Enhance SOC workflows with Elastic Security and Recorded Future threat intelligence

Security teams today need to analyze vast amounts of data from various sources, including endpoints, cloud, applications, and user activity, just to mention a few. At the same time, adversary activity is also on the rise and the threat landscape is becoming more and more complex every day.
Further exacerbating the situation, security teams are strapped for resources and unable to analyze the enormous amounts of data and security alerts they receive in real time. Their focus and time is prioritized for matters that have the biggest potential impact on the organizations they protect.
That’s where consolidated solutions can help in enhancing detection and investigation workflows. Read on to learn how the power of Elastic Security combined with threat intelligence from Recorded Future streamlines analyst workflows, helps reduce alert fatigue, and boosts analyst confidence.
The strength of Elastic Security
Elastic Security unifies security information and event management (SIEM), endpoint security, and cloud security on an open platform, arming SecOps teams to protect, detect, and respond at scale. Elastic Security allows you to use data from across your environment to make sense of attacker behavior. You can power detection and response workflows with data gathered from your endpoints, users, network devices, cloud workloads, and applications.
To avoid the limits of traditional solutions, Elastic Security allows you to scale and adapt using flexible data tiers. The tiering model can support your data retention requirements, allowing you to analyze data in real time as well as retrospectively. The unified approach of SIEM, endpoint, and cloud security means Elastic Security empowers organizations to not only detect and respond to cyber attacks but proactively protect against them.
