Don’t let your data rain down: A beginner’s guide to cloud security

As digitalization becomes a norm, businesses are transitioning to cloud services for increased scalability, cost-effectiveness, and operational efficiency. But this transformation comes with a new challenge — securing the cloud.
The complexity of cloud security
Cloud security is inherently complex due to a variety of factors. There is diversity among cloud services, such as IaaS, PaaS, and SaaS, and each comes with its own set of security considerations. Coupled with this, the shared responsibility model demands both the cloud service provider and the user to take part in securing the cloud, which often leads to ambiguity in roles and responsibilities.
Furthermore, the cloud's dynamic nature allows for rapid scalability, but this also leads to an ever-changing attack surface that can be hard to keep track of. This is exacerbated by the challenge of managing access controls in an environment accessible from anywhere in the world.
Finally, unlike traditional on-premises setups where organizations have complete control, gaining visibility and control over the virtual infrastructure in the cloud is inherently more complex and challenging.
In light of these intertwined complexities, securing the cloud requires a vigilant, adaptive, and well-integrated security strategy that takes into account the fluid nature of the cloud and the multifaceted challenges it presents.
How to secure your cloud environment: 3 key steps
Step 1: Gain visibility
The first step in cloud security is understanding what you need to protect. One of the ways to begin gaining visibility into your cloud environment is by collecting logs — detailed records of your system's activities.
Logs are invaluable tools for threat detection and past incident analysis. They provide insight into user activities, system errors, data transactions, and security incidents. These logs can reveal patterns and provide insight into the behavior of users, systems, and networks. Over time, this information can be used to create a baseline of normal activity, which can help you detect anomalies that may signal a security threat.
Yet, viewing cloud security through the lens of logs alone resembles the well-known tale of the blind men and the elephant. Each man, limited to their touch-based experience of a single part of the animal, forms an incomplete perception of the whole. This parable rings as true in cloud security as it does in ancient wisdom; limited perspectives risk overlooking the full picture.
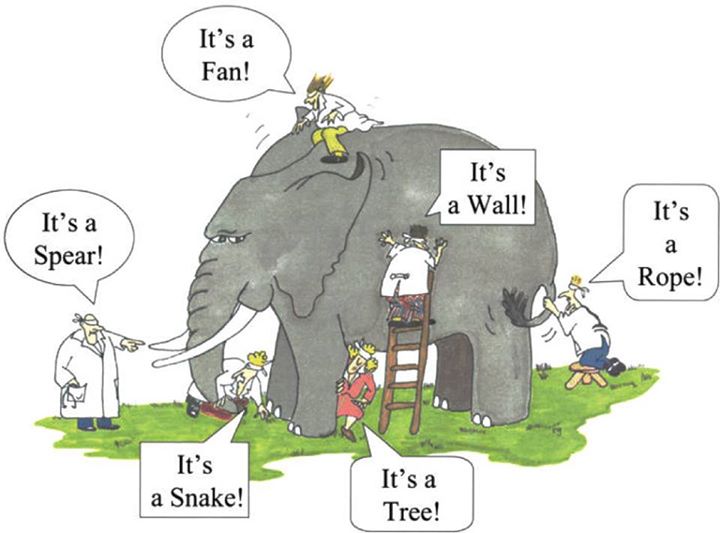
To get a comprehensive understanding of your cloud environment, catalog all your cloud assets. This step allows you to see your environment as a whole — much like understanding an elephant in its entirety rather than just its individual parts. The principle here is simple: you cannot protect what you don't know exists.
Step 2: Understand your security posture
With this visibility, you can now understand your overall cloud security posture. Understanding your cloud security posture involves two key parts:
- Configuration audit. Conduct a thorough audit of each asset's configuration settings. Poorly configured assets can be easy targets for cyber threats. Ensure configurations align with established hardening guidelines, a set of best practices that reduce system vulnerabilities, and your organization's security controls.
- Vulnerability assessment. Identifying existing vulnerabilities is paramount. Run vulnerability scans on your assets to spot vulnerabilities in the systems that process your data and then proactively address any vulnerabilities that could be exploited.
Remember, assessing your cloud security posture isn't a one-time task. With the evolving threat landscape and changing cloud environment, continuously reevaluate your assets' security posture.
Step 3: Monitor the runtime of your workloads
Cloud Service Providers (CSPs) offer various computing services, which process large amounts of data that often are critical for business operations. Therefore, maintaining comprehensive visibility into the runtime of these workloads is not just desirable; it's absolutely essential. This visibility allows you to understand what is happening within these workloads at any given time.
Why is this important? Because as workloads process data and are often interconnected, they can become targets for cyber threats aiming to disrupt business operations and steal data. If these threats take hold, they can quickly spread throughout your cloud environment, causing extensive damage.
By having clear visibility into the runtime of your workloads, you are well-equipped to detect these threats as they arise. You can spot unusual patterns, anomalous behaviors, or indicators of compromise that could signal a potential threat. This enables you to act swiftly and decisively, neutralizing the threat before it has the chance to propagate within your environment.
Conclusion
Cloud security is a journey, not a destination. From gaining visibility into your cloud assets to understanding your security posture and monitoring your workload's runtime, the process requires a comprehensive, integrated security strategy. It's also essential to remember that securing your cloud isn't a one-time task but a continuous process, necessitating regular reevaluation and updating of security measures. As we navigate through an increasingly digitized world, implementing effective cloud security practices is not just an option — it's a critical necessity.
Wondering how Elastic Security can be an ally in your cloud security odyssey? Dive into my blog post, Leveraging Elastic Security for comprehensive cloud protection, where I explore how Elastic Security empowers you to maintain the confidentiality, integrity, and availability of your data in the cloud.