Elastic modernizes security teams with SOAR and automates actionable threat intelligence within SIEM

Elastic continues to provide customers the ability to modernize their security operations programs. Today’s launch celebrates several initiatives that together equip customers to modernize security operations, including:
- Recently announced SOAR features that reduce MTTR by accelerating analyst workflows
- Key enhancements to our threat intelligence function that decrease an analysts’ time to review threat intelligence and take action on it
- The continuing evolution of built-in cloud security and endpoint security capabilities
Soar into XDR
Extended detection and response (XDR) continues to be a key approach to modernizing security operations. We are adding endpoint and cloud response actions, including automated response, rollback, and workflow capabilities. These new actions further reduce the time to remediate and the analyst’s time with each case.
Make threat intelligence actionable
Threat intelligence (TI) is a key component of a modern security team that helps organizations gain deeper understanding of current and emerging threats and rebuff unfolding attacks. We understand that the typical organization subscribes to five threat intelligence platforms. This rich context helps organizations automate the detection of known threats and respond more quickly to adversaries that make it past the first layers of defense.
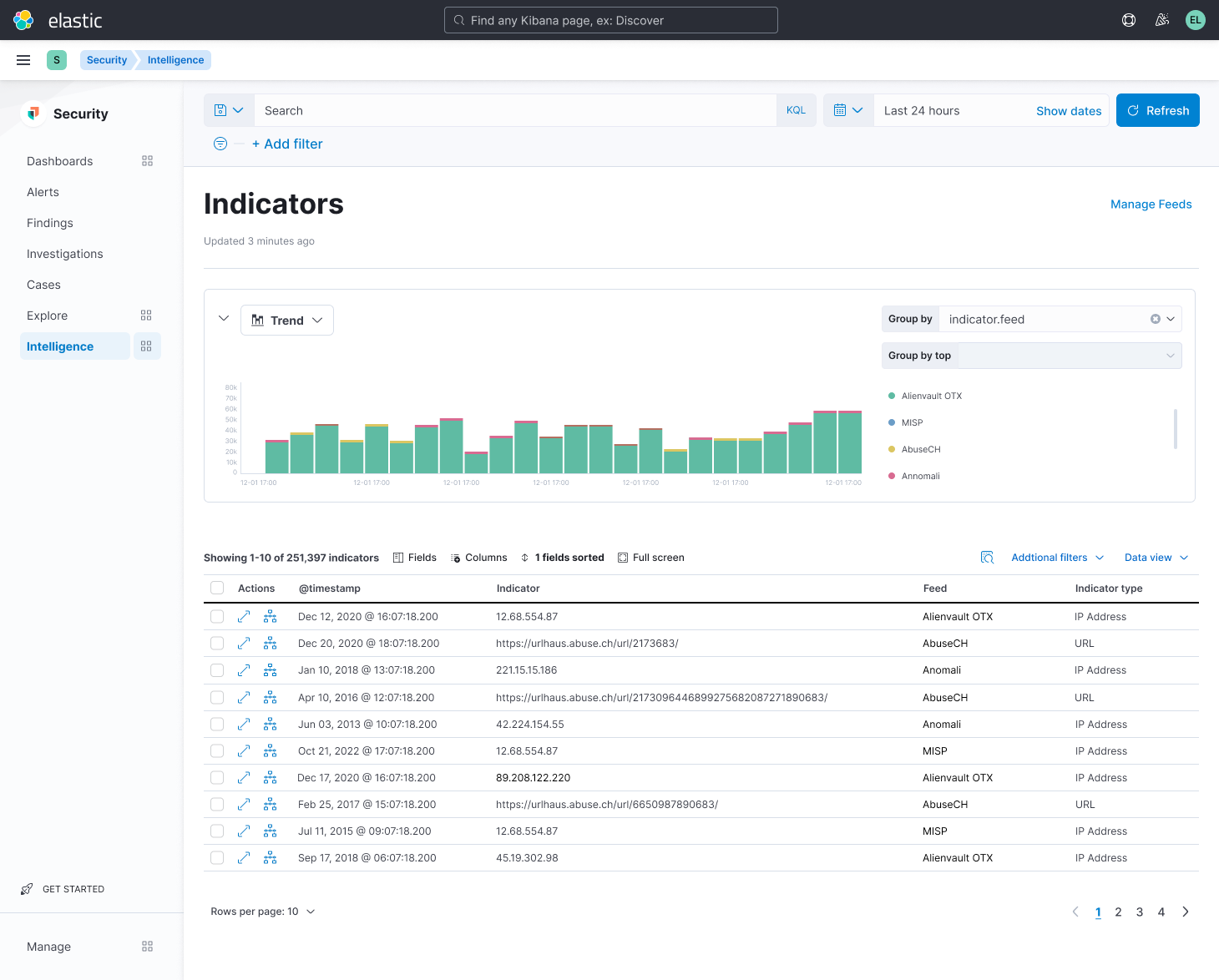
Elastic Security eases the ingestion and preparation of threat intelligence from numerous sources, including AbuseCH, AlienVault OTX, Anomali, Cybersixgill, MISP, Recorded Future, and ThreatQuotient. Today, Elastic announced our ability to make threat intelligence more actionable by gathering Indicators of Compromise (IoCs) into one unified view. Now, teams can search, sort, filter, and take actions on TI, allowing practitioners to add to and directly investigate within Elastic Security’s investigation interface. In addition to helping cyber threat intelligence analysts better understand emerging threats, Elastic allows practitioners to quickly see and act on reported threats, substantially reducing adversary dwell times.