Security challenges take away the opportunity to get actionable insights that allow teams to eliminate blind spots and stop threats at scale.
The value of threat intelligence for SOC teams
Through an integration, Recorded Future and Elastic Security bring threat intelligence correlation capabilities to security analytics. Recorded Future is the world's largest intelligence company. The Recorded Future Intelligence Cloud provides complete coverage across adversaries, infrastructure, and targets. Combining persistent and pervasive automated data collection and analytics with human analysis, Recorded Future provides visibility into the digital landscape, empowering countries and organizations to take proactive action to disrupt adversaries.
Threat intelligence can help to answer questions such as:
- “Is this indicator malicious?”
- “If so, why is it malicious? What is the context around the threat?”
- “Is this indicator associated with a threat actor or malware campaign?”
- “Who is the attacker?”
- "What other indicators should I be concerned about?"
Combining Elastic Security and Recorded Future
By using both Elastic Security and Recorded Future, security teams are able to streamline their workflows by gaining access to readily available intelligence, when and where they need it.
Streamlined analyst workflows
Engineered to integrate with Elastic Security, Recorded Future puts comprehensive intelligence at the analyst’s fingertips without adding additional complexity. SOC staff have the ability to quickly rule out false positives by using additional information and context. Thus, they can triage alerts on the fly and with far less effort.
