What’s new in Elastic Security 8.2: Streamline analyst workflows with context and expertise

Elastic Security 8.2 powers the efficiency and effectiveness of security teams, arming analysts with invaluable insights and deep visibility into the attacks targeting their organization. The release delivers rich alert contextualization, osquery host inspection directly from an alert, new investigation guides, and the general availability of threat intelligence.
Let’s jump in.
Streamline analyst workflows with context and expertise
Curated UI for analyzing user activity
Elastic Security 8.2 provides new visibility into user activity, helping practitioners address insider threats, account takeover, privilege abuse, and related vectors. The experience is consistent with existing analyst workflows for exploring host and network data.
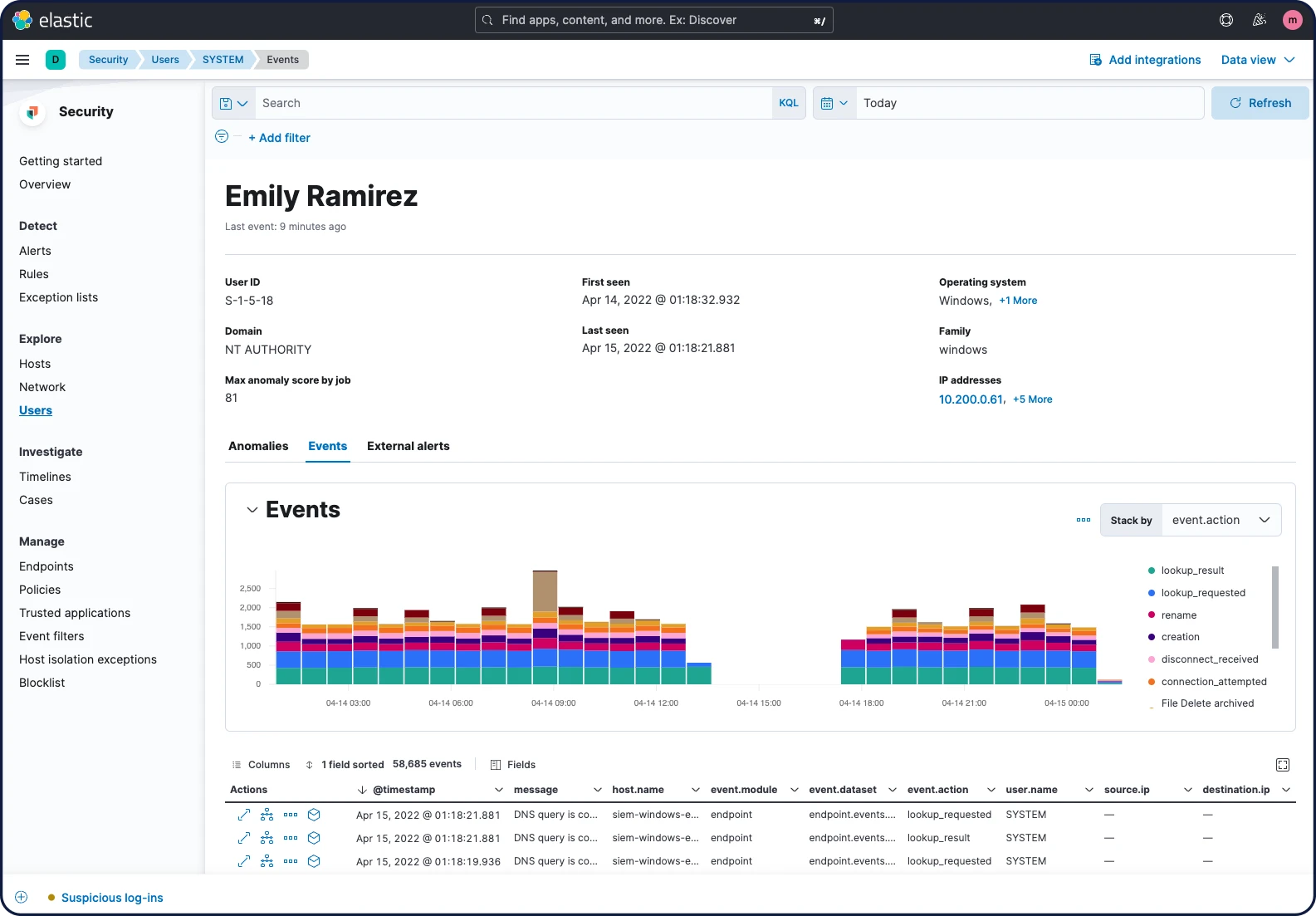
Users View supports security monitoring by presenting environment-wide user context in curated visualizations and tables. It surfaces context such as total unique users and successful/failed authentications, and provides quick access to user events, anomalies, and alerts.
