AI and the 2025 SIEM landscape: A guide for SOC leaders

Security teams often find themselves having to put out the immediate fires in front of them, but this comes at the expense of implementing a more methodical risk reduction strategy. Attack surfaces are expanding, and new risks emerge with new tech. Modern security operations center (SOC) teams are drowning in alerts, stretched thin by talent shortages, and racing to stay ahead of increasingly sophisticated adversaries.
Security information and event management (SIEM) platforms are instrumental in this fight. They help members of the SOC ingest, analyze, and operationalize security data in real time. Now, artificial intelligence (AI) in cybersecurity is transforming what SIEM can do and how security teams can use it to multiply their defensive efforts.
In this blog, we explore the evolving SIEM landscape, the growing role of AI, key architectural elements, core capabilities, and the benefits and challenges of modern SIEM solutions.
AI’s role in today’s modern SIEM
Cybersecurity is experiencing an AI paradox. AI in the hands of adversaries helps them increase the scale and sophistication of their attacks. But AI in the hands of defenders is improving productivity, reducing mean time to detect (MTTD) and respond (MTTR), and bolstering overall security posture.
SIEM analyzes a wide set of data points and offers security teams a centralized view of their organization’s systems and overall security posture. Integrating AI tools into this process can refine, accelerate, and streamline data collection, workflow, and analysis.
When applied to SIEM workflows, AI is helping security teams relieve traditional burdens through the following capabilities:
Faster analysis: AI in SIEM accelerates threat detection and response by automatically correlating vast amounts of security data, surfacing anomalous patterns, and enabling cybersecurity analysts to prioritize and investigate incidents faster.
Alert distillation: AI reduces alert fatigue by filtering out false positives, prioritizing the most important threats based on risk levels and historical context.
Workflow recommendations: AI generates suggestions for analysts on next steps during investigations, streamlining decision-making processes and generating context-rich summaries.
SIEM content migration: AI facilitates the transition from legacy SIEMs to modern platforms by automating the conversion of existing detection rules and other content.
