Identifying malicious Remote Desktop Protocol (RDP) connections with Elastic Security
The new advanced detection analytics package to detect lateral movement

Lateral movement is a dangerous threat in the landscape of highly integrated technologies. If attackers gain access to an endpoint, it’s critical for security teams to identify any and all movements they make. To combat this threat, Elastic Security is excited to announce a new lateral movement detection package that makes use of advanced analytics.
In the past, we explored how we can detect malicious lateral file transfers using commonly abused admin tools, such as SAMBA, SMB/PS Remoting, FTP, SFTP, SSH, and SCP. But we wanted to explore further how to detect fileless malware that attackers use to hijack and compromise systems like the execution of malicious processes and the exploitation of remote services and sessions.
Adversaries frequently try to compromise active Remote Desktop Protocol (RDP) sessions to launch malicious code or gain access to other hosts in the network. In the 8.9 release, we introduce additional anomaly detection jobs and rules in this package capable of detecting lateral movement attacks for the most commonly abused operating system feature: Windows RDP.
This blog post gives a high-level overview of our technique to detect malicious RDP sessions and provides a breakdown of the steps to enable the assets under this package.
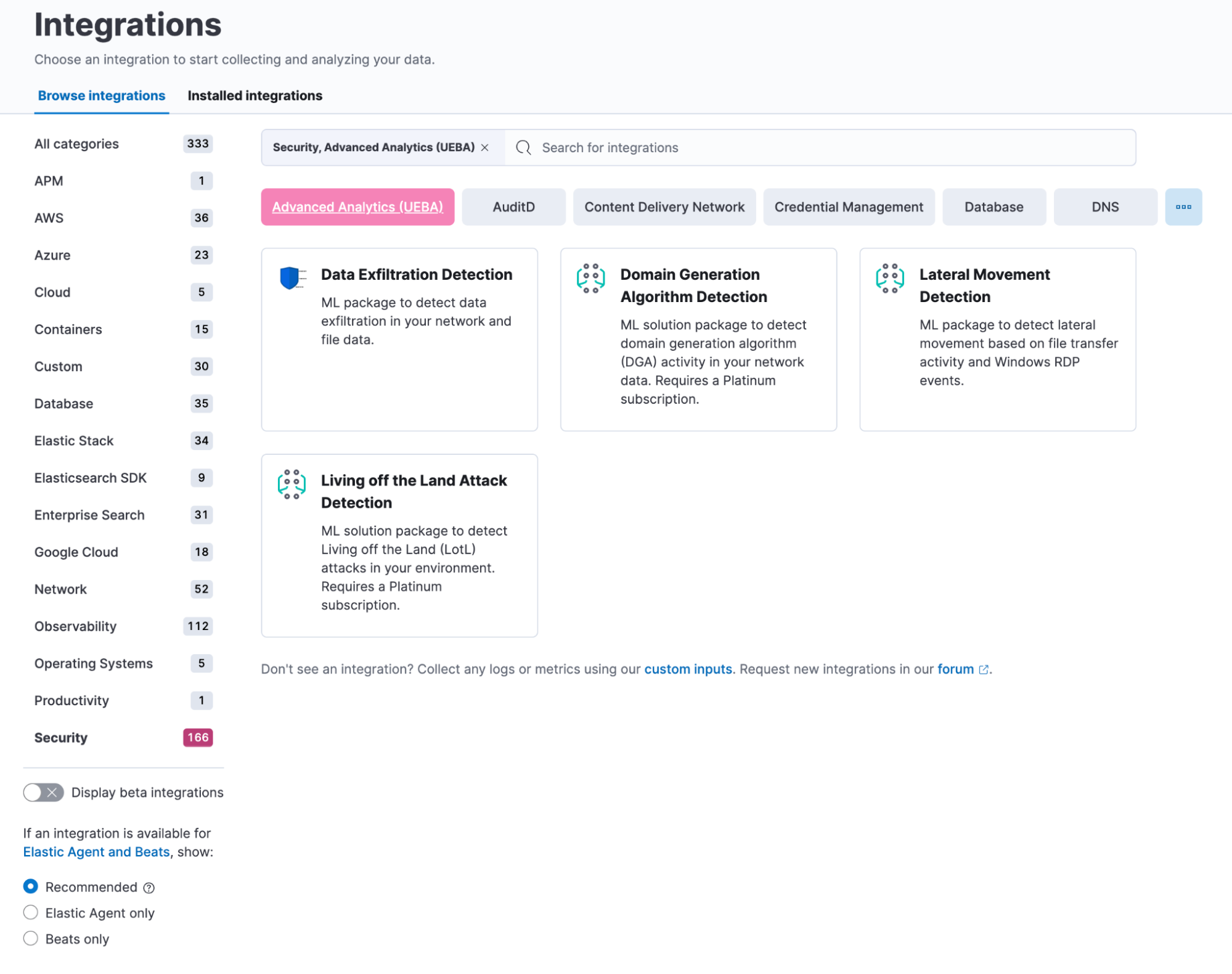
Lateral Movement Detection is now generally available
The Lateral Movement Detection package is generally available to Elastic® users in 8.9. With this Advanced Analytics use case, users can detect malicious file transfers and RDP session activities.
Detecting malicious RDP sessions
Identifying malicious lateral movement activity can be challenging, as attackers use legitimate software and tools to move unnoticed under the security radar. While teams can and should apply signature-based detections, these are vulnerable to zero-day attacks and should not be the main line of defense. To help prepare for zero-day attacks, security teams can implement behavioral signals to distinguish between legitimate and malicious tool use.
In this package update, we employ anomaly detection to establish a baseline for the expected behavior of RDP sessions and flag any divergence or statistical deviations from the norm. The anomaly detection jobs and rules are used in conjunction with Elastic®'s pre-built detections to increase the system's efficacy.
