About the Yokogawa Electric Corporation
Yokogawa Electric is a manufacturing company with over a century of history and boasts over 400 billion yen in sales per year (FY2019/Consolidated), primarily from its plant control systems. Yokogawa Electric is a global company — literally, with plants and offices in 62 countries around the world and international sales accounting for 80% of total sales.
The Advancement of Digital Strategies Makes It Essential to Improve Security Monitoring
Yokogawa Electric has now positioned digital transformation (DX) as a core pillar of its business strategy. The company’s primary strategy for DX is to combine its control systems and other operational technology (OT) with information technology (IT) in order to provide support services for intelligent factories. Cloud-based AI will be used to analyze massive amounts of data collected using IoT sensors from equipment in customer plants. Factory simulations will be created, and customers will be provided with services including device failure prediction, proactive part/device replacement based on such predictions, and energy management (Fig. 1).
To summarize that strategy, Yokogawa Electric will make full use of technologies such as the cloud, containers, data analytics, AI/ML, and IIoT with the aim of providing equipment as a service and transforming its traditional business model based on “hardware sales + maintenance services” to a recurring model.
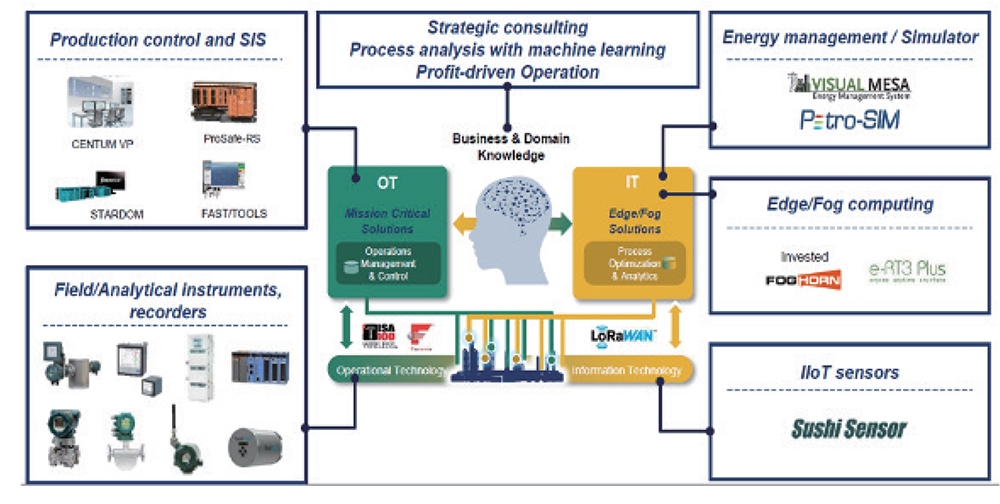
Figure 1: Next-generational support services using AI designed by Yokogawa Electric
Yokogawa Electric is also promoting DX within the company. For example, it is creating data lakes derived from a variety of sources and putting that data to use to make data-driven management and systems administration even more efficient.
“In implementing this DX strategy, it is extremely important that we beef up security,” noted Tetsuo Shiozaki, Deputy Director of the Digital Strategy Headquarters at Yokogawa Electric.
For example, since OT has traditionally been used in closed environments cut off from the internet and other external networks, there is little risk of exposure to cyberattacks and there were sometimes cases in which defenses against such attacks were lacking. As OT is combined with IT to promote the transition to smart factories using the cloud, there will be a strong need to bolster defenses for both OT and IT environments. Mechanisms and systems will need to be created that prevent IT environmental threats from invading OT environments, as well as rapidly detect any other threats that may invade OT environments.
“In order to address such issues, it was essential that we build up expertise in OT and IT security. Otherwise, I thought it would be impossible for us to reliably implement both our internal and external DX strategies. Yokogawa Electric has traditionally outsourced security monitoring of internal company systems to outside IT companies, but we revisited that approach and decided to establish our own SOC and conduct our own security monitoring, even as we work with external IT companies,” said Mr. Shiozaki.
Selecting Elastic Cloud for Its Open Development Model and Lack of Product Dependencies
The Digital Strategy Headquarters to which Mr. Shiozaki belongs was spun off from the Information Systems Division (IT Division), and today is solely responsible for both implementing DX within the company and creating mechanisms for supporting DX strategy directed outside the company to its customers.
There are also regional IT divisions established at offices across the world, but recently the Digital Strategy Headquarters in Japan has taken a central role in shifting to shared global IT services and shared, optimized global application/infrastructure environments. Those initiatives have been pushed forward in the same way as security products, including the run up to the launch of the company’s SOC. “Beginning in the fall of 2018, we set out to select a shared solution towards establishing a global SOC infrastructure,” said Mr. Shiozaki.
