How Orange Business Services is building a better SIEM with Elastic
I’m a security analyst at Orange Business Services in Paris, and one of my current projects for the Orange Group is implementing a new SIEM based on the Elastic Stack. In this blog post, I’ll share why we chose Elastic and how we were able to integrate Elastic into our existing SIEM, resulting in faster investigations and saving our engineers’ time.
So follow along:
Orange Group is a multi-service network operator and digital service provider in 26 countries and serves about 253 million customers with 147,000 employees. Orange Business Services, the unit dedicated to businesses and organizations, focuses on digital services. From connectivity, the Internet of Things (IoT), and the cloud to artificial intelligence (AI), application development, and cybersecurity, Orange Business Services works with its clients to harness the true value of their data, helping them every step of the way.
Integrating the Elastic Stack into our SIEM strategy
The Orange International Network Infrastructure (OINIS) department, which is in charge of building the Orange group’s international network, identified the need for a modern security monitoring solution capable of keeping up with the constant changes in the fast-paced world of security. As a result, two of our departments recently decided to collaborate on redesigning and modernizing the Orange Business Services SIEM infrastructure, which has been dubbed “EYES.” The key criteria for selecting our new solution were speed, simplicity of data integration, and better visualization tools.
Elastic had piqued our interest as early as 2018. We were finally convinced to take the plunge with Elastic after the ElasticON Tour Toronto and hearing the feedback from the security team at Bell Canada (before Elastic introduced its own turnkey SIEM solution, which we will be rolling out soon). Finding themselves in a similar situation to our own, the team at Bell Canada had quickly taken the initiative of completely replacing their SIEM with the Elastic Stack, which was capable of ingesting all of their security logs, automatically detecting threats, and standardizing the format of their logs. We were also interested in Elastic’s machine learning features, which promised to help us modernize our SIEM approach.
We decided to implement the Elastic Stack for a functional proof of concept (POC) in less than three months. However, we took a slightly different approach than Bell Canada, in that our SIEM solution is still being used for its correlation engine. Following our three-month-long POC, we copied all our logs into the new infrastructure and enabled the Elastic Stack’s security features to protect access to our clusters. We started by learning to use the Elastic Stack ourselves; we were able to find all the necessary information to get started on the Elastic blog. Later on, we started working closely with the teams at Elastic in order to roll out new features. Elastic’s Support team has always proven to be very responsive, whether we came to them with application debugging questions or requests for advice on integration, or even our security architecture.
Our infrastructure evolved very quickly as a result:
- We separated the Dev, Preprod, and Prod environments, allowing us to quickly test the new features offered by Elastic and determine whether we wanted to go into production with them.
- Logstash also quickly went from a simple parsing tool to an essential tool for enriching our logs.
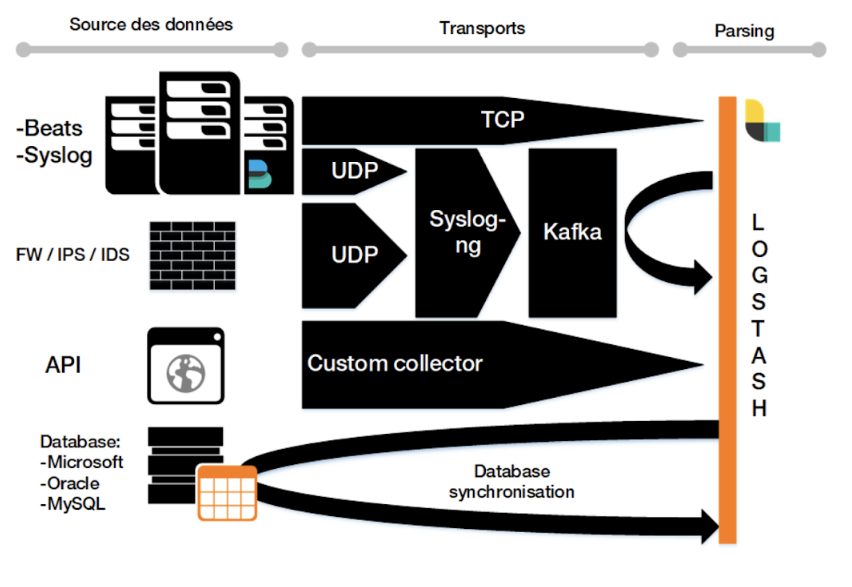
Architecture diagram - We also applied the hot/warm/cold formats for managing the lifecycle of our indices, allowing us to improve both performance and security.
