SIEM optimisé par l'IA,
open source et abordable
Elastic SIEM a fait ses preuves dans des milliers d’environnements réels et est alimenté par l’IA, ce qui vous permet de détecter les menaces plus rapidement et de scaler sans dépenses excessives.
Démo guidée
Identifiez les menaces qui se cachent dans vos données
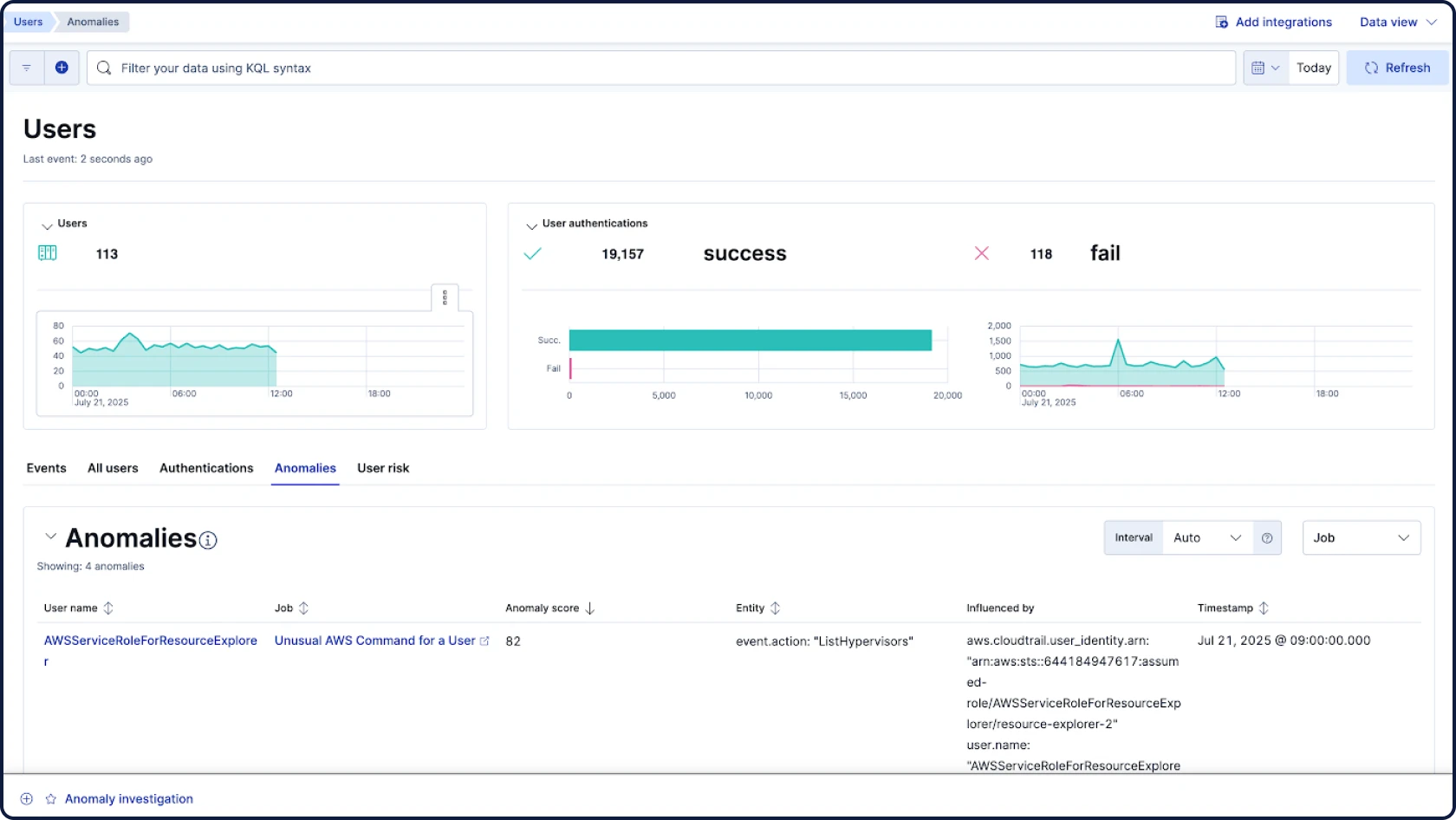
La sécurité commence par les données, et les données sont ce que nous connaissons le mieux. En tant qu'entreprise à l'origine d’Elasticsearch, le premier moteur de recherche et d’analyse open source au monde, notre SIEM offre une détection et une investigation puissantes, pilotées par l’IA, pour toutes vos données de sécurité, à n’importe quelle échelle.