Effective solutions were needed for the collection and analysis of various log files in order to establish the global SOC infrastructure to support our larger DX strategy. In our estimation, Elastic Cloud fully met those needs.
At the end of this solution selection process, Yokogawa Electric chose to adopt Elastic Cloud, a cloud solution with a wide range of applications including SIEM solutions, endpoint security, threat hunting, and cloud monitoring.
It goes without saying that the company adopted Elastic Cloud because this cloud service fulfills the requirements needed to establish a global SOC infrastructure.
One of those requirements was to enable the collection and analysis of logs from a wide range of devices and systems without dependency on a particular security product. For example, as mentioned earlier, Yokogawa Electric had previously outsourced its security monitoring services to external IT companies, and those companies used an intrusion detection system (IDS).
According to Mr. Shiozaki, it is difficult to monitor today’s advanced, complex cyberattacks with IDS monitoring alone, and false positives are a common occurrence. Therefore, in building the company’s SOC infrastructure, a solution was needed that would enable log collection and analysis from a variety of security devices and systems.
However, in 2018 when the monitoring tool selection process was underway, there were no shared, standardized security products in use at the global offices, and different security products were used at each location. In order to be able to collect and analyze logs from such diverse products, a open source monitoring solution was needed that was not dependent on any specific product.
Taking into account the requirements described above, Yokogawa Electric selected Elastic Cloud as its leading candidate and conducted a proof of concept (PoC) for three months beginning in January 2019. The company’s tests involved collecting logs from IDS and authentication servers (AD servers), DHCP/DNS servers, and other sources at both the Tokyo headquarters and Singapore offices, then forwarding those logs to Elastic Cloud and looking at “how much time was required from log collection to analysis.” Based on the results of these tests, the company determined that security monitoring systems using Elastic Cloud function effectively as global SOC infrastructure, and in April 2019, Yokogawa Electric formally adopted Elastic Cloud as its security solution. The system used for the PoC was upgraded with additional resources and then deployed as-is to the production environment. The company then launched development of its security monitoring infrastructure towards the goal of setting up a SOC.
Centralized Monitoring of 30,000 PCs, Key Servers, and Networks across 15 Locations Worldwide
The first step that Yokogawa Electric took in the development of its SOC infrastructure using Elastic Cloud was to hire engineers familiar with Elastic. Specifically, the company sought Elastic engineers through its engineering center in Bangalore, India, and made some hires that took the lead in setting up the SOC infrastructure.
In order to brush up its engineers’ skills in this process, Yokogawa Electric utilized Elastic’s training and consulting services pertaining to Elastic Common Scheme (ECS) definitions and Logstash server log filtering configurations.
“In our case, we were collecting logs from a wide variety of different security products, so if these common schemes were not defined in advance, we wouldn’t be able to improve search speeds. For that reason, it was very important to have our engineers learn ECS, and it seems this strategy was very effective,” said Mr. Shiozaki.
Yokogawa Electric proceeded with building SOC infrastructure and data analysis systems, launching security monitoring at major plants and offices (Japan, Europe, North America, Singapore, the Middle East, and India) in FY2019. Alongside this, it also focused on improving its monitoring and detection applications. These initiatives linked Elastic Cloud with threat intelligence and IOCs (indicators of compromise: indicators and evidence of security violations caused by cyberattacks) to increase the precision of threat monitoring and detection capabilities.
Additionally, in 2020, Yokogawa Electric expanded its monitoring efforts to China, Russia, South America, Taiwan, the Philippines, Indonesia, and other sites.
This resulted in the monitoring coverage of PCs (antivirus software and EDR), key servers (AD servers, DHCP/DNS servers, etc.), IDS, and Microsoft Azure/AWS Web Application Firewalls (WAF) across 15 sites throughout the world. The logs and event data collected from those devices and systems were also stored in an Elastic Cloud managed service environment. As that data is analyzed in real time, this security monitoring framework predicts cyberattacks and detects security violations on a daily basis (Fig. 2).
