SOC analyst vs. security analyst: What’s the difference?

A security operations center (SOC) analyst enhances your security posture by defending the organization against cybersecurity threats. Responsible for monitoring, detecting, investigating, and responding to cyber threats, the SOC analyst is the first line of defense in keeping the organization’s IT ecosystem secure when an incident arises.
A security analyst, similar to a SOC analyst, is responsible for proactive defense and security posture. However, security analysts tend to have a more strategic, preventive focus and may or may not work within the SOC.
With such critical responsibilities, what does it take to become a SOC analyst or security analyst? Let’s explore the job, required skills, and the career path of both.
What is a security analyst?
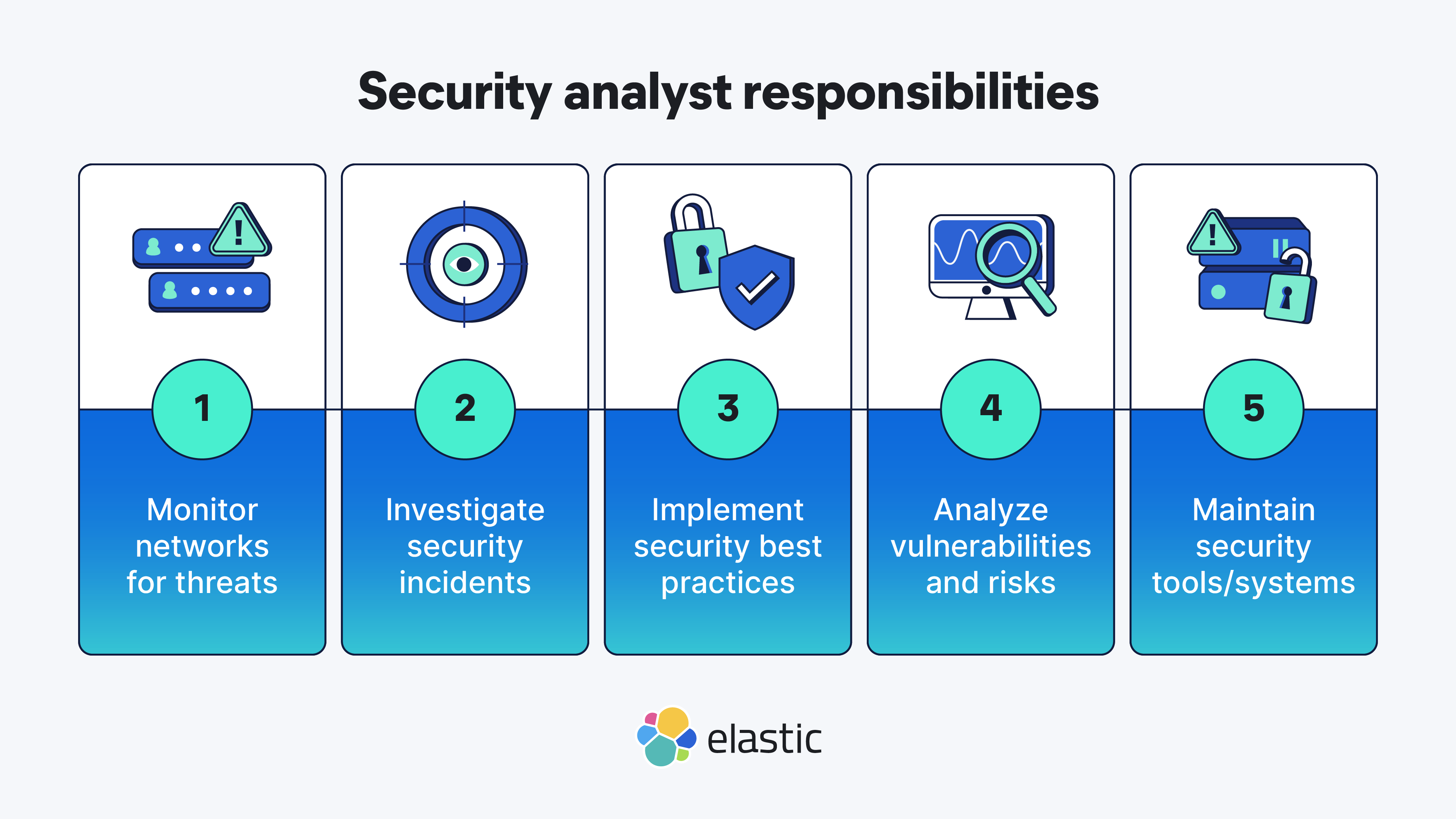
A security analyst is an expert who finds and fixes problems in security systems and networks. For many, working in cybersecurity is aspirational. The security analyst role was ranked #6 in 2025’s 100 Best Jobs.1 Though challenging and selective, the security analyst job promises competitive pay, job security, and growth opportunities. It requires both technical and problem-solving skills while offering a chance to make a difference.
