Cyber threats explained: How to safeguard your enterprise

Cyber threats 101
Cyber threats (also known as cybersecurity threats) are events, actions, or circumstances that have the potential to negatively impact an individual or an organization by taking advantage of security vulnerabilities. Cyber threats can affect the confidentiality, integrity, or availability of data, systems, operations, or people’s digital presence.
Cybersecurity threats are constantly evolving, with the rapid adoption of artificial intelligence (AI) further exacerbating their scale and sophistication. Cybersecurity awareness is critical for preventing these threats from turning into full-blown cyber attacks. When security teams are knowledgeable about the different types of cyber threats, they can prevent, detect, and respond more holistically and effectively.
Importance of cybersecurity
An effective cybersecurity practice ensures the confidentiality, integrity, and availability of an organization’s data, systems, and networks by prioritizing the mitigation of cybersecurity risks. By recognizing various threat types and implementing strategies to prevent them from becoming breaches, an enterprise can protect its sensitive information, reputation, and profits. There’s a lot at stake — it’s estimated that the cost of cybercrime will continue to grow annually and could reach as high as $15.63 trillion by 2029.1
Overview of common cybersecurity threats
Nation states, terrorist groups, criminal organizations, or individual hackers can all be perpetrators of cyber threats. Cybersecurity threats can be:
External (i.e., malicious attack) or internal (i.e., insider threat)
Intentional (i.e., hacking) or accidental (i.e., sensitive data sharing)
In the past, security teams were concerned with simple viruses that infiltrated a computer, causing minor damage. However, today’s world grows ever more interconnected, resulting in widespread implications for cybersecurity threats. Sophisticated attacks like malware, ransomware, and more can grind the operations of multinational enterprises and even entire countries to a halt. Security teams are now tasked with finding vulnerabilities and protecting much larger attack surfaces that encompass distributed systems, Internet of Things (IoT), mobile devices, and other vectors.
Malicious actors design some cyber attacks to steal data, sensitive information, or secrets for financial gain, while others are designed to cause reputational harm for political or personal gains.
Types of cybersecurity threats
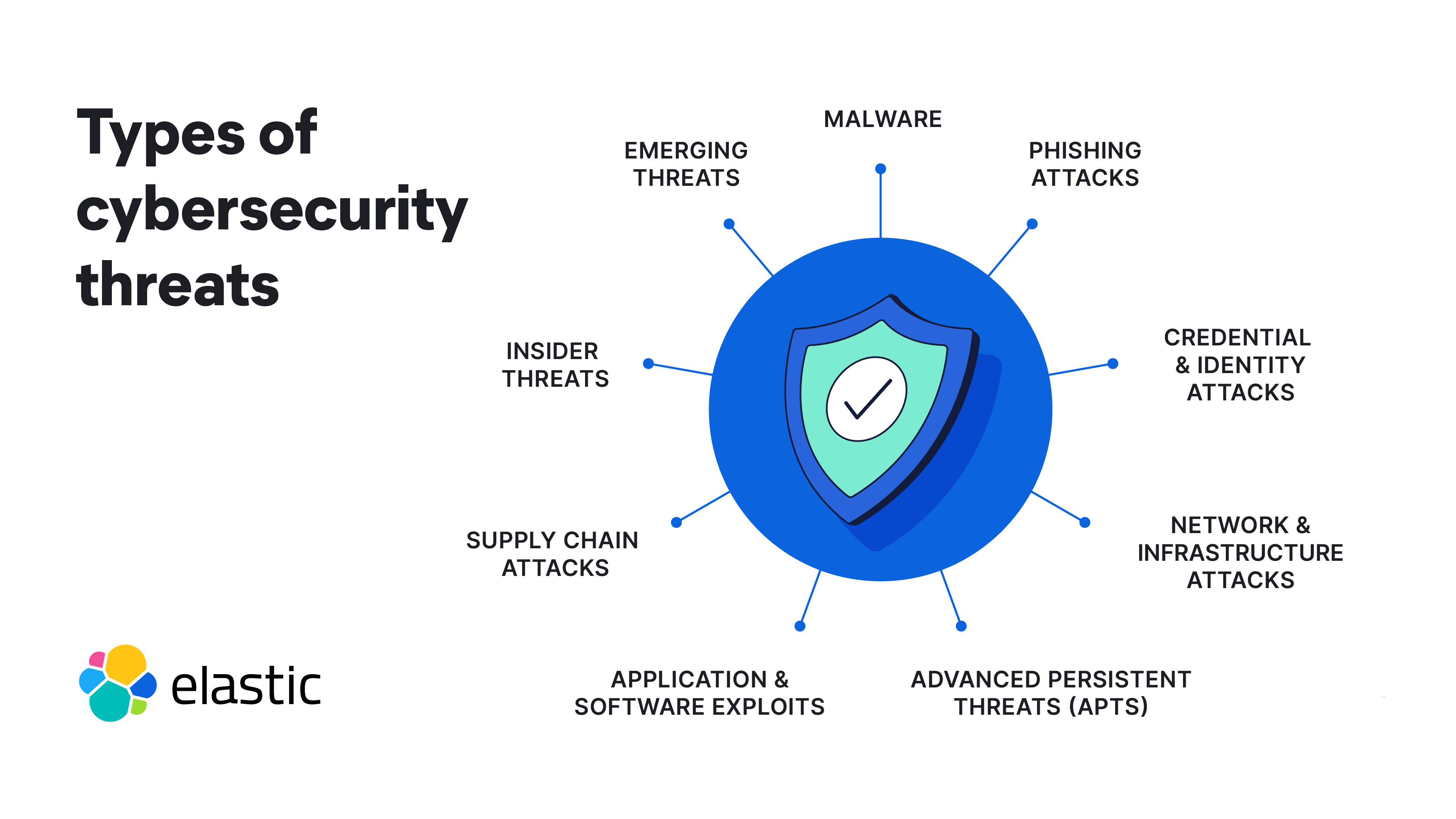
Organizations must be prepared to face increasingly sophisticated cybersecurity threats that exploit weaknesses and vulnerabilities across a growing attack surface. Here are some common cybersecurity threat types:
Malware