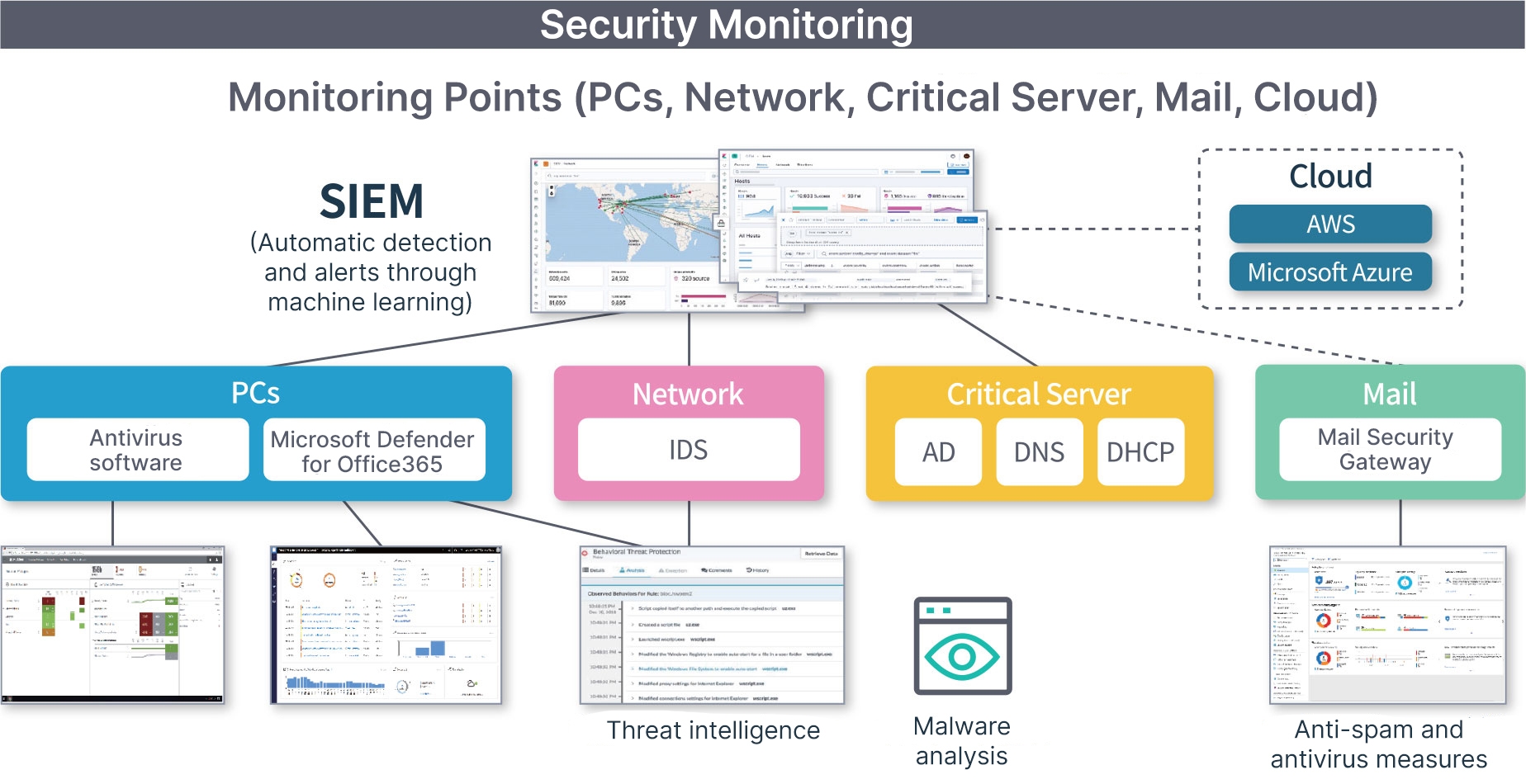
Figure 2: Conceptual image of Yokogawa Electric’s SOC infrastructure using Elastic Security
Of the devices and systems monitored, PCs alone total around 30,000 across the world, from which 5 to 6 million pieces of event data are collected every day that total 250–300 GB. This constitutes a true security data lake of security logs from a variety of devices.
Development of an Advanced Detection Program Combining Elastic SIEM and Machine Learning
As described above, Yokogawa Electric used Elastic Cloud to set up its global SOC infrastructure and steadily increased its monitoring coverage over time. Looking back on those initiatives, Mr. Shiozaki summarizes the benefits of Elastic Cloud implementation as follows.
“The biggest benefit of implementing Elastic Cloud was that we were able to visualize our wide variety of different logs and analyze them in real time. Furthermore, adopting the Elastic Cloud service enabled us to set up our global SOC infrastructure more quickly. That was another extremely meaningful benefit to our company.”
In the future, Yokogawa Electric plans to strengthen its security monitoring operations using Elastic Cloud. It has already adopted Elastic Cloud’s SIEM service, developed an advanced detection program that includes machine learning, and is promoting the use of MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge: a knowledge base in which vulnerabilities and attacks are categorized by tactics, technology, and method).
Additionally, Yokogawa Electric linked its SOC infrastructure up with the IT management tool (ITSM tool) ServiceNow, and has set up and begun using mechanisms to add comments and solution methods to incident alerts produced by the SOC as well as automatically send notifications to the relevant personnel.
Furthermore, the Elastic security monitoring expertise developed in the course of setting up this SOC infrastructure is also being shared with Yokogawa Electric’s operational departments, which provide security monitoring services to customers, in order to bolster the quality of those services as well.
Elastic Cloud continues to support Yokogawa Electric’s DX strategy today.
