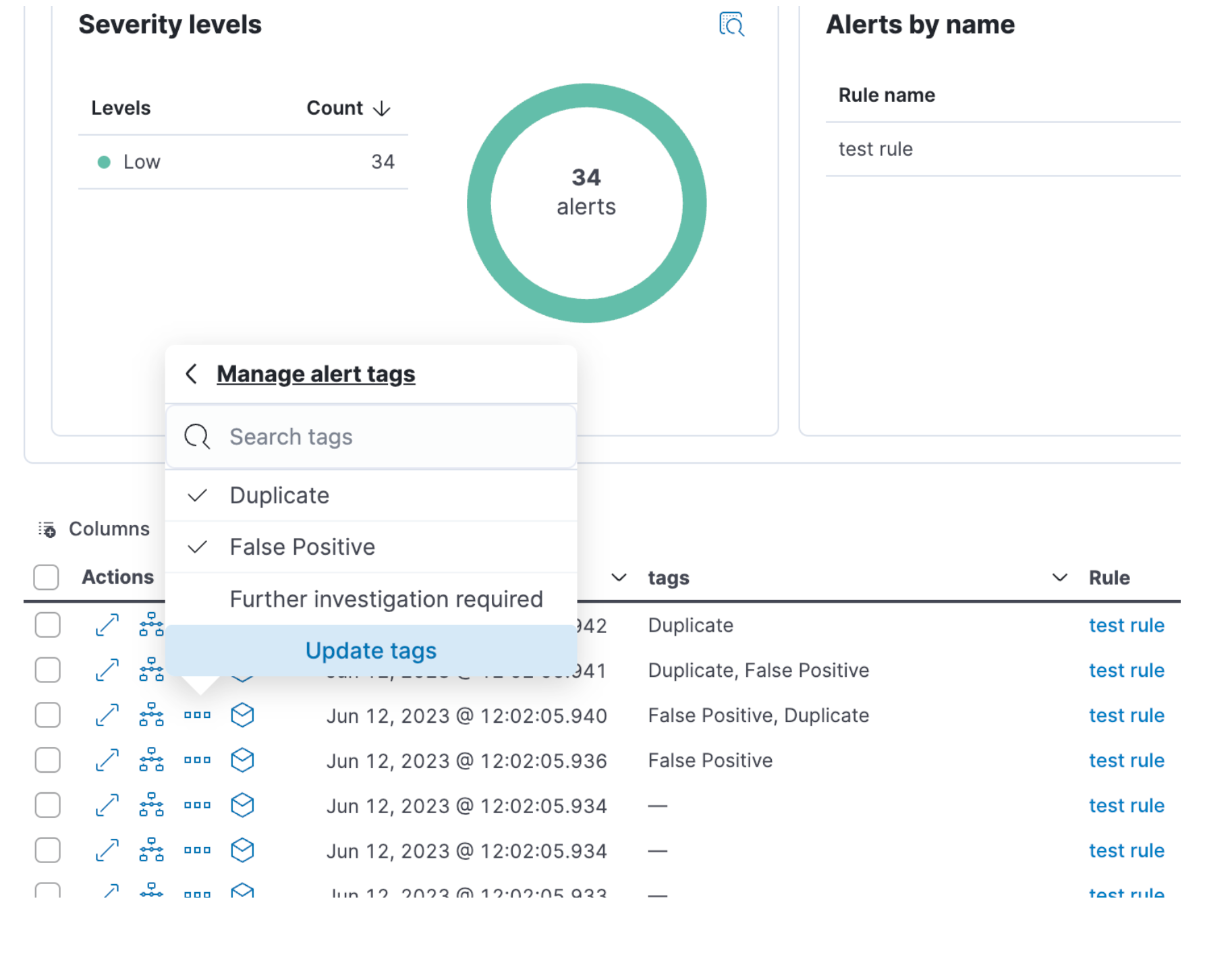
In 8.9, we’ve introduced a number of improvements to help with investigations, namely alert analysis, detections monitoring, and rule tuning. To help analysts reclaim their day, 8.9 brings users the ability to tag alerts to provide additional context such as what further action is required or why the alert was closed. This contributes to a cleaner environment by filtering, automating responses, and grouping and reporting on specific alerts. The default alert tags can be customized via advanced settings to accommodate specific workflows.
