You thought Elastic only did SIEM? Think again!
Elastic Extended Security, born from the acquisition of Endgame, brings years of battle-tested EDR and threat prevention expertise directly into Elastic’s Search AI Platform. This isn’t a bolt-on or third-party integration; it’s a native, deeply embedded component that redefines what’s possible with XDR.
As data volumes grow exponentially, traditional EDR tools hit walls. Elastic doesn’t. Only Elastic can deliver true XDR: natively correlating endpoint, network, user, and cloud telemetry at search speed, across petabytes of data, all in a single platform.
But Elastic goes further:
- Best-in-class endpoint built in: Our agent protects Windows, macOS, and Linux with the award-winning prevention and detection capabilities originally pioneered at Endgame and evolved into a scalable platform for modern threats. Advanced malware, behavioral, memory, and ransomware defenses are included out of the box.
- Hybrid endpoint, real-world ready: Most enterprises rely on multiple endpoint vendors, and Elastic meets them where they are. Elastic Security’s vendor-agnostic platform seamlessly operationalizes data from third-party EDR tools alongside Elastic Extended Security’s own endpoint agent — all within a unified detection and response workflow. No silos. No pivoting.
- Unlimited deployment model: With Elastic, every user gets unlimited agents. Scale up during incidents. Deploy widely during mergers and acquisitions. Build a resilient baseline across thousands of machines — without hidden per-endpoint pricing. Elastic delivers a mission-ready platform that protects today’s infrastructure and scales to meet tomorrow’s complexity. This is XDR the way it was meant to be: flexible, powerful, and unified.

No per-endpoint fees. No limits. No compromises.
At Elastic, we don’t believe in locking you into restrictive licensing based on per-endpoint counts or forcing you to pay extra for every additional capability. While others charge you for every module and device, Elastic gives you SIEM, endpoint security, and XDR on a single, unified platform. At Elastic, you only pay for the data you use. Endpoint protection is included with the platform — you simply deploy the Elastic Defend integration to enable it — and you’re charged solely for the telemetry you collect and retain, at efficient, data-lake-like pricing. Our vendor-agnostic model lets you ingest and operationalize data from any EDR vendor, giving you unified visibility without vendor lock-in or added costs. Protect what you need, scale how you want.
No limits. No surprise fees. Just powerful, unified security built for you — not your vendor’s bottom line.
True XDR, not just a buzzword: Unified detection and response across your environment
Elastic solved the hardest problem of XDR before most vendors even recognized it: scaling to massive data volumes with real-time speed and advanced analytics across your entire environment — whether on-premises, across multiple clouds, or distributed globally. For over 15 years, we’ve led the way in operationalizing security data at scale — something many EDR vendors are still scrambling to figure out. While others struggle with data limits, sluggish queries, and siloed detections, Elastic delivers true, unified detection and response across endpoint, cloud, network, and third-party data — without compromise.
Modern attacks rarely stay confined to a single system — and neither should your defenses. Elastic Security brings together SIEM and EDR capabilities into a single, scalable platform, giving security teams comprehensive, correlated visibility across endpoints, cloud workloads, networks, and user activity. This integrated approach empowers analysts to detect, investigate, and respond to multi-stage lateral threats with speed and precision. By correlating endpoint telemetry with broader security data via hundreds of out-of-the-box integrations, Elastic enables true XDR outcomes: faster detection of complex attack patterns, reduced investigation times, and a more efficient, streamlined security operation. With Elastic, you break down data silos, regain control of your security data, and stay ahead of advanced threats with the context your team needs to act decisively.
