Elastic Security 8.8: Powerful endpoint response, alert triage, and data accuracy to bring more efficiency to security

As the volume and complexity of cyber threats continue to increase, security analysts face mounting pressure to protect their organizations from attack with maximum efficiency. Elastic Security 8.8 introduces features designed to help analysts digest, prioritize, and quickly respond to security incidents. These features include the following:
- The improved alert triage experience, with customizable controls and multi-field grouping, allows security analysts to sort and organize their alerts to ensure they are able to quickly address the most critical issues.
- The new Execute command feature empowers analysts to flexibly diagnose and remediate security issues on hosts remotely and efficiently, without having to physically access the devices.
- Quickly identify and resolve data quality issues with the new Data Quality dashboard, ensuring that data is accurate, complete, and up-to-date.
- Releasing in beta in 8.8, we have Cloud Native Vulnerability Management where quick visibility to cloud vulnerabilities can be identified and corrected, as well as Container Workload Protection (CWP) to provide application and data safety for containerized environments.
Elastic Security 8.8 is available on Elastic Cloud — the only hosted Elasticsearch offering to include all of the new features in this latest release. You can also download the Elastic Stack and our cloud orchestration products, Elastic Cloud Enterprise and Elastic Cloud for Kubernetes, for a self-managed experience.
What else is new in Elastic 8.8? Check out the 8.8 announcement post to learn more.
Streamline alert triage
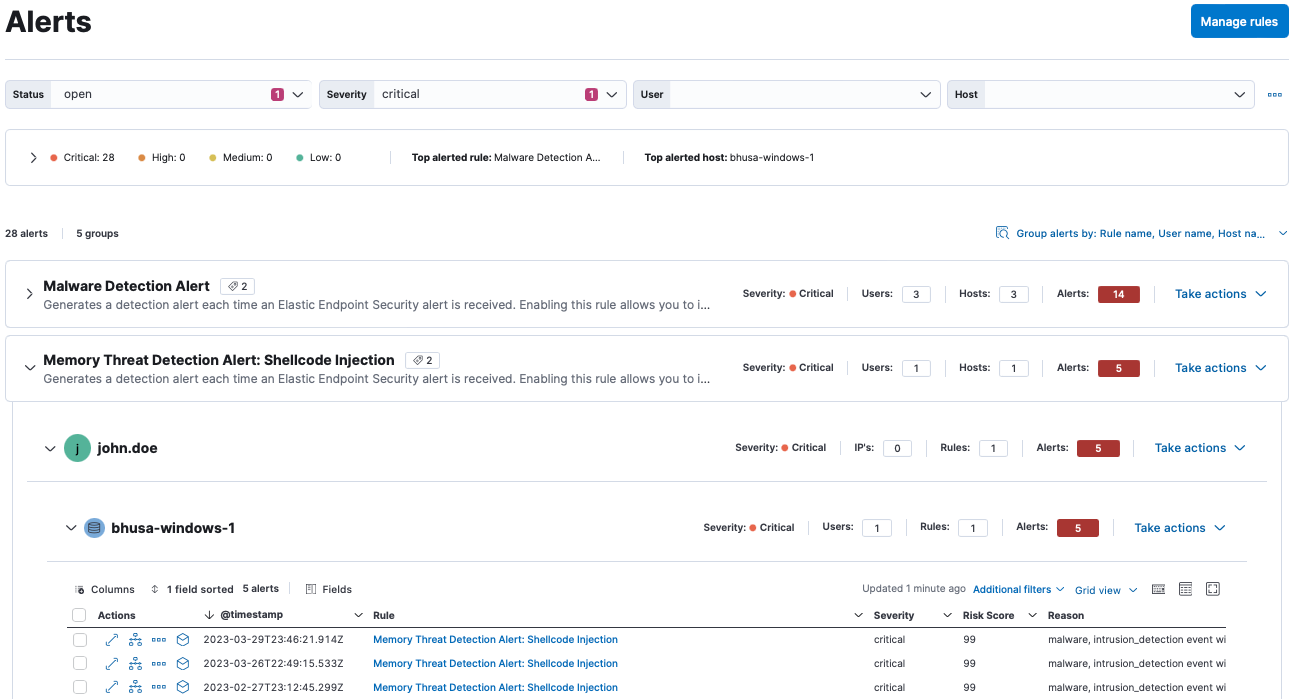
After introducing alert grouping in 8.7, Elastic Security continues to improve the alert triage experience by adding customizable controls to enable enhanced filtering as well as multi-field grouping to further organize alerts.
