New on Elastic Cloud: AWS PrivateLink and IP filtering
Today we are pleased to announce new traffic management features for Elastic Cloud. Now you can configure IP filtering within your Elastic Cloud deployment on Amazon Web Services (AWS), Google Cloud, and Microsoft Azure. We are also announcing integration with AWS PrivateLink. These features help give you greater control over the network security layer of your Elastic workloads.
Learn more about these improvements — and watch a live demo of these features in action — in our on-demand webinar.
Control network access to your deployments
IP filtering enables you to specify network access to your Elastic Cloud deployment based on singular IP addresses, as well as IP address blocks or ranges. AWS PrivateLink provides private connectivity between your virtual private clouds (VPCs), AWS resources, and on-premises applications. This gives you the ability to secure the network connection between your applications and your Elastic Cloud deployment.
A well-thought-out security policy includes provisions for the principle of least privilege, as well as the application of security in layers. While this is only a small part of developing a strong security posture, the idea is to limit application, data, and systems access to users and systems with a legitimate business need. We also recognize that no security tool is a complete solution for protecting against threats, so we must layer our security controls. IP filtering takes both of these concepts to heart.
To add another layer of security to your installation and deployments, you can restrict inbound IP address traffic to trusted sources. For instance, you might want to restrict access to the deployment strictly to the range of IPs associated with the VPC in which the production version is deployed to while opening up the deployment the dev version is deployed to more widely to developers.
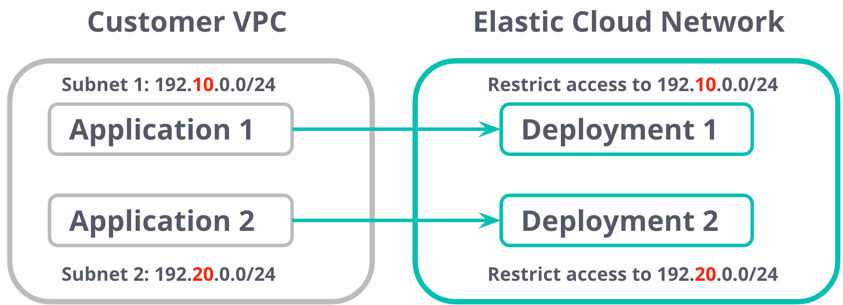
Use PrivateLink to secure access to your deployments
A common security architecture involves ensuring your databases and data stores only expose private IP addresses to your public-facing applications. This is preferable if you are storing personally identifiable information (PII) or sensitive data in your data stores.
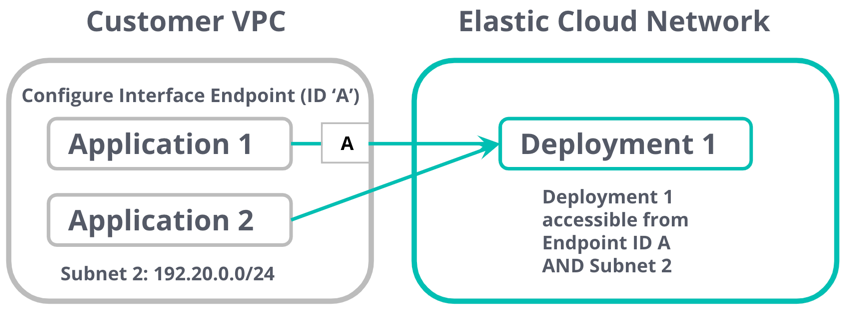
PrivateLink is rapidly gaining traction as the preferred way for providing secure connectivity. It connects the VPC that your application (service consumer) is deployed on, with the VPC that your Elasticsearch deployment (service provider) resides on.
Accessing services over PrivateLink offers many advantages including secure communication using a private IP and simplified network management. Unlike VPC peering and internet gateway-based solutions, PrivateLink is unidirectional, meaning it only allows traffic from the consumer VPC to the endpoint.
You can further decide to choose which of your VPCs and subnets can have access to the PrivateLink endpoint. This effectively allows the service endpoints to function like they are hosted directly on your private network while only allowing traffic in one direction (from your VPC to ours).
Using traffic management features in Elastic Cloud
Create a traffic filter
You can choose between creating a PrivateLink connection to peer your VPC to ours, or you can create an IP filtering ruleset to restrict the set of IPs that have access to your deployment.