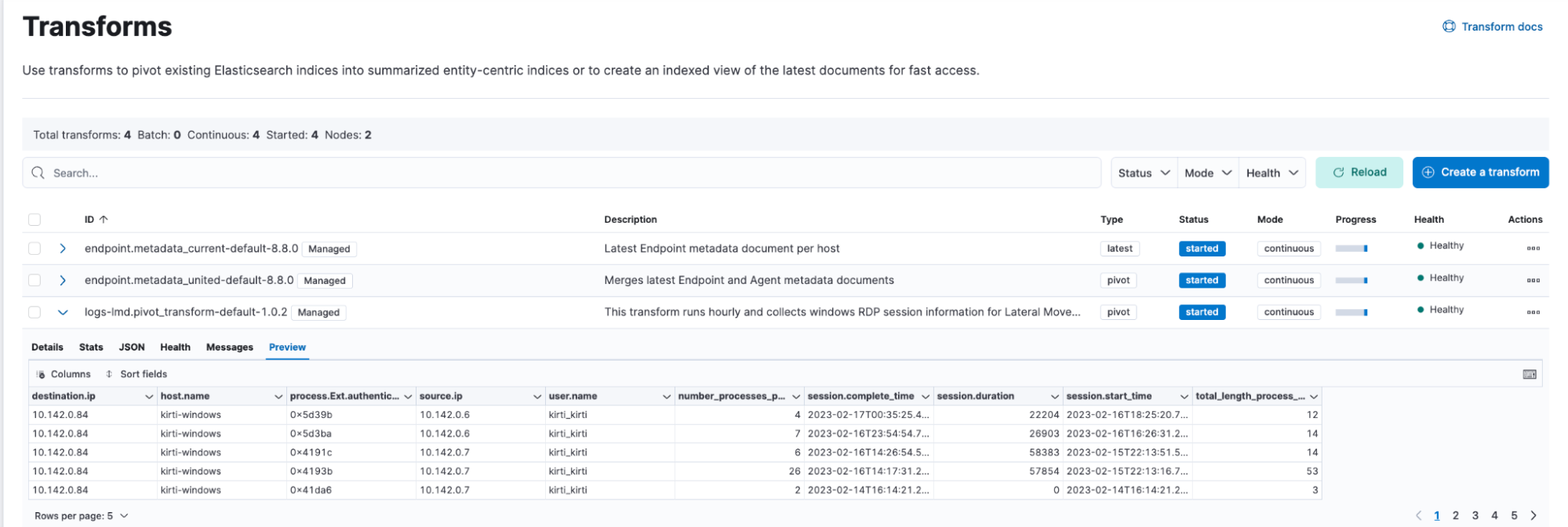
When working with an RDP session, we collect all the activities logged within the timespan of a user's log in to log out. We then extract aggregated features from raw Windows RDP events using a pivot transform to establish a session. To monitor the RDP sessions, we extract each session's start and end time, total duration and length of process arguments of a session, and number of processes started in a session.
The following screenshot illustrates the data extraction process.
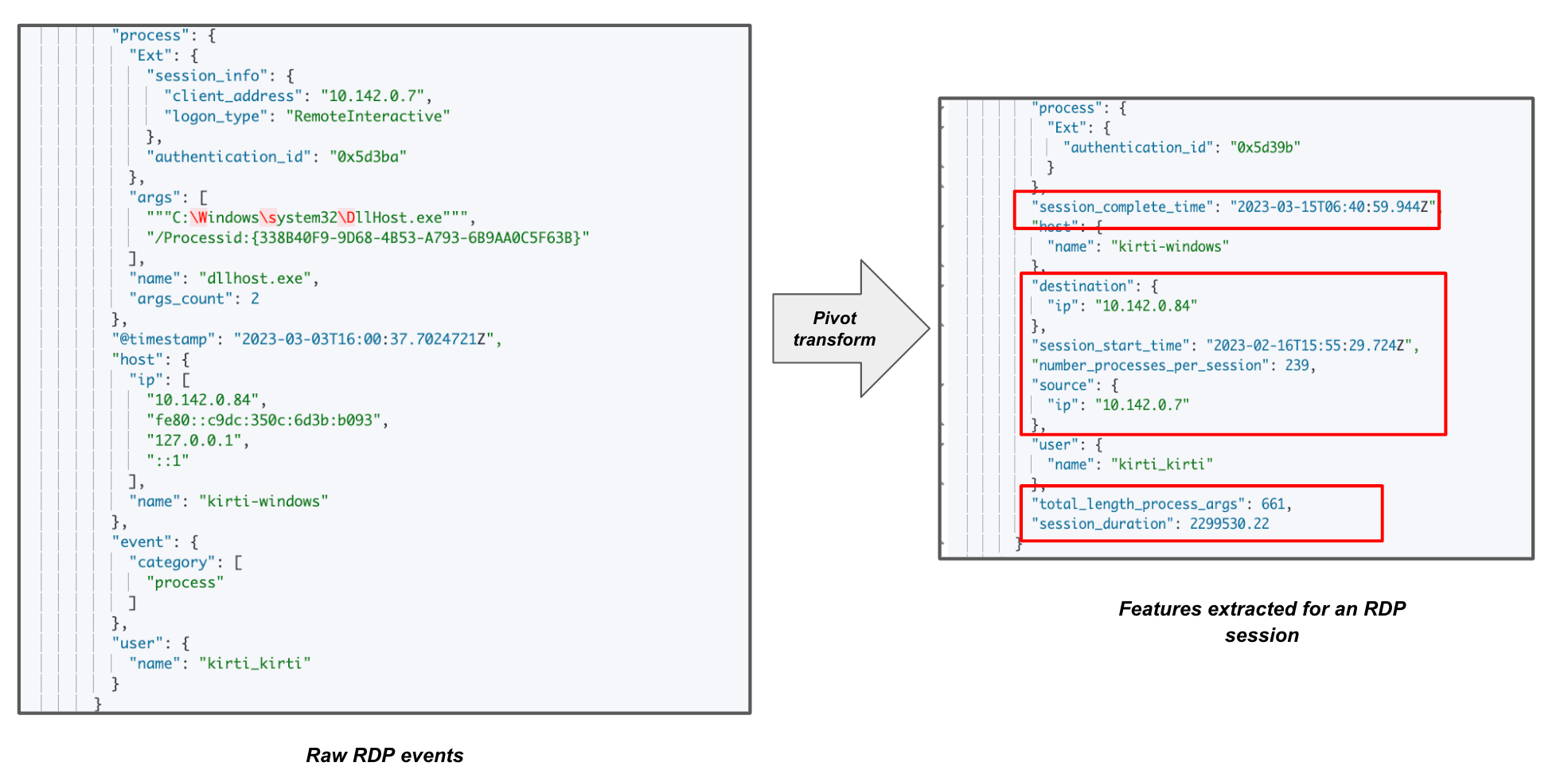
While reviewing sessions, abnormal activity is flagged by anomaly detection. For instance, these jobs look for unusually high RDP session duration and unexpected times or days for a session start. Detecting increased process execution and process arguments helps identify possible malicious activity in a session. We also track abnormally high RDP connections between source and destination IPs.
Additional RDP detection through LotL
To take detection further, security teams could also leverage our existing Living off the Land Attack Detection(LotL) package to identify malicious processes that started during an RDP session.
The following sample document is an example of the LotL package’s supervised model prediction on the RDP events.
