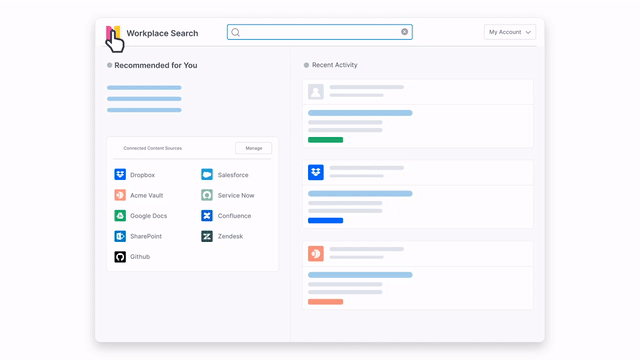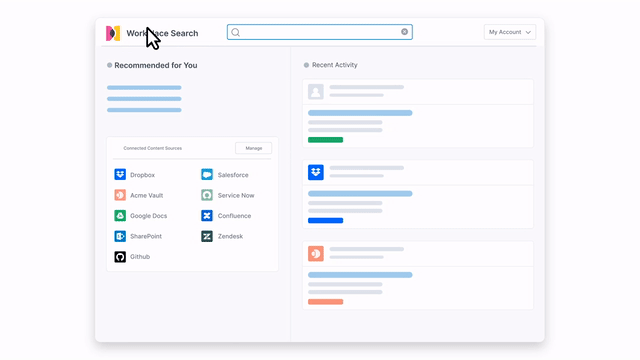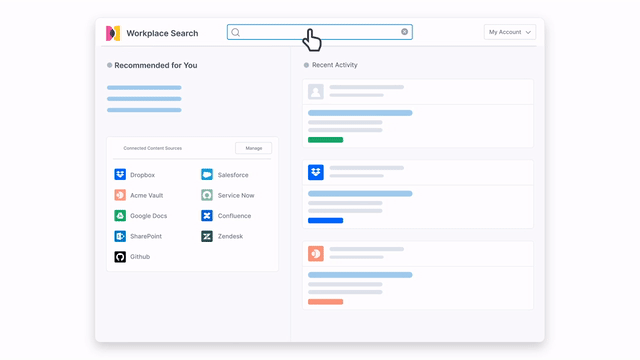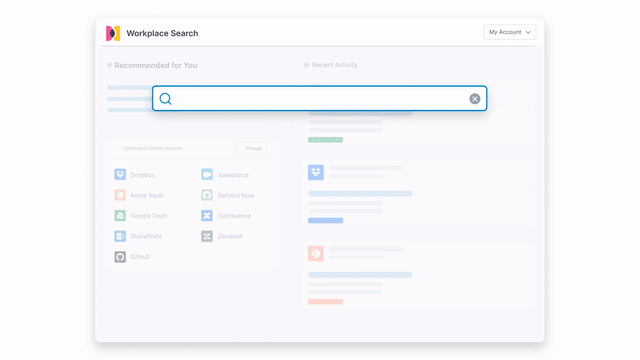
Mitigate security risks by solving your hidden data challenges
Your organization has data stored all over. With that comes increased potential points of failure and elevated risk for monetary and reputational loss. Because of increasing attack surfaces and sophisticated security threats, security teams need to analyze every security event to keep their organization and customers protected, remain in compliance, and avoid reputational loss.

Implement search, observability, and security solutions to transform your data into answers in real time
Unfortunately, your current tools aren't working
Slow time to results
Inflexible architecture
Disconnected workflows
Opting for point solutions like log monitoring, APM, and SIEM may seem strategic for mitigating security risk, but it can lead to drawbacks that ultimately impact your security posture. But don't worry! There's a better solution.

Meet Elastic
Elastic is a leading provider for comprehensive search, observability, and security solutions. All powered by the same flexible and performant data analytics platform, Elastic helps organizations around the world unlock the full potential of their data to mitigate security risks.
Additional resources
What are leading organizations doing to protect against rising security threats — and what differentiates advanced organizations from beginners?
Consolidating all data sources into a single platform enables security teams to quickly correlate and respond to security incidents by providing a complete view of the infrastructure.
A data store that offers various security features like built-in data encryption, access control, audit logging, field-level security controls, and data masking and anonymization capabilities is crucial.