Create a PrivateLink endpoint
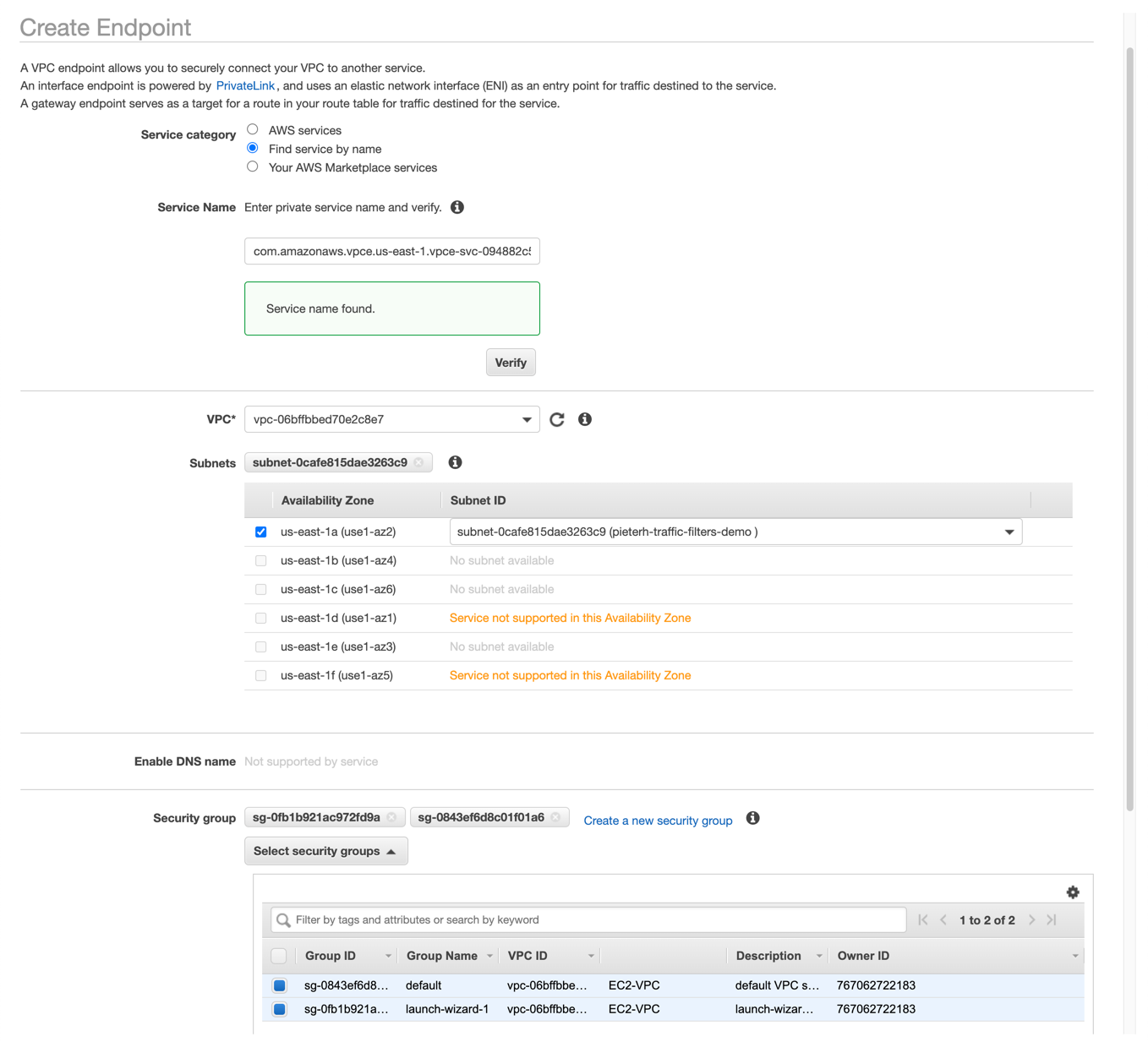
Configure a VPC endpoint on AWS
- Log in to your AWS account and create an interface VPC endpoint. Refer to the traffic filtering docs to configure the service name for the region where you are creating the interface endpoint. In the us-east-1 region, for example, the service name would be
com.amazonaws.vpce.us-east-1.vpce-svc-0e42e1e06ed010238. Assign the security groups that should have access to the endpoint. When complete, you will get an interface VPC Endpoint ID, which you will need later. - Configure a DNS CNAME alias that points to the domain name of the endpoint interface you just created.