Security analysts face alert fatigue due to the high volume of alerts faced each day. Grouping and prioritizing information is critical to lessen the burden of frequent alerts. By adding multi-field grouping to the 8.7 alert grouping feature, users can further group information into manageable buckets of information. Additionally, the alert page controls allow for quick filtering for priority information. Whether using the default controls, customizing your own, or following prebuilt controls from dashboards, users can quickly narrow their vision to the most important alerts.
Reduce MTTR with powerful endpoint response capabilities, including Execute
Elastic Security 8.8 continues to expand our response action capabilities with the addition of the Execute response action. The Execute response action enables security analysts and administrators to remotely execute terminal commands on hosts through our centralized response console, without requiring analysts to have physical access to the host. This provides the flexibility to customize remediation and response based on the specific threat or incident, through the execution of custom commands or scripts.
As an example, it's common for malware to use persistence techniques to remain on the compromised host for as long as possible. One common technique on windows systems is to create a scheduled task to execute any payloads or commands repetitively. In this scenario, we will use our Execute response action to remove the scheduled task that the malware created on this host, after the behavior was identified via an Endpoint behavior rule and picked up by an analyst during triage.
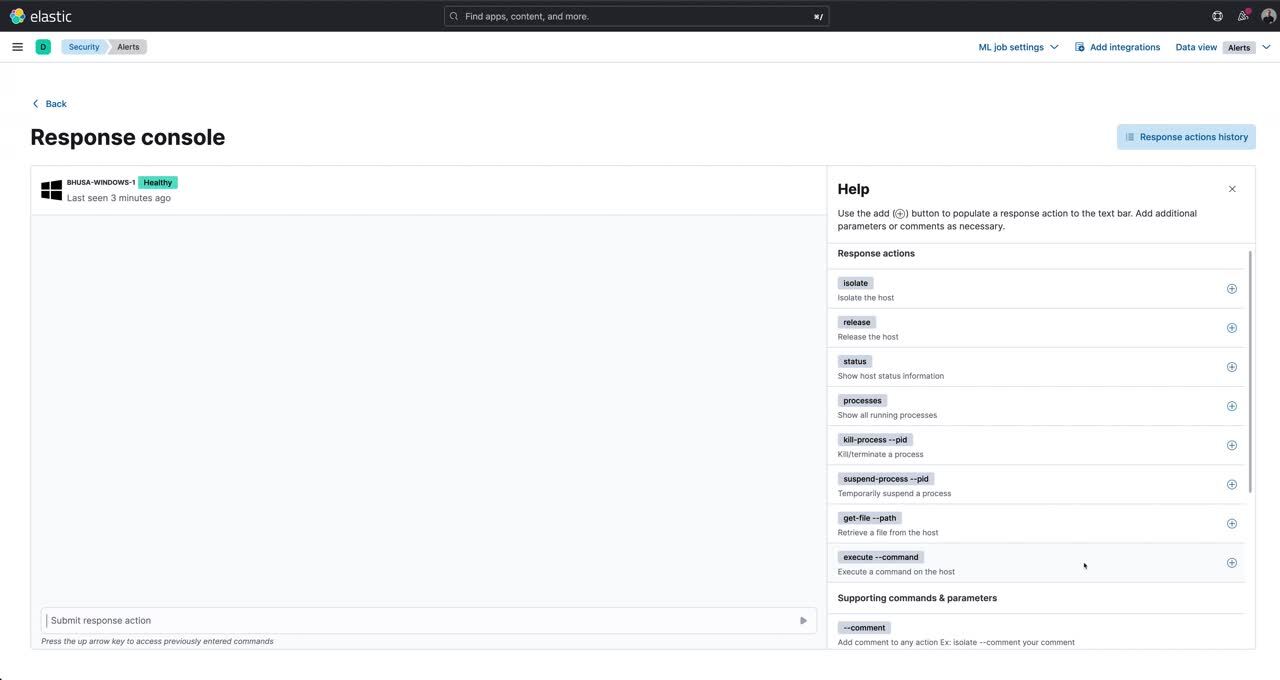
This is just one example of how the Execute action delivers crucial response capabilities for advanced security operations. This capability is generally available in 8.8 for every OS protected by Elastic Agent and is accessible via the Elastic Security Enterprise subscription tier for both self-managed and cloud deployments.