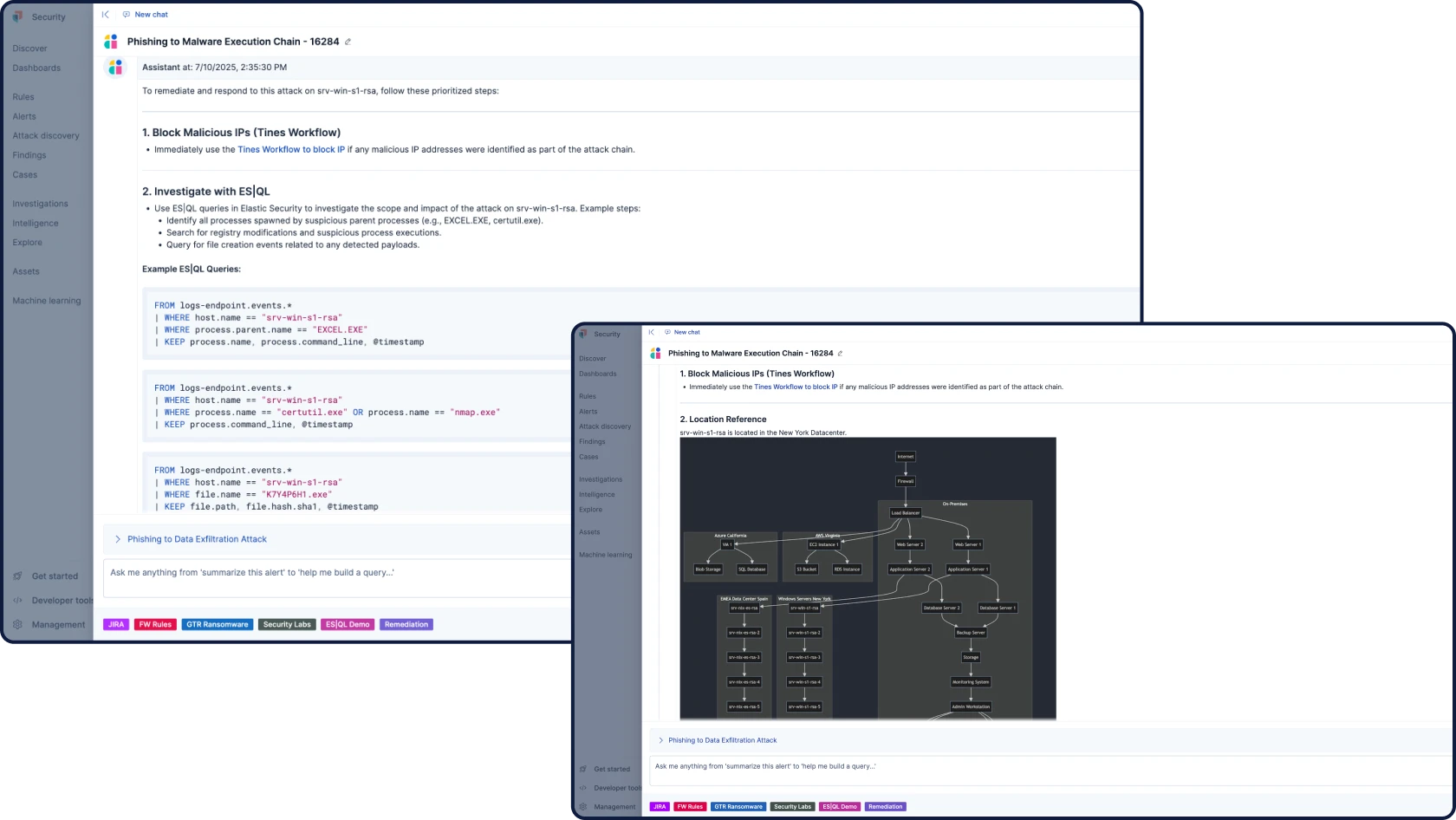
HUNT & INVESTIGATE
La solution SIEM pour le SOC de demain
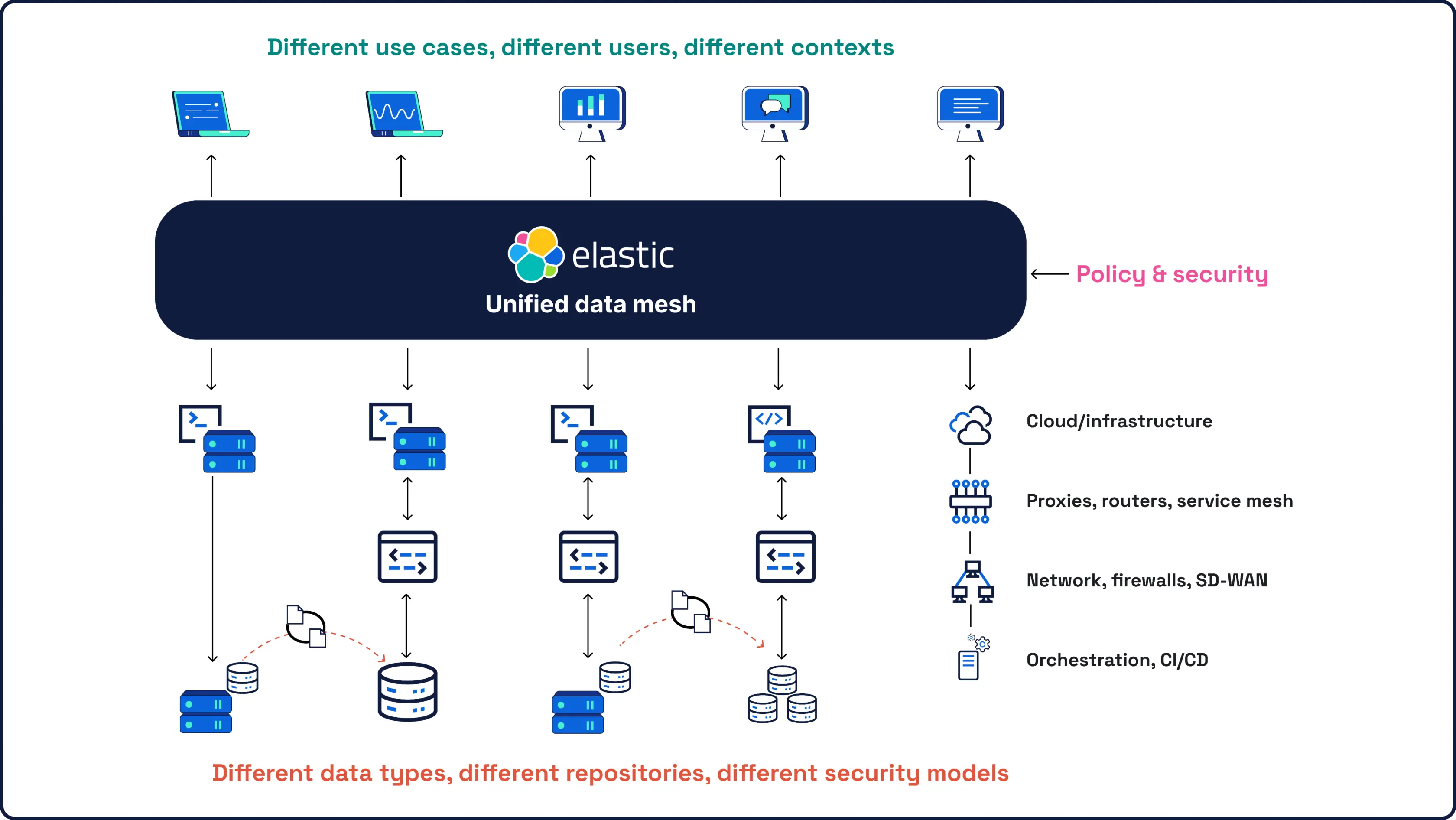
Toutes vos données de sécurité, votre IA et vos enquêtes dans une plateforme ouverte, extensible et scalable
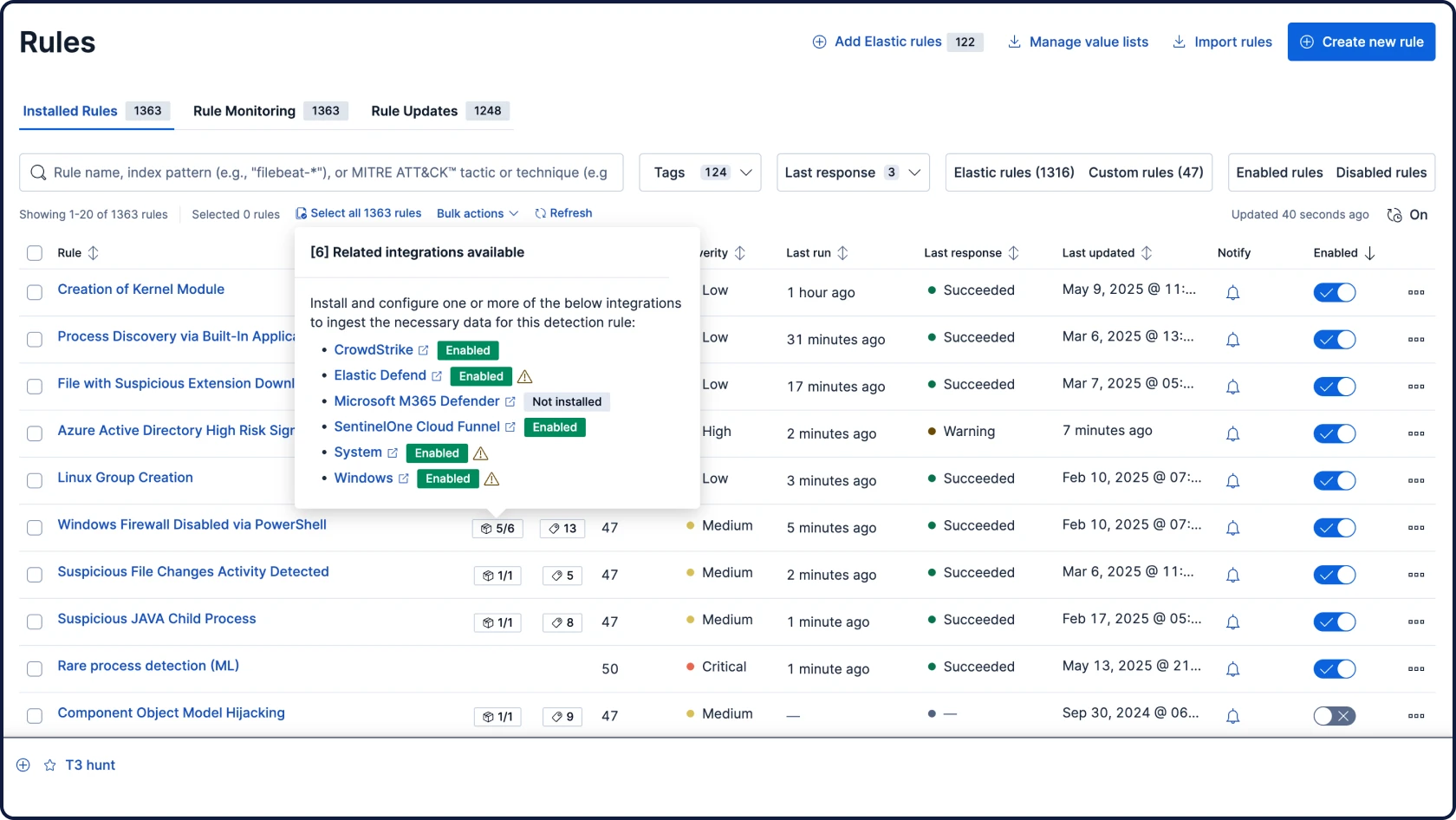
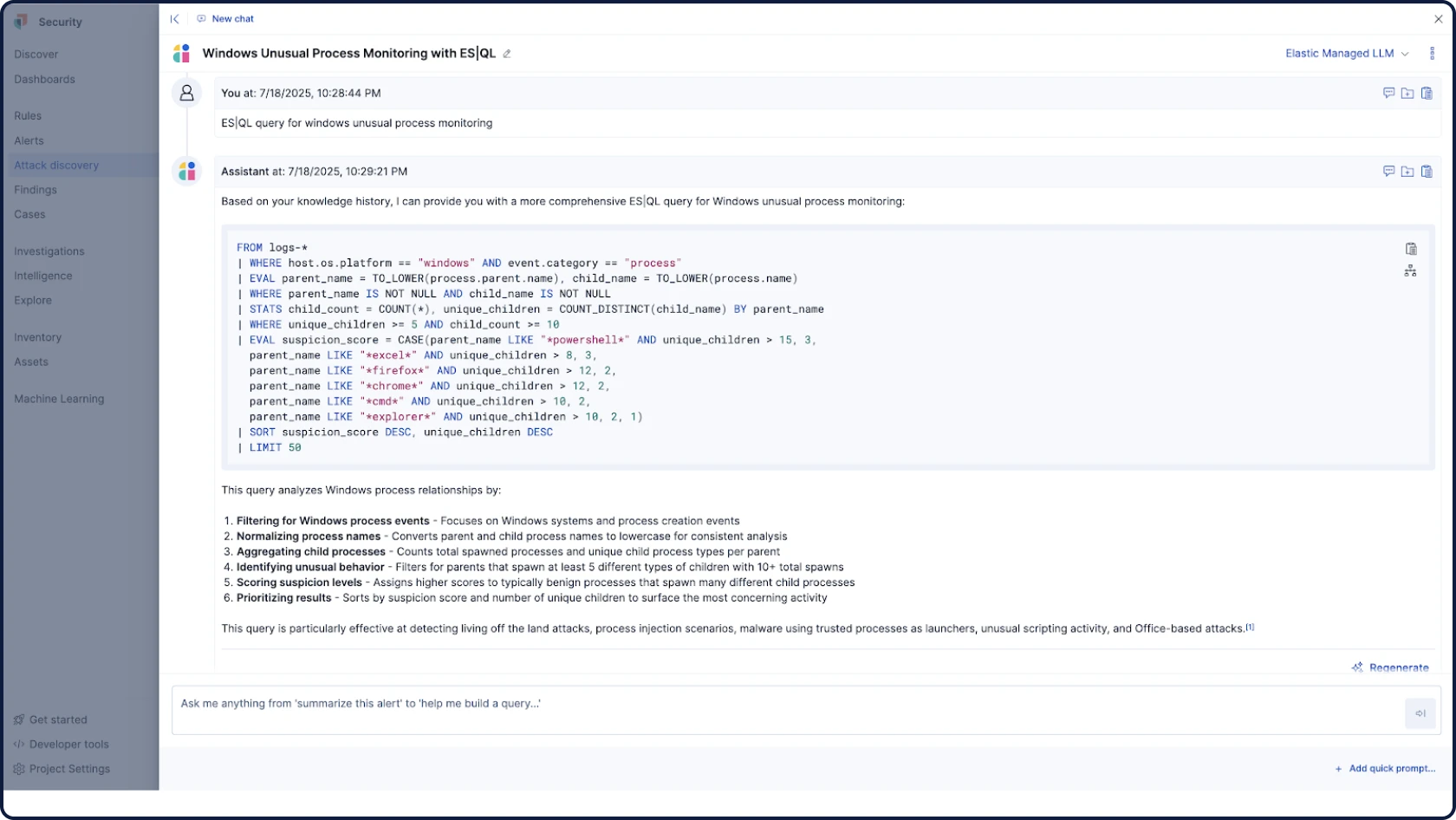
Automatisez vos workflows avec une IA pour la sécurité ancrée, contextuelle et transparente. La fonctionnalité Attack Discovery identifie les comportements et chemins d'attaque réels en corrélant les alertes, tandis que l'Assistant IA répond aux questions et guide les prochaines étapes de l'analyste.

OPTIONS DE PACKAGING