Malware, or “malicious software,” is a broad threat category that aims to damage or disrupt systems, steal sensitive information, or enable unauthorized access to networks.
Viruses are among the oldest types of malware. Viruses execute malicious code that spreads from computer to computer. Viruses can disrupt systems’ operations and cause data loss.
Worms self-replicate, spreading to other devices using network protocols, without human intervention. Malware worms evade detection by using techniques such as polymorphism, behavior mimicking, and encryption. Some worms also use machine learning to predict and counteract intrusion detection systems.
Trojan horses hide within legitimate software or are disguised as useful files, attachments, or applications. In particular, attackers are increasingly using compromised websites and fake links, a type of social engineering, to deliver Trojan payloads. Once downloaded, a Trojan gains control of the victim’s device, system, or network. According to the 2024 Elastic Global Threat Report, Trojans account for 82% of all malware types observed. To dig even deeper, banking and “stealer” trojans currently dominate this threat category. They are designed to harvest sensitive data such as logins or financial information, and they continuously evolve to avoid detection.
Cryptomining is also known as cryptojacking. Cryptomining malware hijacks a victim’s computing resources to mine cryptocurrencies. This malware enables threat actors to generate cash in secret, over a long period of time.
Ransomware is an advanced malware that is designed to hold a victim’s information hostage or prevent use of a system until they pay a ransom to unlock it. Usually, threat actors encrypt certain file types and then force victims to pay for a decryption key. In 2024, according to Chainalysis, victims paid approximately $813.55 million to ransomware attackers.2 The latest ransomware operations are fast and adaptive, target supply chains, exploit unpatched systems, and employ AI to automate attacks and improve evasion.
Fileless malware is very difficult to detect due to its nature — it doesn’t create files on the hard drive. Instead, fileless malware resides in memory. This type of attack exploits existing, legitimate programs to execute malicious activities, often bypassing user and endpoint defenses. By manipulating native, legitimate tools, fileless malware does the same damage as traditional malware — it can steal data, extort ransoms, and mine cryptocurrencies.
- Malware-as-a-Service (MaaS) is now one of the biggest threats to organizations. Rather than a type of malware, MaaS is a business model that allows threat actors to easily acquire malware that is ready to use, effective, agile, and hard to detect. MaaS (and Ransomware-as-a-Service, or RaaS) enables cybercriminals without technical expertise to buy and deploy the most advanced malware, such as stealer trojans, and receive support and software updates.