Improve data accuracy with Data Quality dashboard
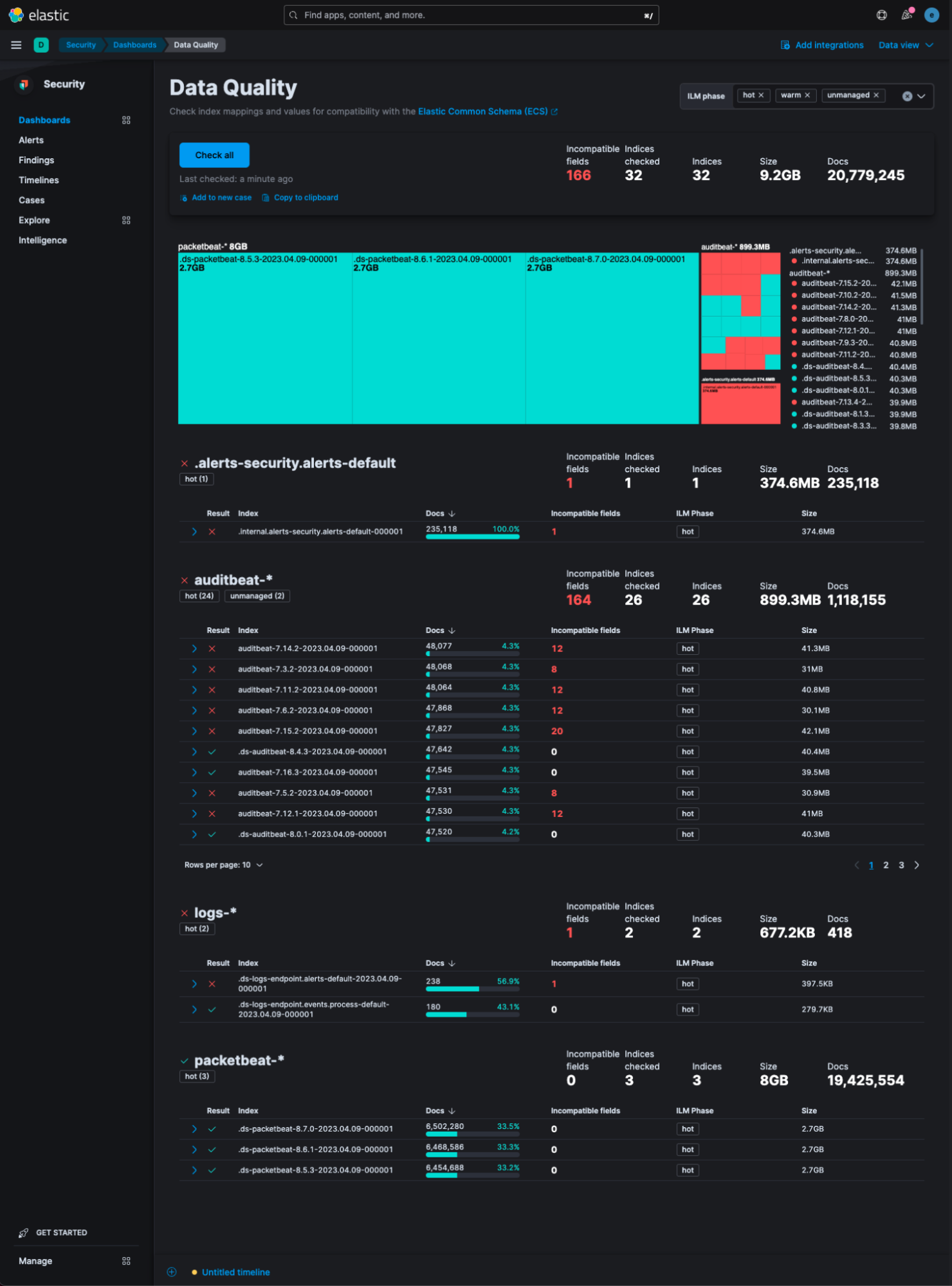
With the 8.8 release, Elastic Security brings a workspace for assessing and monitoring data quality. The Data Quality dashboard simplifies the process of determining whether data is accurately mapped to Elastic Common Schema (ECS) and also provides visibility into storage usage for indices. The Data Quality dashboard enables checking all indices for mapping conflicts with a single click and facilitates sharing the results with other members of the organization using Cases.
