Elastic and AWS — Securing the cloud, together

Elastic is pleased to announce that we have recently achieved the AWS Security Independent Software Vendor (ISV) Competency Partner status with specialization in Threat and Detection Response (SIEM, SOAR, and XDR). This recognition highlights our commitment to providing you, our customers, with advanced security capabilities that can help you protect your sensitive data and applications in the cloud.
The AWS Security ISV Partner Competency is awarded to partners who have demonstrated technical proficiency and proven customer success in delivering security solutions on AWS. To achieve this status, Elastic had to undergo a rigorous validation process, including a technical audit of its security capabilities and a review of customer case studies.
Elastic's achievement of this status is a significant milestone. It showcases our dedication to delivering innovative security solutions to help you protect your cloud environments. By leveraging Elastic's solutions on AWS, you can benefit from the scalability and agility of the cloud while maintaining the highest levels of security and compliance.
What is Elastic Security?
Security teams must defend a rapidly evolving organization against increasingly sophisticated and numerous adversaries — despite finite resources, disjointed technologies, and the limitations of traditional security tools. Employing a solution engineered for tomorrow’s threat landscape is vital.
Elastic Security is built on the company's Elasticsearch technology, which enables fast and scalable search and analytics capabilities. It integrates seamlessly and compliments AWS services like AWS Security Hub, AWS Web Application Firewall (WAF), Amazon Inspector, AWS Network Firewall, AWS CloudTrail, Amazon Key Management Service (KMS), and Amazon GuardDuty to provide real-time threat detection and response capabilities.
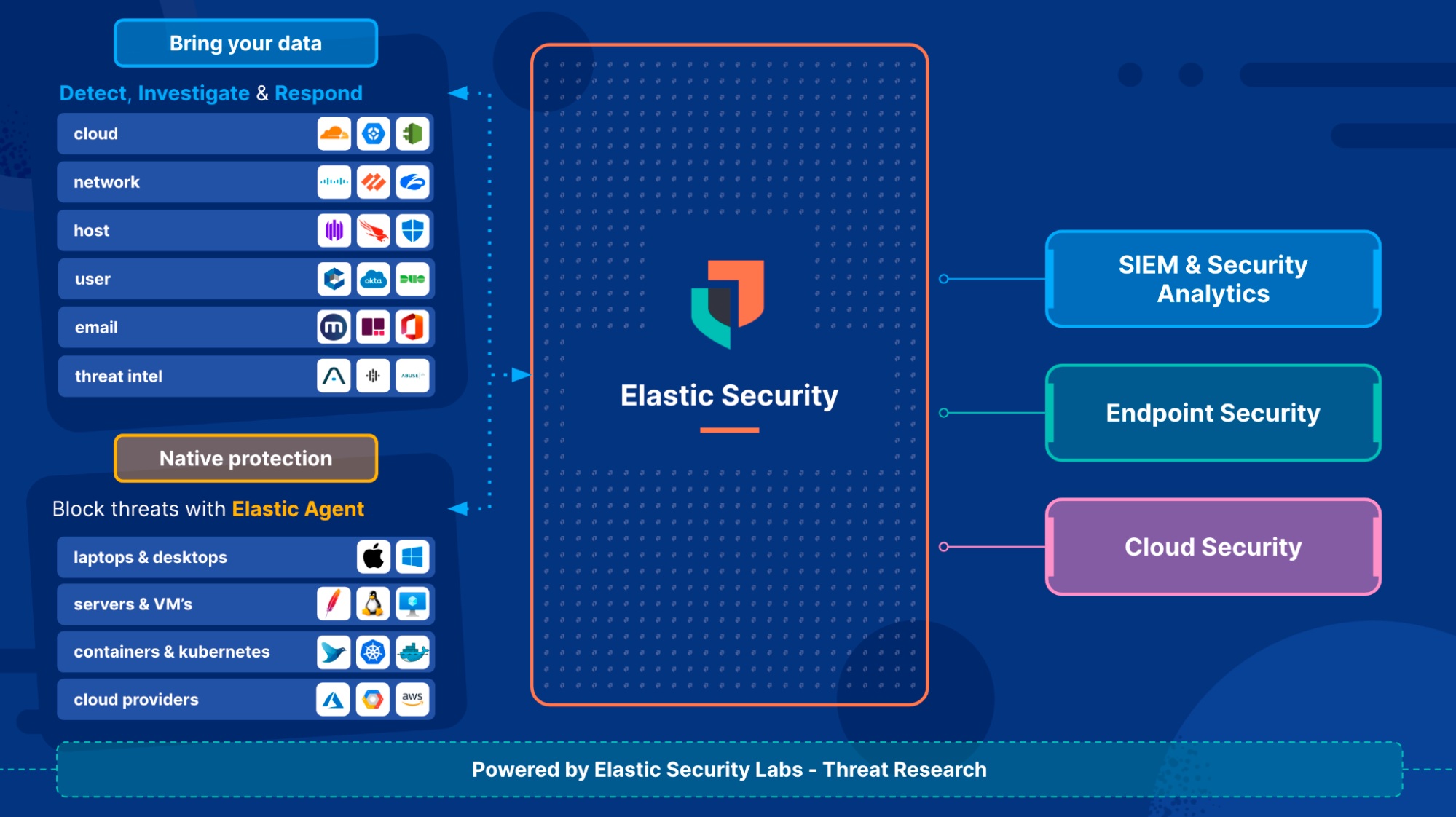
Elastic Security unifies the capabilities of SIEM and security analytics, endpoint detection and response (EDR), and cloud security, helping your team protect, investigate, and respond to threats before damage is done. On an open platform built for the hybrid cloud — with an agent that stops ransomware and advanced threats alike — Elastic Security arms the SOC to reduce overall risk by 60%.* By fueling advanced analytics with years of data from across your attack surface, Elastic Security eliminates data silos, automates prevention and detection, and streamlines investigation and response.
With features like anomaly detection, machine learning-powered analytics, and threat intelligence feeds, Elastic Security can help AWS customers identify and respond to security incidents in real time.
- Elastic Security for Endpoint provides advanced endpoint protection for AWS instances and workloads. With features like malware prevention, behavioral monitoring, and file integrity monitoring, Elastic Security for Endpoint helps you protect your data and infrastructure from cyber threats.