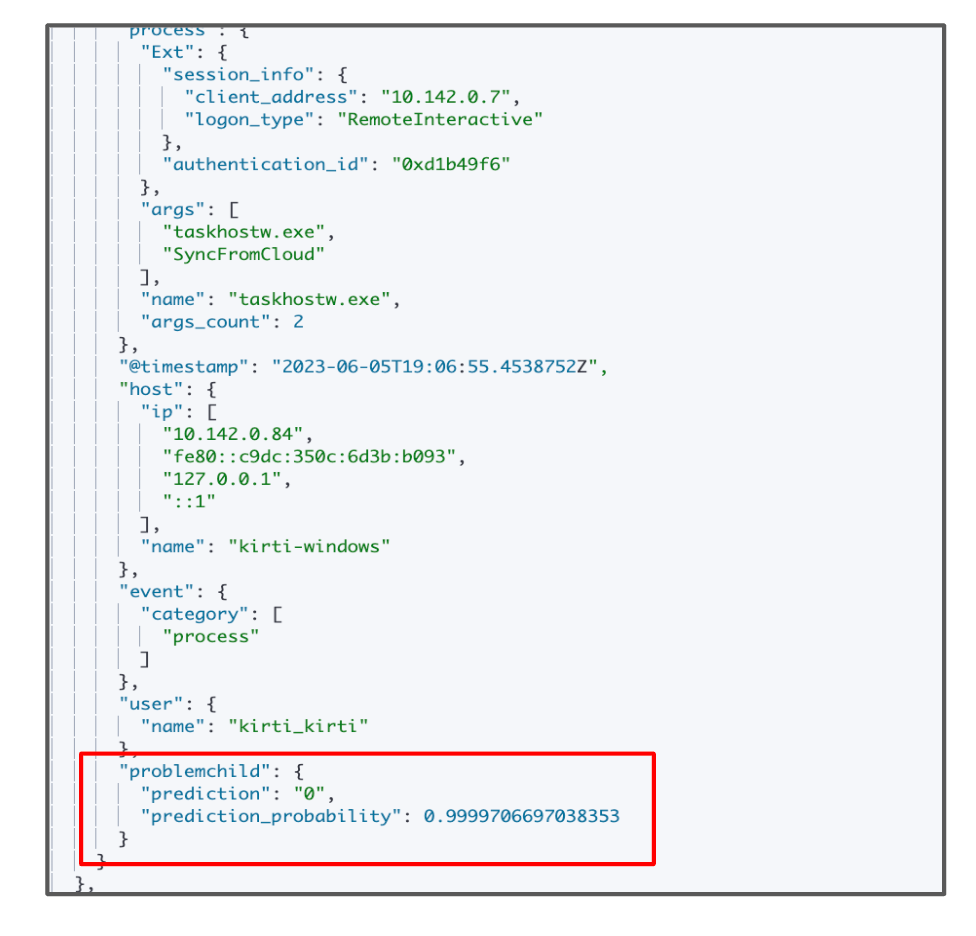
Follow this documentation to enable the LotL package with the RDP-based events in your environment.
Prerequisites for Lateral Movement Detection
To ensure the included anomaly detection jobs and ML rules can be enabled successfully within the environment, security teams must configure one of the log data sources below:
File transfer events
You should have the data equivalent to this query in your environment to exploit the anomaly detection jobs and rules based on the file transfer events. The standard Elastic index pattern for endpoint file transfer events is logs-endpoint.events.file-*.
RDP events
The default index pattern for Windows RDP events is logs-endpoint.events.process-* . Refer to the below query to inspect the volume of RDP events in your process data logs.
"query":{
"bool": {
"must_not": [
{
"term": {
"user.name": "system"
}
}
],
"filter": [
{
"exists": {
"field": "process.Ext.session_info.client_address"
}
},
{
"exists": {
"field": "process.Ext.authentication_id"
}
},
{
"exists": {
"field": "host.ip"
}
},
{
"term": {
"event.category": "process"
}
},
{
"term": {
"process.Ext.session_info.logon_type": "RemoteInteractive"
}
}
]
}
}Additionally, if you’re not using the Elastic Agent, you must confirm that your data fields are named in accordance with the field names required by the aforementioned queries. This is not an issue if you are using the Elastic Agent to acquire endpoint logs.
Getting started
As of version 8.8, users can install the new additions in the Lateral Movement Detection package from the Integrations app in Kibana®. To set up and begin using all of the assets under this package, follow the steps listed below.
Step 1: Installing the package
To install the updates in this package, go to the Settings tab and click on Install Lateral Movement Detection assets. If you have already installed the package, click the upgrade button under Settings. This will install all of the artifacts under this package to generate events and alerts when Lateral Movement is detected in the file transfer activity and Windows RDP events.
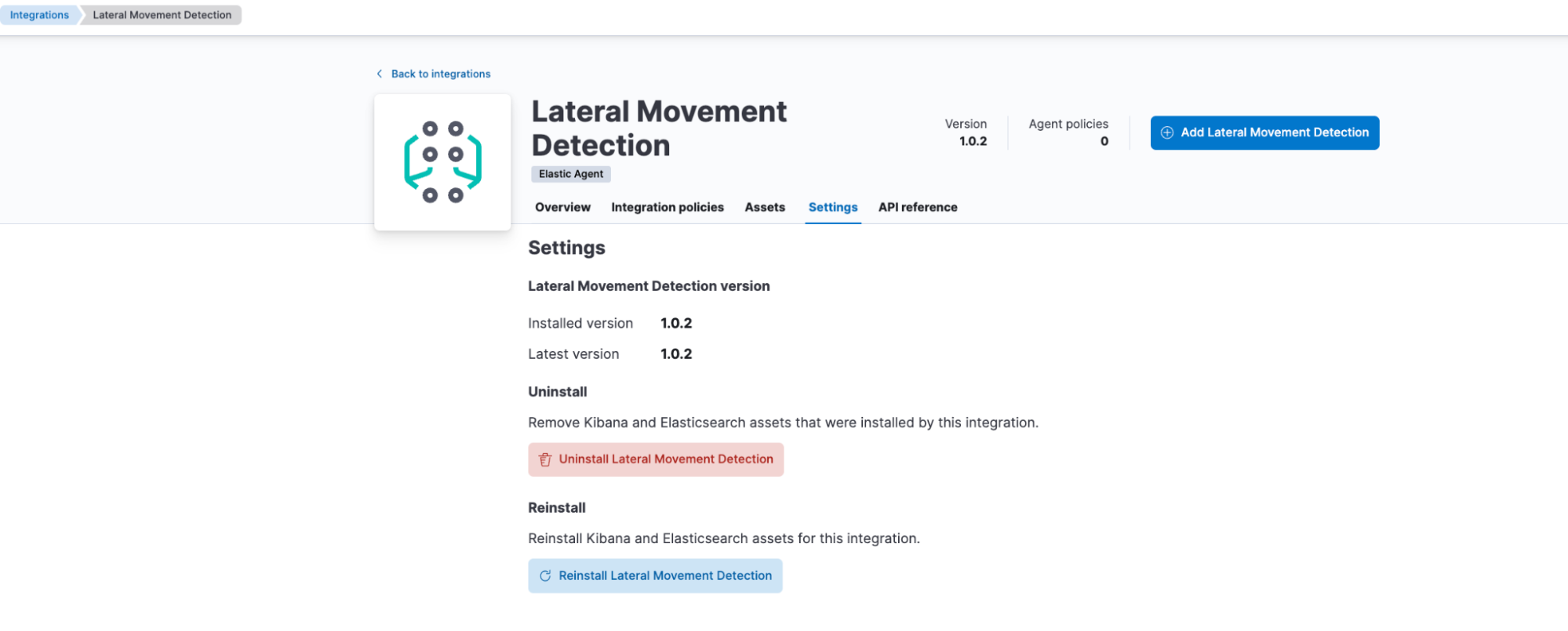
Step 2: Installing the pivot transform
As discussed, this package installs and runs a pivot transform to extract features from raw RDP process events. After successfully installing your package, you can see the transform up and running under Stack Management > Data > Transforms.