Through the dashboard, a summary of incompatible field mappings within any index and details when the field lacks the expected mapping can be easily viewed. The dashboard empowers users to promptly identify and address data quality issues, ensuring the accuracy, completeness, and timeliness of data. By ensuring data integrity, we can more effectively detect and prevent cyber threats while fostering greater trust in our ability to safeguard data and assets.
Protect Cloud Workloads with Container Workload Protection (CWP)
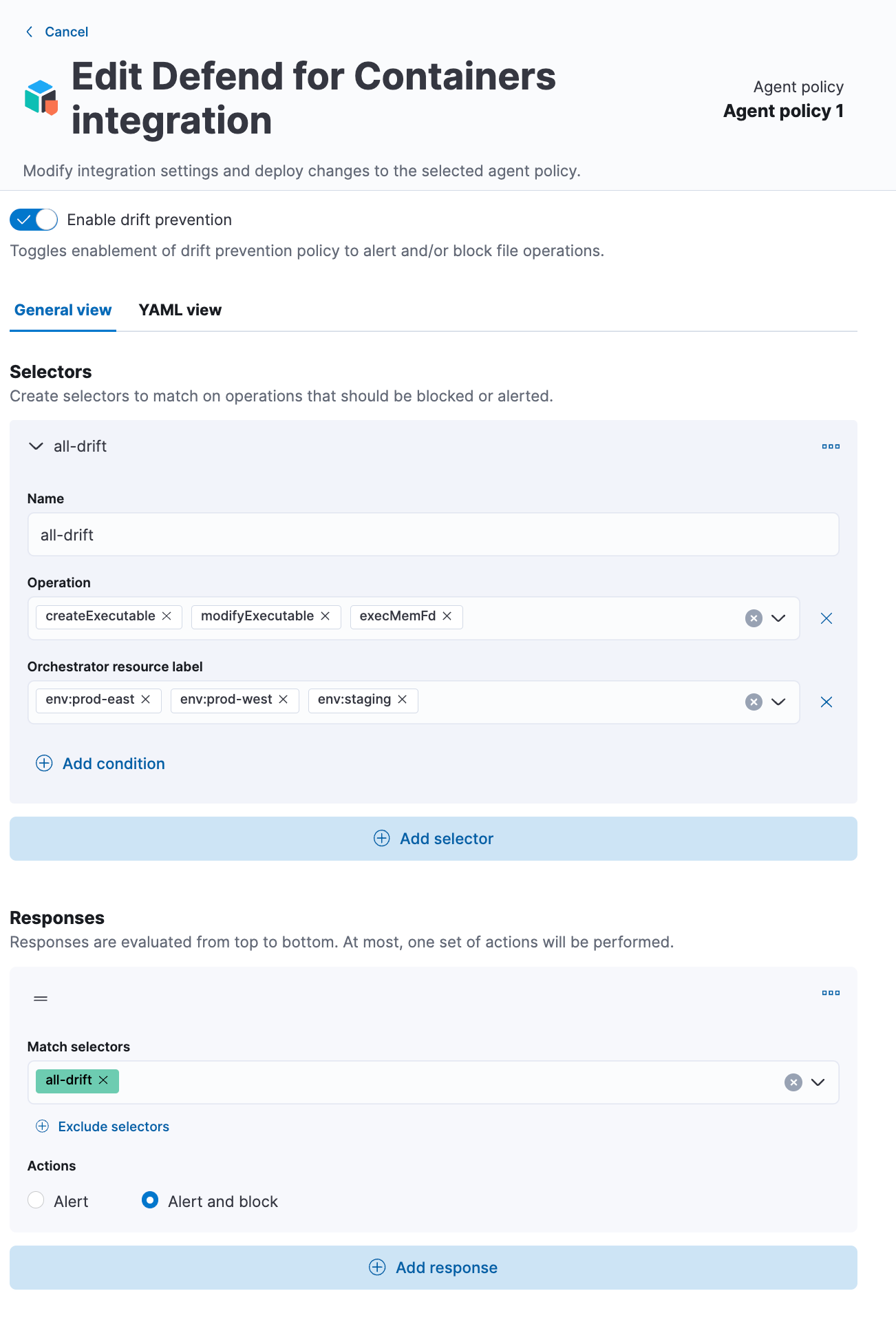
The advent of containers and Kubernetes has transformed the way software applications are developed, deployed, and managed. Elastic Security has stepped up to the challenge of providing comprehensive protection for container runtime environments with the Container Workload Protection (CWP) solution, which will be released in beta as part of 8.8.