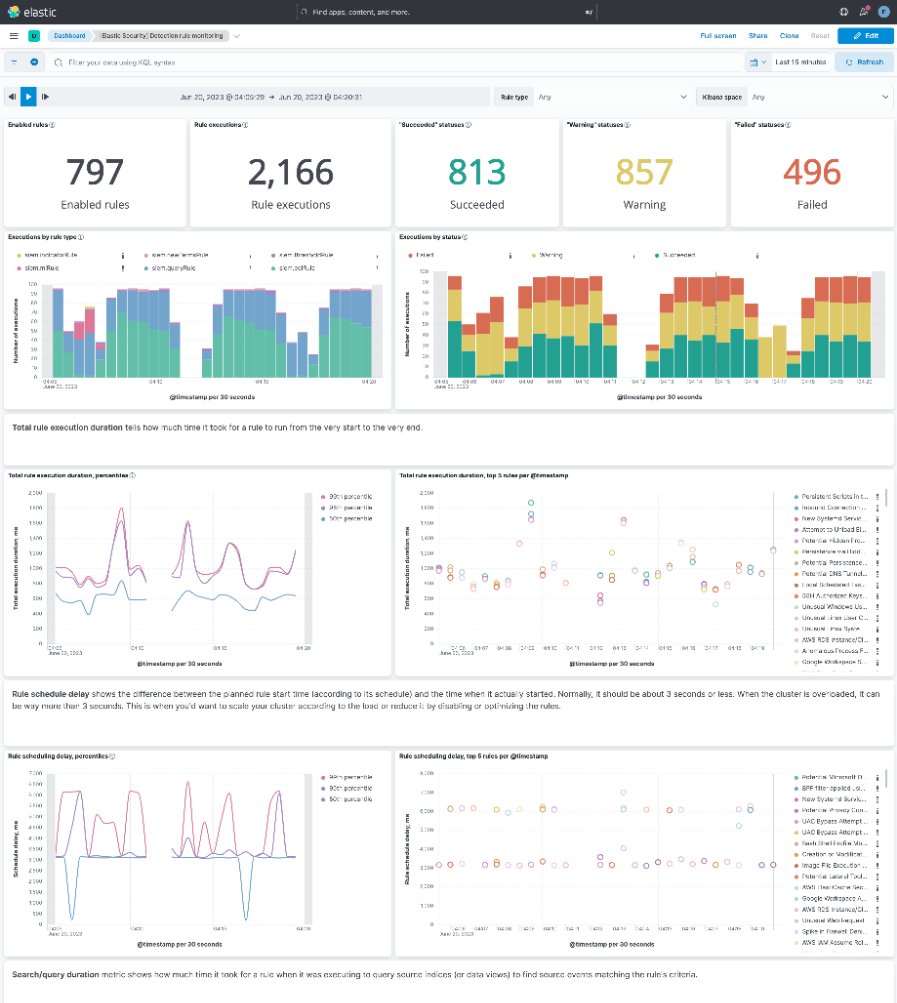
In order to ensure that detection rules are working as expected, we’re introducing a new dashboard for detection rule monitoring. This allows analysts to keep an eye on performance, as well as identify and resolve issues pertaining to any rules in their environment. This includes a variety of charts with metrics like:
- How many rules in a status
- Execution duration and delay over time
- The 10 rules that have been running the longest
- The 10 rules with the highest delays
- The 10 rules that have acquired the most “failed” statuses
These metrics can be aggregated both per space, for all spaces, and per rule, or for all rules.
Alert tuning and rule performance are just a few capabilities in this release committed to keeping an analyst sane. Also in this release, we’ve included more ways to identify threat actors.
Detect lateral movement more effectively
Attackers use sophisticated software and tools to move under the security radar, and it can be very difficult for SOCs to detect malicious lateral movement with traditional detection rules. While we released the initial Lateral Movement package in February 2023, Elastic Security has been busy identifying more ways to detect these threats within an environment.
With the 8.9 release, our Lateral Movement Detection package has been made generally available. In addition to identifying network and file based threats, the package detects malicious activities in Windows RDP events using prebuilt ML jobs and specific detection rules.