Accelerate security response with smarter analyst workflows
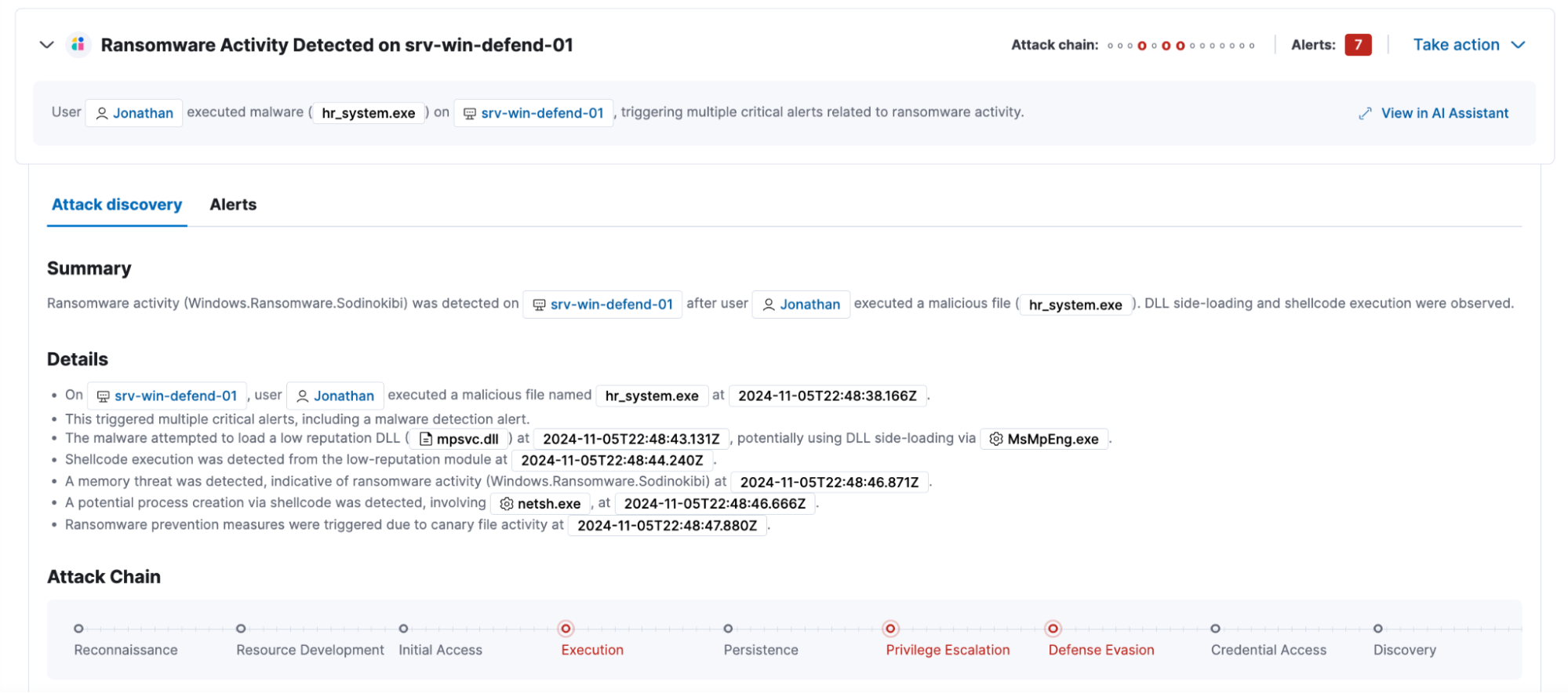
In today’s fast-paced threat landscape, speed and precision are everything. Elastic Security puts AI to work for your team with powerful, analyst-centric features designed to cut through noise and accelerate response. Attack Discovery automatically surfaces high-risk attack paths and suspicious behaviors by analyzing detections and endpoint telemetry in real time — no manual pivoting or hunting required. Paired with the Elastic AI Assistant, analysts can instantly summarize incidents, get contextual explanations, and receive guided next steps tailored to each investigation. Automatic Import streamlines onboarding and normalization of custom data, giving analysts immediate visibility and context regardless of the data source.
AI-driven fixes at your fingertips
Endpoint security is essential, but it can sometimes introduce system slowdowns or conflicts that affect performance. Troubleshooting these issues manually is complex and time-consuming, often delaying the deployment of security tools and creating critical visibility gaps across your environment.
Elastic’s Automatic Troubleshooting uses AI to automatically identify third-party antivirus and security software causing endpoint performance issues and slowing your users down. We even help you fix these conflicts, with fast one-click exclusions.
This gives security teams fast, clear insights and guided steps to resolve performance problems — helping you maintain strong security without sacrificing endpoint performance or user experience.
How does Elastic Extended Security protect my endpoints?
Elastic Defend is the endpoint protection integration within Elastic, delivering real-time prevention, detection, and response capabilities. It protects against a broad spectrum of threats — including malware, ransomware, fileless attacks, and adversary techniques like process injection and credential dumping — while continuously monitoring for malicious behaviors at both the host and process level. In this section, we’ll dive into how Elastic Defend detects, blocks, and responds to these attack types to maintain endpoint security.