Phishing attacks
Phishing refers to attacks that attempt to gain access to sensitive information, such as banking information, login credentials, or other private data that can be used for nefarious purposes. Phishing attackers use emails, text messages, phone calls, or social media in attempts to trick users into sharing information through legitimate-looking correspondence.
Phishing is a form of social engineering (also known as human hacking), a manipulation of a person to take action that exposes their personal information or compromises organizational security.
Usually, phishing entails sending fraudulent emails, messages, and other communications to as many users as possible, but it can also be targeted. For example, “spear phishing” personalizes messages to target a specific victim, while “whaling” targets high-value individuals, such as executives.
Another phishing attack variation is called business email compromise (BEC). In a BEC attack, a threat actor poses as an executive, vendor, or trusted colleague to trick victims into sending money or sharing sensitive data. BEC cost the US economy over $2.9 billion in 2023, according to the FBI.3
Just like malware, phishing threats evolve. Today, cybercriminals can use generative AI to develop highly personalized and convincing phishing campaigns. Attacks created with AI can produce documents that closely mimic legitimate communications, which makes it harder for victims to spot fraudulent content, increasing the likelihood of a successful attack.
Due to its ease, many cyber attacks start with a phishing email, making them incredibly popular among cybercriminals. According to the Anti-Phishing Working Group, there were almost 933,000 phishing attacks between July and September 2024 — up from 877,536 between April and June 2024.4 And anyone can become a victim: 8 out of 10 organizations had at least one individual who fell victim to a phishing attempt by CISA Assessment teams.5
Denial-of-service (DoS) attacks
A DoS attack makes a website or network resource unavailable by overloading it with a large volume of traffic. A distributed denial-of-service (DDoS) attack involves incoming traffic to the victim’s servers from multiple sources.
By overwhelming servers with traffic, threat actors cause service disruptions for legitimate users, as well as system crashes.
A DDoS attack is considered more serious than a DoS attack and usually leads to the victim’s system or network crashing. It’s also harder to contain, as it can involve thousands of machines infected with malware that attack repeatedly, sometimes for hours.
Threat actors choose to carry out DDoS attacks for various reasons, including political or ideological reasons, as a protest, or to disrupt a competitor. DDoS attacks oftentimes involve extortion, with a cybercriminal crashing the servers, installing malware, and forcing the victim to pay a ransom to reverse the damage.
Similar to malware and phishing, DDoS attacks evolve over time. The latest, for example, are exploiting a weakness in the HTTP/2 protocol, allowing attackers to generate hyper-volumetric DDoS attacks. Their number is constantly growing as well.
Advanced persistent threats (APTs)
Advanced persistent threats are coordinated, sustained, and stealthy cyber attacks, often carried out by a nation-state or criminal groups working under state sponsorship. They aim to steal sensitive data from a specific organization or individual.
Traditionally, APTs often reflect global and regional geopolitical conflicts, and many are linked to state sponsors such as Russia, Iran, North Korea, and China. The cybercriminal groups they sponsor are skilled and well-funded, and they use the latest advanced tools. They usually target governments, critical infrastructure, financial institutions, and defense industries.
APTs are similar to malware in that threat actors first exploit vulnerabilities to gain access to the victim’s system. Then, they install a backdoor to maintain access over time, using custom malware to evade detection measures. Gradually, threat actors move across the network to steal more data or disrupt the entire system. These can remain undetected for months or years.
Emerging cybersecurity threats
Emerging threats — new tactics, techniques, and procedures (TTPs) that cybercriminals employ to exploit, disrupt, or breach security systems — continuously evolve. As they evolve, they become harder to detect and mitigate. Threat actors often use the same technological advancements as cybersecurity defenders, such as machine learning, generative AI, and IoT devices. Here are some of today’s emerging cyber threats:
IoT vulnerabilities
IoT devices include household appliances, security cameras, industrial sensors, printers, and other equipment connected to the internet. These devices often lack proper security protections and are easy to abuse. Common vulnerabilities include firmware exploits, on-path and hardware attacks, and weak credentials.