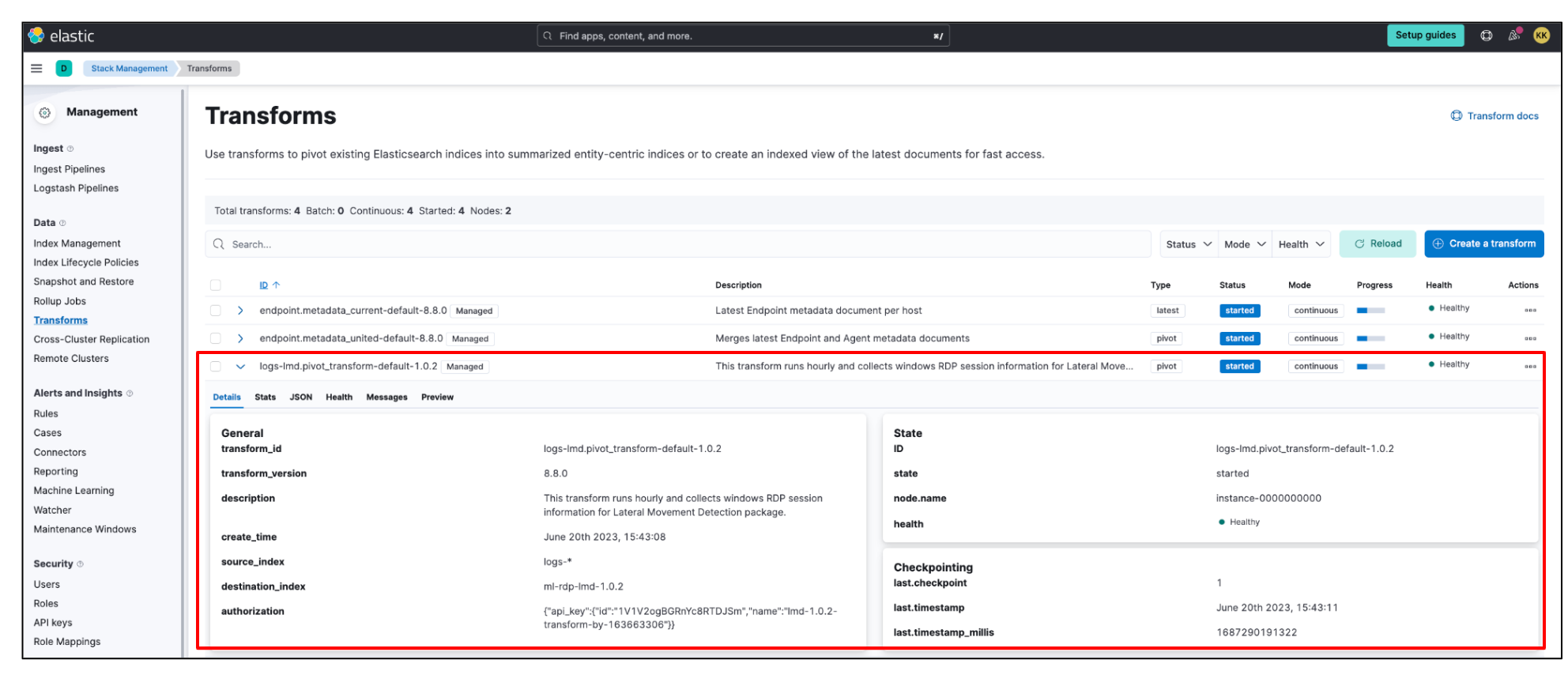
You can view the transform’s results in the preview section or destination index ml-rdp-lmd-1.0.2.
Step 3: Running anomaly detection jobs
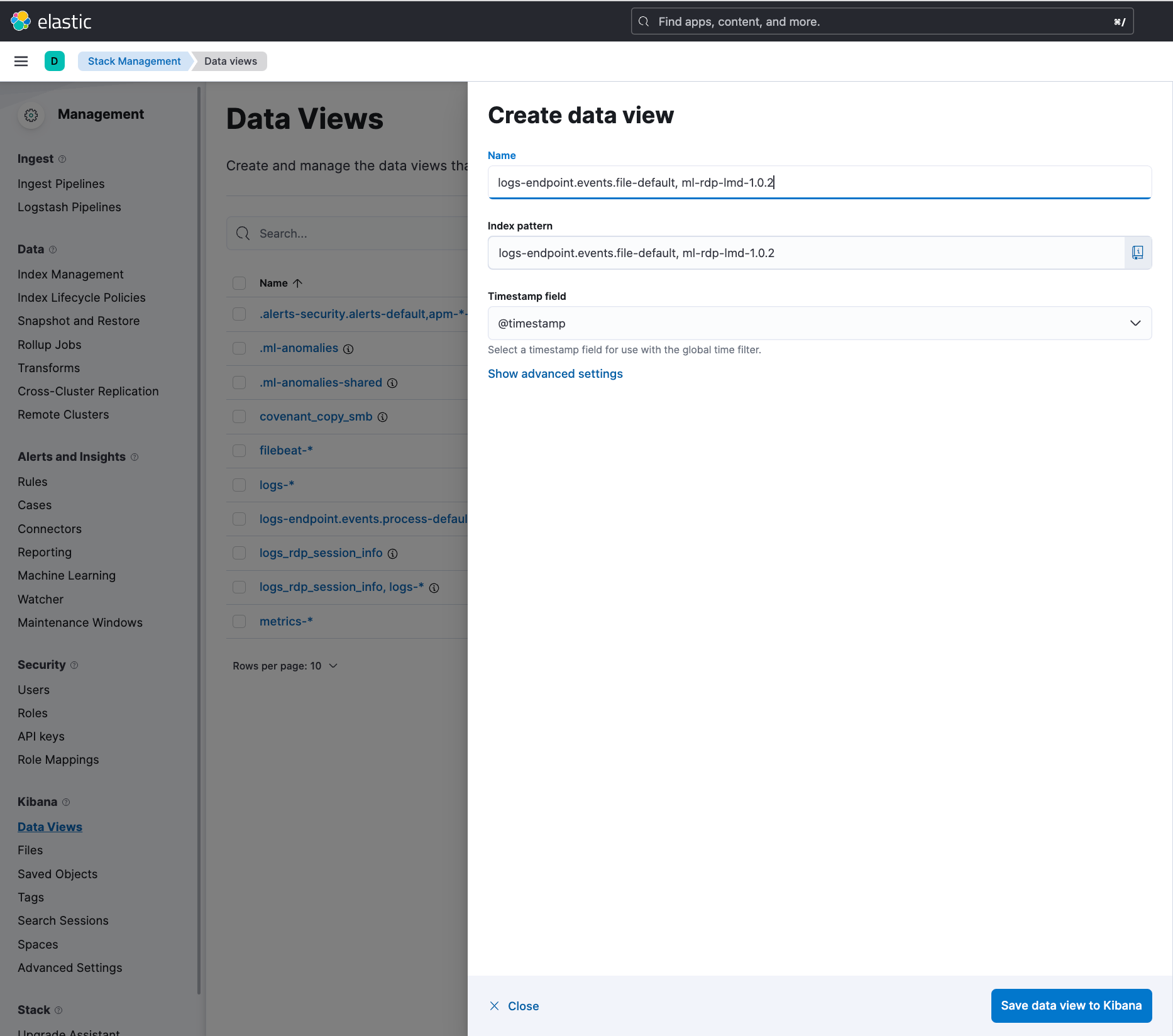
Before enabling the anomaly detection jobs, create a new data view grouping the transform’s destination index (ml-rdp-lmd-1.0.2) and the index with file transfer events (logs-endpoint.events.file-*). This will ensure all the required configurations are available for enabling these jobs.
