5 practical concepts for building trust in government digital strategies with Elastic

In a previous blog post, we explored some recurring concepts in the digital strategies of European countries. Here, we’ll dig a little deeper and explore how Elastic can help the public sector meet these priorities with efficiency and security.
We’ll explore five strategic concepts that directly align with the pillars in the Netherlands' Digital Strategy (NDS)1 but are also reflective of other countries’ strategies:
Open source and open standards
Sovereign infrastructure
Responsible AI
Cybersecurity and resilience
Data driven government
Open “everything”
From inception, openness has been a cornerstone of Elastic. But open has many different interpretations. Often, it is simply equated with software that is developed in the open, where code is shared in public repositories, such as GitHub. At Elastic, we recognized early that one of the superpowers of open source development is that more eyes looking at the code will surface issues sooner rather than later. This means that there’s a community to help threat hunt and remediate for Elastic Security — an amazing advantage.
But open means more than that. It also implies that roadmaps and priorities are not set by a single organization. By listening to our large user community, Elastic builds tools and features that are useful and sought after. This also requires open and well-documented APIs, integration libraries for developers, and a data store that is not dependent on proprietary and/or closed formats.
If open has one superpower, it’s community. It stands for bringing people together, so they can learn from each others’ successes and failures and build on achievements by peers. In the Netherlands alone, the Elastic community is over 3,000 people strong!2
Trusted globally and headquartered in the Netherlands, Elastic helps Dutch and European public organizations — ranging from ministries and regulatory bodies to municipalities and executive agencies — gain visibility, better control, and insight over their data.
Sovereign infrastructure
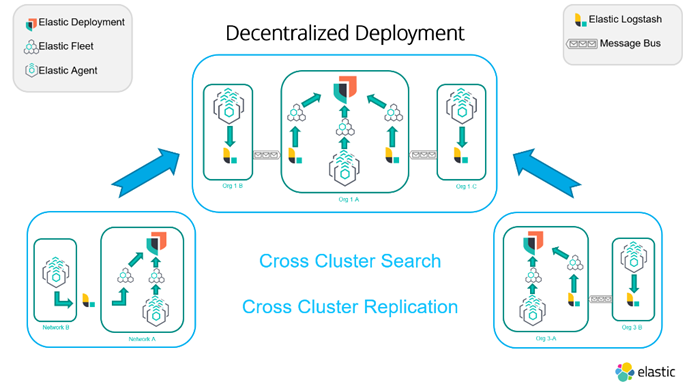
As the global political climate continuously shifts, the concepts of government or sovereign infrastructures are gaining momentum again. While large cloud providers bring broad capabilities, they may face some inherent limitations, which is why partnering with smaller local infrastructure can be a good option for sovereign cloud solutions for the public sector.
Given that this space continues to evolve, it’s difficult to predict future needs. In turn, this makes a flexible platform even more of an advantage. Platforms like Elastic that offer a variety of deployment options — your own data centers, in private/public/sovereign cloud environments, or on standard hardware or complex microservices architectures — without any loss of functionality can enable each organization to choose the option that best fits their needs and mission.
Deciding on deploying open, infrastructure-agnostic solutions like Elastic comes with the freedom to migrate to (and sometimes back from) one deployment model to another. This guarantees time invested in making teams knowledgeable and productive with the technology is never lost.
It also very neatly solves the “data gravity” problem where hybrid deployments are the standard deployment model to avoid costly and time-consuming movement of data. Simply keep the data where it is created and use Elastic as a distributed data mesh to search and analyze your data holistically. Elastic cross-cluster search and cross-cluster replication capabilities allow for distributed deployments where access control is strictly defined and enforced through role-based access control (RBAC) and attribute-based access control (ABAC).
Responsible AI
Public organizations have a big responsibility when working with artificial intelligence and machine learning (ML). They need to provide transparency around its use while protecting sensitive data. This is not new, but the rise of generative AI (GenAI) made it much more apparent. Fortunately, Elastic has been active in the AI field for close to a decade now. And our platform has been built with data protection in mind and has evolved to integrate AI responsibly and securely. For example, all AI training performed in Elastic has automatic governance applied; using the model map attached to each trained model, we give complete insight into what data was used, how the model is used, and who has used it.
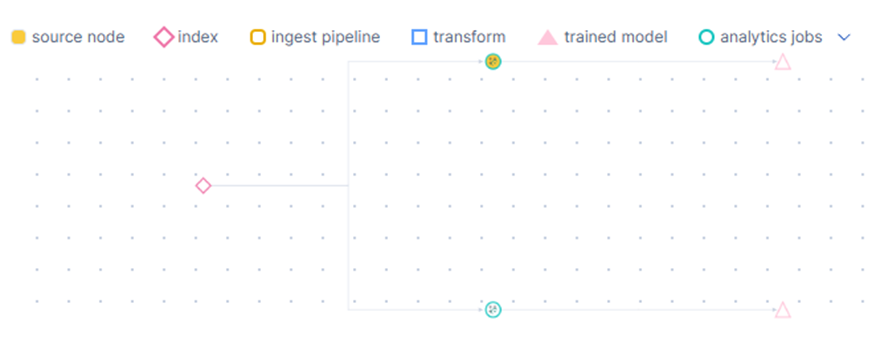
When public organizations use AI, they are expected to have full explainability about the results from the AI models. For regular ML models like regression or classification, Elastic offers the possibility to train those models with “explainability” in mind. This way, any inference from those models comes with concrete justifications from the data. This simple, basic capability of Elastic can make AI usage safer.
Neural networks that are the basis of all natural language/semantic search and the large language models (LLMs) that underlie GenAI are unfortunately nondeterministic by nature; it is not possible to “explain” this class of AI models. There is simply no practical way to tell why they take the logical steps they take. But some models are more open to showing their internal “thinking” strategies.