- Finally, we added a monitoring cluster to collect the metrics for the various components of our systems and keep a close eye on the performance of our clusters.
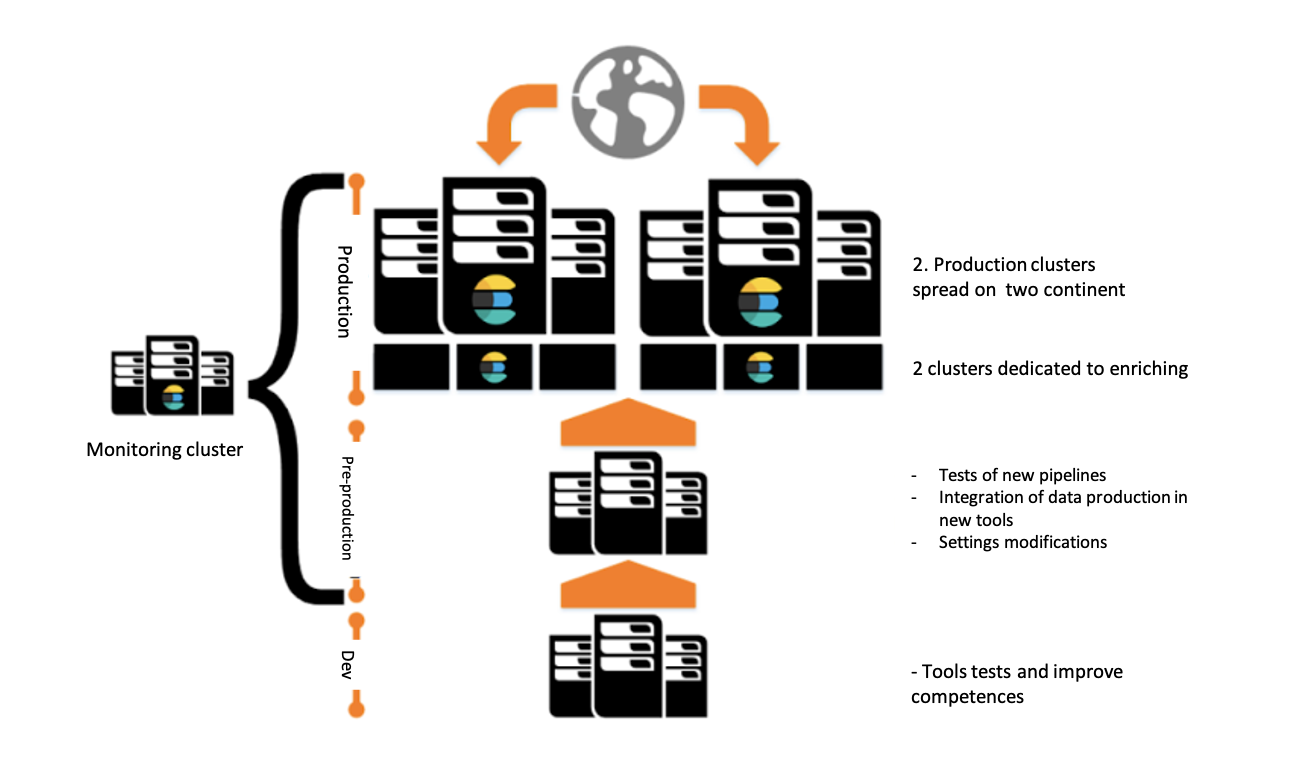
In these architectures, we use the products in the Elastic Stack (Elasticsearch, Logstash, Kibana) and have implemented Beats for a handful of very specific needs (application logs, NetFlow) that have not yet been standardized. We now have around 20 Elasticsearch nodes spread across two geographic sites. With all components included, this makes for a total of 80 servers, nearly 100 billion logs indexed, and several dozen terabytes of data.