“Security teams are constantly looking for ways to reduce mean time to detect and remediate,” said Santosh Krishnan, General Manager of Elastic Security. “Now, customers can maximize the value of their investments in threat intelligence and take action directly from the Elastic Security solution.”
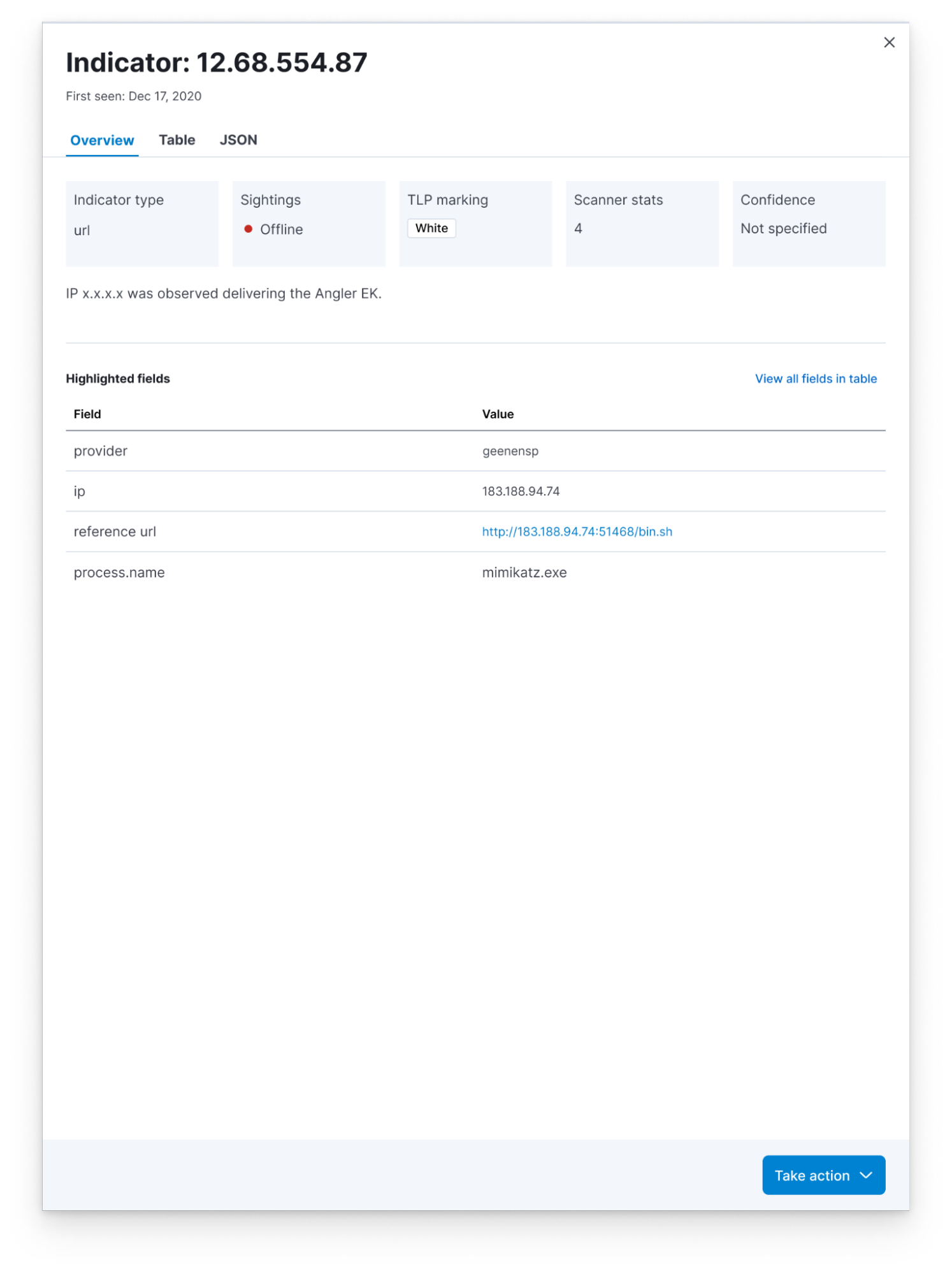
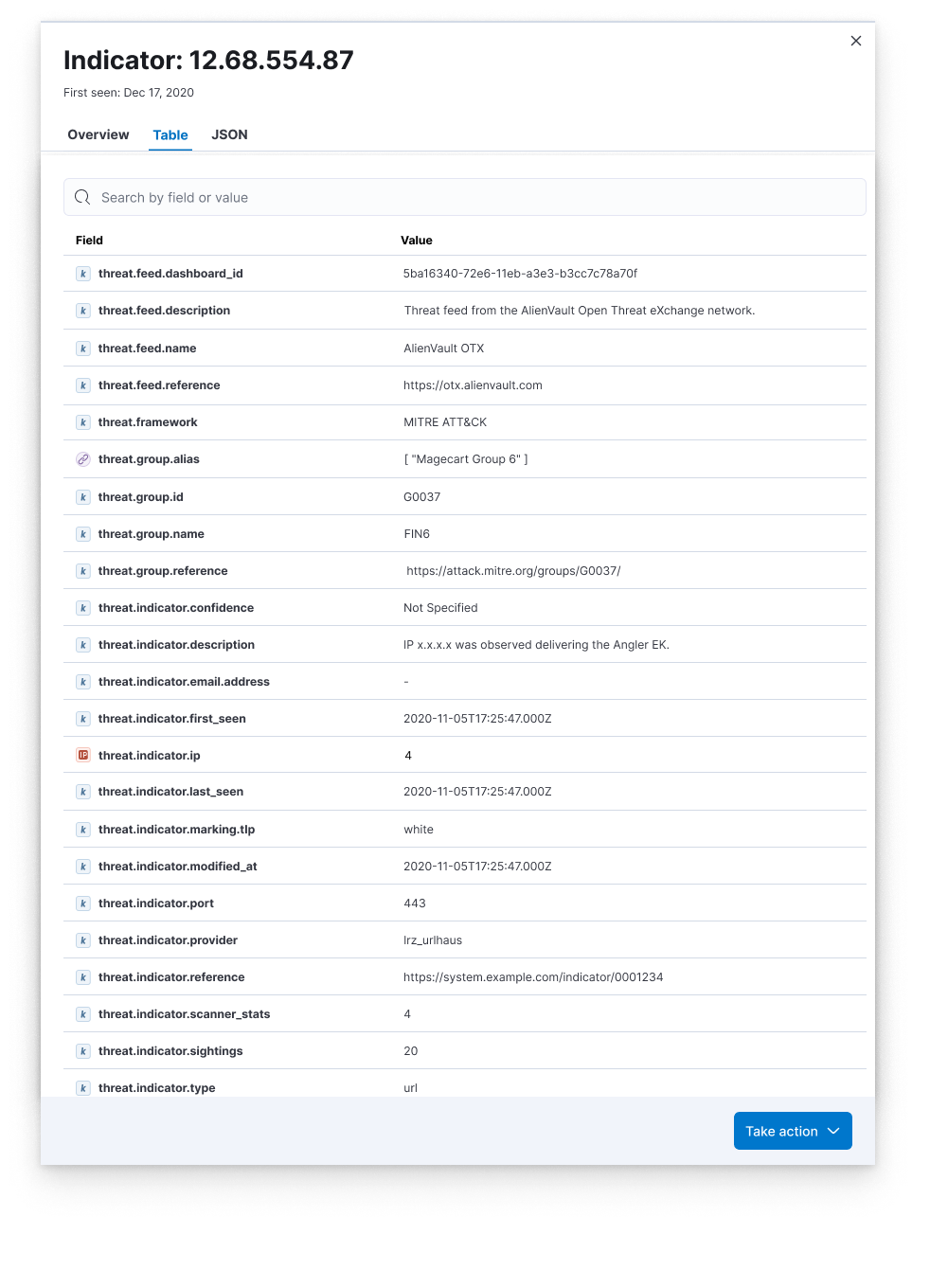
Many organizations lack the technology to view all relevant threat intelligence side-by-side in their SIEM and some lack the staff to automate the use of threat intelligence to improve protection. Elastic consolidates the artifacts of all active threat intelligence feeds into one view. Rather than jumping between separate applications, analysts simply select an Indicator of Compromise (IoC) to view associated metadata, see when it was last observed in your environment, and take necessary action, like investigating matches with Elastic’s Timeline feature and escalating to a case. This reduces cognitive load and hastens response.
Here are several example views of IoCs:
“We’ve worked with Elastic for years to ensure our joint customers have a seamless experience with our products. It’s great to see Elastic making our intelligence actionable.”
Jamie Zajac, Vice President of Product at Recorded Future
Protect with Elastic Security for Cloud
We’re building on our previously released Elastic Security for Cloud features as well. Customers can leverage Elastic to ensure visibility to cloud workloads and protection against threats targeting cloud workloads.
Adopt a Modern Security Operations Practice Now
Elastic continues to deliver on our promise to modernize security operations. We believe it can be more efficient and effective for our users. We’ve also made Elastic Security Labs research available within Elastic to increase security knowledge. We’ll continue to innovate and rapidly deliver product enhancements in security.
Check out the SOAR Overview Guide.
Learn more about Elastic Security.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.