The User Details page provides a comprehensive view of an individual user, including key attributes, observed activity, and related anomalies and alerts. A related flyout arms analysts in the flow of a hunt or investigation with relevant user context, including account details and anomalous activity.
Examine process executions with Session View
Elastic Security 8.2 streamlines triage and investigation workflows with Session View, a new interface for examining process executions on Linux systems that provides a forensic view of system workloads. It helps analysts understand user and service behavior, reconstructing sessions as if peering at the terminal of an adversary attempting to sudo and curl their way to paydirt or a script configured to open a socket connection to a C2C server. An analyst can see, for example, if a reverse shell has been initiated from bash or if a compromised web server is exfiltrating sensitive resources over a freshly opened network socket. Selecting an event surfaces further details, including context on related processes, hosts, and alerts.
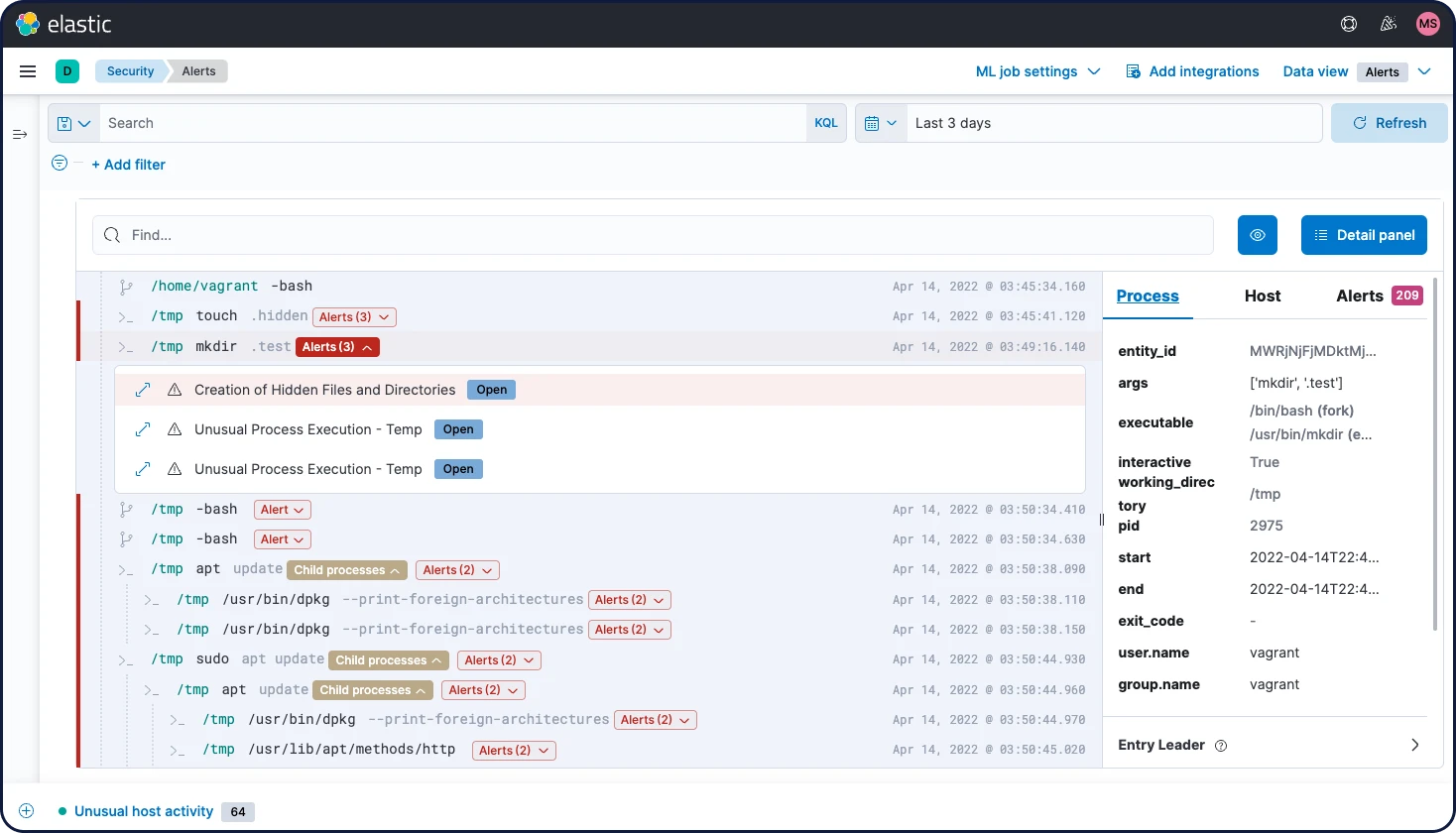
The release also introduces Linux host event collection via eBPF — the magic behind Session View — providing richer visibility into the kernel activity of Linux infrastructure and endpoints than previously possible. For older kernel versions, the solution is backwards compatible.