Malware
Elastic Extended Security helps protect your devices from malware on Windows, macOS, and Linux by using multiple layers of defense. It scans files when they’re saved or run to catch bad software before it can cause harm. Using smart detection methods like YARA signatures and threat intelligence lookups, it can spot threats quickly. On Windows and macOS, Elastic Extended Security also uses a risk score model using machine learning, called MalwareScore, to help prioritize the most dangerous threats. Plus, it lets you block unwanted programs, quarantine suspicious files, and even restore them if needed. On Windows, it goes a step further with features like self-healing and driver protection to keep your system running smoothly and safely. Together, these tools work quietly in the background to keep your endpoints secure without slowing you down.
Ransomware
When it comes to ransomware, Elastic Extended Security offers strong protection primarily for Windows endpoints. It both watches for suspicious behaviors that indicate ransomware activity and uses “canaries” — special decoy files designed to detect when ransomware tries to encrypt data. Elastic Extended Security can also protect the Master Boot Record (MBR), which ransomware often targets to lock you out of your system. If ransomware is detected, Elastic Extended Security can automatically kill the malicious process to stop the attack in its tracks.
Fileless attacks
A fileless attack is a type of cyber attack that doesn’t rely on downloading malicious files — instead, it runs harmful code directly in your device’s memory, making it harder to detect with traditional security tools. Elastic Extended Security helps protect your devices from these tricky memory-based and fileless attacks on Windows, macOS, and Linux. It uses YARA scanning to spot suspicious code patterns across all platforms. On Windows, Elastic Extended Security also monitors memory threat system behaviors in real time, identifying suspicious process activity, in-memory injection techniques, and other indicators of fileless attacks. If a threat is detected, Elastic Extended Security can kill the malicious process immediately to stop the attack. On Windows, it also includes self-healing features that automatically repair affected parts of the system. This multi-layered approach helps keep your endpoints safe from stealthy attacks that try to fly under the radar.