A dedicated intelligence management interface
The Elastic Security interface makes threat intelligence actionable by centralizing all active Indicators of Compromise (IOCs) in one place. These IOCs can thus be searched, sorted, and filtered in real time as part of an investigation.
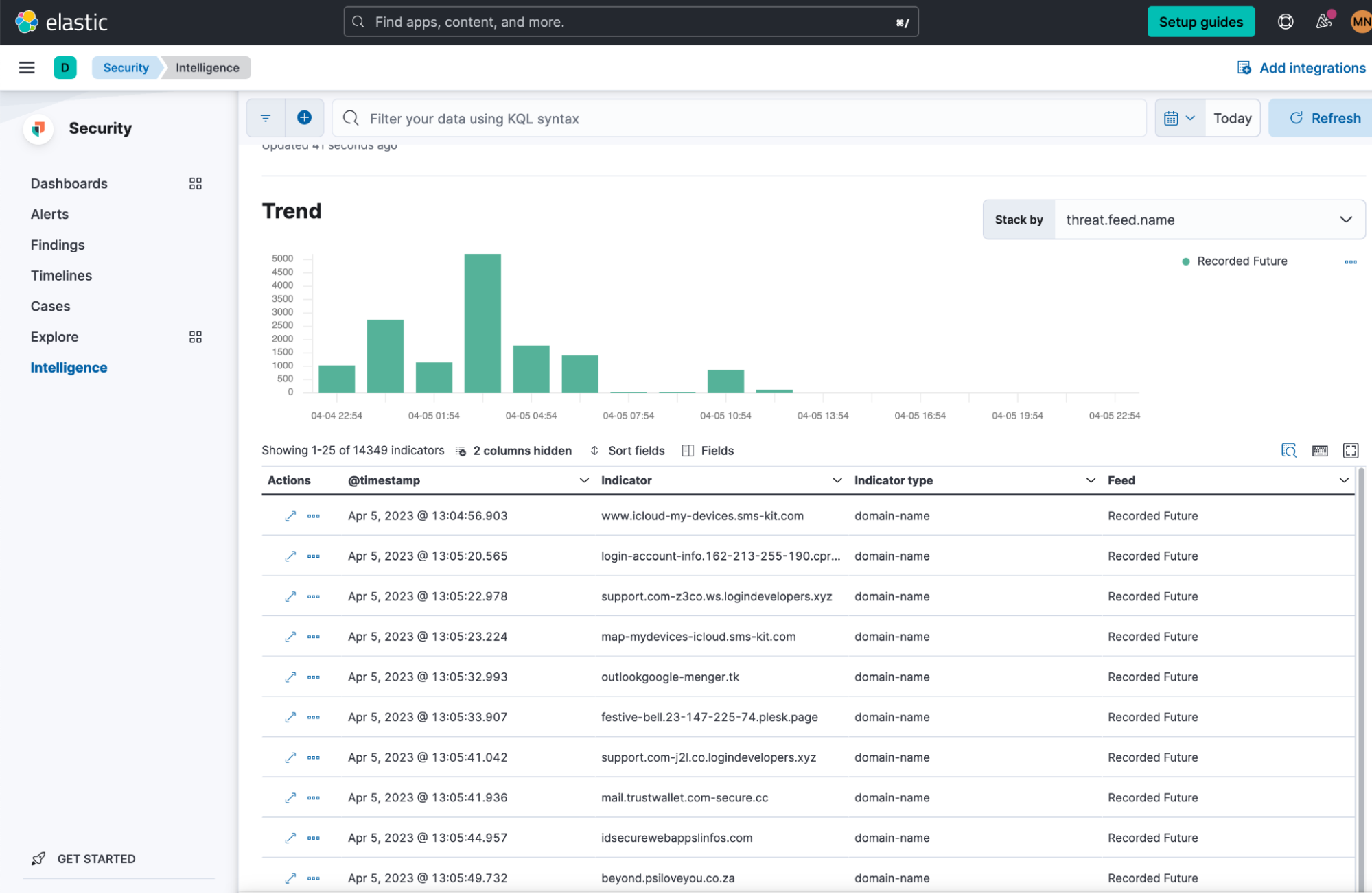
Escalate threat intelligence via cases
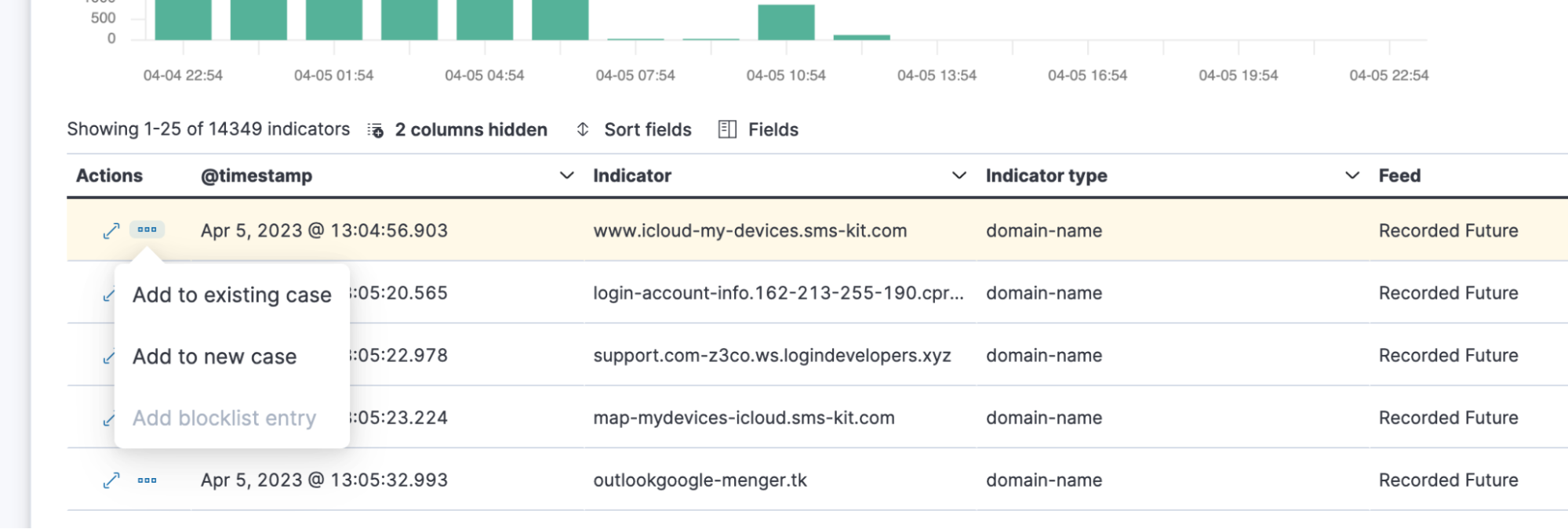
IOCs seen as relevant to an investigation can be added to either a new or existing case as evidence, thereby escalating threats and their related context. Cases are a place in Elastic Security where a security team can track investigations, add alerts and other evidence, and make all this shareable within and beyond the team. The latter creates visibility into actions taken on escalated threats.
Enrich investigations via timeline
The IOCs can also be added to Timeline, a workspace for investigations and threat hunting in Elastic Security. Timeline facilitates correlation capabilities at investigation time through query and filter capabilities. It is a place where analysts can easily structure queries, add filters, drag and drop fields, and specify a date or time range, in a quest to find answers to questions during an investigation.
Go to Figure 5 in the threat hunting section below to see Timeline in action!
Alert fatigue reduction
A huge part of a SOC analyst's day is spent attending to alerts generated by multiple security tools, including SIEM and EDR technologies. Determining if an alert is severe and poses a real risk requires gathering related contextual information from both internal data sources and external threat databases.
Indicator match rules