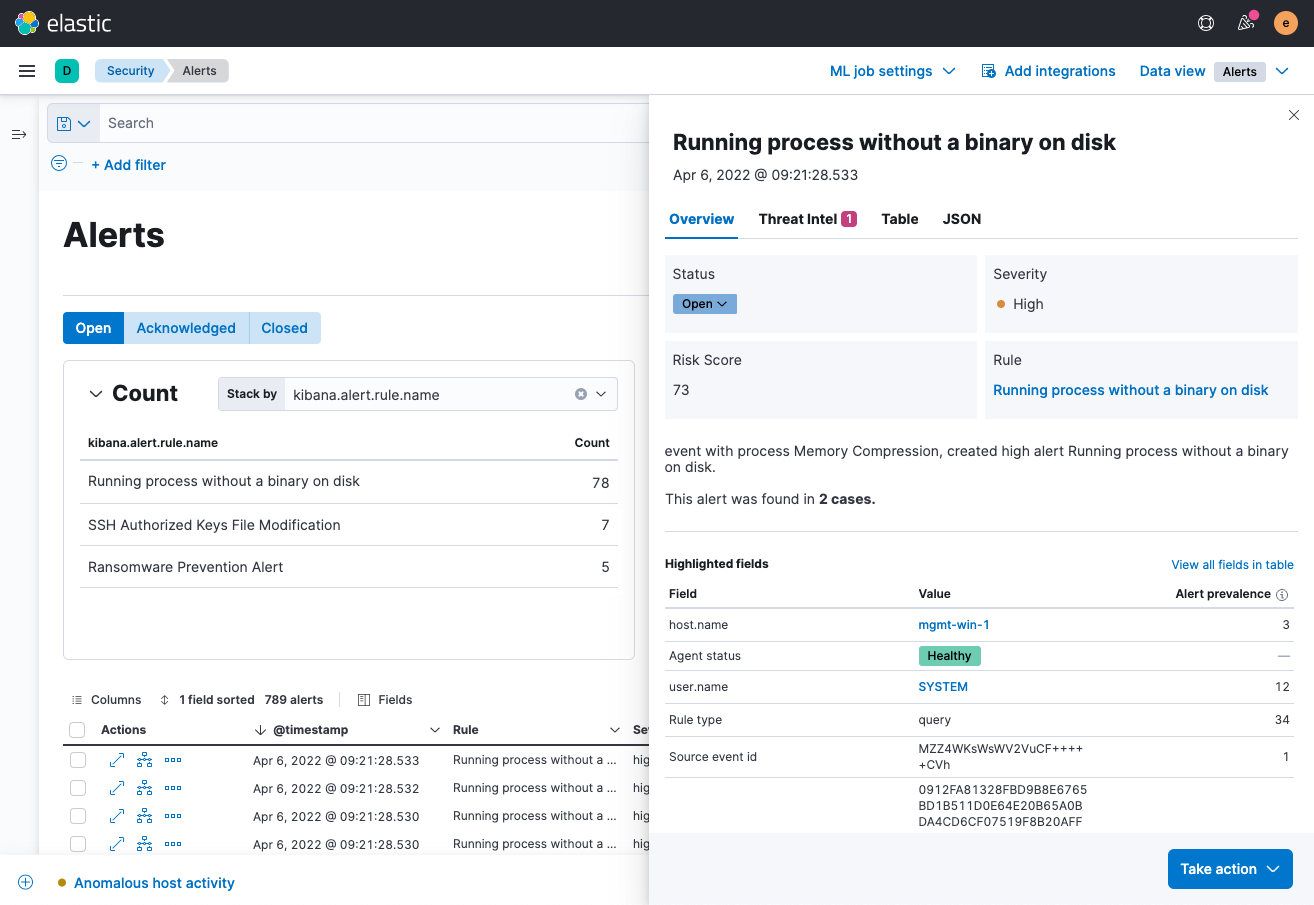
Accelerate alert triage with richer context
Elastic Security 8.2 enables analysts triaging an alert to quickly ascertain how many alerts within a given timeframe share a specific attribute, such as an impacted user or host. Knowing how many alerts are associated with the same host, user, IP address — you name it — helps them accurately identify alerts meriting investigation and spot opportunities to reduce false positives by honing a detection rule.