One of the more well-known IoT attacks involves using unsecured IoT devices to generate network traffic in a DDoS attack. Each IoT device has its own IP address, making such attacks harder to block.
Cloud security threats
Similar to IoT, cloud computing uses networks and services to manage data online, making it accessible from anywhere with an internet connection. This convenience for users also makes it a convenient target for cybercriminals.
Many cloud security threats stem from identity and access management issues. Insider threats, for example, are exacerbated by the cloud’s remote access. Whether intentional or accidental, insiders (contractors, business partners, or employees) can expose the organization to security risks. With remote access, insiders can misuse their access rights from anywhere, making detecting and preventing such threats much harder.
The scalability and flexibility of the cloud enable businesses to grow operations and adapt to changing market conditions, but they also expand the potential attack surface.
Artificial intelligence and machine learning threats
The same advanced technology that improves the workflows of security teams also improves the efficiency of cybercriminals. AI enhances the existing TTPs, making malware, social engineering, and phishing attacks more efficient, effective, and harder to detect. Overall, it’s expected that AI will increase both the volume and the impact of attacks in the near future.
An example of AI abuse includes the creation and use of deepfakes, which provide near-parity impersonations to deceive victims. Additionally, threat actors are starting to use large language models (LLMs) to help generate code for malware and write more convincing, personalized phishing emails. They can also instruct an LLM or an AI agent to find and exfiltrate sensitive data or perform another malicious action.
Explore the top 10 most common LLM-based attacks techniques. See how LLMs can be abused and how those attacks can be mitigated in Elastic Security Labs’ LLM Safety Assessment.
While AI lowers the barrier for junior security analysts to investigate and respond to attacks, it does the same for threat actors. With AI, less skilled hackers and cybercriminals can carry out effective and sophisticated attacks at scale, making even more organizations and individuals around the world less safe.
Strategies for mitigating cybersecurity threats
Individuals — whether end-users, security analysts, or system administrators — are the first line of defense against cyber threats. At the organizational level, reducing exposure to cybersecurity threats means having a robust cybersecurity risk management plan and proactively updating, testing, and improving cyber defenses.
Here are key strategies for mitigating cyber threats:
Proactive threat hunting strategies
One key strategy to prevent cybersecurity threats before they become a problem is taking a proactive approach rather than reactively responding to incidents that arise. Organizations should proactively find and detect threats to mitigate risk.
With threat hunting, security teams will proactively look into any anomalies, investigate them, and ensure that there are no malicious activities that could lead to a large-scale breach. Threat hunting is particularly helpful for combating APTs, as these can linger undetected in a network environment for months while collecting sensitive information.
Learn more about threat hunting.
Organizational strategies
Cybersecurity basics like firewalls, VPNs, multifactor authentication, automatic software updating, and network access control can greatly aid organizations. In addition to these best practices, organizations should foster a culture of security awareness, train employees on how to identify and avoid cyber threats, and take steps to protect the organization's assets and data.
Organizations should also use automatic threat protection to help identify and block common cybersecurity threats, such as malware or ransomware, in real time, before damage can occur.
Learn more about automatic threat protection.
Incident response and recovery
No security system is complete without an incident response and recovery program.
When a cyber attack occurs, it’s essential that an enterprise investigates and responds as quickly as possible. A fast response is essential so that the impact of an attack is minimized.
Learn more about cyber investigation and response.
Mitigate cybersecurity threats with Elastic Security
Elastic Security delivers unlimited visibility into threats, reduces investigation times, and protects your enterprise from the ever-evolving threat landscape. With Elastic Security, powered by the Search AI Platform, security teams gain visibility across their attack surface, reveal hidden threats, and stop attacks at unprecedented scale.
Stay ahead of cyber threats with Elastic Security.
Sources
1. Statista, “Estimated cost of cybercrime worldwide 2018-2029,” 2024.
2. Chainalysis, “35% Year-over-Year Decrease in Ransomware Payments, Less than Half of Recorded Incidents Resulted in Victim Payments,” 2025.
3. Federal Bureau of Investigation, “Internet Crime Report,” 2023.
4. Anti-Phishing Working Group (APWG), “Phishing Activity Trends Report,” 2024.
5. Cybersecurity & Infrastructure Security Agency, “Phishing,” 2023.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.