Custom data integration: AI-driven tools can build custom data integrations in minutes as well as the necessary configuration to ingest data from any REST API. Seamless data ingestion now comes with minimal effort.
These capabilities drive security teams toward increased practitioner productivity, accelerated detection and response, and overall risk reduction.
Understanding SIEM architecture and components
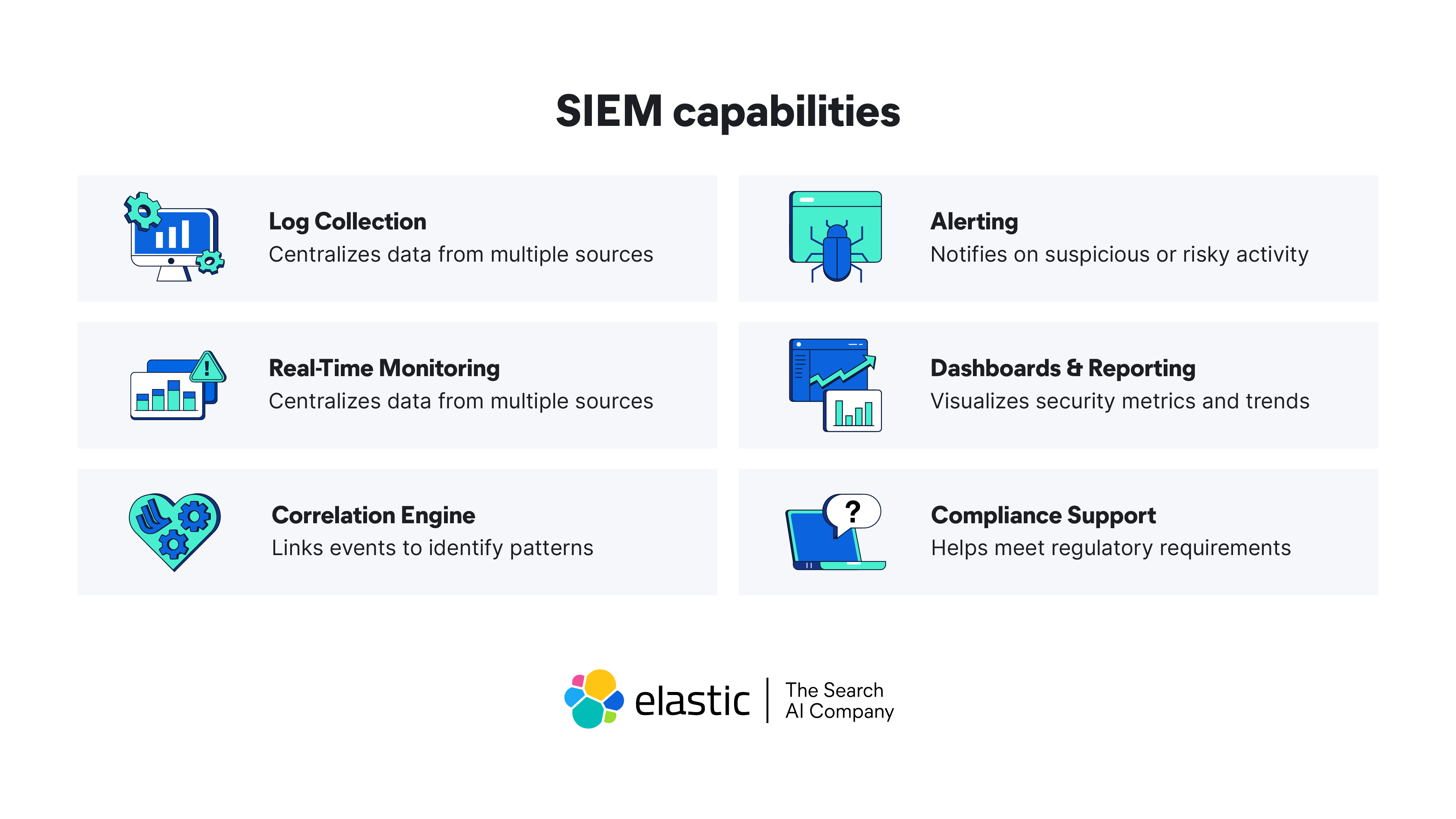
At the heart of any SIEM platform are several core functionalities that enable SOC teams to monitor, detect, and respond to security incidents.
Log collection
SIEM solutions will ingest logs from applications, users, cloud workloads, networks, endpoints, and security software and hardware.
Data normalization
Normalization is the process of integrating diverse data sources into a common schema for standardized analysis.
Automated detection engine
A SIEM can streamline events across sources to detect patterns indicative of threats.
Real-time monitoring and alerting
With real-time monitoring and alerting, security teams gain immediate visibility into suspicious activity, allowing for rapid incident response and containment. Alerts and notifications surface any anomalous patterns detected with an associated severity score for further triage and resolution.
Compliance and reporting
SIEMs also provide robust reporting features to support regulatory compliance with frameworks like HIPAA, PCI-DSS, and GDPR. Dashboards offer real-time visibility into security data and incidents through customizable visualizations. These reporting tools not only help demonstrate adherence to standards but also enable continuous security posture assessment. They also help security teams meet regulatory requirements, such as GDPR, HIPAA, PCI-DSS, and ISO 27001.
Security integrations
A SIEM solution can be connected with tools like security orchestration, automation, and response (SOAR), cloud detection and response (CDR), endpoint detection and response (EDR), identity and access management (IAM), and threat intelligence platforms (TIP).
Incident response modules
Facilitate alert triage, investigation, and remediation through built-in workflows or external SOAR platforms.
Correlation and analytics
After collecting and normalizing logs that establish a baseline of normal organizational activity, SIEM correlation identifies anomalous patterns across events, which is key to detecting complex threats.
SIEM deployment
Today’s most versatile solutions support a wide range of deployment types from SIEM-as-a-service, self-managed, multi-cloud, hybrid, or on-premises architectures.
