Automating insight into SEC cybersecurity filings with Elastic

The Securities and Exchange Commission (SEC) adopted new rules last week that require companies listed on the US Stock Exchange to disclose any material cybersecurity incidents.
In addition to reporting incidents, companies are also required to describe their approach to cybersecurity risk management, strategy, and governance on an annual basis.
The new rules are primarily intended to provide transparency to shareholders and investors, but the information within relevant SEC filings will be of interest to CISOs, security teams, and business leaders who will want answers to questions like:
- What types of incidents do public companies deem material?
- Which of the companies that we rely on have experienced material security incidents?
I did a quick proof of concept to see how easy it would be to collect relevant SEC filings and analyze them in Elastic®.
Spoiler alert: it’s really easy.
First, some notes on SEC reporting mechanisms
The SEC requires companies to file various reports — with annual and quarterly financial statements as probably the most well known and well publicized. In addition to filing annual financial reports on Form 10-K and quarterly reports on Form 10-Q, public companies must also report material corporate events on a regular basis.
Form 8-K is the form used to announce major events that shareholders should know about. Here’s a listing of all of the 8-K forms filed with the SEC on July 27, 2023. Within this existing 8-K form, a new “item” or sub-heading 1.05 will contain details of any reportable security event.
All of this data is public and is made available via the SEC’s “EDGAR” platform. With this in mind, I thought it should be pretty simple to:
Collect all 8-K filings on a periodic basis
Filter on those that include item 1.05
Analyze this data to answer the questions posed above, or
Trigger an alert or workflow when a company we care about files an incident report
The data is mine — pivoting from EDGAR to SEC-API.io
While the EDGAR platform offers public APIs for the type of data we’re looking for, I found that there was not an API that could provide the data in a way that was going to be convenient for this use case — at least, not without the need to do a lot of data processing up front.
Not disheartened, I continued digging and discovered that sec-api.io was already doing this pre-processing and making the data available through a more complete and flexible set of APIs. And what’s more, sec-api.io uses Elasticsearch® under the hood, meaning we can use Elasticsearch Query DSL to retrieve data from its Query API. This seemed very promising!
I registered for a free tier API key and quickly built a working query in the sandbox. Remember, we’re looking for any instance of Form 8-K that contains item 1.05. So, the query would look like this:
{
"query": {
"query_string": {
"query": "formType:\"8-K\" AND description:\"1.04\""
}
},
"from": "0",
"size": "200",
"sort": [{ "filedAt": { "order": "desc" } }]
}If you're paying attention, you'll notice that the new cyber reporting mechanism uses item 1.05 of Form 8-K, but I'm searching for 1.04. Why? Item 1.05 was introduced in late July 2023 specifically for cybersecurity incidents and is not formally mandated before December 2023, so we can’t expect there to be any results yet.
To prove our concept, we’ll need to use a different item code with more history. How about Item 1.04 Mine Safety – Reporting of Shutdowns and Patterns of Violations?
Mining safety has been a concern for a bit longer than cybersecurity. Tweaking the query to specify item 1.04 returns 200 filings of shutdowns and violations in the mining industry dating back to 2013 — all in nice and easy-to-use JSON. Perfect.
Putting the data to use in Elastic Cloud
I spun up a quick trial instance of Elastic Cloud and used the Data Visualizer to quickly ingest the data and view it. Once I understood what the data looked like and had a better idea of the most important fields, I created a filebeat config and a quick-and-dirty bash script to automate things, making the process repeatable and zero-click.