Elastic enables users to choose any model they want based on criteria they find important. We have a full suite of connectors that make it easy to connect to any publicly available model service. And, especially important for public organizations, we can connect to locally hosted LLMs. As more models become available for download, a major privacy hurdle keeping many public organizations from exploring the advantages of GenAI and retrieval augmented generation (RAG) architecture is finally falling away.
The combination of AI and data protection by design and the capability to run an end-to-end AI pipeline completely in your own trusted environment can simplify the process of operationalizing data and AI in public organizations.
Cybersecurity and resilience
Cybersecurity is another domain that is evolving at a breakneck pace. Research like the Elastic Global Threat Report shows that threats are multiplying, getting smarter, and persisting for longer dwell times.
Many security practitioners are looking for a modern security solution that is flexible, can cover all your assets (cloud and on-premises), and allows for long-term forensic analytics without breaking the budget. The main issue with budget is that, from a security perspective, you never want to be in a position where you need to decide whether a certain piece of equipment is “important enough” to require security. Simply put, consciously allowing blind spots in your environment completely undermines any security practice.
Elastic Security offers an industry leading holistic solution for security information and event management (SIEM), extended detection and response (XDR), and cloud security — all powered by AI. Customers using Elastic Security are already seeing outcomes, including a 36% annual reduction in risk exposure and up to 56% reduction in total cost of ownership.
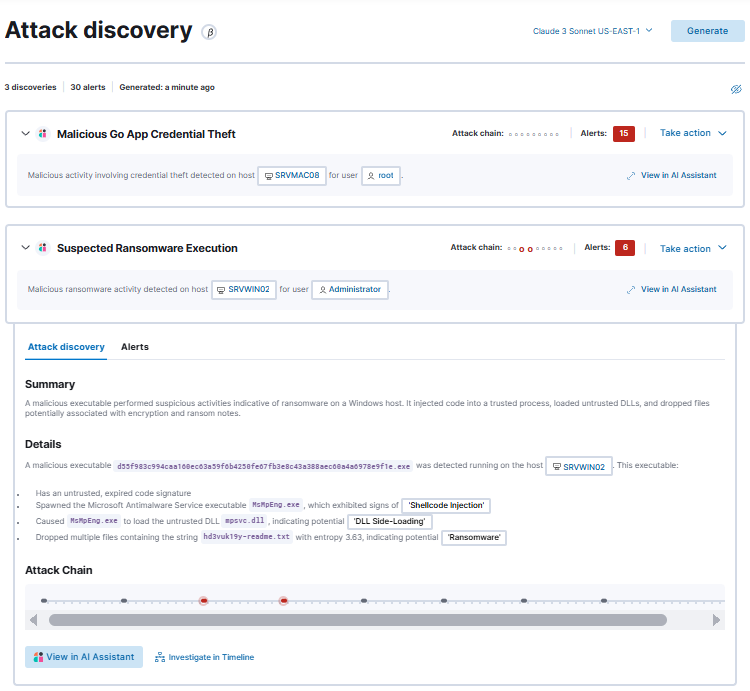
Now, of course, when you start ingesting more data to feed the security use cases, your Elastic environment can be adjusted in a cost-effective way to support the growing volume and maintain mission-critical operations. For example, instead of adding more nodes, you can choose to retain specific data sets for a smaller amount of time. For security (and especially compliance) use cases, a retention time of 10 to 15 years or more is often a requirement. But datasets that are only used for monitoring like system metrics can often be deleted much sooner, freeing up space in your existing environment.
Long-term data retention is a standard best practice for security use cases. And with Elastic’s flexible tiering approach, keeping decades of data in low-cost blob-storage is possible without going over your budget. Even in Elastic’s frozen tier, data is still fully searchable and ready for analysis without the need for a time-consuming ingesting, thawing, or importing.
Data-driven government
As noted in the previous blog, data-driven government is a goal that many public sector organizations are striving toward today. And that data needs to be available at speed; it needs to be secure; and it needs to be based on open standards and tooling. With Elastic, all these bases are covered from the start.
The flexibility that Elastic offers allows any organization, regardless of size, to deploy a unified platform for observability, security, and next-generation search that is scalable based on budget and use cases.
Register for Elastic{ON} 2025/2026 for detailed discussions on any of the topics above. Most event locations have ancillary events dedicated to public sector organizations. (Hint: Elastic{ON} Amsterdam on October 30, 2025, is always a blast — hope to meet you there!)
Continue exploring the topic
- Blog: Building the foundation of trust in government digital strategies
- Blog: Understanding data mesh in public sector: Pillars, architecture, and examples
- Blog: Understanding AI in government: Applications, use cases, and implementation
- White paper: Cybersecurity Guide for Public Sector: Protecting data and assets in the era of AI & efficiency
- Report: Analyzing the economic benefits of Elastic Security
Sources
The Netherlands' Digital Strategy, Netherlands Digital Government, June 2025
Elastic Netherlands User Group, Meetup
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.
In this blog post, we may have used or referred to third party generative AI tools, which are owned and operated by their respective owners. Elastic does not have any control over the third party tools and we have no responsibility or liability for their content, operation or use, nor for any loss or damage that may arise from your use of such tools. Please exercise caution when using AI tools with personal, sensitive or confidential information. Any data you submit may be used for AI training or other purposes. There is no guarantee that information you provide will be kept secure or confidential. You should familiarize yourself with the privacy practices and terms of use of any generative AI tools prior to use.
Elastic, Elasticsearch, and associated marks are trademarks, logos or registered trademarks of Elasticsearch N.V. in the United States and other countries. All other company and product names are trademarks, logos or registered trademarks of their respective owners.