Sounds too good to be true? The security analyst role comes with a big responsibility to your team and your SOC. But what exactly are their responsibilities?
Monitoring systems and networks: Security analysts use continuous profiling to monitor network traffic, log files, and other systems for suspicious activity. They analyze data to identify potential security threats and vulnerabilities. They perform regular vulnerability assessments, risk analysis, and penetration testing.
- Investigating incidents: Security analysts respond to security incidents and data breaches, investigate, and analyze their root cause. They find ways to contain the damage. They continuously research and analyze emerging threats to stay up to date on the latest security trends.
Implementing security measures: Security analysts create and maintain documentation, such as incident response and recovery plans. They install and maintain security software and hardware, managing user access to systems and data. They also have to communicate security risks and recommendations to other team members and stakeholders.
What is a SOC analyst, and what are SOC analyst levels?
SOC analysts are responsible for real-time monitoring across networks. They analyze security events to identify, investigate, and resolve security incidents and help proactively locate hidden threats. As a rule, not every security analyst is responsible for all of these tasks.
Usually, SOC analysts work as part of a larger team within the SOC. This team includes a SOC manager, security engineers, security administrators, and other SOC analysts divided into three tiers.
Tier 1 SOC analysts
Tier 1 SOC analysts are entry-level SOC analysts. They are the initial responders to security alerts and potential threats, responsible for real-time monitoring of networks and systems. They should be able to triage alerts, enrich alert data with additional context, and document their findings.
These SOC analysts follow established protocols to identify, evaluate, and respond to security threats. They are also responsible for managing SOC monitoring and reporting security tools, such as security information and event management (SIEM) or extended detection and response (XDR).
Tier 2 SOC analysts
Tier 2 SOC analysts provide incident response, handling the identification, investigation, and resolution of security incidents. Usually, these are more senior SOC analysts with the experience to work on more time-sensitive and challenging issues.
When Tier 1 analysts escalate cyber attacks, Tier 2 SOC analysts decide how to respond. They conduct forensic analysis, implement containment and remediation strategies, and help to coordinate incident response across security teams.
Tier 2 security analysts should have the depth of knowledge to develop custom detection rules, correlate events to gain valuable context, and understand the scope of a potential attack. They should be proactive in helping to improve and automate security workflows. They also often act as mentors for Tier 1 SOC analysts.
Tier 3 SOC analysts
The most experienced SOC analysts are threat hunters who proactively search for hidden threats within the organization's systems and network.
Tier 3 SOC analysts look for vulnerabilities, study the latest cybersecurity trends and threat intelligence, and develop custom detection mechanisms for emerging threats. As experts in forensic analysis, reverse engineering, and vulnerability assessments, they conduct thorough investigations into more sophisticated attacks.
Tier 3 security analysts are also leaders. They provide technical leadership and mentorship to all SOC analysts while collaborating with threat hunters in other organizations.
Required skills for SOC analysts
There’s no single set of required skills for SOC analysts. In fact, even a background in cybersecurity isn’t a requirement. Of course, some technical experience, such as networking or software development, is usually preferred for those interested in this type of job. But a SOC analyst job is equal parts leadership and problem-solving.
Typically, successful SOC analysts have a combination of skills in a few of these areas:
SOC tools: In-depth knowledge of SIEM platforms is crucial, but understanding other security tools (including security orchestration, automation, and response (SOAR), XDR, vulnerability scanners, and log monitoring) can also be helpful.
Network security: A solid grasp of networking fundamentals (TCP/IP, HTTP, DNS, and SSL), firewalls, VPNs, and intrusion detection and prevention systems (IDS/IPS) is essential.
Cloud security: Familiarity with major cloud providers and the basics of cloud security is important for securing cloud environments.
Threat analysis and intelligence: Familiarity with MITRE ATT&CK® and the Cyber Kill Chain frameworks and a threat intelligence platform (TIP) is a must.
Threat hunting: Responding to incidents involves locating and identifying vulnerabilities, triaging alerts, investigating the root cause, containing the damage, restoring affected systems, and performing digital forensics.
Scripting and reverse engineering: Automating workflows and repetitive tasks is done using one of the scripting languages (e.g., Python), while reverse engineering involves an understanding of debugging tools, disassemblers, and internal system tools.
Security compliance: Most organizations are required to comply with a combination of industry-specific, government-mandated, or international cybersecurity regulations, including NIST 2.0 framework, ISO/IEC 27001, the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the CIS Critical Security Controls (CIS Controls).
Soft skills: Problem-solving, communication, and analytical skills are essential for this role.
Replace legacy SIEMs with AI-driven security analytics.
While there are some crucial ones, SOC analysts can pick up many of these skills once on the job.
