Elastic Security 8.1: Stop novel attacks in their tracks

With the release of Elastic Security 8.1, enhance defenses against novel attacks like Log4Shell and prevent adversaries from compromising macOS systems. Achieve visibility into host-based network activity, leverage new sources of threat intelligence, collect data from across your enterprise, and more.
Let’s jump in.
Defend in depth against emerging exploits
Log4j protections
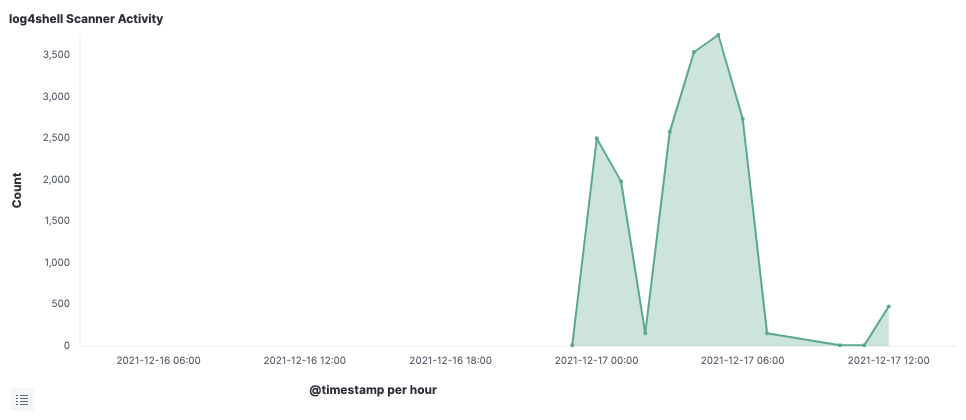
Just hours after an unprecedented Log4j vulnerability was publicly announced on December 10, Elastic threat researchers detailed how to defend enterprises with Elastic Security, sharing a Log4j research brief, complete with targeted searches and automated protections. We also buttressed existing attack-agnostic protections with threat-specific detections, streamlining investigation and preparing organizations for future JNDI-based exploits. Over the following week, amidst the subsequent discovery of several related vulnerabilities, we shared further findings and protections, helping organizations mitigate risk without diminishing visibility.
Windows protections
Likewise, our original research into the BLISTER malware campaign shaped the development of new malicious behavior protections for Windows systems. These preventions help secure RunDLL32 — a popular ransomware vector — and block multiple methods for malicious credential access, including NTDS and CredMan. To further buttress the security of Windows systems, Elastic shared detection rules for centralized alerting on suspicious PowerShell payloads and scripts, attempts to remotely reset Windows passwords, and accounts identified by Azure AD as having heightened likelihood of compromise. These new protections are mapped to the MITRE ATT&CK® framework, addressing attack techniques related to Execution, Persistence, Discovery, and other tactics.
macOS protections
To overcome the escalating threat activity targeting macOS systems, Elastic Security has released several sets of out-of-the-box protections. A substantial portion of these artifacts interrupt methods for illicitly accessing user credentials and escalating account privileges. Additional macOS protections thwart avenues for attackers to reveal, bypass, and evade security controls. Together, these capabilities bolster defense-in-depth on macOS systems.
Deepen visibility to accelerate detection and response
Network packet analysis with Elastic Agent
To ingest host-based network activity with Elastic Agent — in addition to gathering logs, stopping ransomware and advanced threats, and enabling remote host inspection and response — check out our new Network Packet Capture integration. It includes a free commercial license for Npcap, the widely deployed packet sniffing library for Windows, enabling network visibility on every host, no matter the OS.
Companies can now collect and normalize network packets from an unlimited number of Windows, macOS, and Linux systems, equipping practitioners to monitor for suspicious activity and glean valuable forensic insights. This data reveals traffic that firewalls can’t see, helping security teams address malicious behavior within and beyond the network perimeter, like watering hole attacks, data exfiltration, and DNS attacks.
New threat intelligence feeds and data integrations
Elastic Security 8.1 streamlines the ingestion and normalization of threat intelligence from Recorded Future, ThreatQuotient ThreatQ, and Cybersixgill. The solution applies threat intelligence from an array of providers to power dashboards, detection rules, and contextual data enrichment, helping analysts automate detection, improve prioritization, and accelerate practitioner-driven analysis.