Accelerating triage with insights on alert attributes benefits downstream SecOps processes, too — enabling responders to focus on high-priority alerts and reducing adversary dwell times.
From this same flyout, analysts can now quickly access links to all cases to which an alert has been linked, accelerating triage and investigation.
Investigation guides with expert advice
Elastic Security 8.2 helps security teams triage, investigate, and respond to alerts with a new set of investigation guides for a large set of prebuilt detection rules. Elastic threat researchers help practitioners decide how to address an alert by developing this rule-specific expertise and surfacing it alongside associated alerts. The guides cover why an alert fired, how to determine whether it represents a true threat rather or merely a false positive, which steps to consider taking for investigation and remediation, and more.
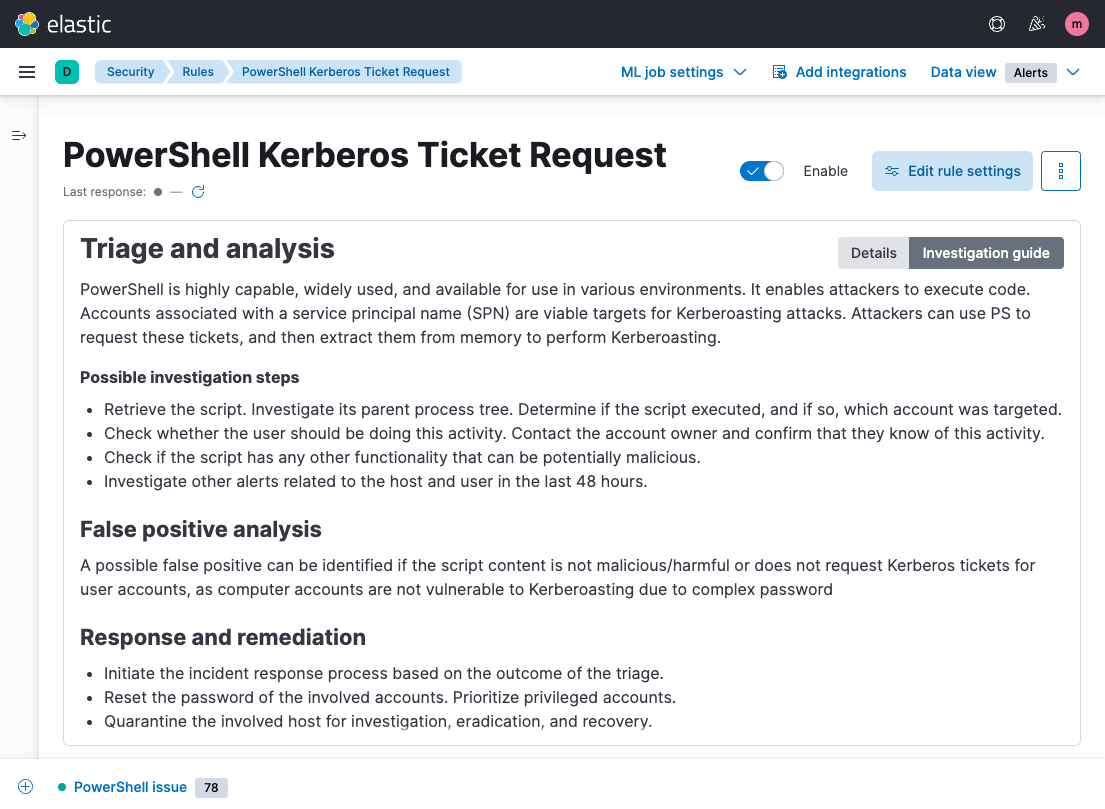
The investigation guides added in this release primarily buttress rules for detecting threats against Windows systems. With expert advice for defending these ubiquitous systems, they uplevel the contributions of junior analysts and reduce the cognitive load of seasoned practitioners.
