Day in the life of an SOC leader

A security operations center (SOC) leader is the point person for an organization’s security operations. They run a team of security analysts, engineers, and other specialists. But what exactly do they do on a day-to-day basis?
As the person managing the organization’s cybersecurity hub, the SOC leader has to navigate all the complexities that come with it. An effective SOC leader (also known as an SOC manager or security operations lead) balances strategy, technology, and team leadership responsibilities. They coordinate efforts of various threat detection and response teams, manage vendor and partner technology integrations, and prepare reports for the company’s leadership teams on the organization’s defensive posture and potential risks.
Sound like a lot? Maybe. But it all comes together in a series of daily tasks. Let’s explore the SOC leader’s role in more detail by delving into a day in their life.
Overview of an SOC
The SOC is an organization’s nerve center for monitoring, detecting, and responding to cybersecurity incidents in near-real time around the clock. It unifies and coordinates all cybersecurity processes, technologies, and operations. SOC teams are responsible for building and maintaining an organization's security posture.
Consisting of security engineers, security analysts, incident responders, threat hunters, and system administrators, an SOC covers everything from planning and prevention to monitoring, detection, response, compliance, and recovery.
Defining the SOC leader role
To put it simply, an SOC leader is in charge of the SOC. But what does that entail? The responsibilities of the SOC leader role include:
Supervising security operations by managing the day-to-day activities of the cybersecurity team, including incident response, security monitoring, and vulnerability management
Setting priorities based on the established goals and long-term roadmap communicated by the chief information security officer (CISO), chief information officer (CIO), or VP of security
Implementing proactive measures, such as threat intelligence feeds, automated responses, and escalation procedures
Overseeing the implementation and maintenance of the security technology stack, including security tools, policies, and procedures
Serving as a mentor for security analysts, particularly those at more junior levels
To perform these responsibilities effectively, a great SOC manager should demonstrate three key traits: leadership skills, technical know-how, and an in-depth understanding of cybersecurity benchmarks and practices.
Every day, SOC leaders have to ask themselves questions like:
Are my teams meeting key metrics, such as mean time to detect and respond (MTTD/R)?
Is our organization safe from the latest vulnerabilities and cyber threats?
What are our organization’s crown jewels and are we protecting them adequately?
Do I have the right resources and tools for complete visibility to detect and quickly remediate incidents?
Are we making the most of the tools and team members we have to minimize risks?
Tools and technologies for SOC leaders and analysts
With such a broad and dynamic perimeter to defend, different team members use different tools for defense. Among these are:
An SOC leader ensures that the tools in the security tech stack are properly implemented and maintained and that the SOC team is using them effectively.
SIEM: See the big picture
An SOC leader uses SIEM solutions to gain visibility into security events across the organization. For many teams, a SIEM is the central dashboard from which to visualize, investigate, and mitigate security events.
SOC analysts also use SIEM to triage alerts, investigate an advancing attack, and stop a threat before damage is done.
SIEM is a great tool that offers continuous monitoring and detailed reporting, which are particularly helpful for meeting compliance requirements and system optimization.
SOAR: Streamline SOC processes
An SOC uses SOAR to streamline incident response processes, automate repetitive tasks, and orchestrate remediation workflows.
Through automation, SOAR substantially reduces MTTR — one of the SOC leader’s key metrics. Moreover, SOAR standardizes SOC processes, ensuring consistent investigation and response while enhancing the skills of security analysts of every experience level.
CDR: Gain cloud visibility
An SOC leader will use CDR to gain a unified view of cloud-native application activity, security events, and infrastructure behavior. SOC analysts use CDR solutions to proactively identify and mitigate threats across different cloud environments, visualize attack paths, and implement preventive measures.
EDR: Obtain visibility into endpoints
EDR addresses cybersecurity threats at the endpoint level. An SOC leader uses EDR solutions to provide granular visibility into endpoint activity. By proactively identifying and addressing security incidents, EDR helps SOC analysts improve the efficiency and speed of threat mitigation and reduce the risk of major breaches.
XDR: Capture a holistic view across endpoints
An SOC leader turns to their XDR solution when they want holistic, unified visibility across endpoints, networks, cloud, and other data sources in order to detect and investigate more complex threats. XDR is key for their team during active incidents to prioritize alerts, correlate signals, and accelerate response.
Threat intelligence: Enhance security posture
An SOC leader’s team uses threat intelligence to get an overview of the threat landscape and its potential impact. Threat intelligence feeds automatically inject insights into the tactics, techniques, and procedures (TTPs) used by threat actors into a team’s SIEM (and other tools). SOC leaders use threat intelligence to anticipate and counter targeted attacks, reduce the likelihood and impact of security incidents, and enhance their organization’s security posture.
