Elastic Security 7.6.0 released
Editor’s Note — August 19, 2020: The Elastic Endpoint Security and Elastic SIEM solutions mentioned in this post are now referred to as Elastic Security. The broader Elastic Security solution delivers endpoint security, SIEM, threat hunting, cloud monitoring, and more.
Elastic Security 7.6 builds on the strengths of Elastic Endpoint Security and Elastic SIEM to deliver unparalleled visibility and threat protection through a unified interface. This release automates the centralized detection of threats in the SIEM app and enhances endpoint detection capabilities on Windows hosts. Access to new data sources and improvements across the Elastic SIEM app further empower security practitioners to accelerate detection and response. Let’s drill down into what’s new in Elastic Security 7.6.
Approach zero dwell time with a new SIEM detection engine and MITRE ATT&CK™-aligned rules
Elastic Security 7.6 introduces a new SIEM detection engine to automate threat detection, minimizing mean time to detect (MTTD) and freeing up your security team for security tasks requiring human intuition and skill. With Elasticsearch at its core, Elastic SIEM already accelerates security investigation time from hours to minutes. This new automated detection capability further reduces dwell time by surfacing threats that would otherwise be missed.
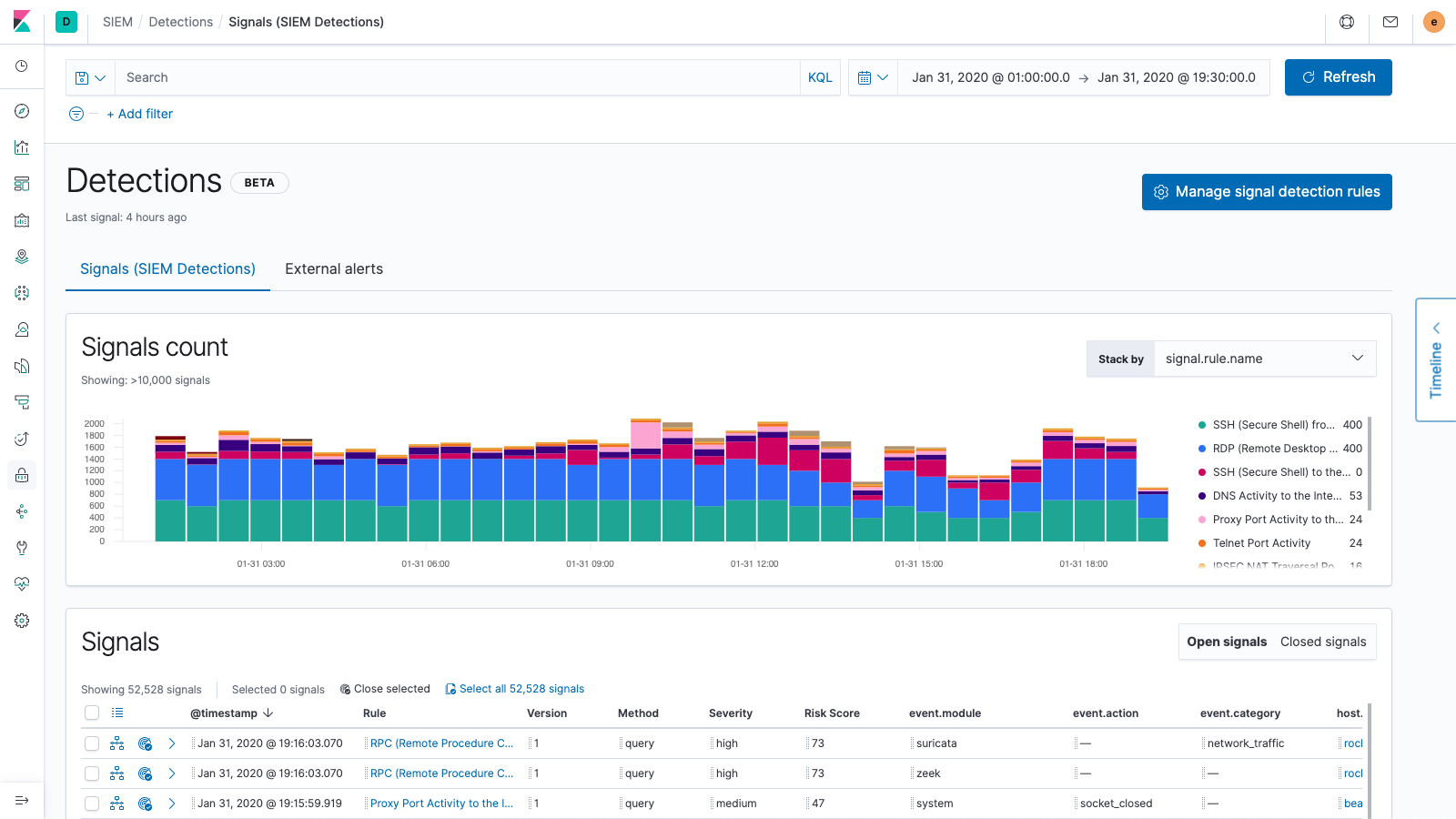
Elastic is also releasing an initial set of nearly 100 out-of-the-box rules aligned with the ATT&CK knowledge base to surface signs of threats often missed by other tools. Created and maintained by the security experts at Elastic, the rules automatically detect tools, tactics, and procedures indicative of threat activity, and will be continually updated to address new threats. Risk and severity scores associated with signals generated by the detection engine enable analysts to triage issues rapidly and then turn their attention to the highest-value work.