To do so, go to Stack Management > Kibana > Data Views and click Create data view. Enter the name of both indices (logs-endpoint.events.file-default and ml-rdp-lmd-1.0.2) to the Name and Index pattern fields and click Save data view to Kibana.
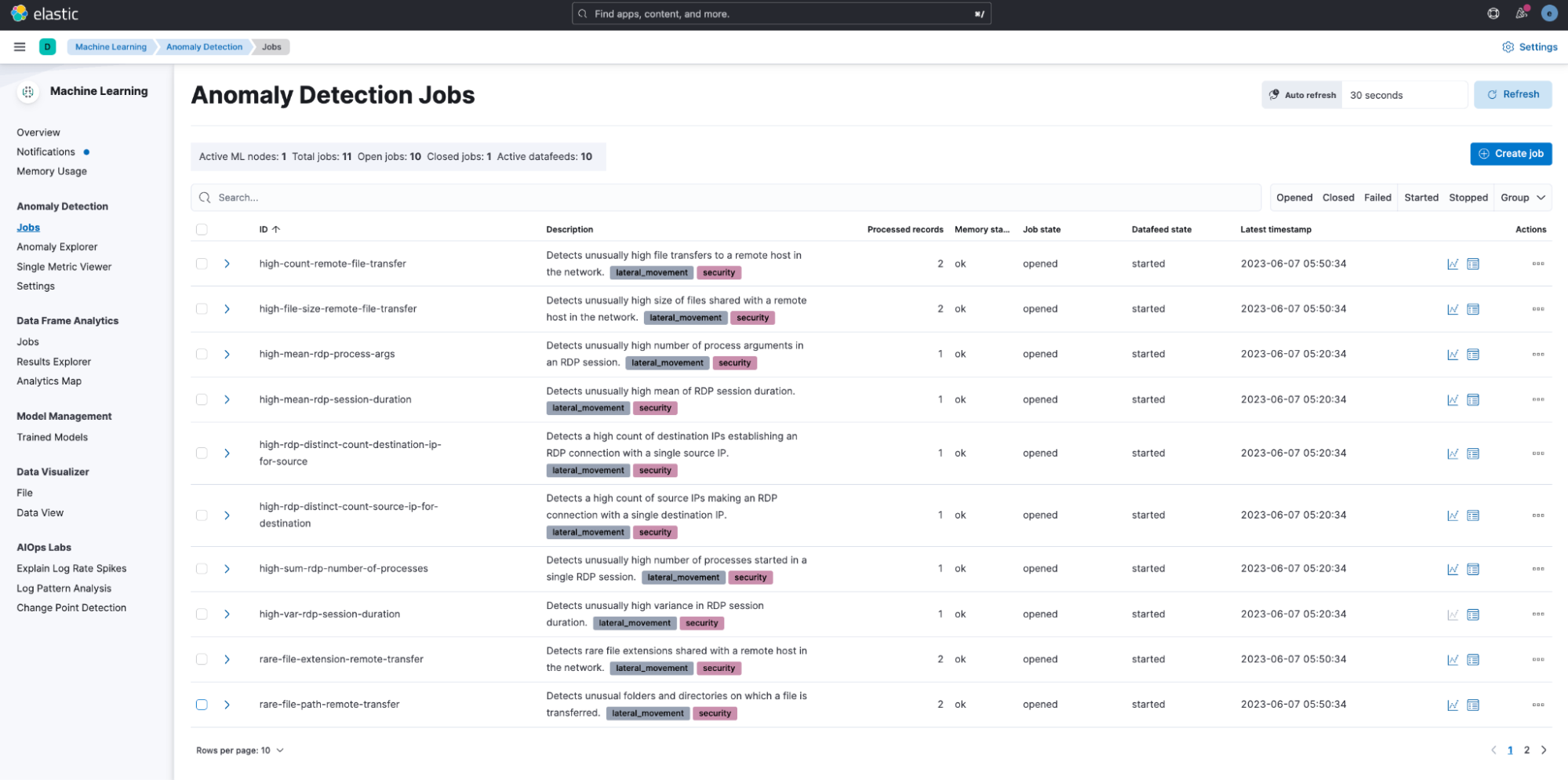
After creating the data view, go to Machine Learning > Anomaly Detection to run all the anomaly detection jobs under this package. Then, go to the Jobs wizard under Anomaly Detection and click on Create job. Select the data view that you just created as the data source.
