It's time for the defense and intelligence community to upgrade endpoint security
.png)
For more than 20 years, the US Intelligence Community (IC) and Department of Defense (DoD) have relied on a legacy Host Based Security System (HBSS) to provide basic endpoint security on critical networks. This solution has generally served its purpose by checking the box for endpoint security.
However, most agencies still lack a truly integrated cross-operating system and cross-domain solution for endpoint detection and response (EDR). Elastic's unified endpoint and extended detection and response (XDR) capabilities combined with powerful native and third-party integrations offer an opportunity to scale, observe, and protect the DoD’s endpoint landscape more effectively.
Endpoint security from Elastic
Elastic’s endpoint security capabilities — born from the acquisition of Endgame in 2019 — bring years of battle-tested endpoint security and threat prevention expertise to the IC and DoD. These capabilities extend across Linux environments, air-gapped networks, and fly-away kits. This isn’t a bolt-on or third-party integration; it's a native component that integrates seamlessly with Elastic's AI-powered security analytics platform. Elastic also has a proven record of delivering security solutions at scale across the US federal government, including:
Cybersecurity and Infrastructure Security Agency (CISA)
Hunt and Incident Response Team (HIRT)
US Air Force Cyberspace Defense — NIPR/SIPR, SIEM (600,000+ endpoints)
C3T — All tactical endpoints covered by Elastic endpoint security capabilities
Scalability for mission environments
As data volumes grow exponentially, Elastic easily scales to meet the demand. Elastic delivers endpoint security and XDR, correlating endpoint, network, user, and cloud telemetry at search speed across petabytes of data all in a single platform.
Elastic goes even further by providing:
Best-in-class integrated EDR: Elastic’s agent protects Windows, macOS, and Linux operating systems with the award-winning prevention and detection capabilities originally pioneered at Endgame and evolved into a scalable platform for modern threats. Advanced malware, behavioral, memory, and ransomware defenses are included out of the box.
Hybrid networks ready for public sector: No cloud-connected artifacts. Deploy wherever your mission takes you — on-premises, on AWS GovCloud, on Elastic Cloud, or in a hybrid environment. Elastic is built to operate in disconnected, intermittent, limited availability networks (DILs) and air-gapped environments.
Policy enforcement and compliance: Government agencies must meet stringent security and regulatory standards. Elastic Device Control enables administrators to enforce device policies aligned with Federal Risk and Authorization Management Program (FedRAMP), DoD Impact Level 5 (IL5), and Criminal Justice Information Services (CJIS) requirements. For example, agencies can restrict device access based on user roles, block unapproved peripherals, and generate audit logs for compliance reporting.
Integration with other vendors: Many organizations rely on multiple endpoint vendors; Elastic meets them where they are. Elastic’s vendor-agnostic platform seamlessly operationalizes data from third-party endpoint tools alongside Elastic’s own endpoint agent — all within a unified detection and response workflow. No silos. No pivoting.
- Unlimited deployment model: With Elastic, every user gets unlimited agents. This allows teams to scale up during incidents and maintain a resilient baseline across thousands of machines without hidden per-endpoint costs. Elastic delivers a mission-ready platform that protects today’s infrastructure and scales to meet tomorrow’s complexity. This is endpoint security the way it was meant to be: flexible, powerful, and unified.