“Elastic has helped our security team focus on what matters by equipping us with the tools we need to efficiently search millions of logs while reducing the number of alerts to a volume that our security team can manage,” said Maxim Verreault, Security Manager at Skytech Communications. “With the release of 7.6, out-of-the-box signal detection rules in Elastic SIEM enable us to automate analysis across our observability data and detect and respond to threats the moment they happen. Elastic Security 7.6 also provides a great way for the community to connect, as we, the security folks, will be able to share custom signal detection rules so that everyone can benefit from them and detect new emerging threats.”
Rules operate on Elastic Common Schema (ECS)-compliant data gathered from Windows, macOS, and Linux systems, as well as network information from other sources. Security teams have the option to create or customize rules, but should never need to rewrite them for new ECS-compliant data sources added to their environment.
Built-in Elastic SIEM threat detection rules are developed and maintained by the security experts at Elastic, and complement both the machine learning-driven anomaly detection jobs of the SIEM app and host-based protections of Elastic Endpoint Security. Speaking of...
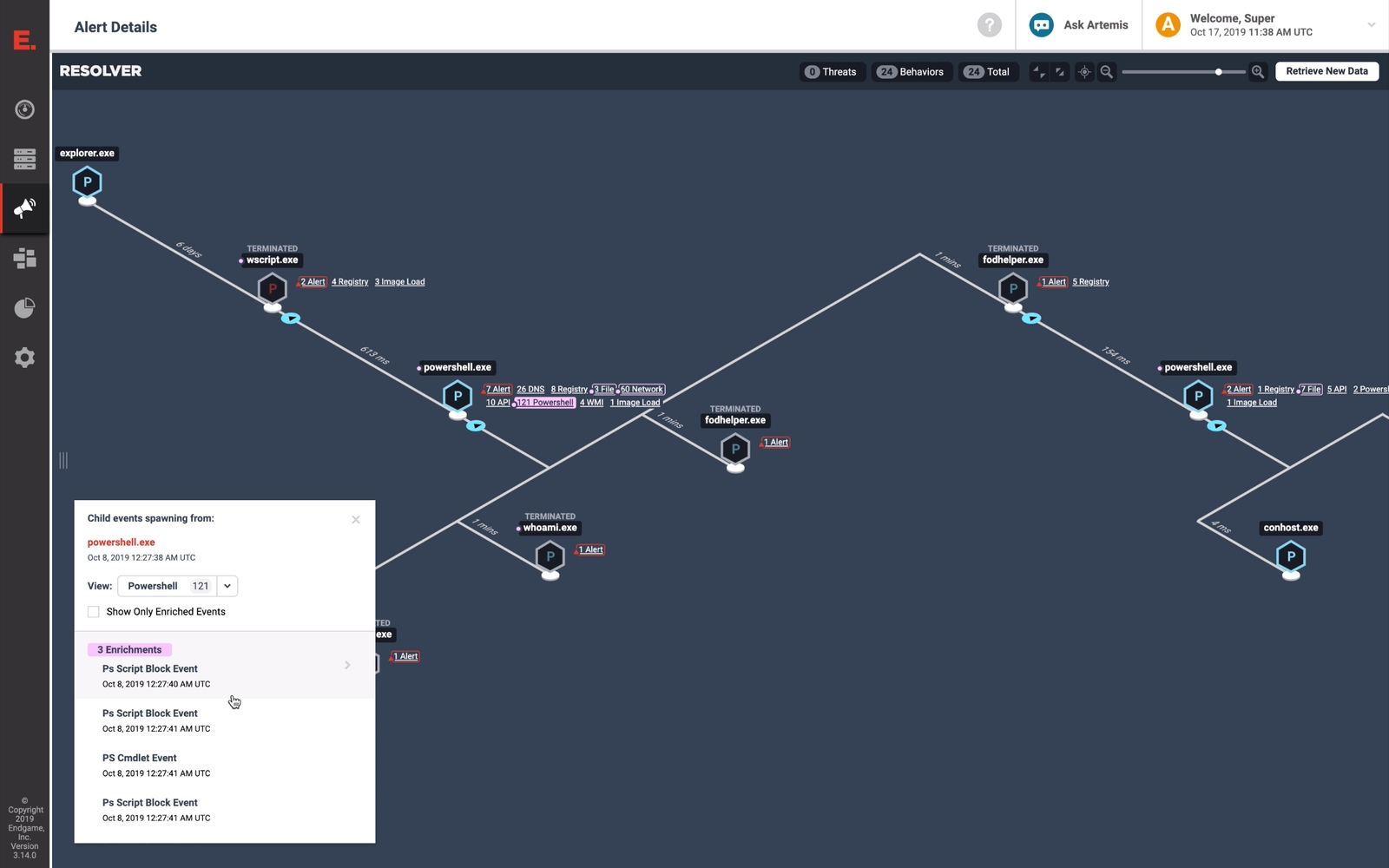
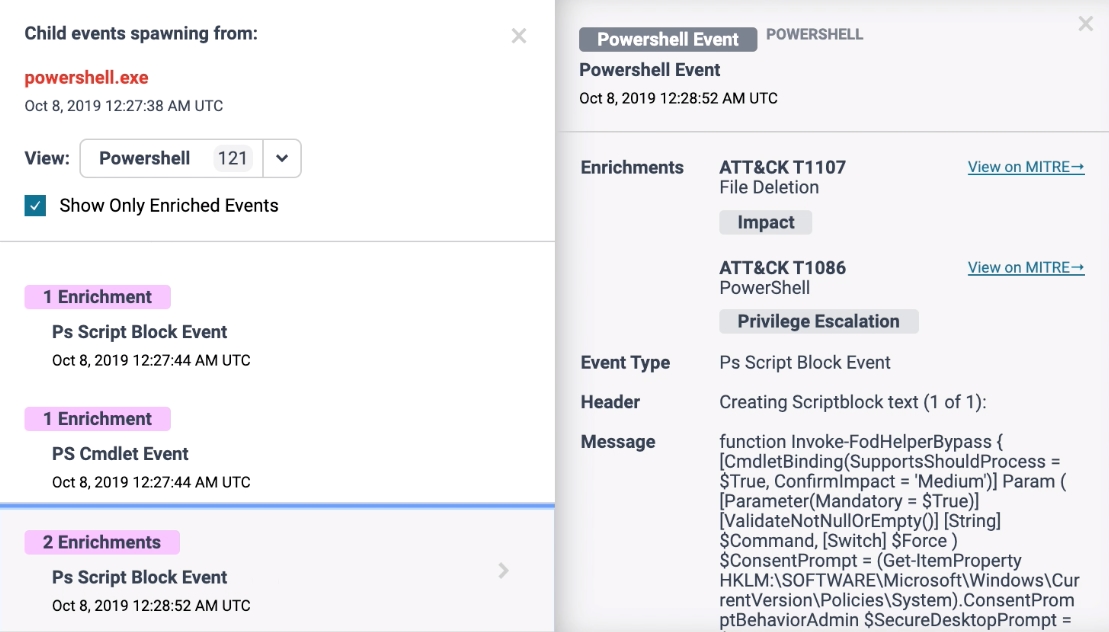
Achieve unprecedented visibility into Windows endpoints
Elastic Security 7.6 delivers unprecedented levels of visibility and protection to Windows systems, which are a major attack target due to their ubiquity and lenient user permissions model. The release deepens visibility into Windows activity and resiliently collects and enriches data from locations otherwise vulnerable to the evasion techniques of advanced threats.
