Securing your Elastic Stack is now simpler than ever

In 8.0, we are excited to bring simplified security features to all of our users. Starting in 7.1, we made all the features that are required to keep your Elastic Stack secure available for free to everyone.
Yet, we know that setting up security is no fun and that you need to focus on your project goals. Good news for you! As of 8.0, Elastic Stack security is on by default for self-managed clusters, with next-to-zero configuration effort. Just spin up the new Elasticsearch and Kibana release and continue making the most of the Elastic Stack, we've got your back! If you’re using the Elastic Cloud, not to worry — we already take care of security for you.
All the security you need with none of the hassle
Simplified security includes the following features, which span across multiple layers and products and are enabled by default:
- User authentication
- User authorization with Role-Based Access Control
- Multi-tenancy with Kibana Spaces
- Encrypted node-to-node communication with TLS
- Encrypted communication with the Elasticsearch API with HTTPS

Of utmost importance to us on the Stack Security team is that our users benefit from as much security as possible when installing and running the Elastic Stack — while at the same time eliminating any friction. So we set up an ambitious goal: to deliver all the previously listed security features in a streamlined, effortless, and transparent fashion. We believe that you should not spend your time on cumbersome configurations. At the same time, you should not compromise on security.
In addition, simplified security does not use common defaults across different instances, which gives a false sense of security when features are technically enabled yet are based on known "secrets." In contrast, during the boot process, each new deployment creates and uses unique credentials, certificates, and encryption keys.
Today, we are excited to bring you the product of this ambitious initiative.
If you use Elastic's managed cloud service or orchestration products, Elastic Cloud Enterprise (ECE) and Elastic Cloud on Kubernetes (ECK), nothing changes for you — stack security is already configured by default.
To get started, simply spin up Elasticsearch and Kibana, connect them using the new web UI, and they work together securely, out of the box. And of course, you can customize whatever you need in order to meet your organization's security requirements.
Spin up a new deployment securely in two steps
When you download and run Elasticsearch for the first time, you will receive an enrollment token and the credentials for the elastic superuser. This is literally all the information you need in order to get the Elastic Stack up and running with the security features we described before, so keep it handy and private.
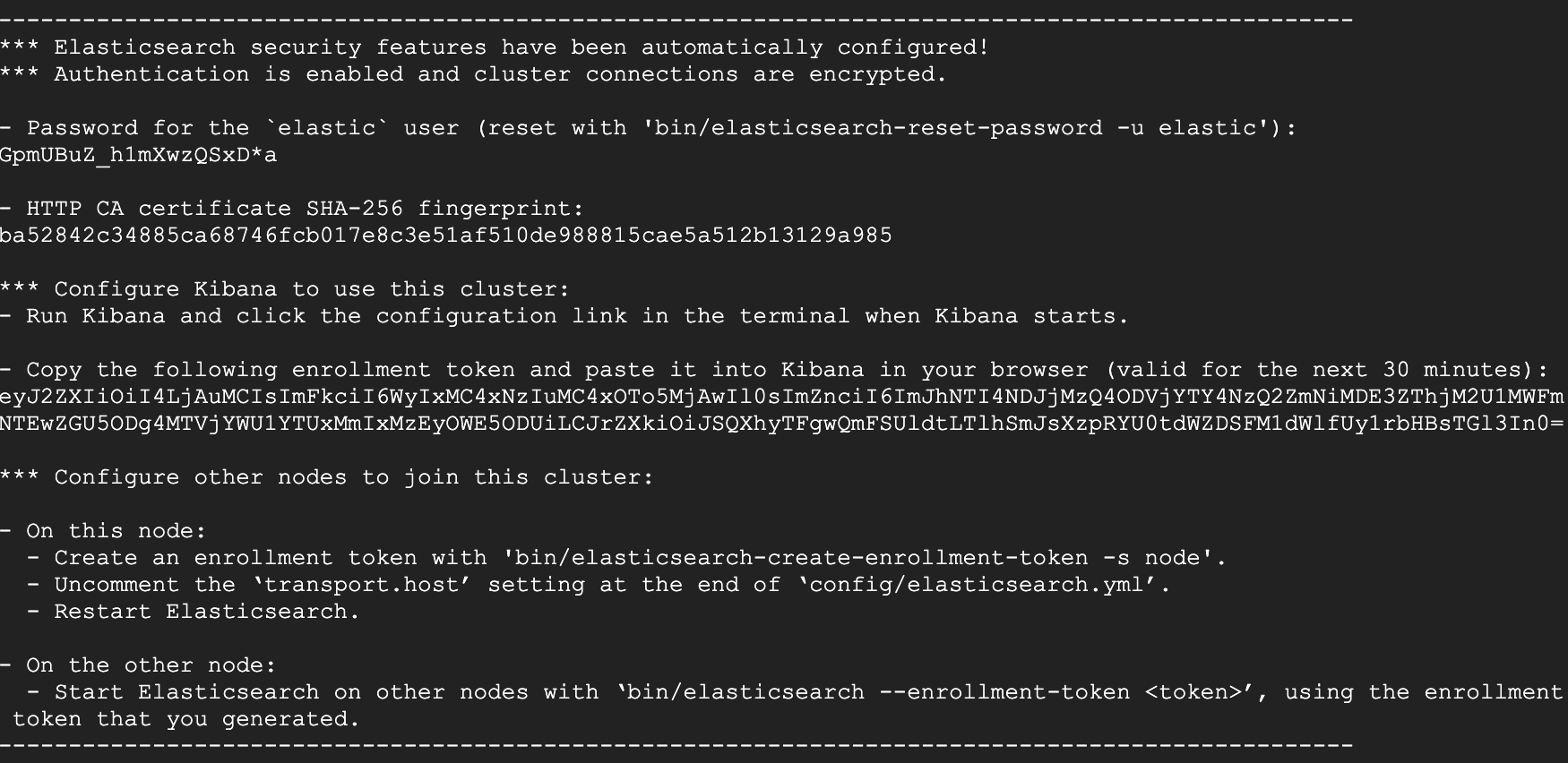
In the next step, you’ll run Kibana for the first time and be pointed to a UI that will help you set up Kibana and connect it to Elasticsearch. In Kibana’s interactive setup UI, paste the enrollment token.
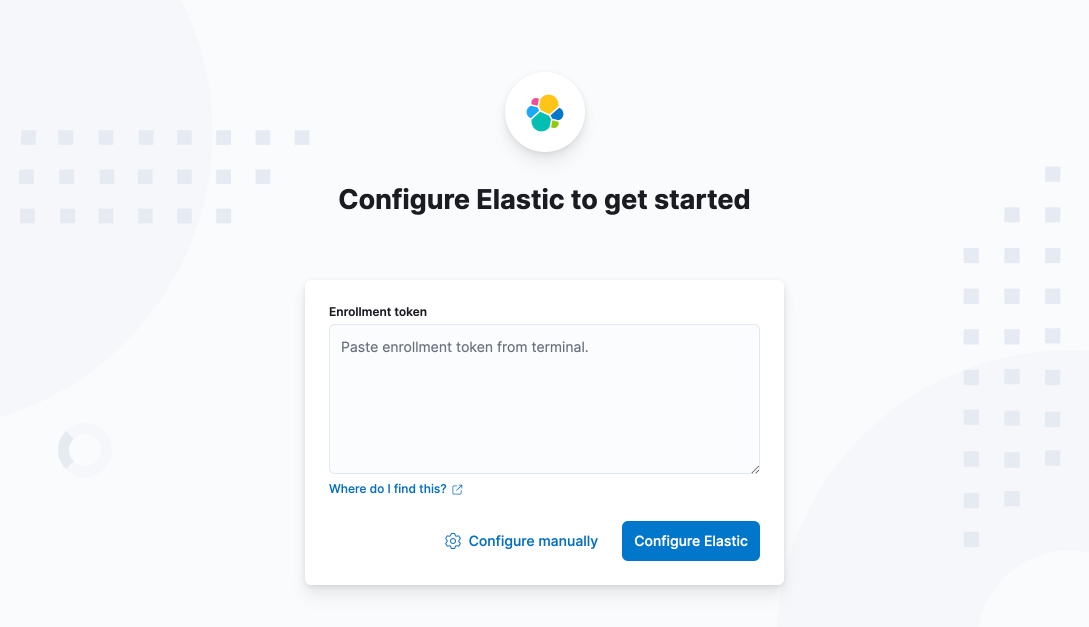
Kibana will set up everything without any configuration required from you and will connect over TLS to Elasticsearch.