Elastic Security comes with prebuilt detection rules and can be used to create and manage rules and view the resulting alerts. One such rule type is the indicator match rule, which creates alerts when indicators from Recorded Future intelligence data have a match against local file or network observations in Elastic Security.
The rule, in real time and retrospectively, matches on indicators such as file hashes, source and destination IPs, domain names, and URLs. Elastic Security allows the use of other fields apart from the ones mentioned, on which the rule can match.
Threat Intel IOC alerts and context
With a dedicated Threat Intel tab in the alert flyout, Elastic Security gives insights into individual threats that match an alert. Elastic finds these threats through either the indicator match rule triggering an alert or through alert enrichment with threat intelligence at creation of an alert. If the alert does not contain threat intelligence data, the Threat Intel tab displays a message that none is available.
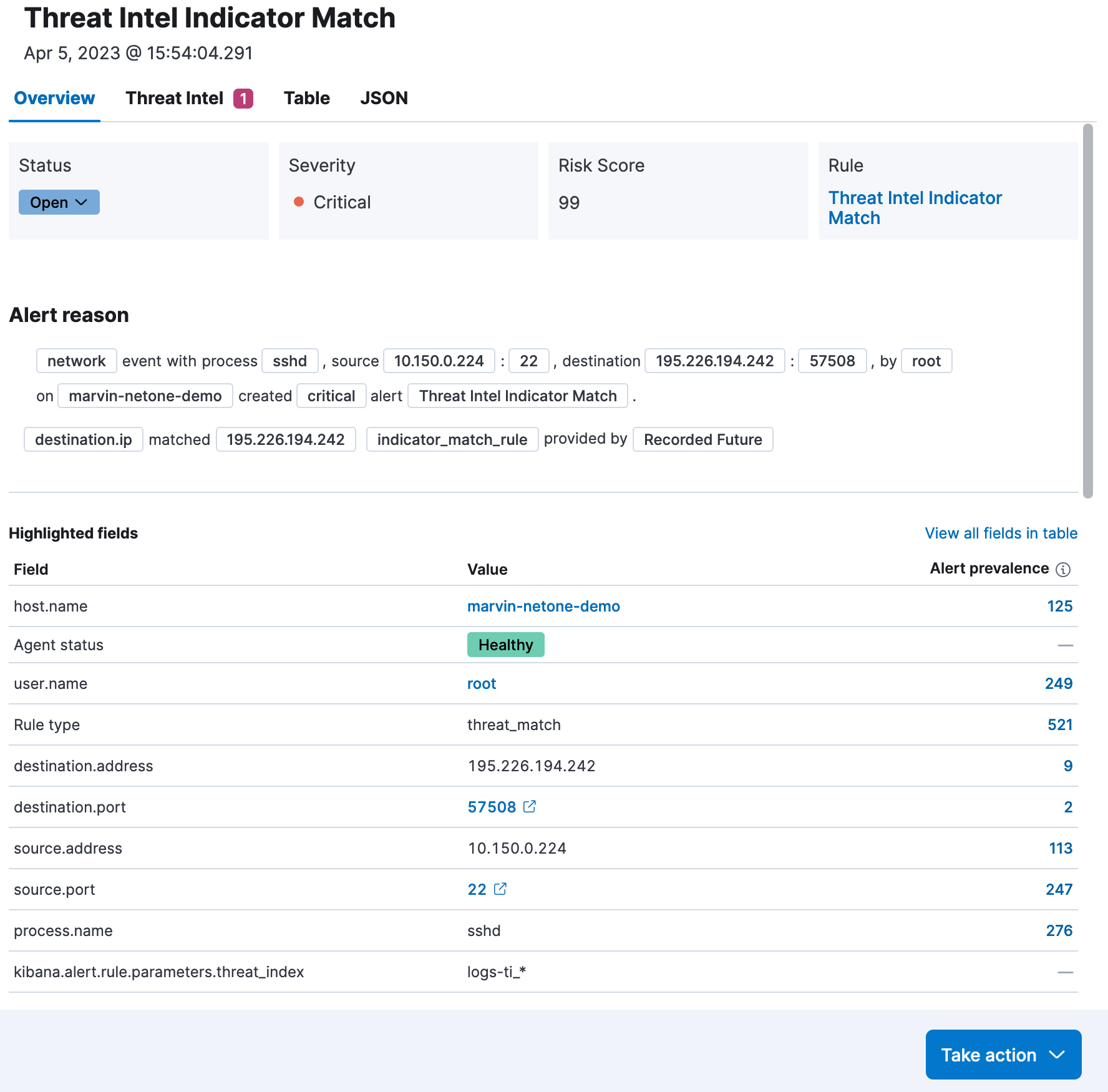
As can be seen in the figure above, when Elastic receives a new IP address IOC it can quickly and automatically retrospectively search for occurrences of the IP in the historical data and inform the Secops team of several potentially malicious attempts to communicate with the IP. Recorded Future threat intelligence data allows an analyst to be alerted on matches.
The analyst can then get valuable context of the observed IOCs from Recorded Future data, thereby helping the analyst triage alerts, correlate with other data in Elastic, and determine the severity of the alert. The alert volumes are made easier to triage and investigate by providing meaningful insights that are truly relevant to the organization. This allows security analysts to zero in on alerts with significant threats and take immediate and informed actions to resolve them.