Cloud-native SIEMs offer scalability, flexibility, and real-time analytics with minimal infrastructure overhead, making them ideal for cloud-based businesses. Hybrid deployments combine the benefits of cloud agility with the control of on-premises systems, which suits organizations transitioning to the cloud or operating in regulated environments. Meanwhile, on-premises SIEMs continue to be a go-to for industries with strict data residency requirements, offering maximum control and security.
Key SIEM capabilities
SIEM analyzes a wide set of data points and offers security teams a centralized view of the organization’s systems and overall security posture. Integrating AI tools into this process can refine, accelerate, and streamline data collection, workflow, and analysis.
Modern SIEM solutions are equipped with advanced features, such as:
AI-driven threat detection that uses machine learning models to identify sophisticated attacks
User behavior analytics (UBA) that establishes behavioral baselines for users and systems to identify anomalies indicating insider threats or account compromise
Integration with SOAR platforms that allows for automated playbooks and response actions, accelerating incident resolution and reducing analyst workload
Integrations with XDR, endpoint, and cloud security that provide rapid response and threat mitigation
Challenges and limitations of legacy SIEMs
Older SIEMs can come with limitations, leading many teams to pursue SIEM replacement. These challenges include:
High operational costs: Licensing, storage, and compute expenses can add up quickly with legacy SIEM vendors.
Scalability issues: Older platforms can’t keep pace with modern data volumes and diverse IT environments.
Integration hurdles: Legacy systems may not have readily available integrations with modern cloud-based security tools.
False positives: A lack of context-aware analytics often results in an overwhelming volume of irrelevant alerts.
Complexity: Configuration and tuning traditionally require specialized skills and extensive effort.
- Learning curve: Many organizations struggle to find and retain qualified analysts to manage SIEM operations.
How AI-driven SIEM benefits SOC teams
The AI capabilities that are now integrated into SIEM solutions can significantly enhance operational efficiency and security posture through improved threat detection, faster investigation times, and automated responses. Proactive, AI-enhanced threat detection can help stop the proverbial fires before they spark.
Enhanced threat detection
AI-driven SIEM solutions accelerate threat detection by analyzing vast amounts of data in real time. These solutions correlate that data against the latest threat intelligence to spot new threat types and surface high-risk anomalies that might otherwise go unnoticed.
Faster investigation
AI propels investigations, reducing dwell time. It surfaces relevant insights from the deluge of data generated by today’s ecosystems, helping analysts get answers quickly.
Automated response
Manual response to alerts can leave organizations exposed as security teams scramble to balance conflicting priorities. AI-powered SIEM enables guided responses and automated workflows against different threats.
Compliance support
Automated creation of data integrations, detection rules, dashboards, and reports streamlines adherence to regulations by making it easier to ingest data from critical applications, systems, and infrastructure — no matter how custom or complex.
Enhanced analyst productivity
SOC teams supported by AI in their SIEM can surface the alerts that matter most, easily import custom data types, and guide workflow suggestions. By doing so, teams have more time to focus on strategic initiatives.
SIEM use cases
Aside from being key to cybersecurity management, modern SIEMs are vital for numerous cybersecurity and compliance scenarios.
Threat hunting
AI-driven SIEMs empower analysts to identify threats more efficiently by acting as a threat hunter’s sidekick — it’s at-the-ready for natural language inquiries into events, data, and context and presents findings quickly and intuitively.
Continuous security monitoring
Continuous monitoring in security proactively provides the real-time status of your data from across your attack surface. This practice eliminates blind spots, empowers practitioners, and reduces risks.
Investigation and response
AI embedded into SIEM helps security teams mitigate threats faster during investigation and response, enhancing cyber resilience.
Compliance
By streamlining the onboarding of custom data sources and creating detection rules, dashboards, and reports, AI-driven SIEMs help organizations remain compliant.
Insider threat detection
By flagging unusual behavior from users with elevated privileges, SIEMs help security teams detect insider threats.