There’s also a range of specialized certifications that can help a security analyst grow and expand their skill set. For example, for aspirational tier 1 SOC analysts and those looking for their first job in the industry, there are the EC-Council's Certified SOC Analyst (CSA), GIAC Information Security Fundamentals (GISF), and CompTIA's Security+. For aspiring security analysts with at least five years of experience, there’s a more advanced Certified Information Systems Security Professional (CISSP) certification.
SOC analyst skills and tools checklist
| Skill/Tool | Importance level | Notes |
| SIEM tools (Elastic Security) | ⭐⭐⭐⭐⭐ (Essential) | Required for log analysis and threat detection |
| Incident response & forensics | ⭐⭐⭐⭐⭐ (Essential) | Ability to investigate and contain security incidents |
| Log analysis & correlation | ⭐⭐⭐⭐⭐ (Essential) | Ability to analyze system, application, and security logs |
| Threat intelligence analysis | ⭐⭐⭐⭐ (Important) | Understanding threat actors, TTPs (Tactics, Techniques, Procedures) |
| Network security | ⭐⭐⭐⭐ (Important) | Monitoring and analyzing network traffic for threats |
| Endpoint security | ⭐⭐⭐⭐ (Important) | Protecting and monitoring endpoints for security threats |
| Scripting & automation (Python, PowerShell, Bash) | ⭐⭐⭐⭐ (Important) | Automating repetitive tasks in SOC workflows |
| SOAR platforms | ⭐⭐⭐⭐ (Important) | Automating security operations workflows |
| Compliance & regulations (NIST, GDPR, CIS Controls) | ⭐⭐⭐⭐ (Important) | Ensuring security policies align with industry regulations |
| Malware analysis basics | ⭐⭐⭐ (Nice to have) | Understanding common attack vectors and analysis tools |
| Cloud security (AWS, Azure, Google Cloud) | ⭐⭐⭐ (Nice to have) | Understanding cloud security risks and tools like CSPM |
Security analyst career path and salary expectations
Typically, security analysts begin their career path in entry-level IT or cybersecurity job roles. As they develop their skill sets, pass certifications, and continuously learn, they advance to junior (or tier 1) security analysts. Then many progress through the tiers into management positions or other cybersecurity roles, such as security engineering and architecture.
Security analysts’ salaries depend on the role, responsibilities, industry demand, location, and experience. According to Glassdoor, security analysts’ salaries range from approximately $60,000 for entry-level positions up to $200,000 for more senior roles.2
Challenges SOC analysts face
With a job so rewarding and critical for an organization, it’s no surprise that SOC analysts face many challenges.
1. Alert fatigue: SOC analysts are overwhelmed by the volume of alerts, including false positives, generated by security tools. All these alerts require attention, triage, and intervention, potentially leading SOC analysts to overlook critical threats.
The potential solution: AI-driven security analytics significantly reduces the noise and prioritizes critical alerts, saving security analysts time and effort.
2. High stress levels and burnout: SOC analysts operate in a high-pressure environment, amid constant demands to respond to yet another threat. Then, there’s the added pressure of a dynamic threat landscape and the need to keep up with emerging and advanced threat actors, new vulnerabilities, and attack techniques.
The potential solution: An AI Assistant can help security analysts gain quicker insights and analysis and
3. Fear of being replaced by AI: As SOC analysts begin to rely on AI to make their jobs easier, many question whether their jobs will become obsolete. An AI Assistant can already triage alerts and monitor networks for threats more effectively than a junior security analyst. What will happen tomorrow?
The potential solution: AI won’t replace SOC teams, but it will fundamentally transform the role of tier 1 SOC analysts. Analysts will be able to forget about time-consuming manual tasks and get AI help in elevating their skills, so they can focus on more rewarding investigations and threat hunting.
How to become a SOC analyst
There are many ways of becoming a SOC analyst. The traditional route is a bachelor’s degree in computer science to an entry-level job. However, others start in IT or other cybersecurity teams. Some nontraditional hires get certifications to make their way into the industry.
Even with a degree or some IT experience, many hopeful SOC analysts turn to certifications for supplemental cybersecurity knowledge.
The most important factor for aspiring SOC analysts or those hoping for a promotion is practical experience. Finding a mentor or applying for internships can help to gain some hands-on experience.
Why SOC and security analysts choose Elastic Security for AI-driven security analytics
Cybersecurity professionals choose Elastic Security for AI-driven security analytics to help consolidate data, automate tasks, and gain actionable insights, ultimately improving their organization’s security posture and reducing costs.
Elastic’s Search AI Platform and features like Attack Discovery and AI Assistant streamline triage, investigation, and response, empowering SOC analysts to focus on the most critical threats, avoid burnout, and boost their productivity.
Learn how Elastic Security can help your organization.
Explore more resources for SOC & security analysts
Sources:
1. U.S. News & World Report, “100 Best Jobs,” 2025.
2. Glassdoor, “How much does a Soc Analyst make?,” 2025.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos, or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.