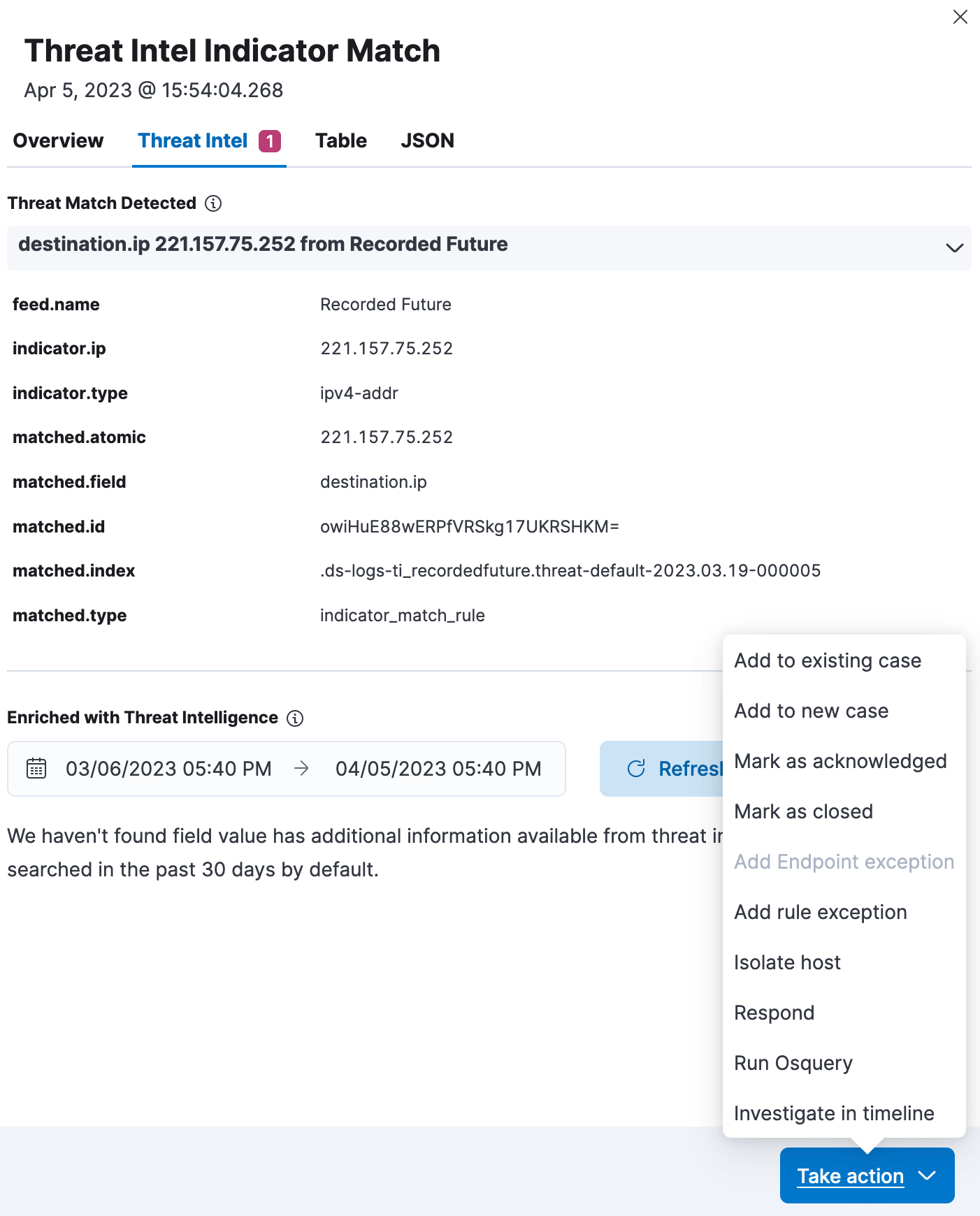
Enhanced threat hunting
Security teams love to be proactive by constantly and iteratively searching for signs of compromise in their environments. The aim is to shorten the dwell time of an attacker and reduce the risk of a breach for an organization. By using Recorded Future intelligence and Elastic Security’s powerful data analytic capabilities, security analysts can trigger their hunt hypotheses based on observed data in Elastic Security, or threat intelligence information, or both.
To run data-driven threat hunts, Elastic Security makes use of the Elastic Common Schema (ECS) to model data to a common set of fields. Adopting ECS makes it easy to analyze, visualize, and correlate data. An analyst can initiate hunts given a certain hypothesis and easily search through petabytes of data. The alerts created from detection rules can also be used to initiate a threat hunt that can be investigated and tracked using Timeline. Analysts can then document and share their findings via cases in Elastic.