Adoptez tout ou avancez à votre rythme
Notre plateforme de sécurité vous accompagne là où vous êtes, et vous emmène là où les plateformes existantes ne peuvent pas aller.
Elastic Security
Tout ce dont vous avez besoin – SIEM, XDR, sécurité cloud et IA intégrée – dans une seule plateforme unifiée.Aucun SKU supplémentaire, aucun module complémentaire, aucun compromis.Une expérience unique et harmonieuse conçue pour la façon dont les analystes pensent, traquent et répondent.
Elastic AI SOC Engine (EASE)
Un ensemble de fonctionnalités d'IA qui vous permet d'adopter Elastic Security à votre rythme, sans suppression ni remplacement complet. Renforcez vos outils SIEM, EDR et autres outils d'alerte existants avec une IA qui se connecte à vos données et workflows — et passez à la plateforme complète lorsque vous êtes prêt.
Vous êtes entre de bonnes mains
Témoignage client
 Airtel renforce sa cybersécurité grâce aux fonctionnalités d’IA d’Elastic, augmentant l’efficacité de son SOC de 40 % et accélérant les investigations de 30 %.
Airtel renforce sa cybersécurité grâce aux fonctionnalités d’IA d’Elastic, augmentant l’efficacité de son SOC de 40 % et accélérant les investigations de 30 %.Témoignage client
 Sierra Nevada Corporation protège son infrastructure, ainsi que celle d'autres sous-traitants du secteur de la défense, avec Elastic Security.
Sierra Nevada Corporation protège son infrastructure, ainsi que celle d'autres sous-traitants du secteur de la défense, avec Elastic Security.Témoignage client
Mimecast centralise la visibilité, dirige les enquêtes et réduit les incidents critiques de 95 %, transformant ainsi les SecOps à l'échelle mondiale.
Rejoignez la discussion
Rejoignez la communauté mondiale d'Elastic Security, participez à des conversations ouvertes et contribuez au renforcement de notre produit grâce à notre programme de signalement de bugs.
Posez des questions, obtenez des réponses et faites entendre votre voix sur notre forum ouvert.











.jpg)