SOC analysts use threat intelligence feeds to detect, prioritize, and respond to threats by identifying indicators of compromise. Threat intelligence provides SOC analysts with the contextual information needed to understand the significance of security alerts and prioritize those that pose the greatest risk.
Responsibilities of an SOC leader
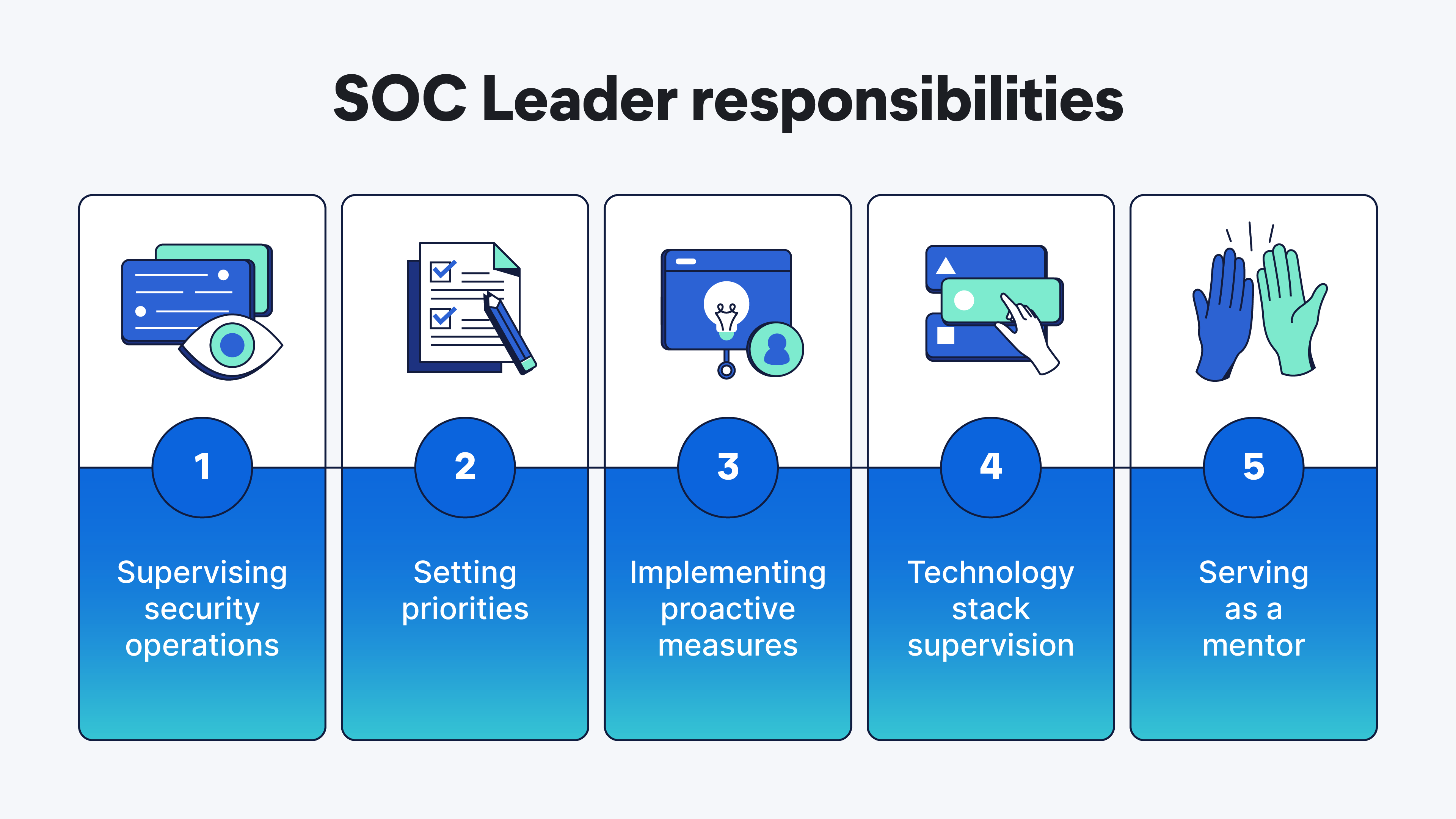
The SOC leader is responsible for managing the SOC team and ensuring that the organization's security posture is strong. This includes leading incident response, overseeing the SOC’s performance and tools, developing and implementing security policies and workflows, and reporting on security operations.
1. Team management and mentorship
An SOC manager oversees Tier 1, Tier 2, and Tier 3 SOC analysts.
Tier 1 SOC analysts are the first line of defense. They’re the initial responders to security alerts.
Tier 2 SOC analysts take on escalated incidents from Tier 1 analysts and can implement complex remediation strategies as well as coordinate complex response efforts across teams.