AI-driven SIEM in action by industry
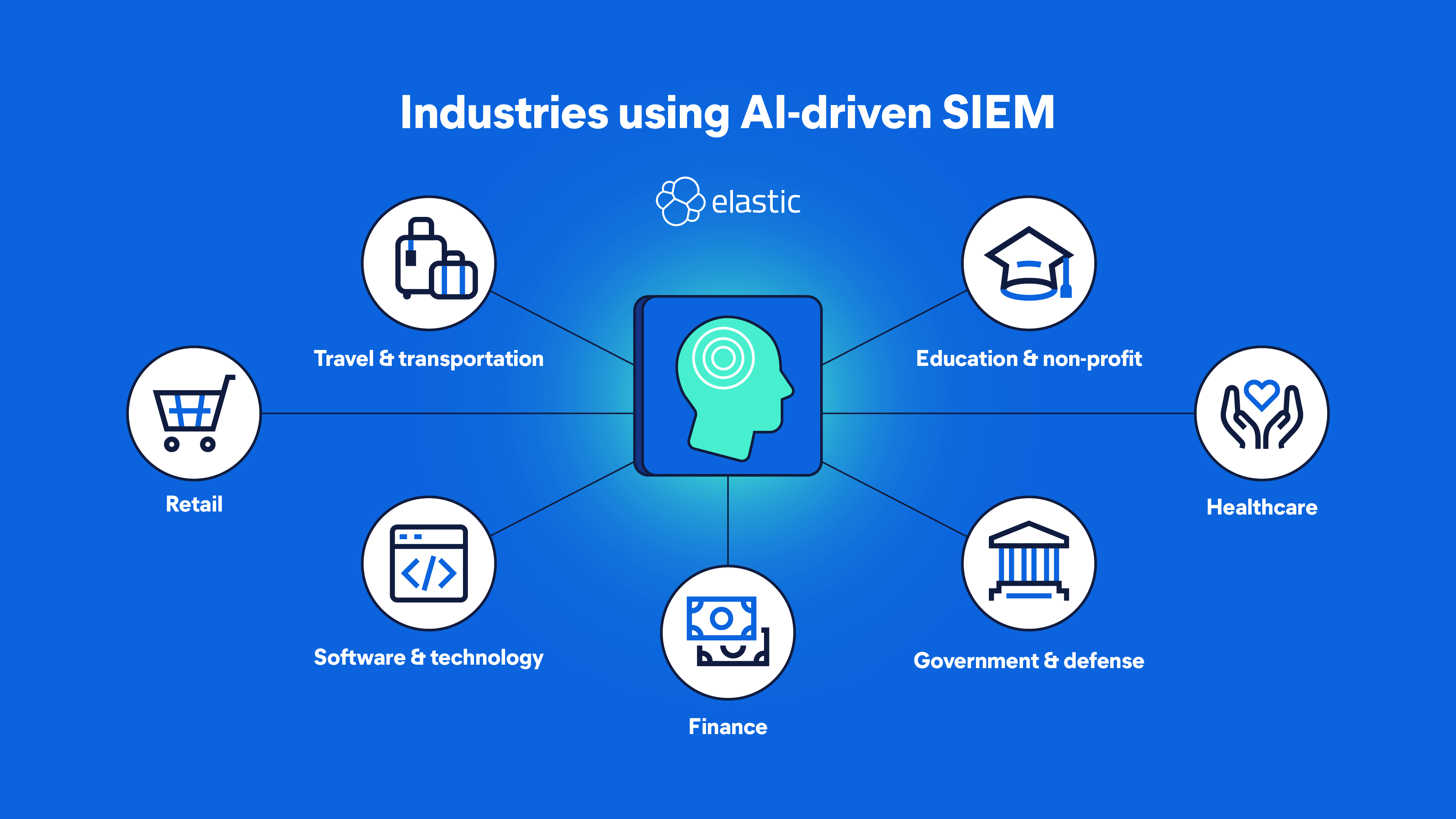
The benefits of AI-driven SIEM apply to all industries.