- Elastic Security for SIEM provides a centralized platform for security event management, threat hunting, and compliance reporting. With features like data normalization, correlation rules, and machine learning-based detection, Elastic Security can help you identify and respond to security threats across your AWS environment.
- Elastic Security for Cloud provides a comprehensive solution to protect the full lifecycle of cloud-native applications. Additionally, Elastic offers various features that help ensure the security of cloud-based applications from development to production — CSPM and KSPM, Vulnerability Management, Cloud Workload Protection, and Container Workload Protection. You can also collect and analyze AWS Services logs — including security audits and access logs — to help you understand AWS access and usage patterns to detect anomalies with unsupervised machine learning to save you time by reducing false positives.
Why does this matter to Elastic and AWS customers?
Many organizations are on a digital transformation journey to provide increased value to end users. AWS Competency Partners have proven expertise and technical capabilities to help you succeed at each stage of your cloud adoption journey.

By attaining this competency, Elastic has demonstrated its ability to deliver best-in-class security solutions on AWS that can help you meet your security and compliance requirements. This achievement is another in a set of external validations which provides you with the assurance that you can rely on Elastic Security’s solution to help you protect your sensitive data and applications in the cloud.
With Elastic's security solutions on AWS, you can benefit from:
- Advanced threat detection and response: Elastic's Security leverages machine learning and analytics to provide real-time threat detection and response capabilities.
- Continuous endpoint protection: Elastic's Security solution delivers continuous endpoint protection against known and unknown threats, reducing the risk of breaches and data loss.
- Single platform and common schema:Leveraging a single platform and common schema, you can quickly and easily secure your cloud environments.
Leading companies around the world including Karbon, Personal Capital, and DISH have benefited from running Elastic on their AWS environments — and you can, too.
Interested in more information?
For further details, please visit the following links:
- AWS Competency Program
- Protect your AWS workloads using Elastic Security
- Elastic integrations with AWS
- Elastic and AWS: Seamlessly ingest logs and metrics into a unified platform with ready-to-use integrations
Search, solve and succeed with Elastic Security on AWS
Ready to transform endless amounts of data into endless possibilities? Start a 7-day free trial by signing up via the AWS Marketplace and quickly spin up a deployment in minutes on any of the Elastic Cloud regions on AWS around the world. Your AWS Marketplace purchase of Elastic will be included in your monthly consolidated billing statement and will draw against your committed spend with AWS.
*Source: Elastic Results That Matter Survey, 2023
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.