Malicious behavior
Malicious behavior protection focuses on spotting harmful actions on your devices rather than just known malware files. Elastic Extended Security monitors for suspicious behavior across Linux, macOS, and Windows using powerful detection methods to identify threats in real time. It looks for a wide range of malicious activities, such as unauthorized privilege escalation, suspicious process spawning, unusual network connections, or attempts to disable security tools. When it detects these behaviors, Elastic Extended Security can kill the harmful process — or even the entire process tree — to stop the attack from spreading. By focusing on what attackers do instead of what they look like, Elastic Extended Security helps catch stealthy threats before they cause damage, keeping your endpoints safe and secure.
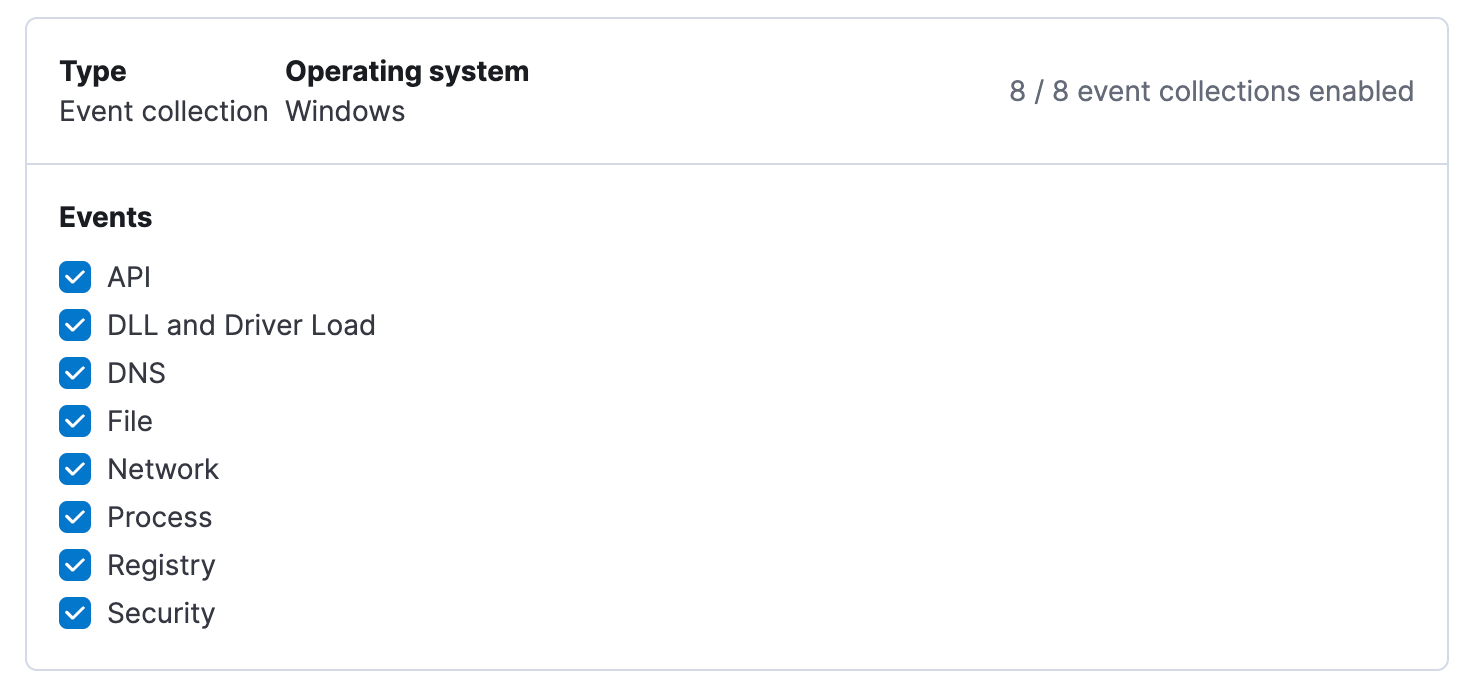
Event collection
Elastic Extended Security selectively collects system activity data to detect and prevent as many threats as possible, while carefully balancing storage use and system performance. By design, Elastic Extended Security focuses on collecting security-relevant activity rather than a complete record of all system events. The event data it generates may be aggregated, truncated, or deduplicated as needed to optimize for effective threat detection and prevention. Recent updates to our default settings have reduced event volumes by as much as 68%, helping you lower data storage costs and improve system performance. Want to see how we did it? Read our blog post: Less noise, more signal: How Elastic Extended Security slashed event volume.
Digging deeper: Investigate threats without data limits
Speed and context are everything in security investigations — and that means having all your data, instantly accessible, whenever you need it. Elastic Security is built to handle security telemetry at scale, so you can retain, search, and analyze vast amounts of data without compromise.
With searchable snapshots and flexible data tiers, Elastic lets you keep months or years of endpoint, cloud, and infrastructure data searchable — without blowing your budget. No more choosing between retention and performance.
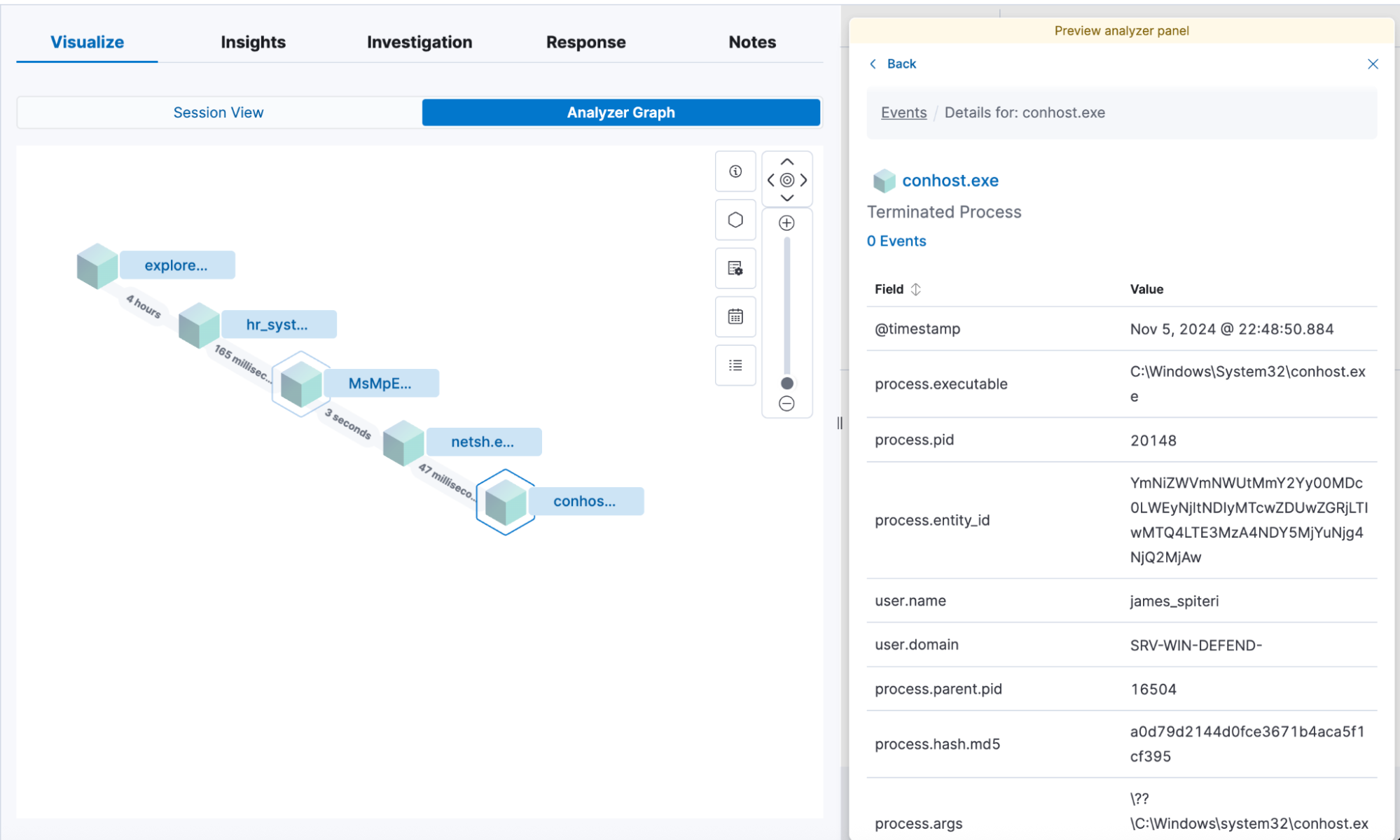