New out-of-the-box detections leverage this data to detect attempts to capture keyboard inputs, load malicious code into other processes, and more. Practitioners can pair events generated by these detection rules with automated responses (e.g., kill a process) to achieve layered prevention. Combining this visibility and protection with the existing prevention, detection, and response capabilities for macOS and Linux systems provides Elastic Endpoint Security users with complete protection across their entire environment.
Reduce MTTD by quickly seeing what matters most
The new Elastic SIEM app Overview page and broader workflow enhancements enable security practitioners to hunt for and investigate threats fast. Users can jump right into an investigation by opening a timeline, viewing the latest detection signals, and reviewing alerts from external sources like Elastic Endpoint Security, Palo Alto Networks, Suricata, Zeek, and others. Wherever you are in the SIEM app, you’re never more than a click away from its integrated threat detection and anomaly detection capabilities.
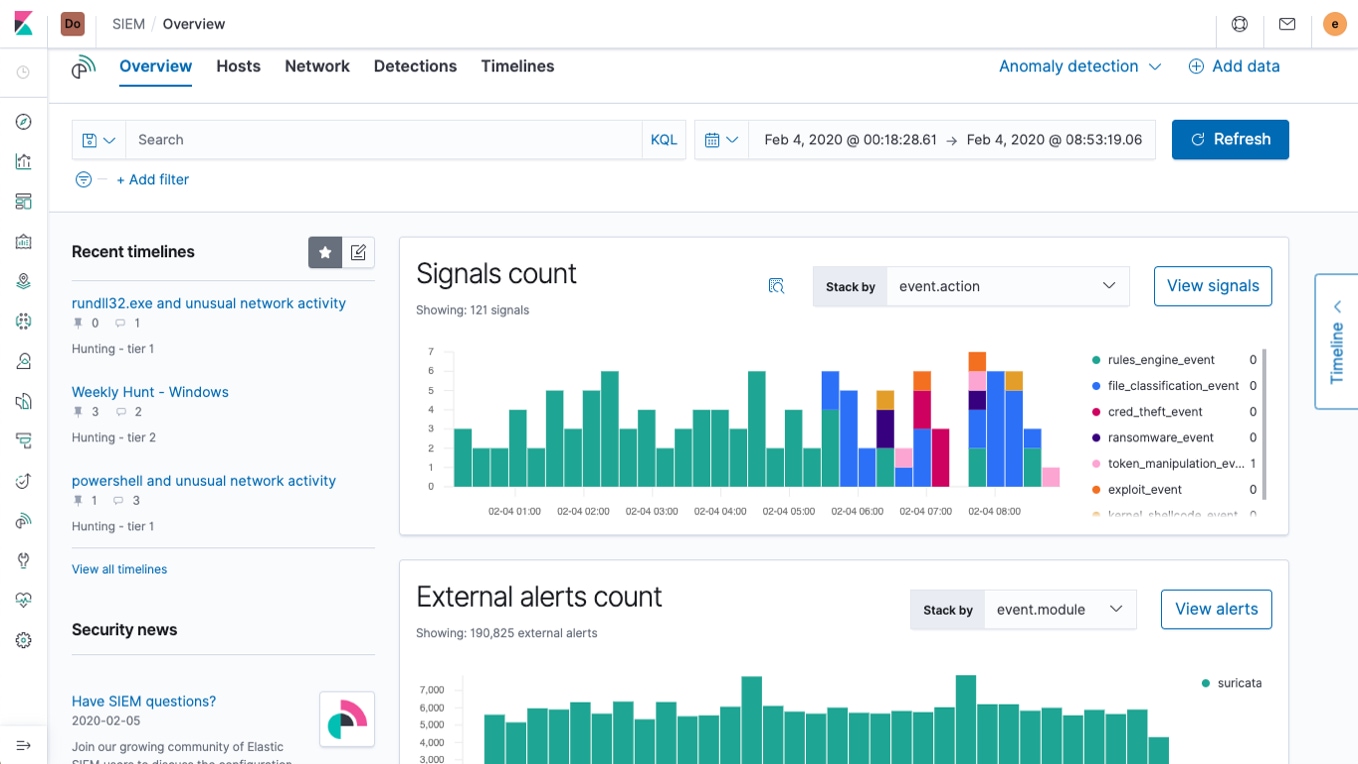
Analysts can also increase operational awareness with new event, alert, and signal histograms, and explore the new and enhanced visualizations in the Hosts and Network views for more specialized analysis.