CWP offers a three-layer approach to ensure application and data safety, which includes detecting unique threats targeting containerized environments, preventing drift by tracking changes to container file systems, and using a powerful policy language to lock down containers and prevent unauthorized access. With CWP, teams can safely deploy their containers to production environments without worrying about security threats. Read more about this new feature.
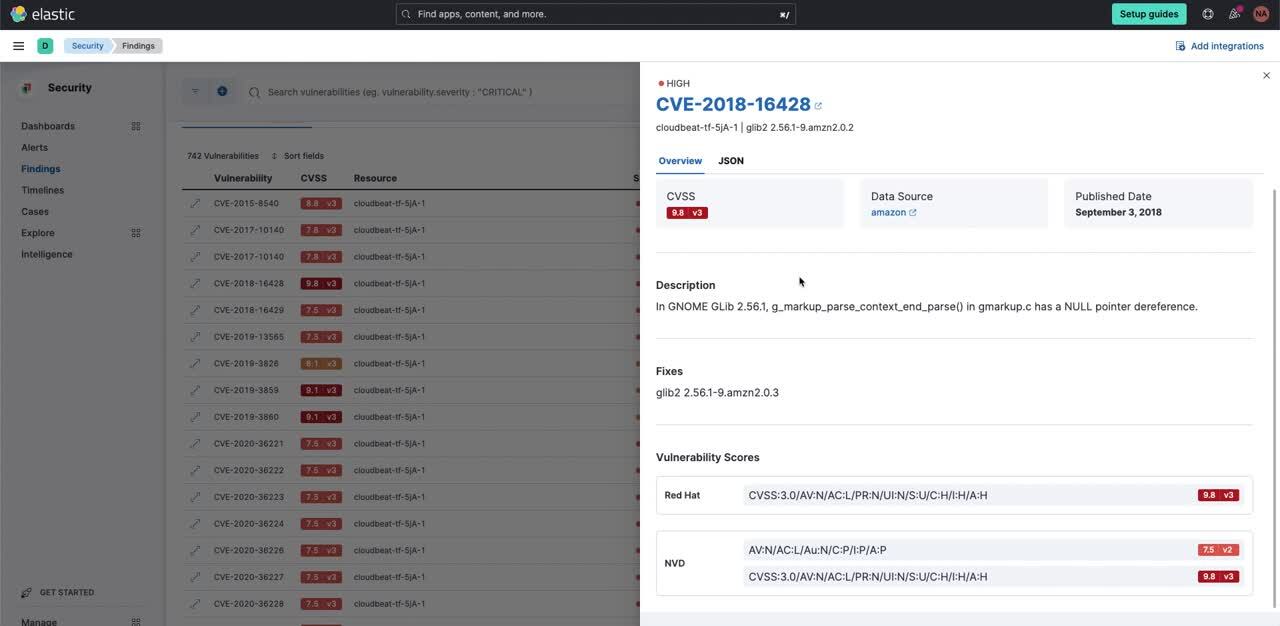
Introducing Cloud Native Vulnerability Management
Elastic Security for Cloud continues to expand its capabilities by introducing a new integration — Cloud Native Vulnerability Management (CNVM) — as a beta release. As cloud security becomes increasingly vital, our latest capability empowers organizations to efficiently detect and mitigate potential security risks within their cloud workloads.
The CNVM feature harnesses the power of AWS snapshot APIs and AWS CloudFormation. During each scan, a single integration instance takes a snapshot of all AWS EC2 workloads in its region using the AWS snapshot APIs and analyzes them for vulnerabilities. This groundbreaking functionality preserves valuable workload resources, reducing costs and ensuring uninterrupted workload performance during scans.
What sets CNVM apart is its effortless installation process. Users can now kickstart the solution with a single click, leveraging the convenience of an AWS CloudFormation template. This streamlined deployment not only saves time but also accelerates time-to-value, empowering organizations to swiftly identify and address vulnerabilities. With CNVM, enhancing overall cloud security posture has never been easier.
Try it out
Read about these capabilities and more in the release notes.
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. Not taking advantage of Elastic on cloud? Start a free trial.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.