Elastic Security 8.6 improves investigation and response across a unified SIEM, endpoint security, and cloud security solution

Elastic Security 8.6 helps security practitioners investigate and respond to threats quickly at cloud scale with SIEM, cloud security, and endpoint security. This release includes new data source integrations, expanded prebuilt detection content, and improved detection engineering and analyst workflows — bringing efficacy and efficiency to the modern security operations center (SOC).
Security operations centers use SIEM to detect malicious activity by analyzing their security-related events and information, but there are a number of distinct operations they must perform in order to do this effectively. Their teams must ingest relevant security information, detect threat activity with rules and other analytics, triage the alerts generated by the rules, investigate activity to determine root cause, escalate to other team members, and, finally, respond to remediate the threat. Phew! Through streamlined workflows and automation, Elastic Security 8.6 helps significantly reduce the time necessary to detect and respond to these threats.
Advancements in the release further allow customers to:
- Detect more threats via automated rules and analytics
- Streamline the alert triage process
- Automate the investigation experience
- Speed the response and remediation of threats
Elastic Security 8.6 is available now on Elastic Cloud — the only hosted Elasticsearch offering to include all of the new features in this latest release. You can also download the Elastic Stack and our cloud orchestration products, Elastic Cloud Enterprise and Elastic Cloud for Kubernetes, for a self-managed experience.
What else is new in Elastic 8.6? Check out the 8.6 announcement post to learn more >>
New security data source integrations