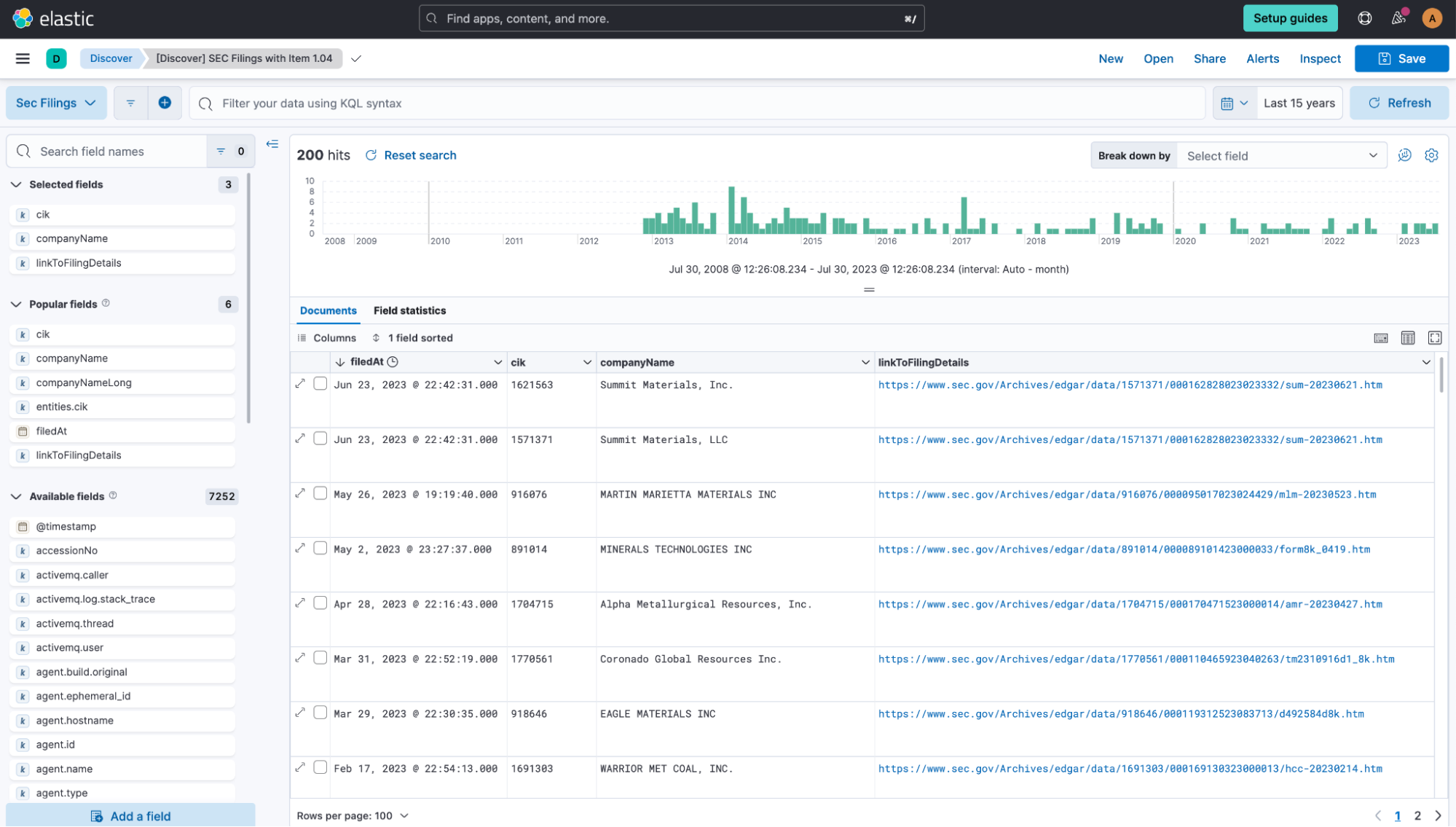
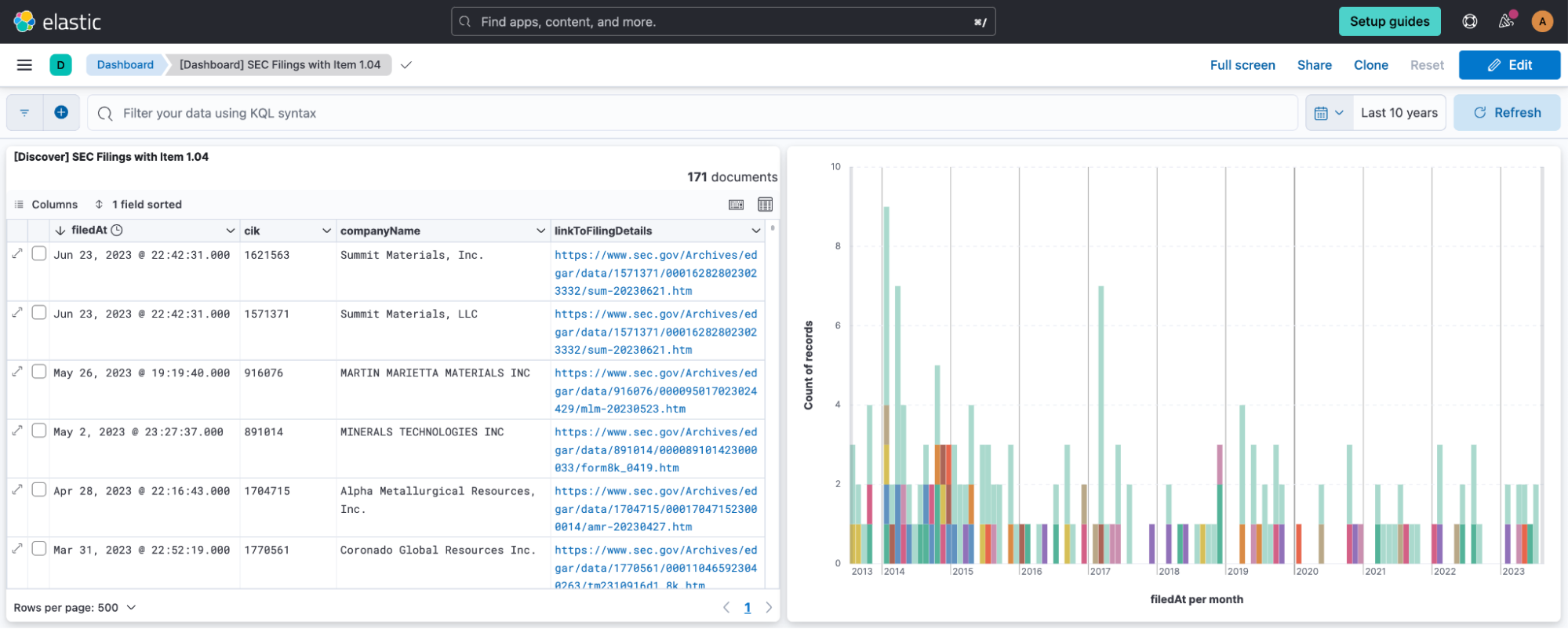
I also created a Kibana® dashboard to show the most recent filings in a table, along with a chart showing all matching filings over the past 10 years stacked by companyName of the most frequently occurring companies.