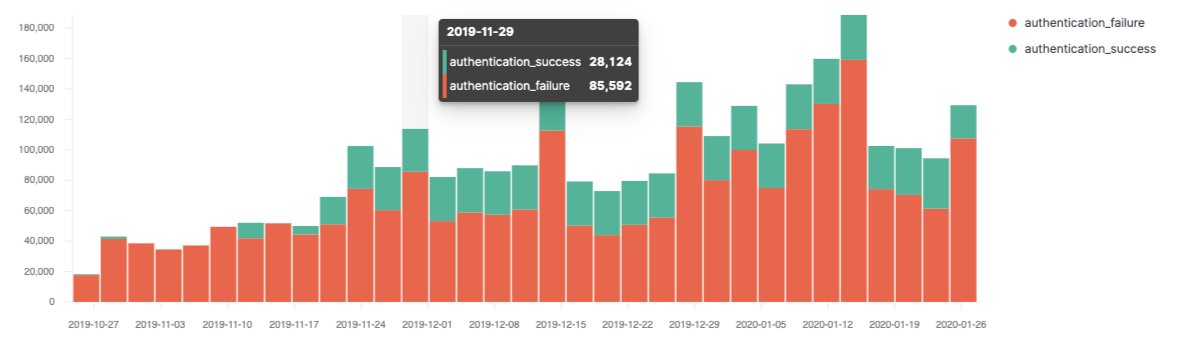
Keep an eye on your applications
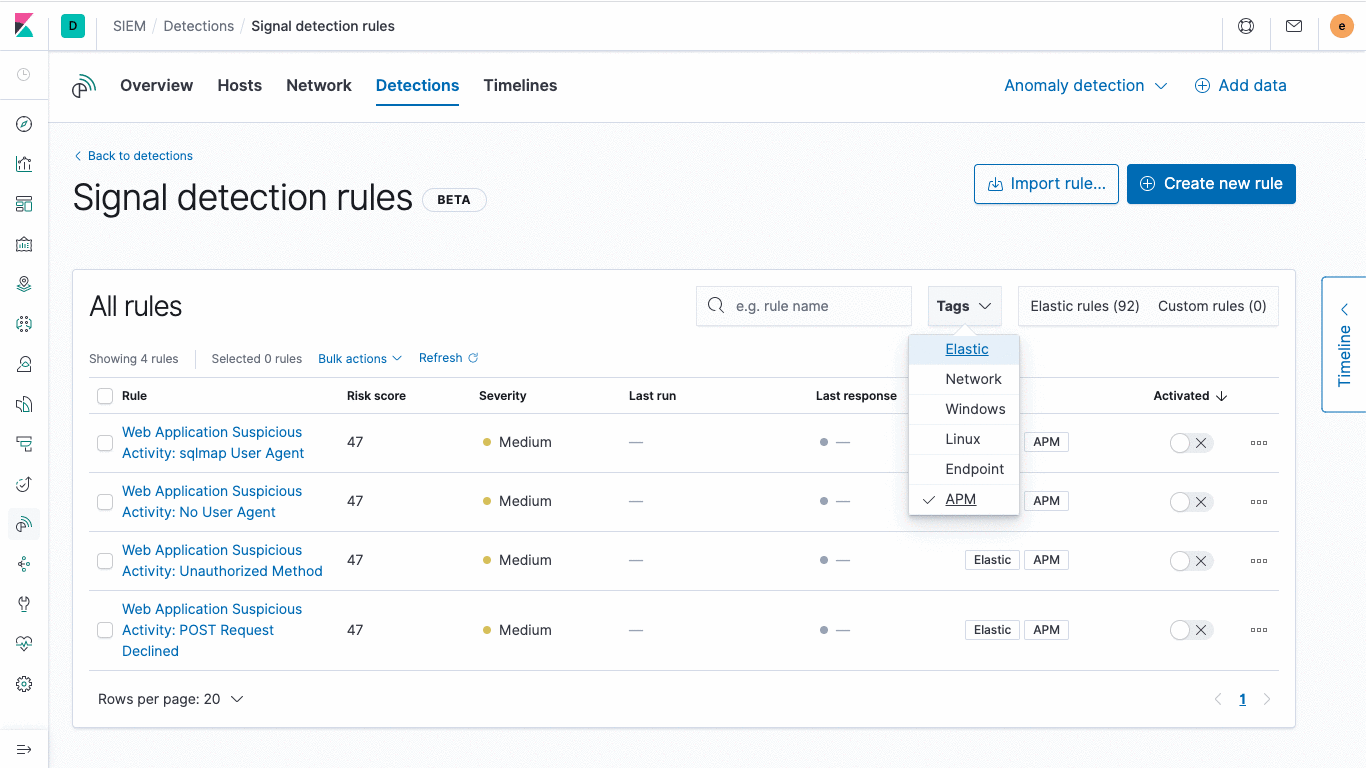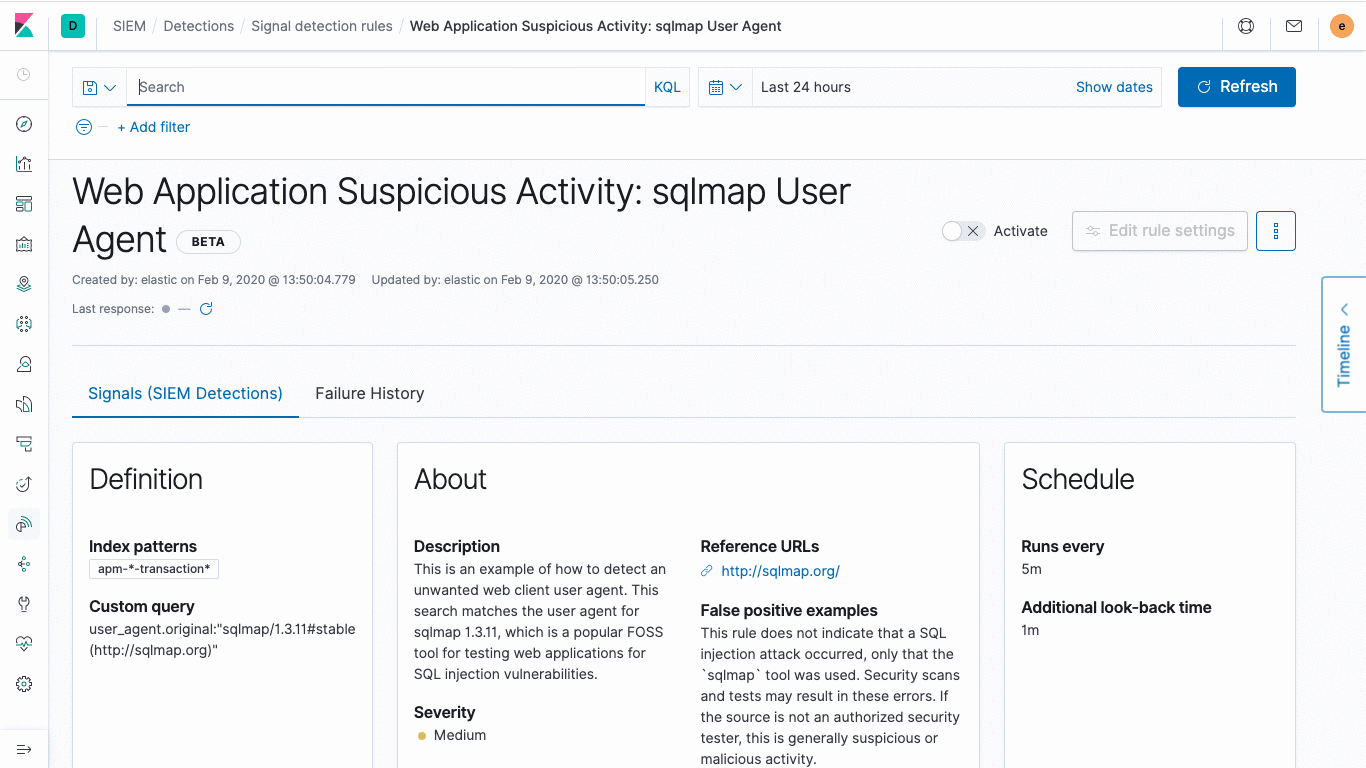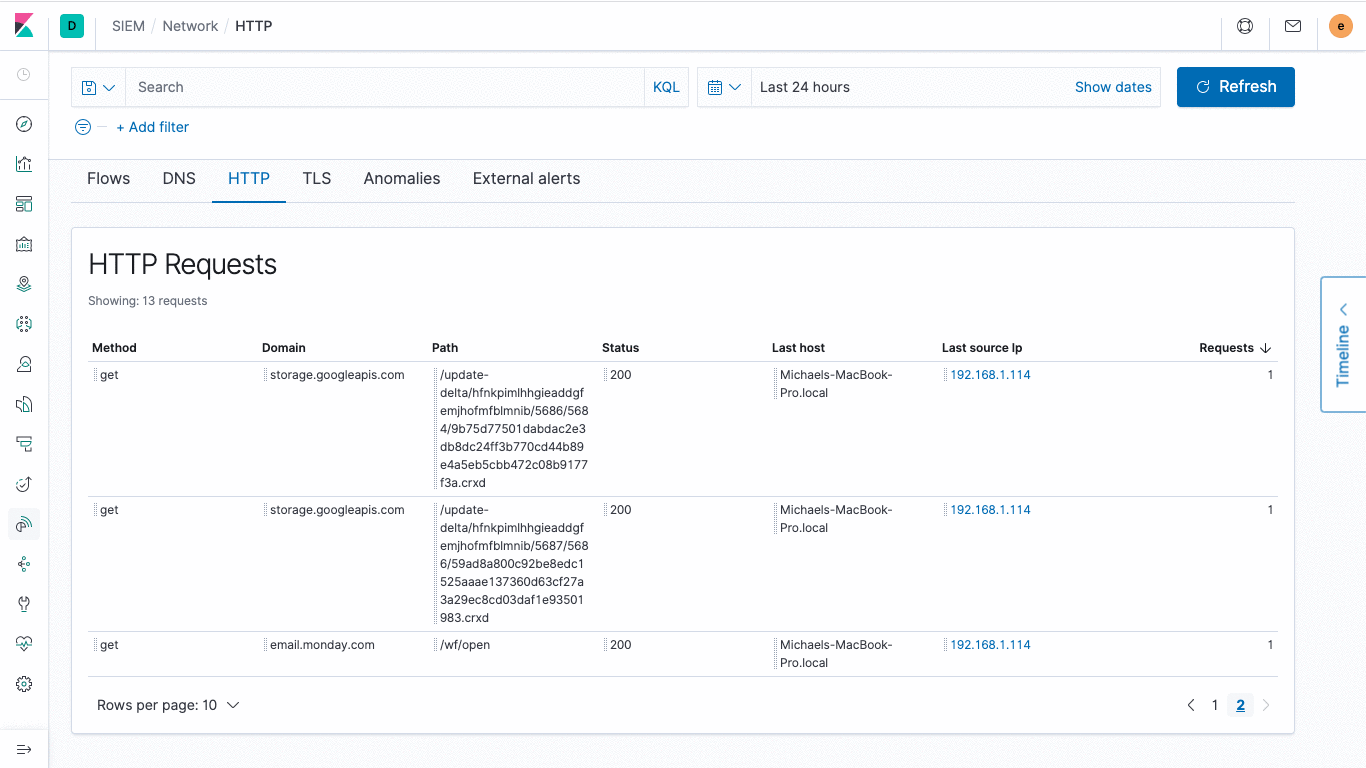
Elastic SIEM also now provides curated visibility into HTTP data, giving you the power to view Elastic APM data from directly within the SIEM app. Multiple out-of-the-box Beats modules provide access to additional ECS-compliant HTTP data, allowing you to easily inspect and visualize all web transactions in one unified view. Dig around and see what you can find — and be sure to also let your DevOps friends have a look sometime soon.
Monitor your cloud data
We’re making it ever-simpler to ingest data into the Elastic Stack for centralized visualization and analysis. 7.6 introduces support for AWS CloudTrail data and enhances support for Google Cloud Platform, providing essential visibility into the modern attack surface. Data in the CEF format, whether from the cloud or elsewhere, is also easier than ever to visualize thanks to our updated CEF module for Filebeat.
Get started today
Want to give Elastic SIEM a spin? Experience our latest version on Elasticsearch Service on Elastic Cloud or try an Elastic SIEM demo. Already have ECS-formatted data format in Elasticsearch? Just upgrade to 7.6 of the Elastic Stack to get on the hunt.