General availability of threat intelligence
Elastic Security continues to make it easy to operationalize threat intelligence — a critical tool for improving detection coverage — to tighten investigation and response intervals and enable threat hunting.
The solution offers turnkey integrations with seven threat intelligence sources, including open source offerings like MISP and AbuseCH and commercial platforms like Anomali and Recorded Future. With the solution, organizations can leverage threat intelligence for event enrichment, automated detection, alert contextualization, and more. With today’s release, these capabilities enter general availability and enjoy full commercial production support.
Stop threats at the endpoint
Prevention with custom blocklists
Administrators can now configure Elastic Agent to protect high-risk systems by blocking the execution of specific applications or code that should never run. This capability is especially useful for protecting systems with highly predictable activity, such as cloud microservices and physical point-of-sale terminals, and can also help ensure that known malicious files are not accidentally executed by an end user. Organizations with access to highly targeted intelligence about the threats facing organizations like theirs can consider defining blocklists to include particularly concerning malware IoCs.
Expanded set of endpoint behavior protections
Elastic Security 8.2 further extends the power of malicious behavior protection on Elastic Agent, which pairs post-execution behavior analytics with targeted response actions to stop sophisticated adversaries. These new preventions enhance protection of Windows, macOS, and Linux systems, addressing a broad set of MITRE ATT&CK® Tactics — particularly initial access, privilege escalation, and defense evasion. These new protections add to the targeted capabilities for stopping advanced attack techniques featured in our 8.1 announcement.
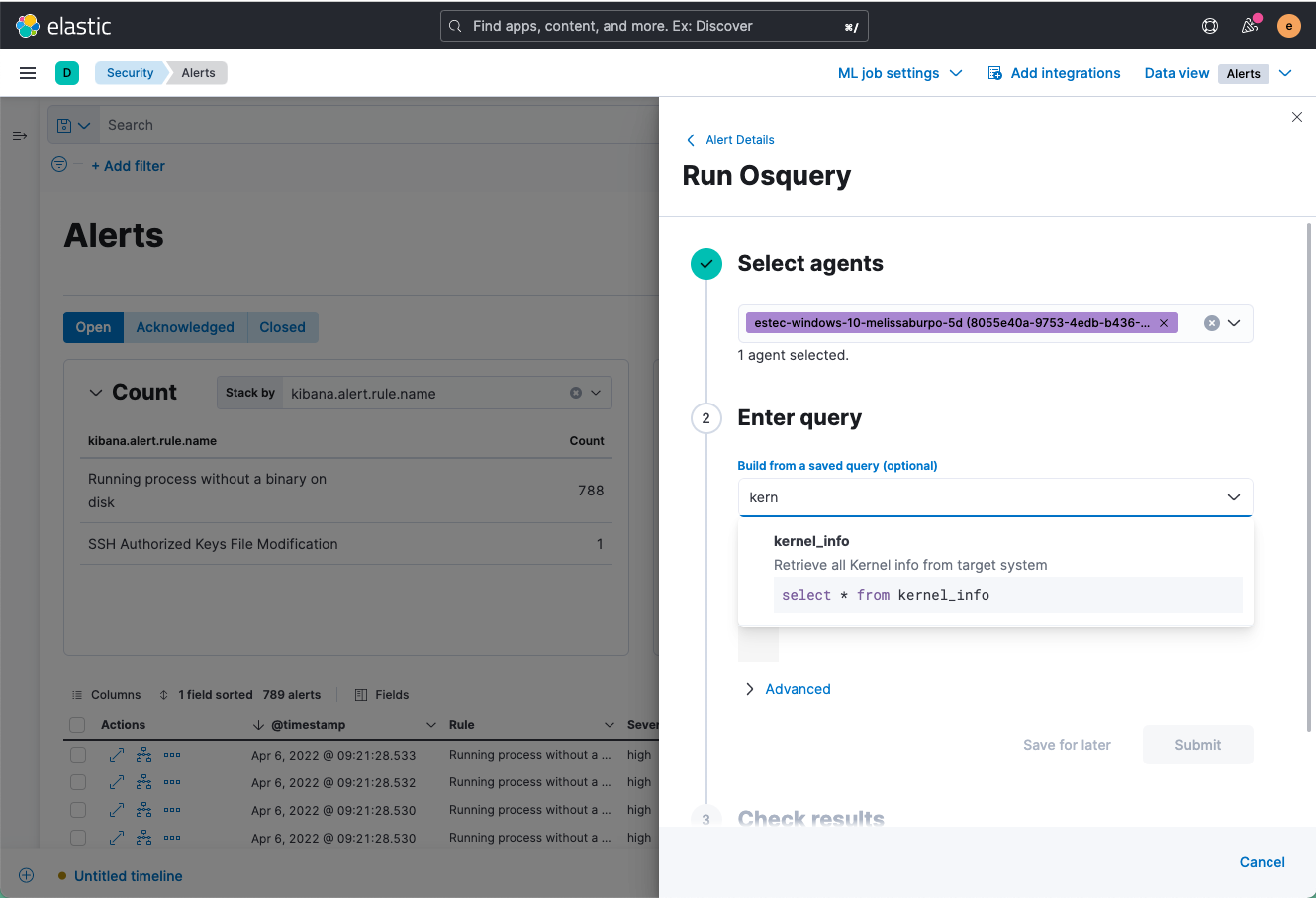
Osquery inspection directly from an Alert
Elastic Security 8.2 arms analysts to inspect hosts directly from an alert, putting host context within immediate reach. Practitioners can craft an ad-hoc query, gather host activity and state data, and prepare next steps — without diverting from their typical workflows. This capability helps analysts investigate and respond to suspicious activity in a fast and informed manner. Remote host inspection leverages the Osquery Manager integration for Elastic Agent, available free and open on Windows, macOS, and Linux systems.