Paired with powerful investigation tools like Timeline, Session View, and an interactive process analyzer, analysts can quickly trace events, pivot between related activity, and uncover the full scope of an incident. The result: faster investigations, deeper insights, and decisions based on complete, reliable data. And thanks to our vendor-agnostic approach, these investigative workflows work seamlessly whether telemetry comes from Elastic, a third-party EDR, or a mix of both — ensuring investigations stay efficient and comprehensive, no matter what tools you’re running.
Open and transparent security
At Elastic, we know SOC analysts rely on transparency and trust to Extended Security against evolving threats. That’s why we made our protections-artifacts repository fully open, sharing the exact detection logic behind Elastic’s endpoint security — including YARA signatures and rules for Windows, macOS, and Linux. This level of visibility lets you understand what’s running under the hood, customize detections to fit your environment, and collaborate with the community to sharpen protections.
Openness isn’t just about sharing code — it’s about empowering you to stay ahead of attackers and keep your organization secure. Elastic also runs a public bug bounty program that covers EDR behavior detection rules, rewarding researchers for identifying ways to bypass detections. This helps security teams strengthen Elastic Extended Security’s protections and stay ahead of evolving attack techniques.
Elastic Security Labs: Open research, stronger defenses
Elastic Extended Security is powered by more than just technology — it’s fueled by the expertise of Elastic Security Labs. Our dedicated threat research team continuously tracks the latest adversary behaviors, malware campaigns, and endpoint attack techniques, translating those insights into actionable protections for Elastic Extended Security users. From new detection rules and machine learning models to advanced prevention capabilities, Security Labs ensures Elastic Extended Security stays ahead of evolving threats. By actively contributing open detections, research reports, and malware analyses to the broader security community, Elastic Security Labs strengthens defenses for both our customers and Extended Securityers everywhere.