The 8.6 release includes further expansion of its set of one-click Elastic Agent integrations for popular security-relevant sources such as AWS Inspector, Box, Darktrace, F5 BIG-IP, Google Workspace Alert Center and DLP, InfoBlox, LastPass, Microsoft 365 Defender, PingOne, and Trend Micro. These integrations help security teams integrate relevant security information and events into Elastic Security for SIEM.
Expanded security detection content helps automate detection and investigation
Elastic Security provides hundreds of prebuilt detection rules and other security analytics that help identify malicious activity within security logs. The 8.6 release strengthens this ability with new rules and three key additions:
Prebuilt rules now detect complex attack behaviors using Elastic’s hierarchical detection engine to correlate groups and/or sequences of previous alerts. By having a single alert for a complex attack, analysts are able to quickly escalate the attack for response and remediation.
Prebuilt rules also now include a technical preview of a new automation capability, in which investigation guides are no longer limited to text-based suggestions on how to investigate alerts, but also include interactive OS-query searches to gather additional contextual information at the click of a button.
A new high-fidelity, ML-based data exfiltration use case identifies attempts to steal data.
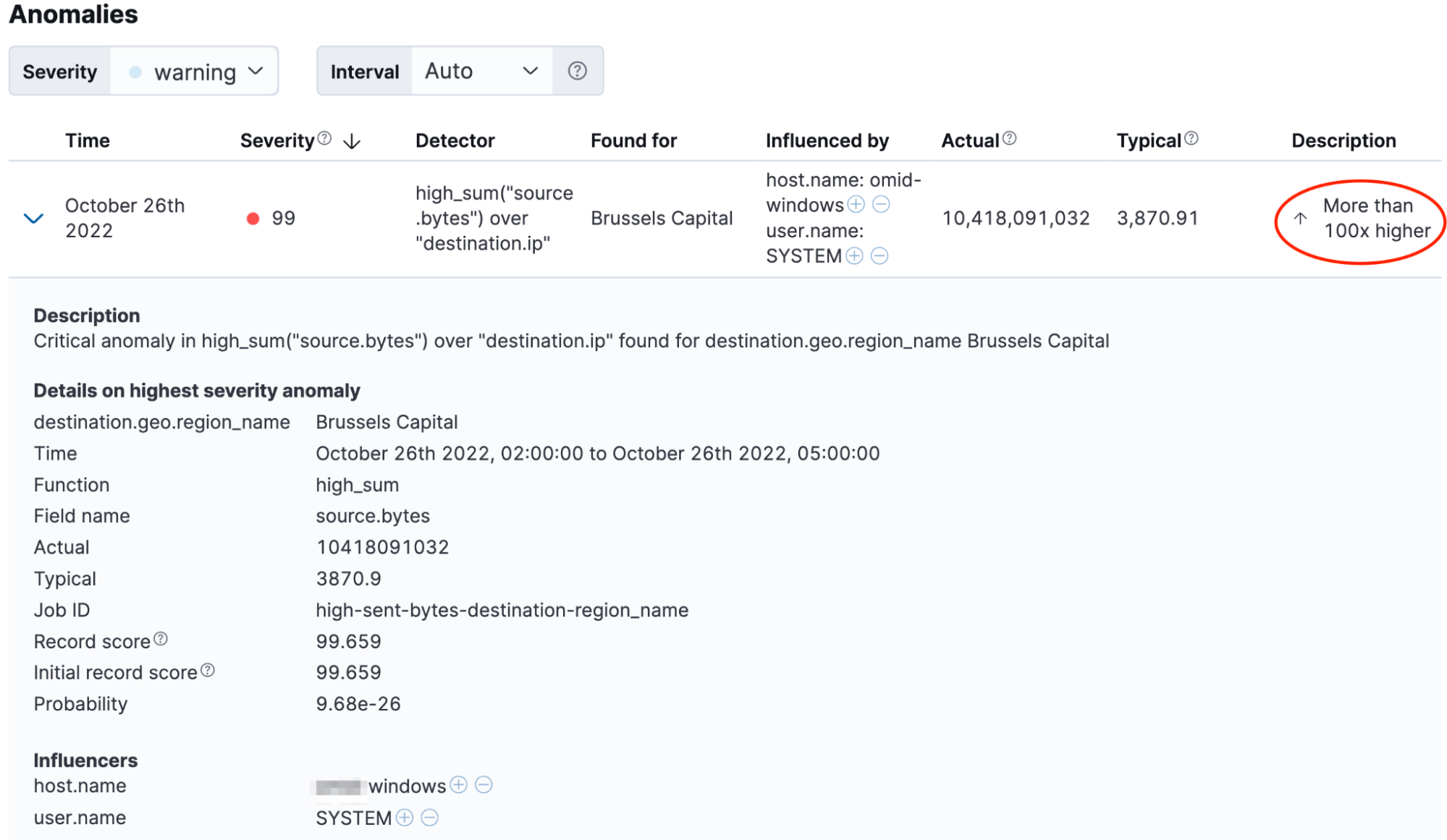
Streamlined detection engineering and analyst workflows
Elastic 8.6 brings enhanced detection engineering workflows, including enhanced rule exception management, multiple-field new term detection, and improved machine learning rule management to help to speed the deployment and tuning of rules.
A new technical preview of alert suppression helps radically reduce the number of alerts, helping analysts avoid alert fatigue. Indicators of compromise (IoCs) can be added directly to a case to provide additional context for escalation.
The 8.6 release also speeds investigations with an improved analyst workflow for investigating multiple alerts in parallel, and an enhanced Cloud Security session viewer that displays file and network alerts to provide additional context for quicker investigations.