Tier 3 SOC analysts are the experts. They can conduct proactive threat hunting, research emerging threats, and investigate the most sophisticated attacks.
In addition to overseeing security analysts and others, an SOC leader ensures the SOC team’s skills evolve alongside security threats via hands-on experience and professional development. An SOC leader is often responsible for hiring, training, and evaluating SOC team members, fostering a collaborative and effective team environment. They also manage staffing, scheduling, and the establishment of clear performance expectations.
2. Incident response coordination
An SOC manager is responsible for guiding and coordinating incident response efforts, ensuring their timely and effective resolution. They ensure SOC analysts are executing quick and efficient threat detection and response while directing the overall incident response framework.
3. Threat analysis and intelligence
By ensuring their technology and team members are up to date with the latest threat actors, attack techniques, and vulnerabilities, an SOC leader can help proactively identify and mitigate risks. The key here is in integrating threat intelligence feeds and working with SOC analysts to gather security intelligence and prioritize responses to critical threats.
To achieve their goals, an SOC leader has to align and manage resources, including human, technical, and budgetary.
4. Reporting, documentation, and metrics
Providing regular reports to senior management is another responsibility of an SOC leader. They have to ensure that comprehensive reports on the SOC’s performance and activities (and security incidents) flow to the organization’s executive leadership. They also have to track key metrics, such as MTTD/R, and ensure regulatory audits are compliant.
Perhaps, even more importantly, an SOC manager has to continuously assess and improve the SOC's capabilities, processes, and procedures to enhance its effectiveness.
Skills required for an SOC leader
A successful SOC leader needs a combination of technical expertise and leadership skills. They must be proficient with security tools and have a deep understanding of cybersecurity best practices while excelling at soft skills, collaboration, and strategic planning.
Technical skills
An SOC leader has an in-depth understanding of SOC workflows and cybersecurity tools, such as SIEM, SOAR, XDR, and others. They have to stay informed about current and emerging threats, vulnerabilities, and attack trends. They also have to be familiar with the organization’s entire environment, networks, and systems; understand data ingestion and scalability flows; and learn cloud or hybrid capabilities.
Leadership and soft skills
Communication, conflict resolution, team building, and the ability to balance daily firefighting with long-term strategy are skills that make a great SOC leader.
An SOC manager, for example, has to communicate technical information to any audience in a clear and concise manner. They have to work effectively with other teams and stakeholders across the organization and motivate SOC analysts to achieve their full potential.
One often overlooked skill is stress management. A team leader has to keep the team comfortable and motivated in any situation because SOC teams often deal with high alert volumes and potential fatigue.
Challenges faced by SOC leaders
An SOC leader plays a crucial role in an organization’s security efforts and is meant to solve challenges that SOC analysts face. However, an SOC manager also faces numerous challenges, including budget constraints, effective incident response, and addressing skill shortages.
Overcoming alert fatigue
SOC team members are often overwhelmed by the sheer volume of alerts, making it difficult to identify and respond to genuine threats.
Solution:
An SOC leader can ensure that processes and tools filter out noise, so analysts can focus on real threats. For example, AI-driven security analytics significantly reduce the noise and prioritize critical alerts, saving teams time and effort.
- An SOC leader can help balance shift work and staffing to reduce burnout. Take this cybersecurity analyst burnout quiz to find out whether your team needs help.
Keeping up with evolving threats
Cyber attackers are constantly developing new techniques and looking for new vulnerabilities, requiring SOC teams to continuously adapt to stay ahead of the curve.
Solution:
By committing to ongoing training, technology upgrades, and cross-functional collaboration, an SOC manager has to adopt a proactive security approach.
A dynamic threat landscape requires dynamic strategies to manage it. This toolset includes proactive threat hunting and AI to help identify potential high-risk alerts or guide analysts through triage, investigation, and response.
Why Elastic is the SOC leader’s strategic partner
An SOC leader's unique responsibilities that combine team management, technical expertise, and strategic direction are crucial for an organization's overall security posture. They ensure proactive threat detection, effective incident response, and continuous improvement in cybersecurity.
Elastic empowers SOC leaders not only by providing a comprehensive security solution but also by addressing key challenges. Explore how Elastic Security can ease the burden on SOC leaders with AI-driven security analytics.
Additional security resources
- Elastic Security Labs
- AI for SecOps
- Discover Elastic AI Assistant for enhanced observability and security operations
- AI adoption in security: Top use cases and mistakes to avoid
- SOC analyst vs. security analyst: What’s the difference?
- Will AI start taking cybersecurity jobs?
- [Webinar] Introduction to Elastic Security: Modernizing security operations
- [Webinar] AI for SOC teams: What’s real and what’s next
- Security Operations Center (SOC) comprehensive guide
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos, or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.