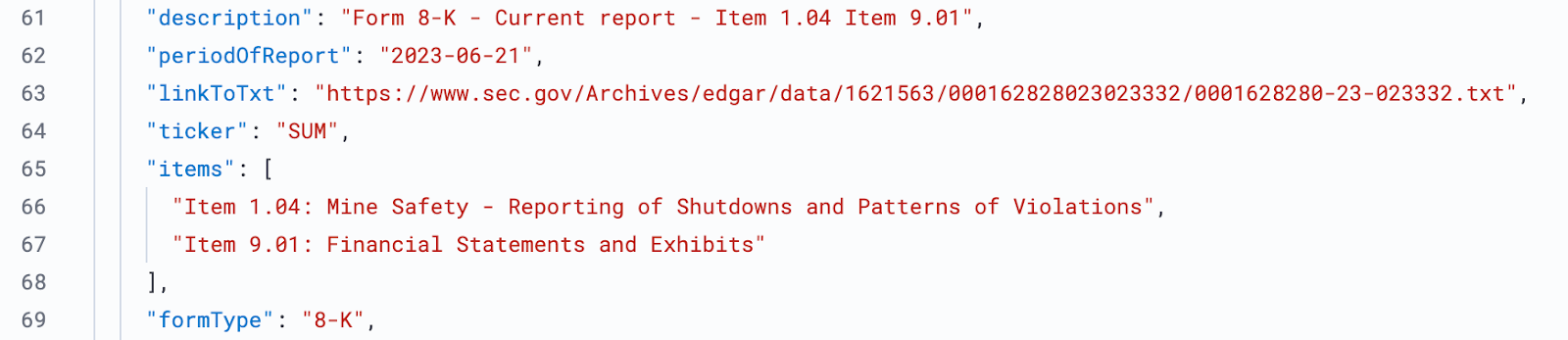
Along with the companyName, there is also a cik field that holds the Central Index Key (CIK). The CIK is a unique identifier for corporations and individuals that have filed with the SEC.