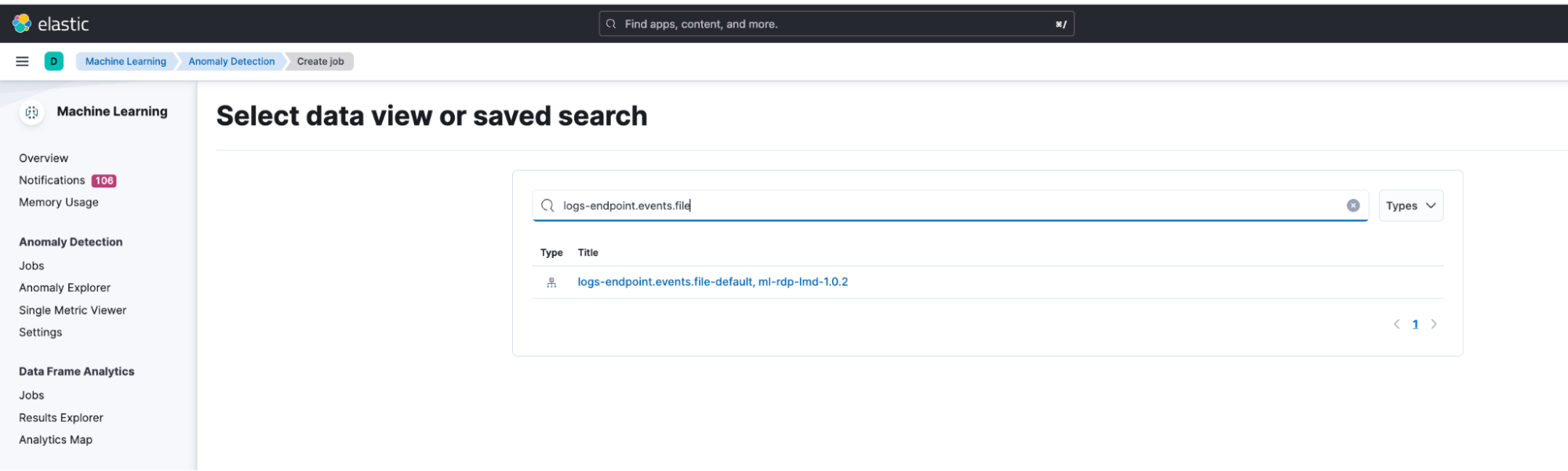
Select the Lateral Movement Detection card under the Use preconfigured jobs option and click the Create jobs button.
Step 4: Enabling security detection rules
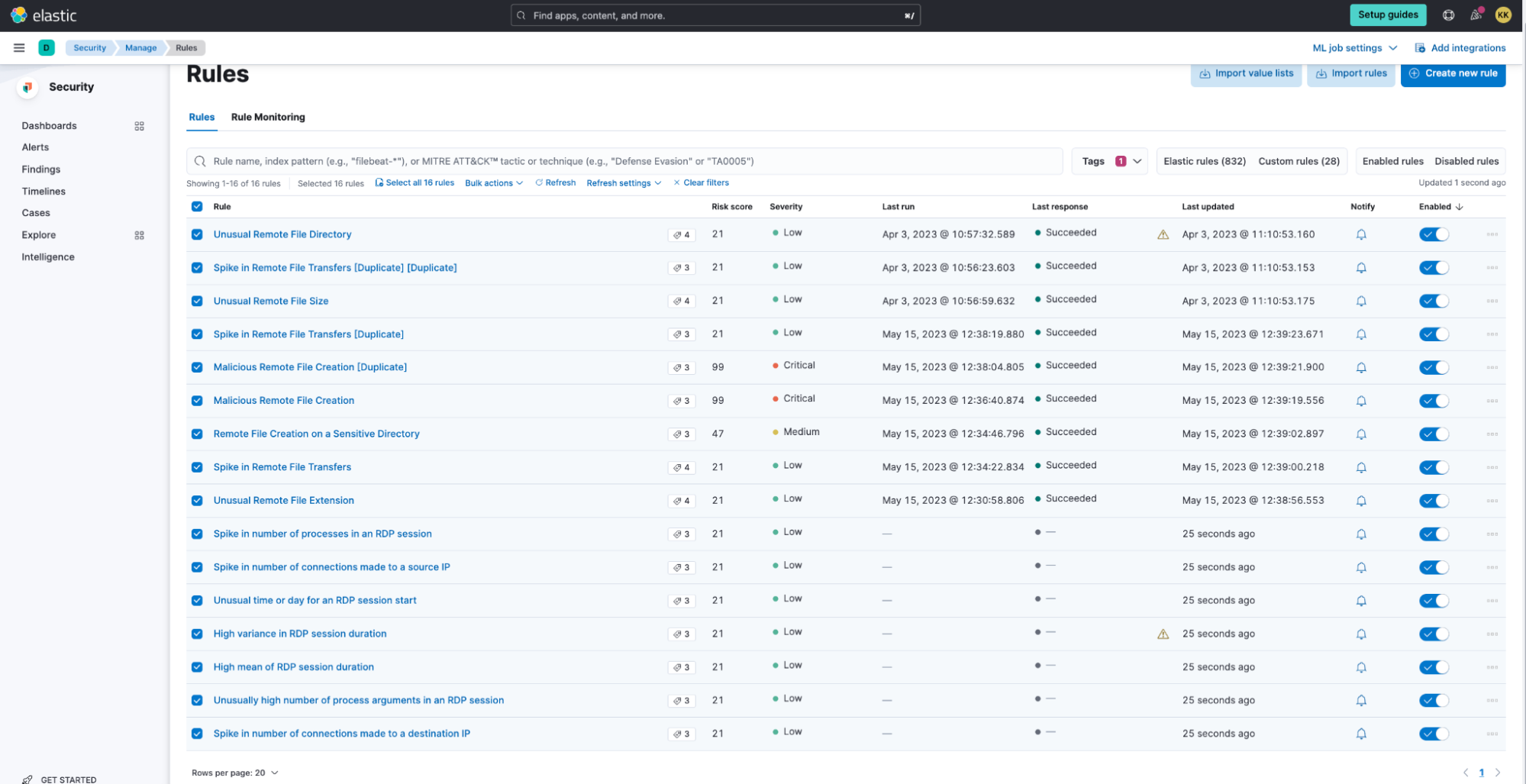
To enable and use the installed rules, navigate to Security > Alerts > Manage rules and select Load Elastic prebuild rules and timeline templates. If you’re running in Elastic Cloud, this step is done automatically.
You can use the Lateral Movement Detection tag to filter for all of the detection rules under this package. The rules based on anomaly detection jobs are triggered when the anomaly score surpasses a predetermined threshold, which can be customized by duplicating the detection rule.
Once you have the Lateral Movement Detection package up and running, the system will inform you of any suspicious behaviors in your environment.