A comprehensive overview of the speed and performance of Elastic Stack
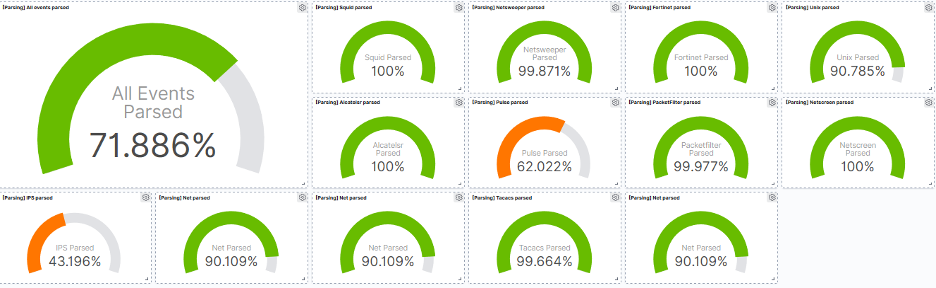
Following the integration of the Elastic Stack, we quickly saw an improvement in our SOC investigation abilities. Thanks to our new infrastructure, we can retrieve the results of our investigations much more quickly, and also benefit from all of the data regarding the security of our information systems (inventories, network mapping, management of computer equipment, alerts for external equipment, etc.) being centralized. This in turn gives us a greater degree of control over the ingestion of our logs, and we have implemented a dashboard that allows us to view the quality of our various pipelines so our SIEM engineers no longer have to waste time investigating whether a log format has been modified following the introduction of a new application or version.
We are now capable of detecting network anomalies more quickly and no longer have to query multiple databases to obtain a single piece of information. Since Orange Business Services has over 1,000 pieces of internal network equipment (LAN), the enrichment of the information taken from IPAM (IP address management) allows us to plot all of our equipment on a map and track the communications that have occurred.
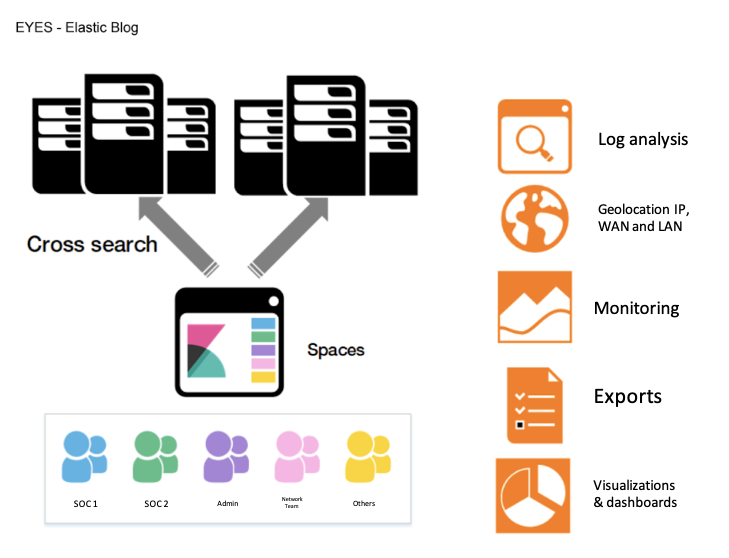
Adopting the Elastic Stack also proved to be quick, as our users make use of Kibana on a daily basis to view their data, and Spaces also allows us to take that one step further by separating out the various workspaces according to their use case (for example, providing access to anonymized logs or masking IP fields).