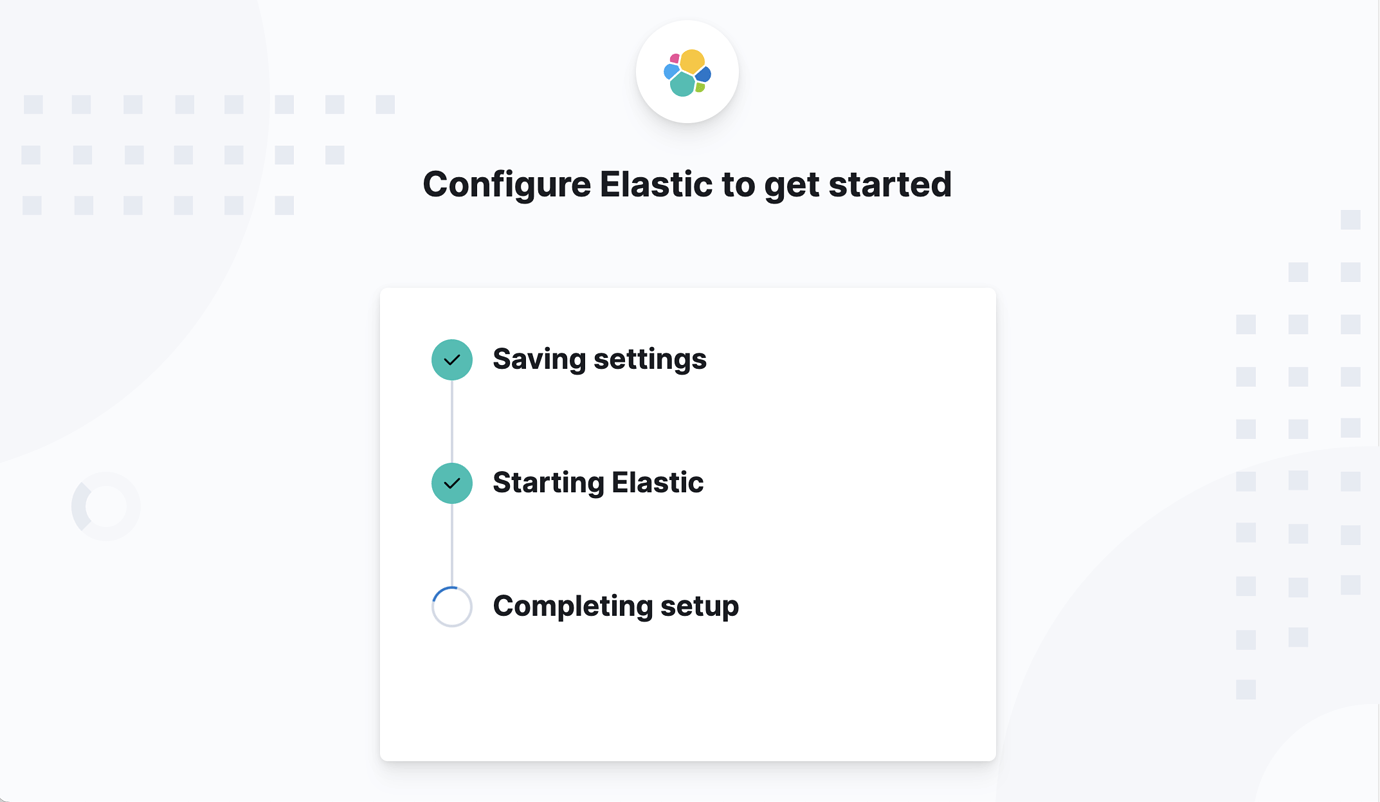
Once setup completes, you are ready to go. Login as a superuser with the credentials that were provided in the Elasticsearch step and start using your new secure deployment.