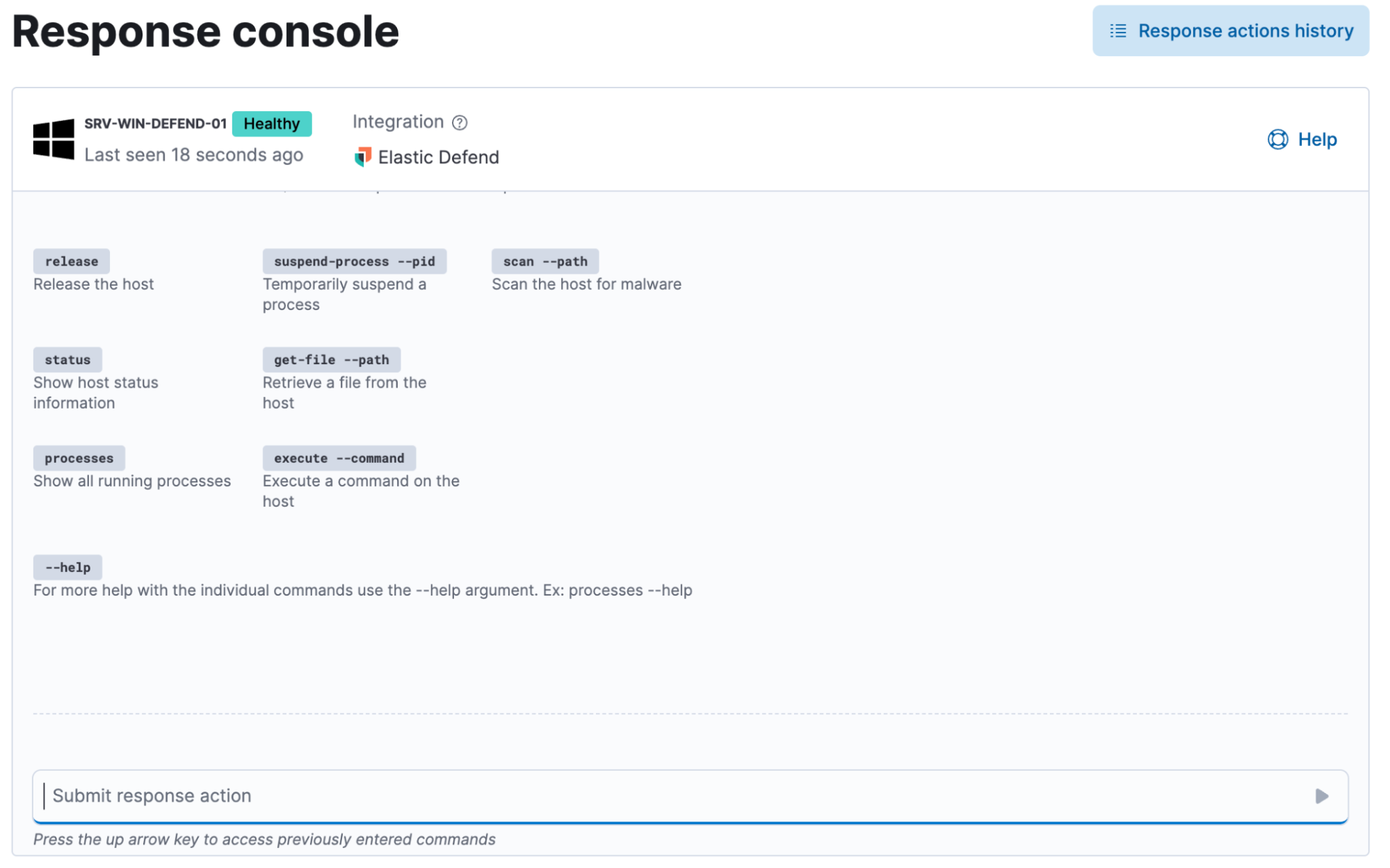
Stop threats in their tracks with response actions
Few things crank up the pressure in a SOC like an endpoint alert that might signal an active threat. Elastic Extended Security equips analysts with a powerful set of response actions to quickly contain and neutralize endpoint threats before they escalate. Right from the Elastic Security UI, analysts can isolate a host, kill malicious processes, and collect vital forensic artifacts like memory dumps or file metadata. These actions can be executed remotely and at scale, helping teams cut dwell time and stop attacks in their tracks. Powered by Elastic’s agent-based architecture, response actions are fast and reliable, and they work across diverse environments — giving SOC teams the confidence and control they need when it matters most.