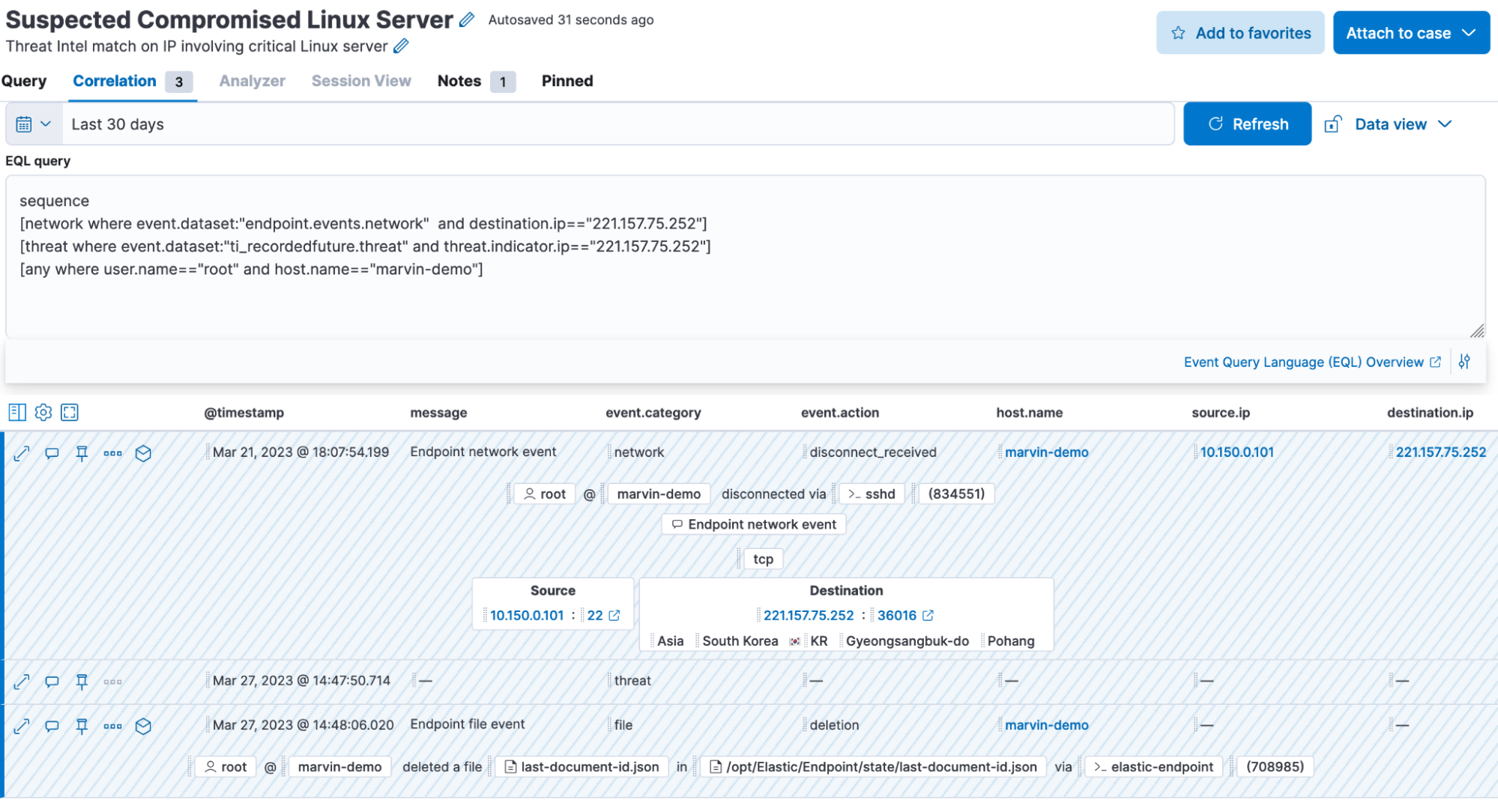
For threat intelligence driven hunts, ECS has dedicated threat fields that have been mapped to the MITRE ATT&CK® framework threat taxonomy. Security analysts are thus able to conduct proactive investigations and understand adversarial capabilities, infrastructure and associated tactics, and techniques and procedures (TTPs). The threat intelligence context received from Recorded Future is parsed and normalized into some of these threat fields, making it easy to have that context in the threat hunting queries and filters.
Of course, you can combine the two threat hunting approaches as shown in Figure 5.
This blog has shown you how you can tremendously reduce analyst alert fatigue, streamline workflows, and boost analyst confidence by integrating Elastic Security with the Recorded Future threat intelligence platform. As threats accelerate and converge in the world around us, your organization can have the right intelligence at the right time and use that as part of its detection and response workflows.
Getting started
Elastic has made it easy to leverage intelligence from Recorded Future. You can ingest threat intelligence on indicators from Recorded Future risk lists with Elastic Agent. Elastic Agent is a single, unified way to add monitoring for logs, metrics, and other types of data to a host.
You can easily get started with Elastic Security. To get a demo of Recorded Future, simply request it.