We have also integrated the Elastic Common Schema (ECS). We realized the importance of having data that follows this model before being able to get started with machine learning and SIEM. Once ECS had been implemented, we were able to work on new security scenarios based on Elastic machine learning features. In the space of just a few weeks, this proved to be successful, allowing us to detect anomalies that were previously undetectable with a traditional correlation engine. The ease of creating machine learning jobs also made it easier for us to implement these “dynamic” rules.
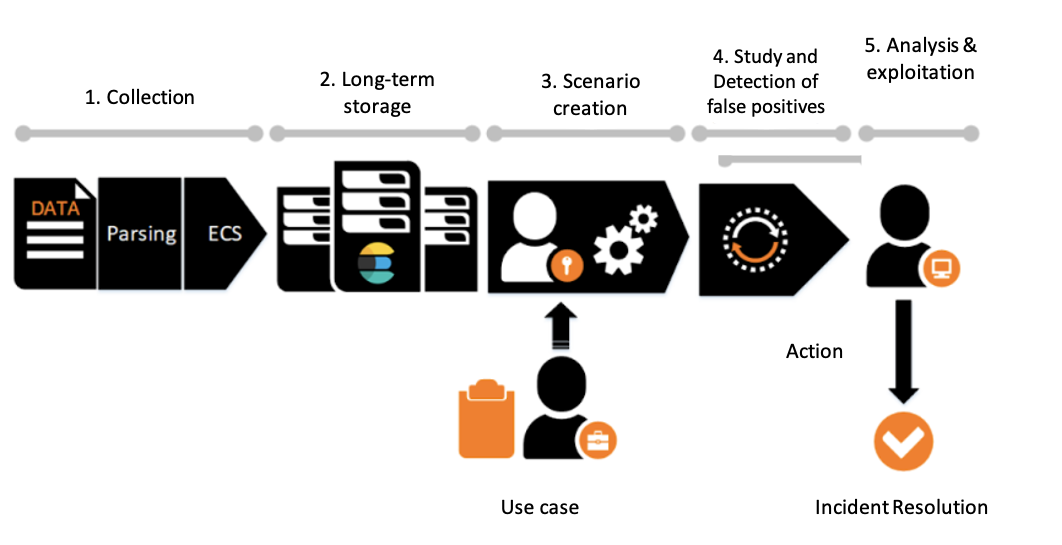
This is now the default process followed by our SIEM engineers. The SOC comes into play at stage 5, analyzing and making use of the alerts raised by the various machine learning jobs.
Next steps: Integrating Elastic Security
Our first steps with the Elastic Stack proved to be successful, and we wish to continue improving our anomaly and intrusion detection techniques by implementing additional tools offered by Elastic. We intend to increase the number of servers and the types of logs collected with the Elastic Stack. We’re also migrating our cold nodes to a new infrastructure based on the Amazon S3 API, which will allow us to use the snapshot features of Kibana — allowing us to increase our data retention capacity without increasing our storage costs. What’s more, we will continue to improve the enrichment of our security logs so as to better identify all the individuals on our intranet and detect intruders. We are also currently developing a “control tower” interface to take our use of Kibana even further with Canvas.
We would also like to improve our use of machine learning and make use of Elastic Security. For one, we will be testing Elastic Security for SIEM — and, more specifically, the correlation rules — in an effort to improve the automation of threat detection, and we would also like to implement Elastic Security for Endpoint security. Pairing the SIEM tool with endpoint security will allow us to improve our security orchestration, automation, and response (SOAR) capabilities, thus providing us with a welcome boost in productivity. Concentrating all our security tools into a single solution will also allow us to simplify investigations. We hope that the data generated by machine learning and endpoint security will supplement the data collected by our security equipment in a helpful way. Finally, this will strengthen the security perimeter monitored by EYES, particularly on our servers.
Jocelyn Renouf has been a security analyst at Orange Business Services in Paris for over two years and is currently focusing on implementing a new SIEM based on the Elastic Stack.