The release also builds on the connectors introduced in previous releases with our most substantial set of data integrations yet:
- Vulnerability details from Tenable.sc, for assessing security posture and triaging remediation steps for reducing exposure to newly disclosed attacks
- Cloud and network events from Akamai, AWS Network Firewall, ModSecurity, QNAP NAS, and Zscaler Internet Access and Zscaler Private Access, for broadening environmental visibility and achieving key use cases
- DevOps logs from Microsoft SQL Server, VMware vSphere, and Atlassian Jira, Confluence, and Bitbucket, for enabling rapid and secure app development and deployment
- Host events from Symantec Endpoint Protection, for securing hosts
- User data from Auth0, for monitoring login behavior
Streamline analysis, detection engineering, and endpoint administration
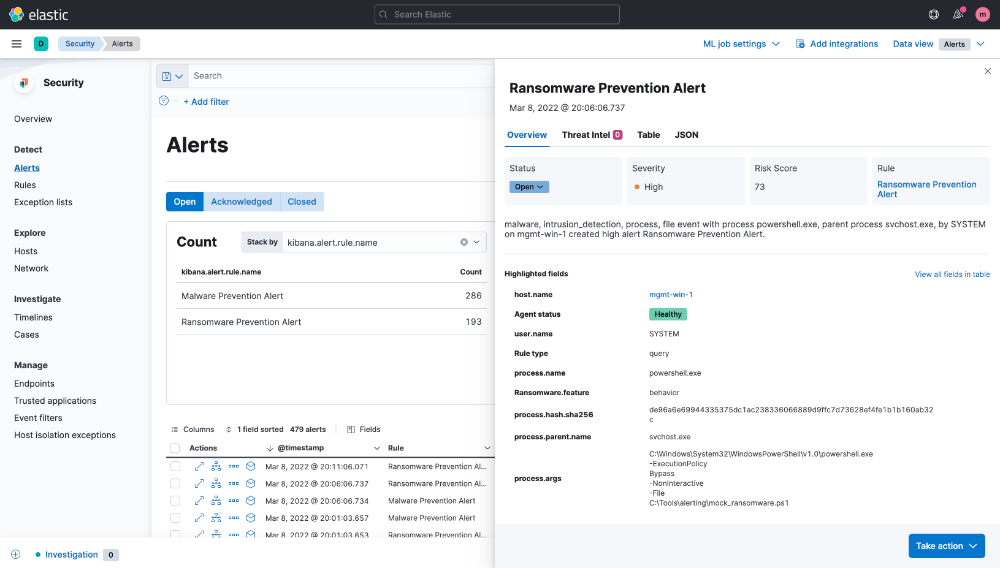
Version 8.1 equips practitioners to triage and investigate alerts faster. Directly from the flyout displayed upon clicking an alert, analysts can update status, view key details, and access relevant context. With just one click, they can view the alert in table or JSON form — or drill in by adding specific values as Timeline query parameters. We’ve applied corresponding design logic to the interface for viewing the details of a specific event. These refinements simplify the analyst experience while preserving immediate access to full context.
The release accelerates detection engineering with a faster interface for tuning rules. Practitioners can now quickly update the datasets that detection rules operate on by adding or removing index patterns to detection rules in bulk. They can also add or remove tags to multiple custom rules at a time, making it easier, for example, to tag a rule for review during an audit or tag rules that operate on custom application logs.
It also includes an early look at another small way to further simplify rule administration…Want to group by severity? Or easily identify warnings or slow-running rules? From the Rules tab, toggle the Technical preview button to enable sorting of the Rule Management and Rule Monitoring tables.