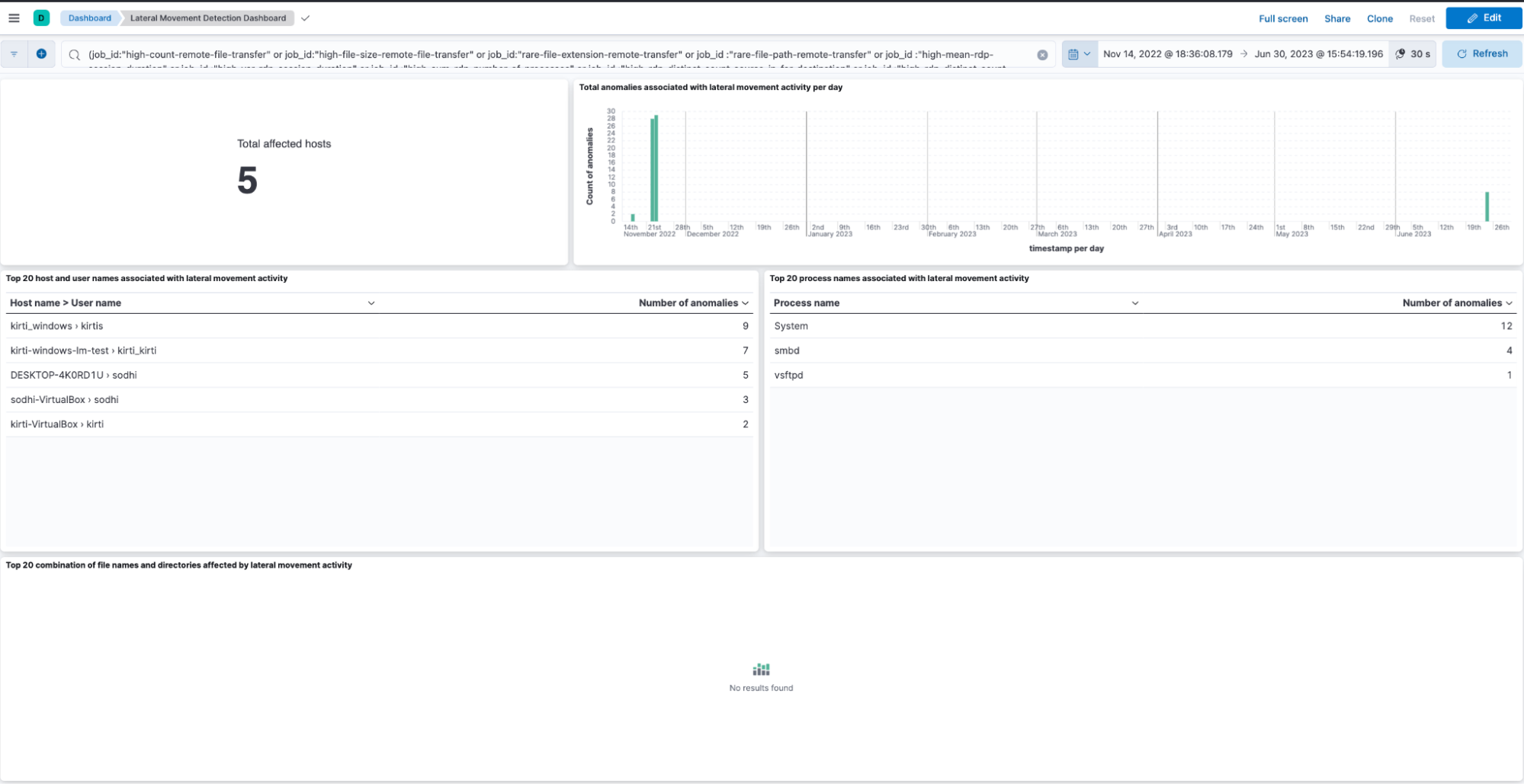
This advanced package uses machine learning for anomaly detection to create a baseline for expected network behavior. We then apply a combination of detection jobs and rules to increase the detection's efficacy. Get more details about this package.
Elastic Agent now drives endpoint orchestration with upload response action
Elastic Security 8.9 continues to expand our native response action capabilities with the addition of the upload response action. The upload action enables security analysts and administrators to upload files to their hosts through our centralized response console, without requiring that analysts have physical access to the host. This capability vastly streamlines workflows for running scripts on remote hosts, giving analysts the necessary tools to run scripts tailored to their organization's specific security needs and expedite tasks related to investigation, remediation, and orchestration. For example, a script could be designed to collect relevant system logs, scan for specific indicators of compromise (IOCs), or extract forensic information from the endpoint for further analysis, like memory and network dumps.

This capability is generally available in 8.9 for every OS protected by an Elastic Agent and is accessible via the Elastic Security Enterprise subscription tier for both self-managed and cloud deployments. Learn more about response actions.
Easily deploy CSPM using AWS CloudFormation
Deploying the Elastic Security Cloud Security Posture Management (CSPM) feature in AWS has become even simpler with the power of AWS CloudFormation. This deployment method brings a host of benefits that not only enhance security but also streamline the entire process. Here's why you should take advantage of it:
- Accurate resource configuration: Say goodbye to manual setup and potential errors. CloudFormation ensures that all the necessary resources for CSPMs are set up correctly and with the right minimal permissions, thereby drastically reducing the potential for errors.
- Saving time and effort: No more wasting precious time on manual resource creation and agent deployment. CloudFormation's auto-provisioning capabilities take care of everything for you. This means you can redirect your valuable time and effort toward other critical tasks that demand your attention.
- Consistency and repeatability: With CloudFormation, deployments can be easily reproduced and consistently maintained across different environments. This ensures a standardized and reliable CSPM setup, regardless of the deployment location.

This deployment option is generally available in the 8.9 release for Elastic Security. By leveraging AWS CloudFormation to deploy CSPM, organizations can enjoy improved security, streamlined deployment process, and significant time savings. Learn more about deploying CSPM using AWS CloudFormation in our step-by-step getting started guide for CSPM.
Try it out
Read about these capabilities and more in the release notes.
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. Not taking advantage of Elastic on cloud? Start a free trial.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.