Travel and transportation
The travel industry and transportation logistics systems rely on complex digital infrastructure.
Bolt now protects its super-app and users with Elastic Security on Elastic Cloud, delivering unified data protection and operational efficiency.
With Elastic, Bolt boosted data protection, reduced maintenance overhead by 75%, and enhanced user confidence, safeguarding millions of journeys while accelerating its move to scalable, AI-powered security in the cloud.
Software and technology
The cybersecurity industry depends on advanced monitoring systems to stay ahead of evolving cyber threats.
For example, when managed security services provider Proficio wanted to optimize its threat detection and response, it turned to Elastic’s AI-driven SIEM solution. By integrating Elastic Security and Elastic AI Assistant, Proficio gained real-time visibility and automated threat detection. This enabled a 34% reduction in investigation time, improved response times by 75%, and decreased false positives, leading to significant operational efficiency gains. As a result, Proficio saw a 60% growth in its business while reducing investigation costs to less than half a cent per alert, saving an estimated $1 million over three years.
Education and nonprofit
Universities rely on flexible, cost-efficient security systems to protect vast and complex networks.
When the University of York needed a more agile and cost-effective SIEM, it turned to Elastic Security. With Elastic’s AI-driven detection and response capabilities, the university reduced query times from hours to seconds, streamlined licensing costs, and enabled its small team to do more with built-in automations and generative AI (GenAI)-powered insights.
Government and defense
Aerospace and defense contractors must meet strict security and compliance standards without sacrificing speed or scale.
When the Sierra Nevada Corporation (SNC) needed to bring its security operations in-house and scale to ingest 10x more data, it chose Elastic’s AI-driven SIEM. With Elastic Security, SNC cut query times from minutes to seconds, launched a revenue-generating managed service, and accelerated threat detection with powerful automation and anomaly detection all on a unified platform built for growth.
Retail
Security is essential to create secure and seamless customer experiences. The Hut Group (THG) protects millions of ecommerce customers by centralizing security with Elastic Security for SIEM, cutting response times by 60% and triage time in half.
With automation, machine learning, and searchable snapshots in Elastic Security, THG slashed storage costs by 60%, enhanced fraud detection, and improved customer experiences.
Finance
Financial institutions can use AI-driven SIEM to detect account takeover attempts and mitigate them in real time with UBA.
Healthcare
Hospitals, clinics, and insurance companies can use SIEM for HIPAA compliance to detect unauthorized access to patient records.
The future of SIEM in cybersecurity
The future of SIEM is linked closely with the future of AI. Security teams are looking for solutions that adapt and scale with their environments and help them keep pace with the fast-changing threat landscape. That’s where AI-driven SIEM comes into play.
Cloud-native SIEMs will continue to gain ground, offering the flexibility, scalability, and simplified operations that modern SOCs require. AI will enable predictive security analytics, continuously learning from your environment and helping teams make smarter decisions faster.
AI-driven security analytics with Elastic Security
Elastic Security provides a SIEM solution that is fast, flexible, and scalable. Backed by AI-powered analytics, it delivers real-time visibility across your entire attack surface from endpoint to cloud and beyond.
With flexible deployment options and seamless integration with the tools you already use, Elastic empowers SOC teams to spot threats in high fidelity, gather relevant context and insights quickly, respond faster, and ultimately stay ahead of evolving threats.
Explore additional SIEM and AI resources
- Elastic named a Leader in The Forrester Wave™: Security Analytics Platforms, Q2 2025
- AI for SecOps
- AI adoption in security: Top use cases and mistakes to avoid
- 2025 SIEM buyer’s guide
- Replace Splunk with Elastic for logs, security, and observability
- Learn how to replace your SIEM
- Access next-level problem-solving with Elastic AI Assistant
- Tracing history: The generative AI revolution in SIEM
- Understanding the CISO: Role, skills, and security impact
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos, or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.