Identifying suspicious lateral movement activity
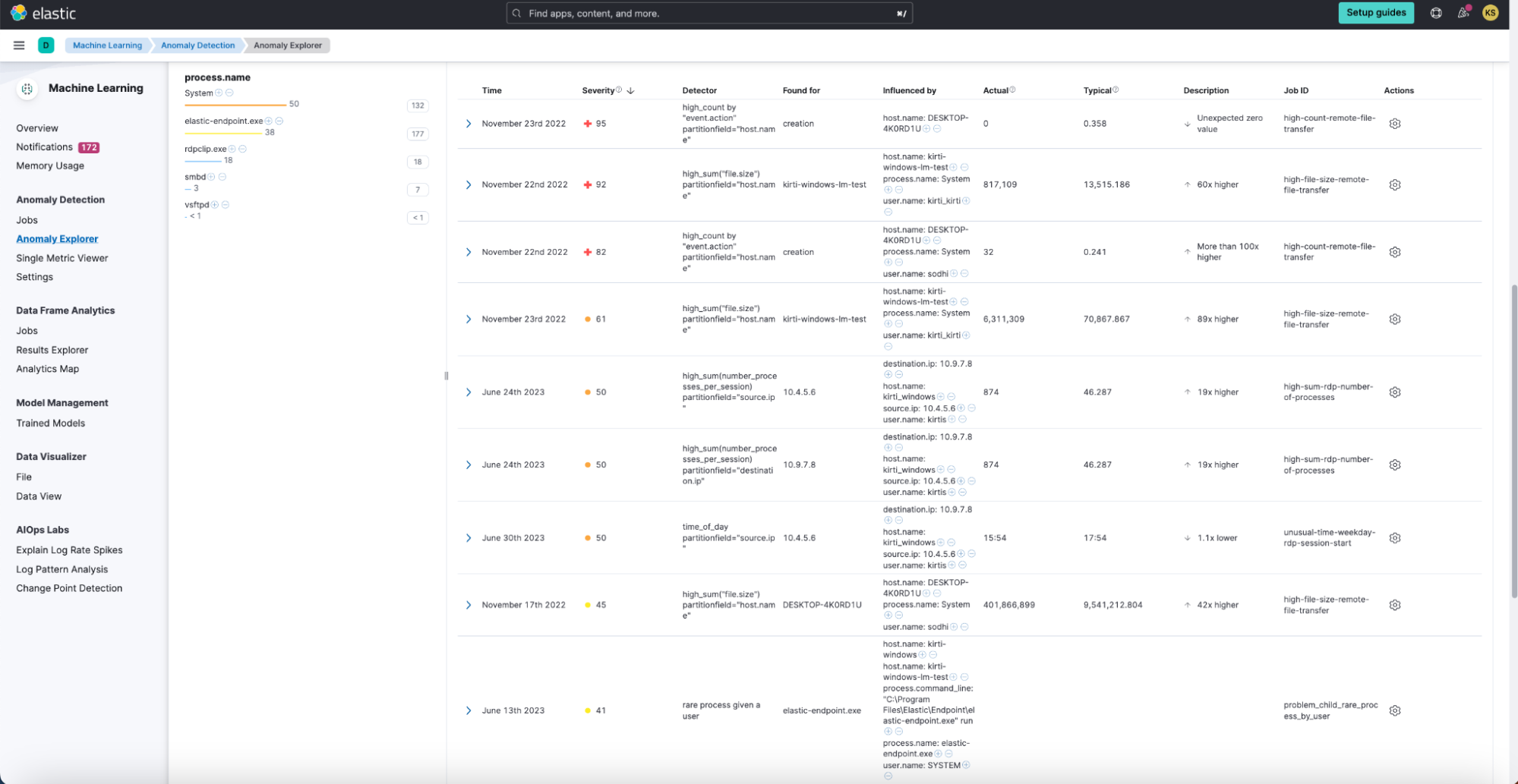
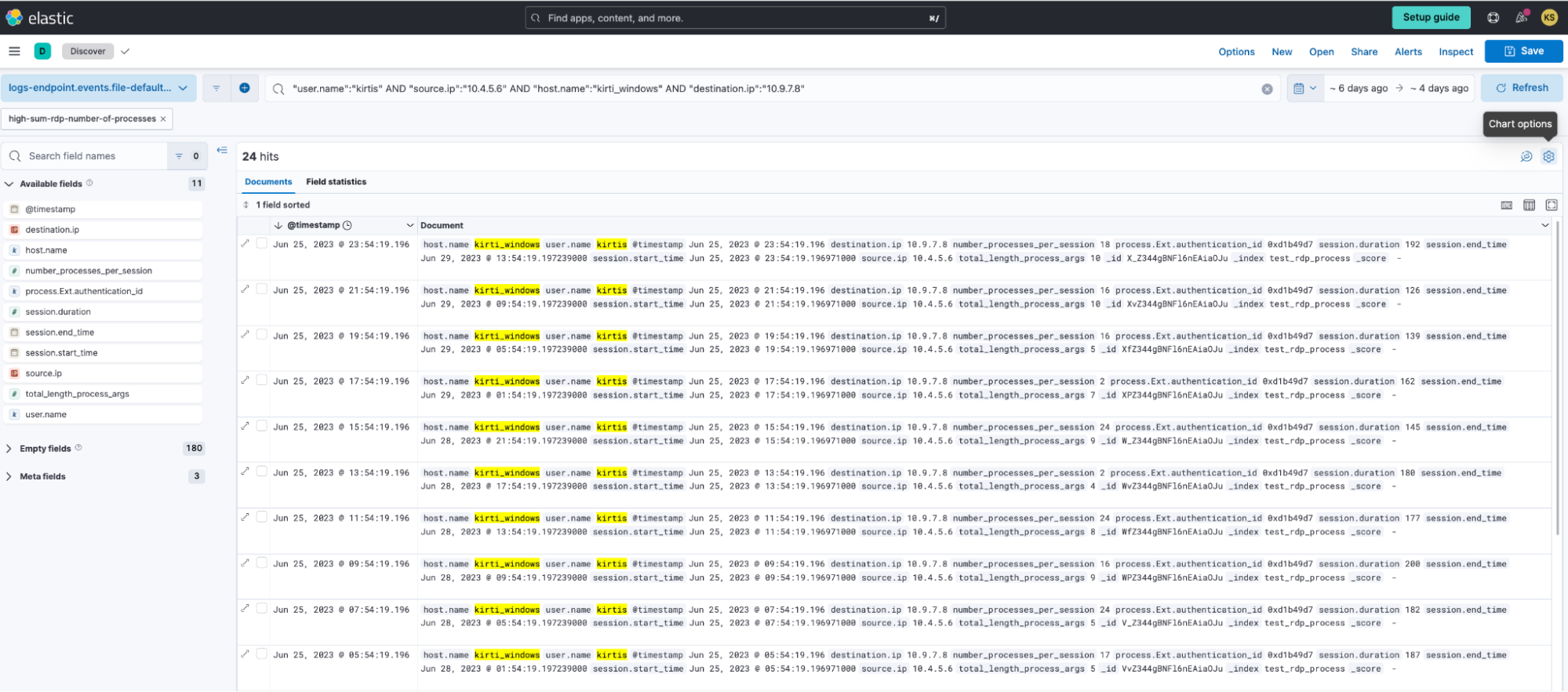
You can view the anomaly detection alerts under the Machine Learning > Anomaly Detection > Anomaly Explorer page. Triage the high severity alerts by clicking on the Actions > View in Discover option at the rightmost corner of your alert.