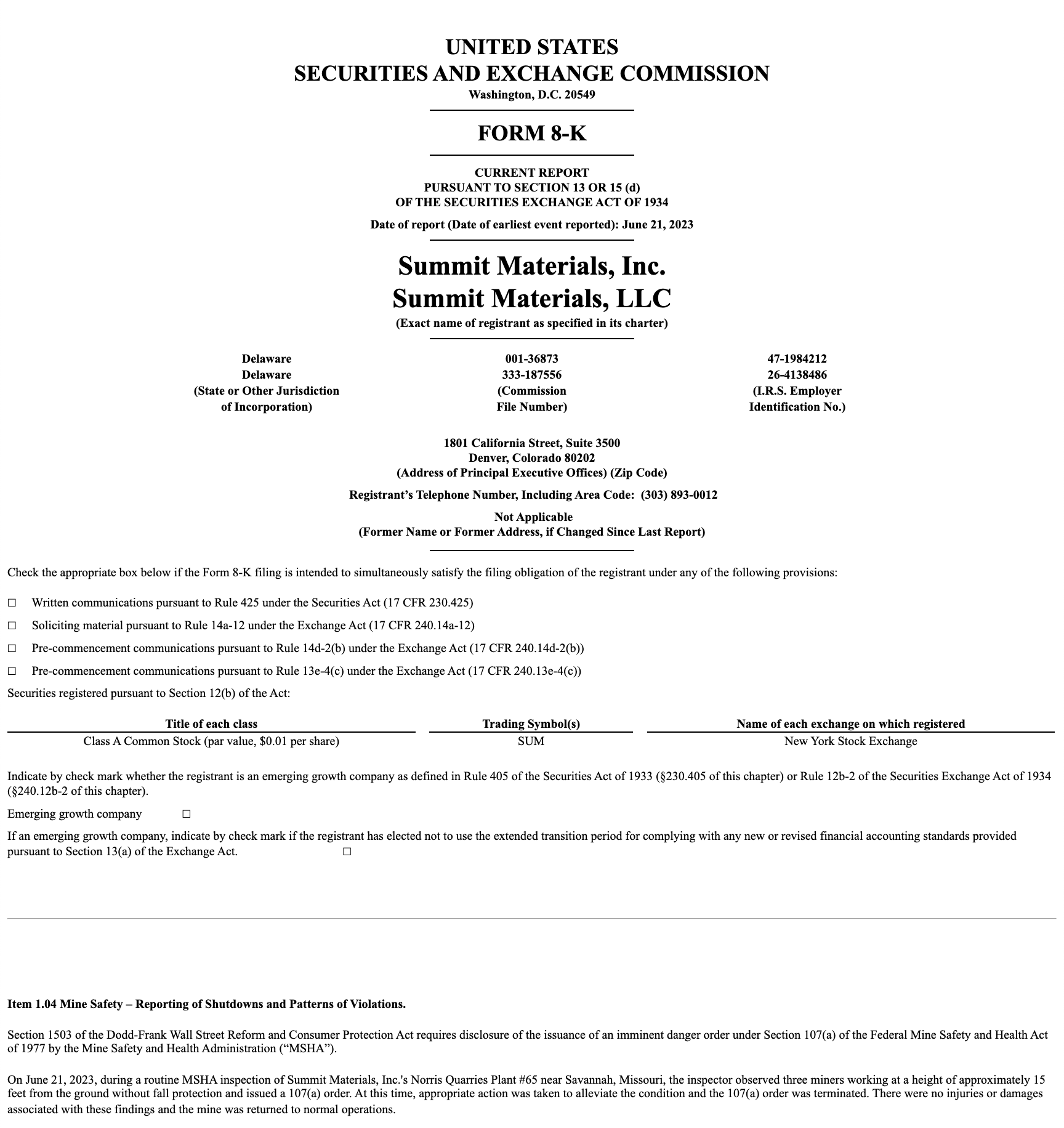
You’ll notice that the linkToFilingDetails field contains a hyperlink that leads to… exactly what you’d expect. Within the filing details, you can read the specifics of the report and the (usually safety related) violation that was reported. In the example below, an inspector observed three minors working at height without adequate fall protection.
With the data already ingested in the Elastic Stack, we could trigger automation to retrieve the file itself, indexing the content of detailed reports for further analysis. Perhaps, we’ll do that as a second step and publish an update to this blog once the new ruling has had time to come into effect and there are cybersecurity incident reports in item 1.05 for us to work with.
In the meantime, we already have a great basis for answering the two questions we asked at the beginning. We’ve surfaced data that would help a CISO to understand which types of security incidents (or mining safety violations) are being reported. We also have a reliable mechanism to trigger alerting when a company that we partner with reports a material security incident. We just need to know who those companies are and have their publicly available Central Index Key (CIK) on file.
Conclusion
This was a short and fun project that showed the power of Elastic Cloud to quickly and easily analyze public data in ways that are useful for CISOs, business leaders, and security teams.
The SEC makes a huge amount of financial and corporate information available, from stock offerings and quarterly results to M&A announcements and insider trades. The approaches used here could be applied to any of this data, using the power of Elastic to provide quick insights and automation.
Want to give this a try? A free tier API key at sec-api.io provides 100 API calls, more than enough for this proof of concept. You’ll need to move to a paid tier if you want to use this in production.
Get your free 14 day trial of Elastic Cloud here.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.