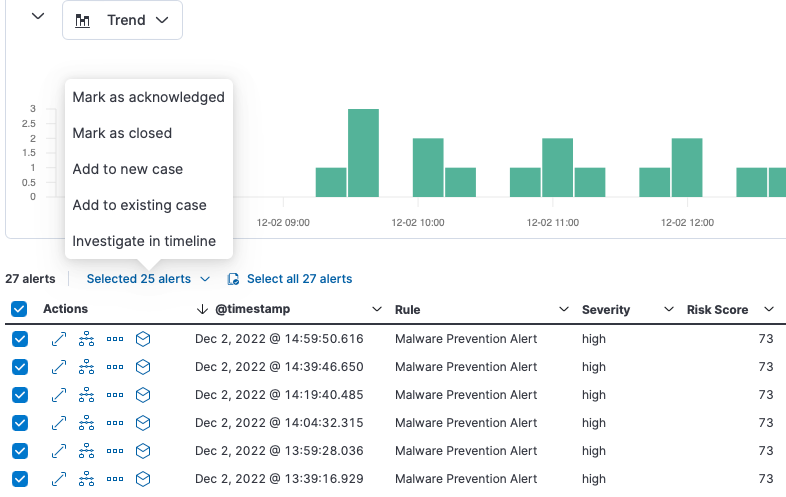
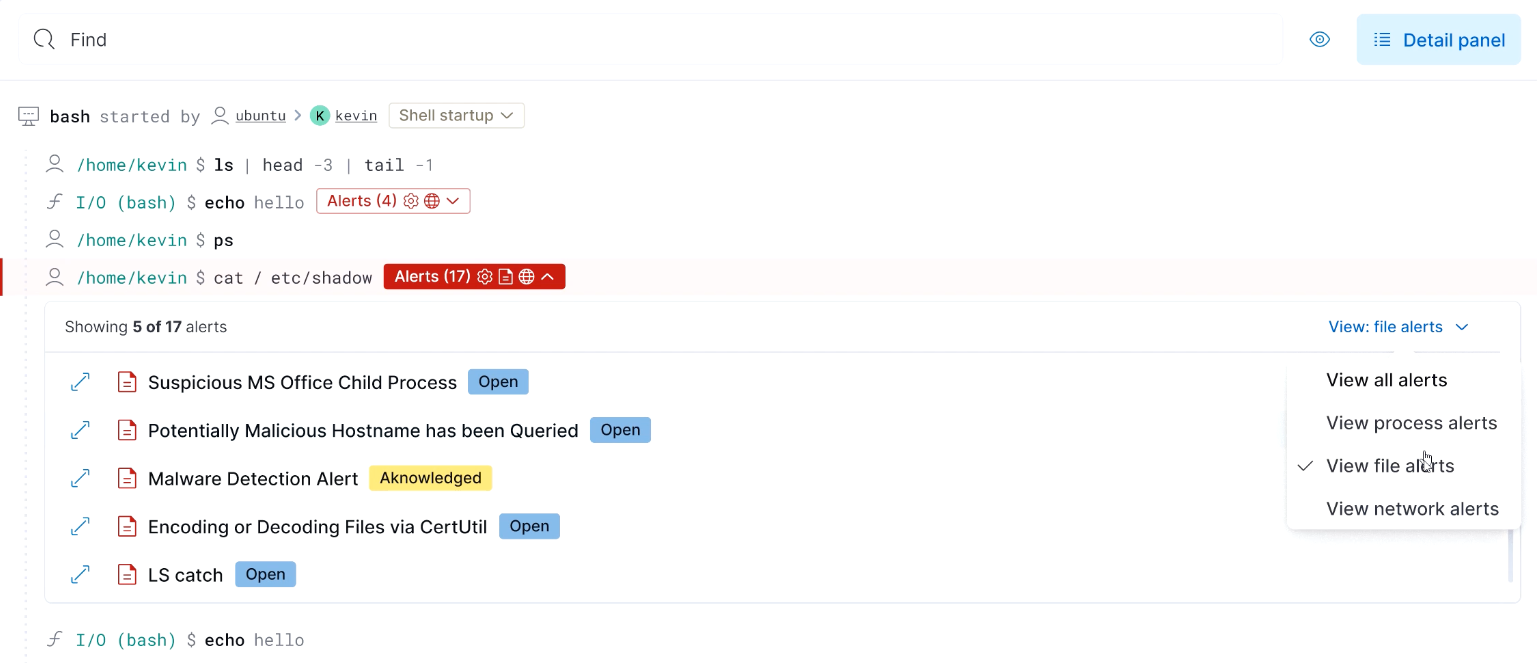
Try it out
Read about these capabilities and more in the release notes.
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. Not taking advantage of Elastic on cloud? Start a free trial.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.