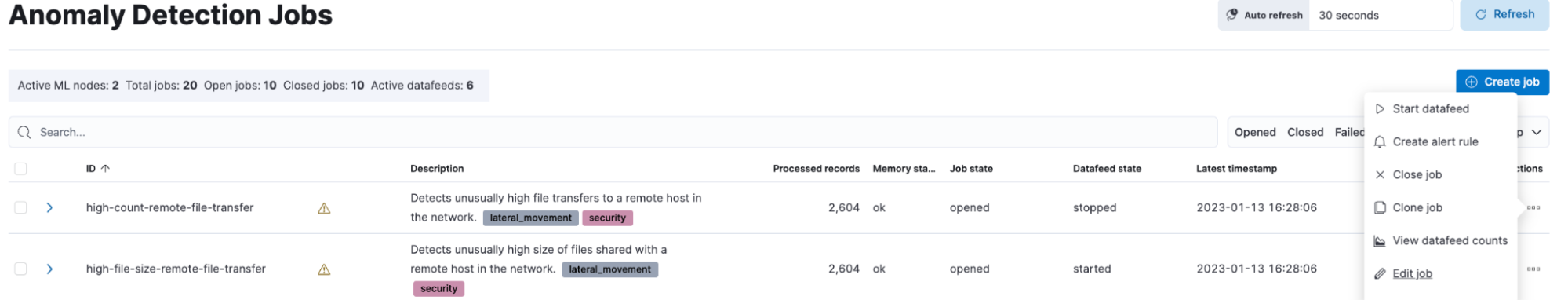
Tuning the package
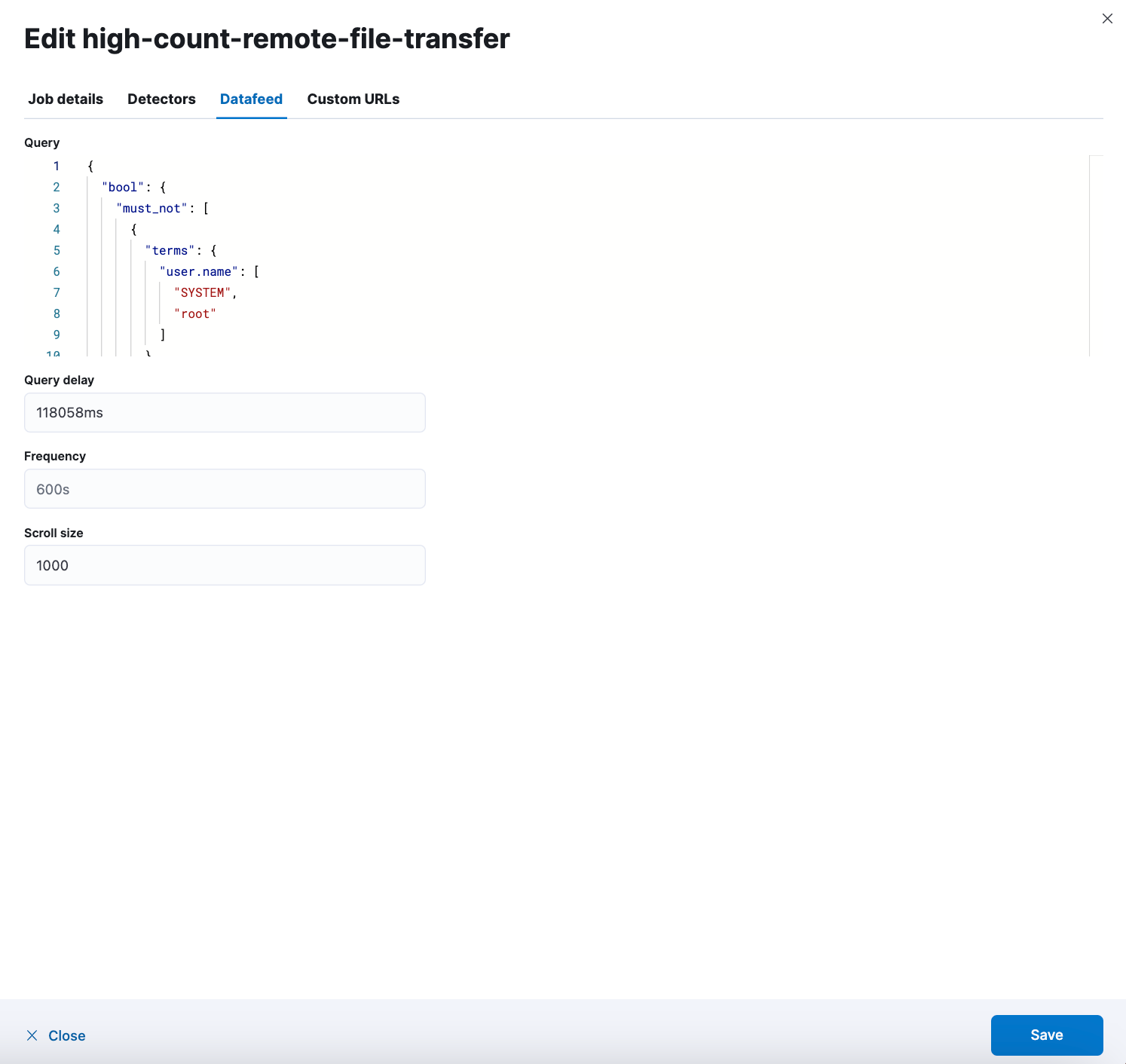
If you’re experiencing a high volume of false positives, it’s very easy to tune the anomaly detection jobs. Go to Machine Learning > Anomaly Explorer > Jobs and click the Edit job option from the Actions panel.
Select the Datafeed option, enter a filter based on your environment, and click Save to enable your changes.
Get started today
Over the last year, we have introduced various Advanced Analytics detection use cases as fleet packages. Our goal is to continue to expand these out-of-the box detection capabilities over time. Elastic users can enable this or any of the Advanced Analytics conveniently from within their environment. These use cases include:
- Identifying advanced attack vectors and persistent threats
- Detecting APT activities out of the box
- Leveraging Elastic’s highly operationalized ML technologies
- Working with the Elastic Detection Engine to provide advanced correlation, scoring, and visualization techniques
Enable these features in your environment and try out our Lateral Movement Detection package today! Elastic Security is dedicated to providing high-value features to security teams all across the globe — and to that effort, we are always excited for feedback. If you have any suggestions or encounter any issues during the process, please get in touch with us on our community Slack channel, discussion forums, or our open detections repository.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
Elastic, Elasticsearch and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.