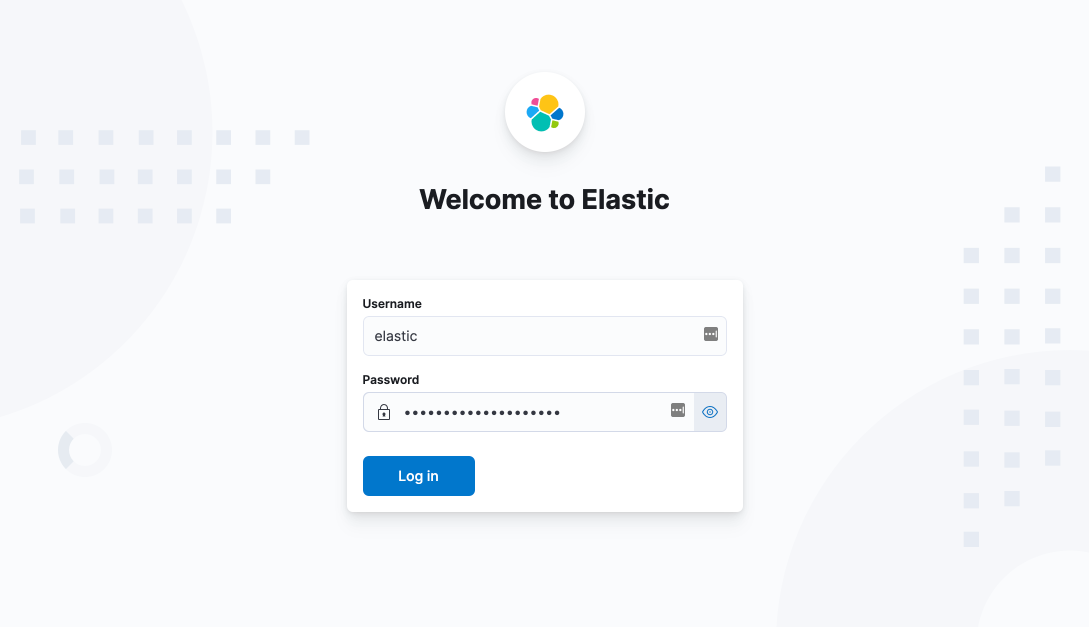
If you need to add more nodes to your cluster, obtain an Elasticsearch enrollment token by running bin/elasticsearch-create-enrollment-token -s node.
Bear in mind that the autoconfiguration process is executed only when a new cluster is started for the first time. If there is an explicit security configuration already set, or if the cluster has been upgraded from a previous version, no changes will be made. The Upgrade Assistant will guide users through the required steps to prepare an upgrade from 7.17.
A quick peek under the hood
When you download and run Elasticsearch for the first time, Elasticsearch will transparently perform the following tasks:
- Set up for TLS: It will generate a Certificate Authority, the transport and HTTP layer certificates, as well as all the related "goodies" required for the TLS dance — including of course the private keys, certificates fingerprints, etc. It will also store passwords securely.
- Set up security settings: This also includes the ones for transport and HTTP encryption: xpack.security.ssl.http.enabled and xpack.security. ssl.transport.enabled
- Prepare for incoming connections: It will produce a special type of token, an enrollment token, which encapsulates all the information Kibana needs in order to connect to Elasticsearch and enables its enrollment APIs, which listens for new connections.
- Generate the password for the elastic built-in superuser.
All these tasks are transparent to the user.
Now, when a user runs Kibana for the first time, they will only need to enter the enrollment token in the new Kibana startup UI and Kibana will unpack all the information it needs in order to connect to Elasticsearch. With the enroll request, Elasticsearch will generate and set the password for the kibana_system user. Kibana will save the configuration and credentials in the kibana.yml and the keystore.
Note that Kibana will not enable web HTTP TLS with the browser. This is an additional step that we recommend considering in order to increase the security of the system further.
Impact on the Stack, Elastic solutions, and other products
We want you to be confident that security is working as expected. We now only allow our Elasticsearch security module to be loaded — it is no longer possible to replace this with a third-party plugin that can intercept and manage incoming REST requests.
As for solutions, Elastic Observability, Security, and Enterprise Search already assume that Stack Security is enabled. Nothing changes here, except that it will be easier to set up these components (since Stack Security is already enabled by default). Other products like Elastic Agent are automatically set up to securely connect to Elasticsearch.
Get started with the Elastic Stack 8.0 today
Download Elasticsearch and Kibana to create your secure Elastic Stack deployment. If you want to learn more about simplified security, please see our guide. Otherwise, you can spin up a secure and free cloud trial deployment on the Elasticsearch Service to start your search, observe, protect journey.
We welcome your feedback and as always, you can find us on Twitter (@elastic) and the Elastic forum.