Stop threats at scale with turnkey integrations and protections
Prebuilt data integrations
Elastic Security 8.2 streamlines collection and preparation with enhanced data integrations, plus dashboards for the Network Packet Capture integration.
The release enhances our support for third-party endpoint security technologies. A new integration for Microsoft 365 Defender enables organizations to collect security events with Elastic Agent, providing an alternative to Filebeat. The release also enables organizations to collect alerts, endpoint events, and watchlist hits from VMware Carbon Black Cloud, building on our support for VMware Carbon Black EDR.
With logs for Cisco Secure Email, an email security gateway product designed to detect and block a wide variety of email-borne threats, organizations can enhance protection against malware, spam, and phishing attempts. The release also adds support for Cisco Identity Services Engine (ISE), an identity and access control policy platform for endpoints, and updates our integration for the ingestion of logs from Cisco Meraki MX, enhancing visibility across the network layer.
Out-of-the-box detection rules
Organizations can now spot a broader set of attack techniques targeting user accounts with new prebuilt detection rules. Several of the new rules help stop adversaries from misusing user accounts and privileges by spotting insecure Windows AD configuration practices and related suspicious activity. Recent newsworthy events indicate that these kinds of rules are essential for detecting disruptive activity before it becomes a headline.
The new detecction rules help ensure that even adversaries leveraging sophisticated evasion methods can’t create or commandeer a user account and escalate privileges without going unnoticed. Another new set of detections helps organizations spot shell evasion techniques. These new detection rules are mapped to the MITRE ATT&CK® framework and developed in our public detection repo.
Try it out
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. If you’re new to Elastic Cloud, take a look at our Quick Start guides (bite-sized training videos to get you started quickly) or our free fundamentals training courses. You can always get started with a free 14-day trial of Elastic Cloud. Or download the self-managed version of the Elastic Stack for free.
Read about other Elastic Stack highlights in the Elastic 8.2 announcement post.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.