Plus, Elastic’s truly vendor-agnostic approach enables seamless response orchestration across third-party platforms like CrowdStrike, Microsoft Defender for Endpoint, and SentinelOne — empowering SOC teams to execute containment and remediation directly from Elastic Security.
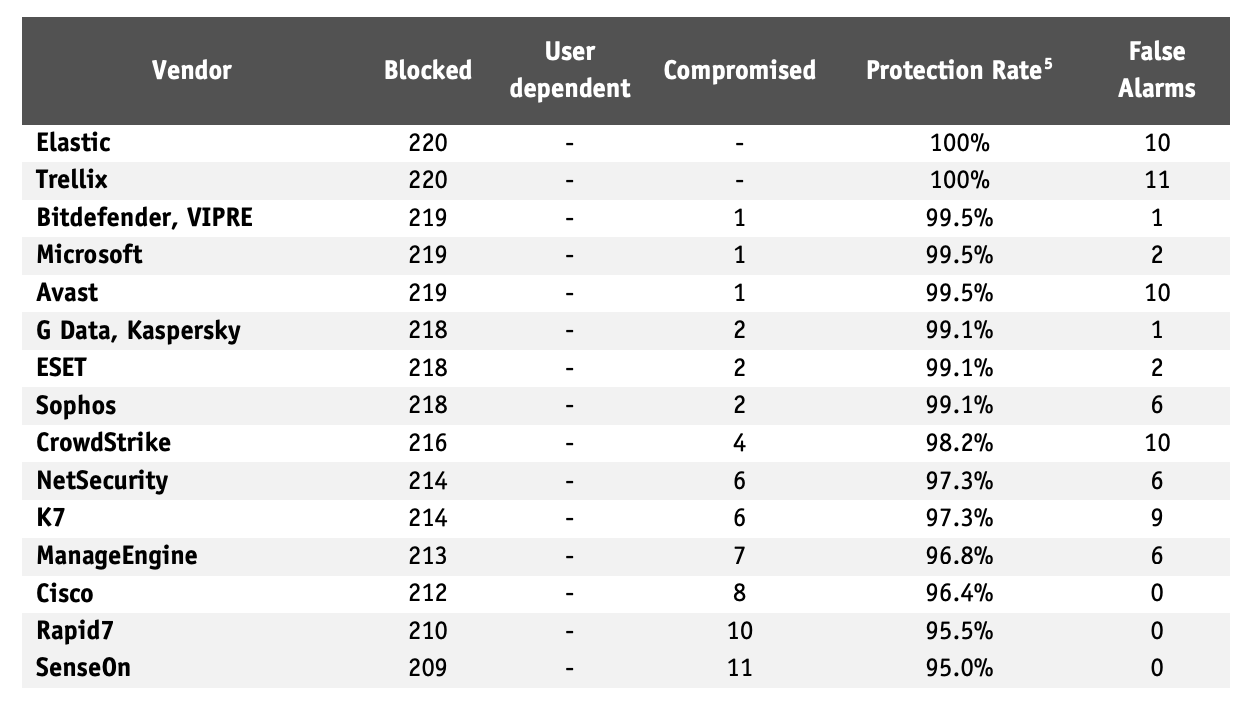
Just how good are Elastic Extended Security protections?
We think Elastic Extended Security is one of the best protection engines in the industry — but don’t just take our word for it. Independent third-party testing continues to validate the strength of our endpoint security capabilities.
In the latest AV-Comparatives Business Security Test (April–May 2025), Elastic Extended Security achieved a 100% protection rate against 200+ advanced attack scenarios and 1,000+ real-world malware samples. That’s top-of-the-table performance in one of the industry's most rigorous evaluations.
And it doesn’t stop there. Elastic Extended Security also earned a Grade A certification from VB100, following its intensive real-world malware and false positive testing.
These results reinforce what our customers already experience: Elastic Extended Security consistently delivers reliable, high-fidelity protection against today’s most sophisticated threats — while staying lightweight and easy to manage as part of the Elastic Security platform.
Get started with Elastic Security
Join the growing number of businesses that trust Elastic Security to protect their organization against attacks. Experience the peace of mind that comes with knowing your endpoints — and organization as a whole — are secure against the latest threats. Start your Elastic Security free trial and discover the difference that our protection can make. Visit elastic.co/security to learn more and get started.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos, or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.