Endpoint security from Elastic
Elastic's AI-driven security analytics empowers you with comprehensive endpoint protection. Detect, investigate, and respond to threats faster with a single agent and unified console. Gain actionable insights for a proactive defense posture — all built on the Search AI Platform.

Proven anti-malware




Endpoint security for everyone
Avert endpoint threats with signatureless prevention, behavior analytics, centralized detection, and fast and informed response.
Prevent in depth
Secure your Windows, macOS, and Linux systems with endpoint security from Elastic. Prevent ransomware, halt malware, and thwart advanced threats using behavior-based prevention. Benefit from additional protections provided by Elastic Security Labs and our global user community.
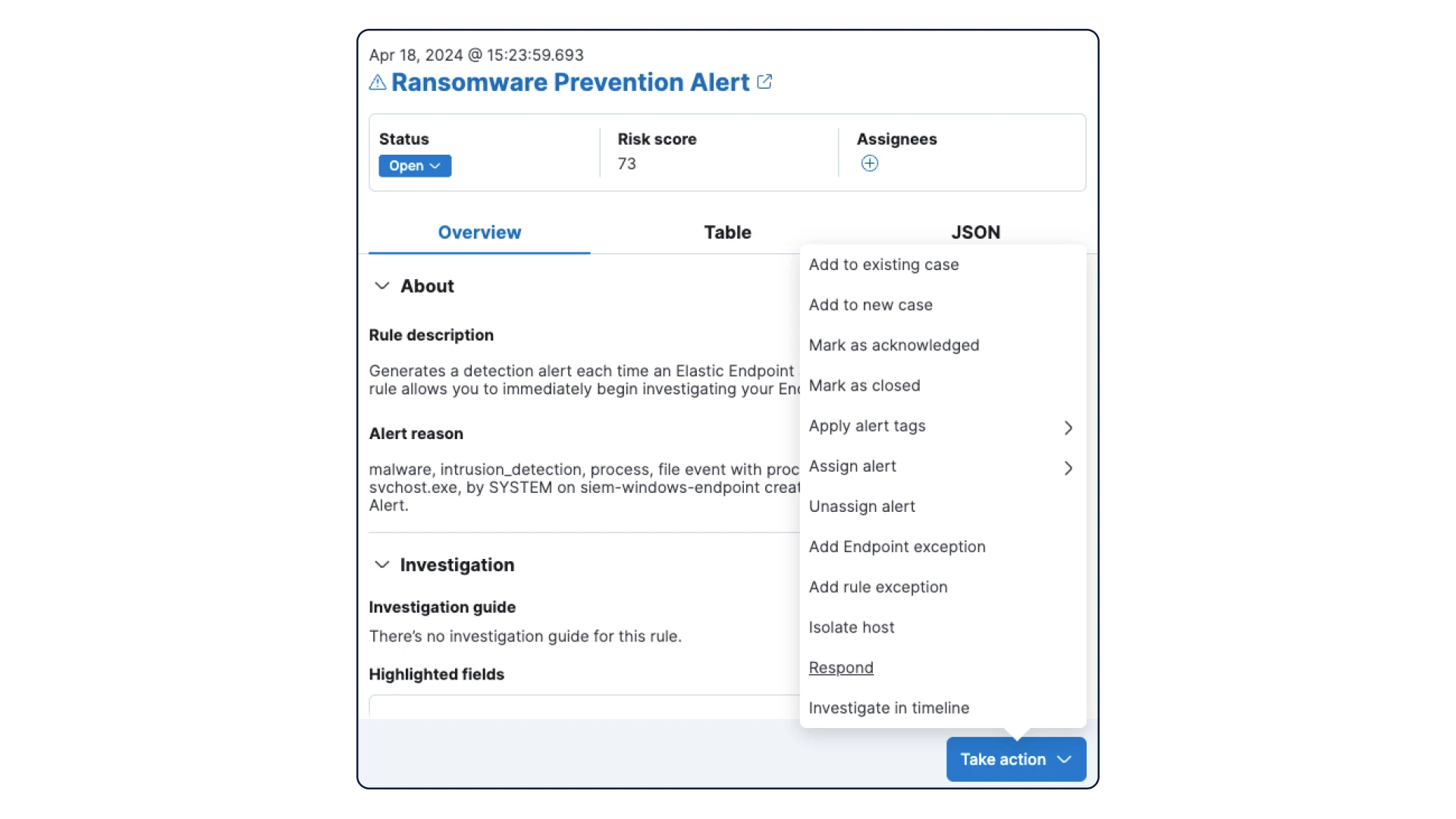
Elevate visibility and defense with XDR
Go beyond the endpoint. Collect telemetry across your security tools to gain contextualized insights and deeper visibility. Monitor activity with integrated dashboards. Choose your security approach: native security at no additional cost or with extended protection by ingesting data from your existing tools.