Elastic delivers proven endpoint excellence
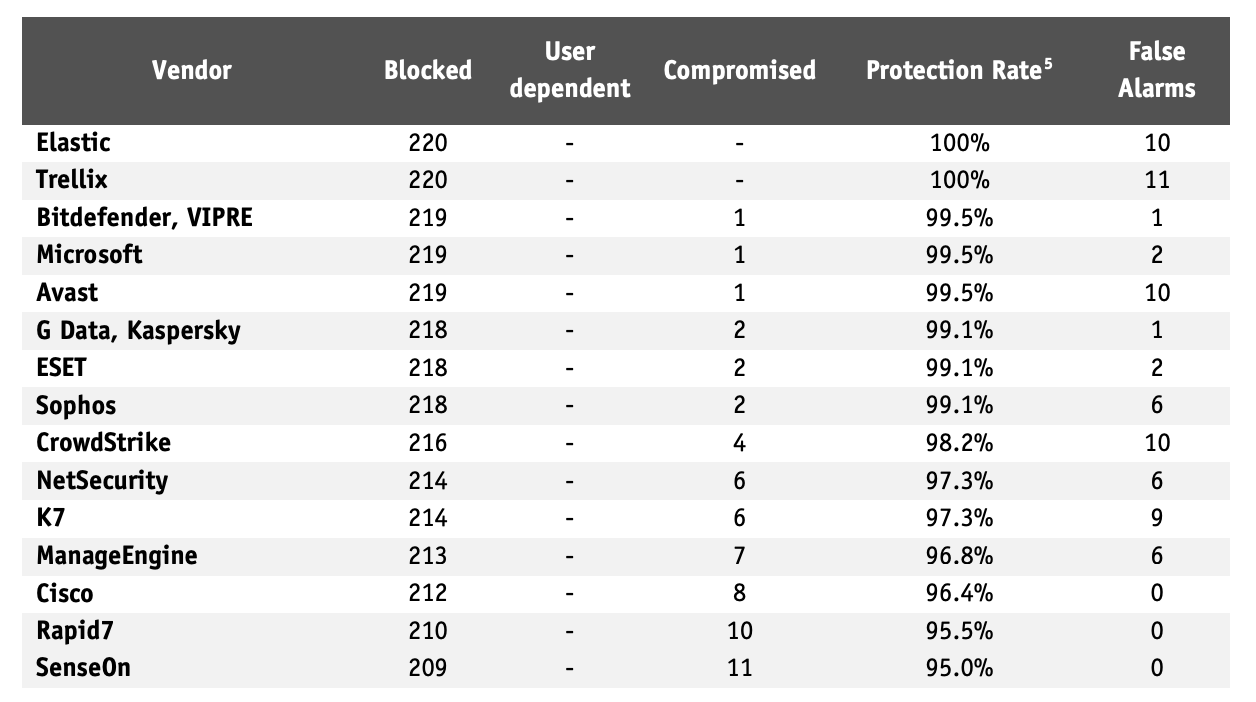
Elastic’s endpoint security capabilities are one of the best protection engines in the industry based on independent third-party testing. In the AV-Comparatives Endpoint Prevention and Response 2025 Report, Elastic Security’s results showed near-perfect prevention rates, minimal false positives, no workflow delays, and favorable total cost projections.
In another test series, the AV-Comparatives Business Security Test (April–May 2025), Elastic achieved a 100% protection rate against more than 200 advanced attack scenarios and 1,000 real-world malware samples. That’s top performance in one of the industry's most rigorous evaluations.
And that’s not all. Elastic Security was also recently recognized as a Leader in the IDC MarketScape: Worldwide Extended Detection and Response Software 2025 Vendor Assessment. IDC specifically recognized Elastic’s native endpoint security capabilities from Elastic Defend. Its real-time behavioral analytics, deception techniques, and active prevention controls surfaced as strengths. IDC also noted that Elastic is well positioned to defend against ransomware by its ability to monitor the endpoint for rapid file encryption, suspicious process spawning, and file system tampering.
Integrated AI for speed and precision
In today’s fast-paced threat landscape, speed and precision are everything. Elastic Security puts AI to work for your team with powerful, analyst-centric features designed to cut through noise and accelerate response.
Attack Discovery automatically surfaces high-risk attack paths and suspicious behaviors by analyzing detections and endpoint telemetry in real time — no manual pivoting or hunting required.
Elastic AI Assistant allows analysts to instantly summarize incidents, get contextual explanations, and receive guided next steps tailored to each investigation.
Automatic Import streamlines onboarding and normalization of custom data, giving analysts immediate visibility and context regardless of the data source.
Furthermore, Elastic emphasizes open and transparent security through a community-reviewed detection rules repository, an active bug bounty program, and a dedicated threat research team. Elastic Security Labs continuously tracks emerging adversary behaviors, malware campaigns, and endpoint attack techniques, translating those insights into actionable protections for Elastic Security users.
Next steps for mission-focused EDR
Elastic is a robust solution for organizations seeking to secure their endpoints and outpace evolving threats. To learn more, reach out to our team.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos or registered trademarks of Elasticsearch B.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.