Configure a traffic filter: PrivateLink endpoint on Elastic Cloud
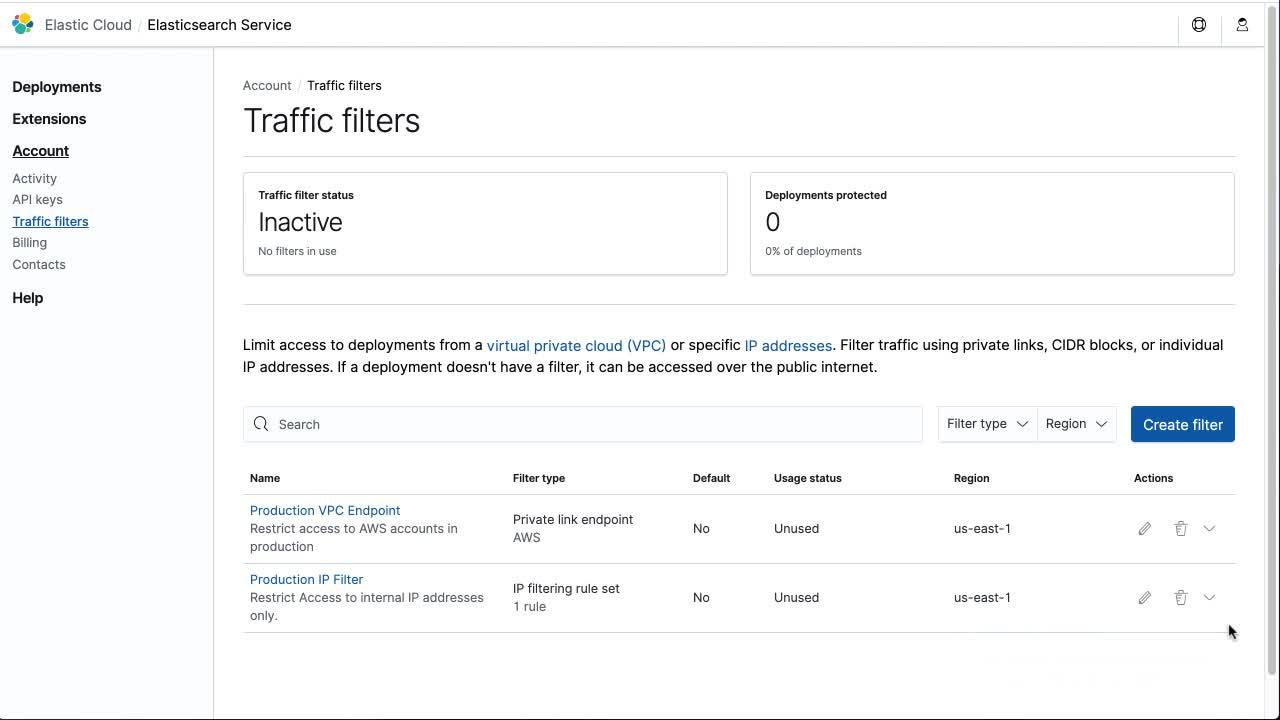
- In the Elastic Cloud console, navigate to Account > Traffic filters and click on Create filter.
- Select PrivateLink. You can give your filter a human-friendly name and description. Consider including your VPC’s region in this name. The Endpoint ID is the interface VPC Endpoint ID you saved in the previous step.
Create an IP filtering ruleset
- In the Elastic Cloud console, navigate to Account > Traffic filters and click on Create filter. Select IP filtering rule set.
- You can give your traffic filter a human-friendly name and description. You can add one or more rules to accommodate multiple CIDR ranges or individual IP addresses.
Once you create traffic filters, you can activate them by associating them with one or more deployments.
Associate a traffic filter with a deployment
Once you have created the filter, you can associate it with a deployment either when creating the deployment or by editing an existing deployment. A traffic filter can be associated with more than one deployment. A deployment can also be associated with more than one traffic filter. You can see a summary of the deployments and associated traffic filter rules from your account dashboard.
See the filter in action
Depending on the filtering rules you configured, your deployments will only be accessible via the PrivateLink endpoint and/or through the list of IPs that have been explicitly configured. To test connectivity from the applications deployed in your VPC, you can attempt to connect to them from destinations that are not configured to have access.
Getting started
Log in or sign up for a free 14-day trial and get started with IP filtering and AWS PrivateLink integration. These features are available for all Elastic Cloud customers across Standard, Gold, Platinum, and Enterprise tiers at no additional charge above the standard cloud provider pricing. You can visit our product documentation to learn more.