Uncover hidden threats
Generate actionable alerts by continuously correlating host activity with broader environmental data. Initiate hunts from anomalies spotted by prebuilt machine learning jobs.
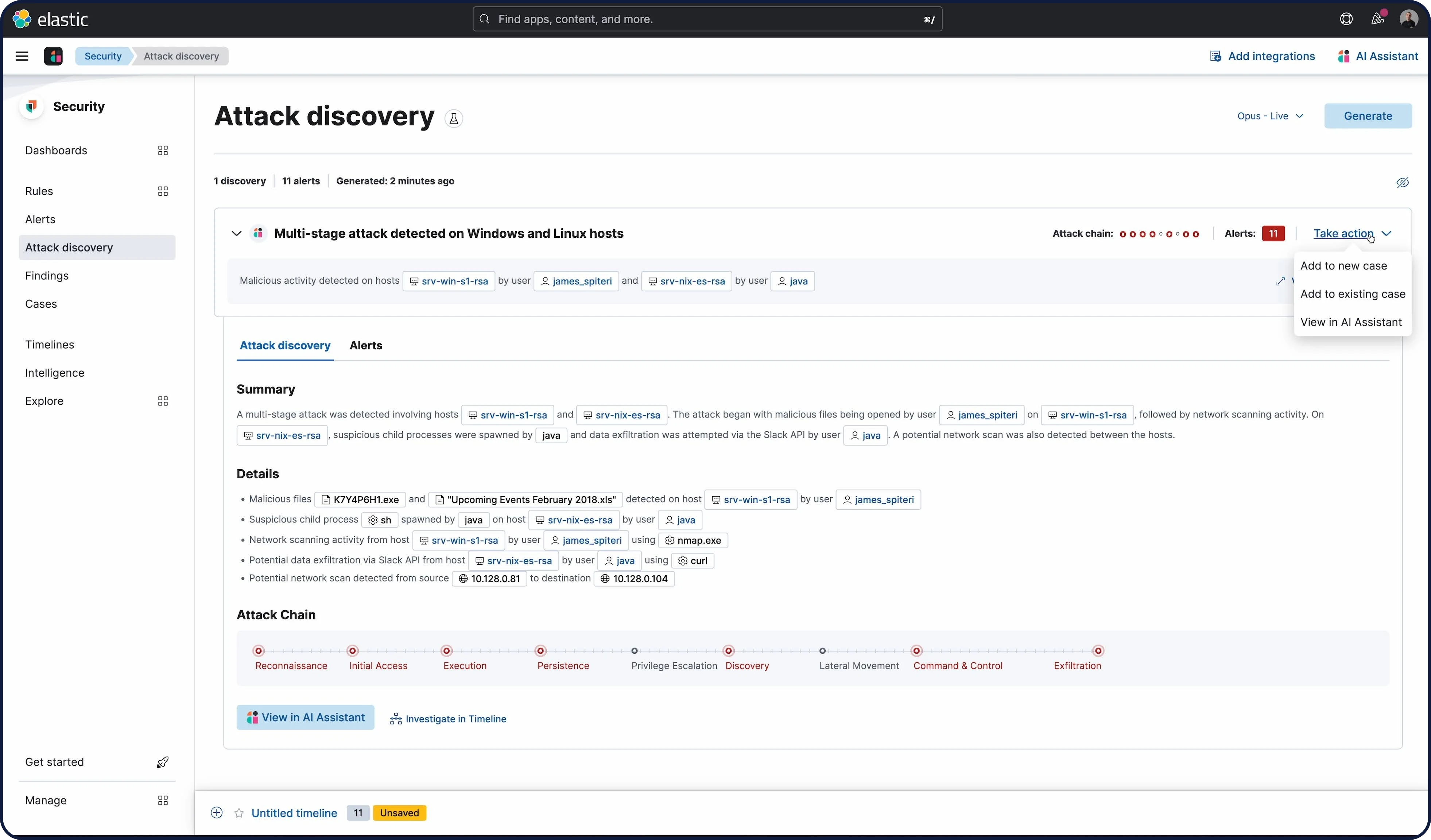
Unmask threats, automate response
Empower analysts with rich context, visualizations, and AI-driven security analytics for rapid investigations. Orchestrate automated responses to kill, suspend, or isolate threats triggered by detections, using native response actions. Seamlessly connect to SOAR platforms for playbooks and broader response actions, Uncover the truth, and neutralize threats faster.

Frequently asked questions
Endpoint security from Elastic is a robust endpoint security solution that prevents ransomware and malware, detects advanced threats, and arms responders with vital investigative context. All on an open platform, for infrastructure and hosts everywhere.
Endpoint security from Elastic delivers advanced threat protection for endpoint devices through machine learning and behavioral analytics, ensuring real-time detection of sophisticated threats. With the incorporation of extended detection and response (XDR), it correlates data across multiple sources for a comprehensive view of security incidents, enhancing detection accuracy and response speed. The endpoint security solution excels in security analytics, providing powerful tools for data visualization and analysis. This enables security teams to derive actionable insights from large data sets, empowering them to make informed decisions and fortify their defense against evolving threats.
Endpoint security from Elastic equips analysts with advanced endpoint threat detection using machine learning and behavioral analytics. The integration of XDR provides a holistic view of threats by correlating data from diverse sources. Analysts benefit from up-to-date threat intelligence, an open architecture for seamless tool integration, and collaborative tools like Elastic AI Assistant for efficient triaging and incident management. This comprehensive approach enables analysts to swiftly and effectively manage threats in real time.
Endpoint security from Elastic offers flexible pricing plans to fit your needs and budget.
- Start for free by exploring core features and get familiar with the platform.
- Scale up with subscriptions to unlock advanced capabilities like XDR, automated response, and in-depth analytics.
- Receive a custom quote for large deployments that tailor solutions for extensive needs and complex environments.
Visit our pricing page for details and find the perfect endpoint security solution to fit your security needs.
Endpoint security from Elastic is a cloud-native endpoint security solution that helps security teams prevent, detect, and respond to threats across their endpoint devices. It leverages the power of Elastic Agent and Elastic Common Schema (ECS) to collect and analyze data from various sources such as operating system events, network activity, and user behavior. Endpoint security from Elastic also integrates with Elastic Security features, such as threat intelligence, machine learning, and case management, to provide a comprehensive and modern approach to security operations.
Start your free trial today! Our comprehensive getting started guide will walk you through every step.