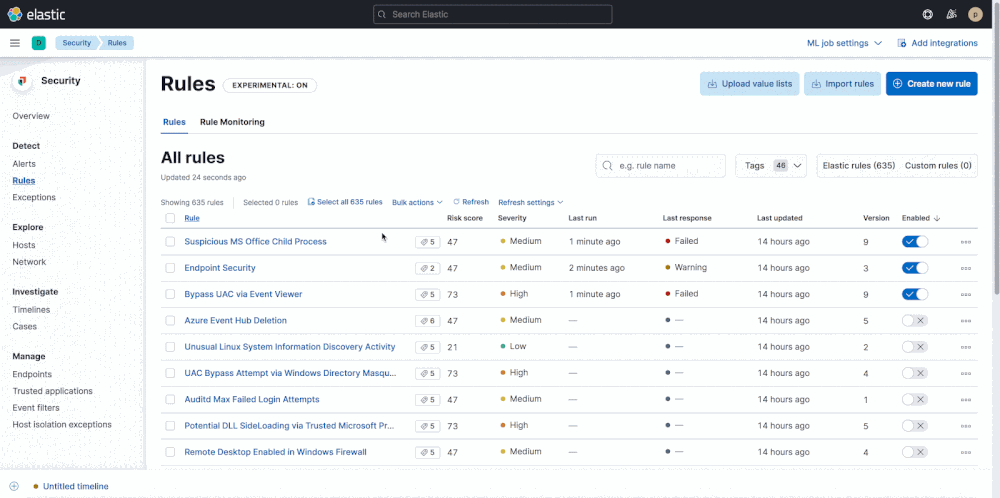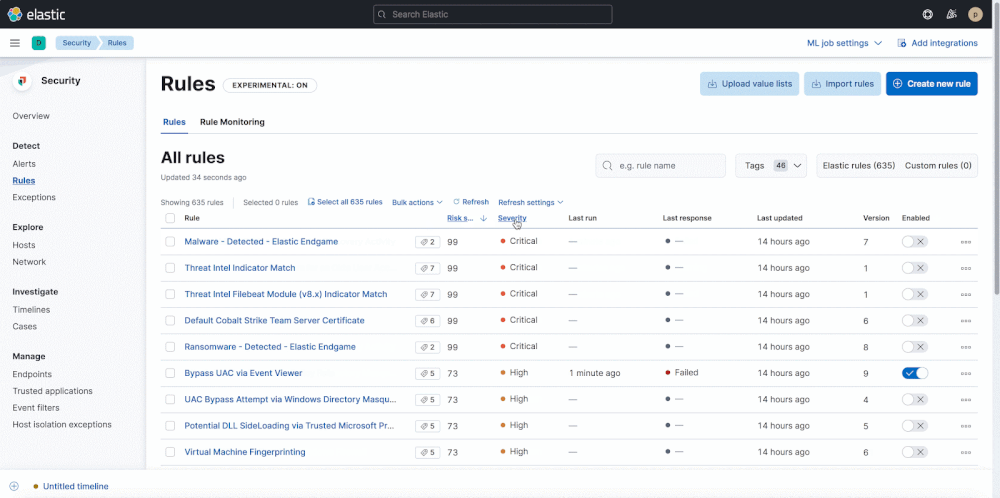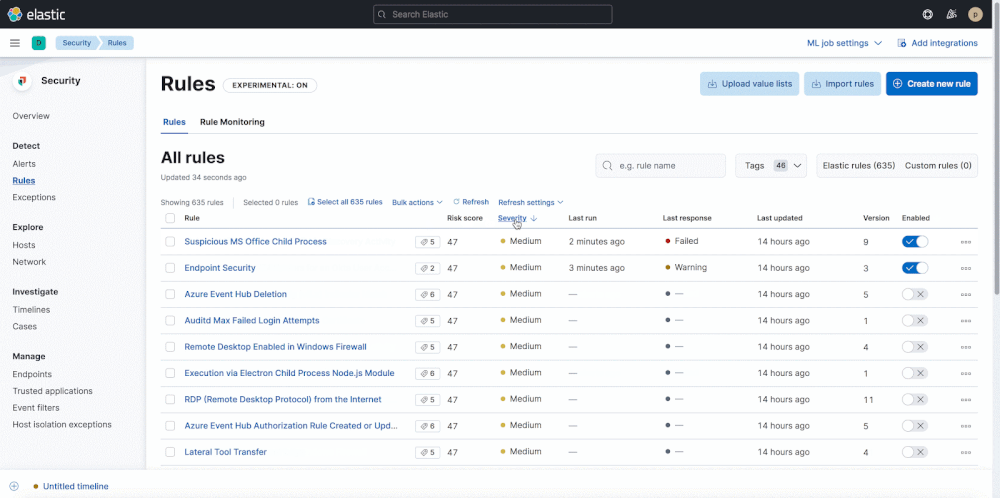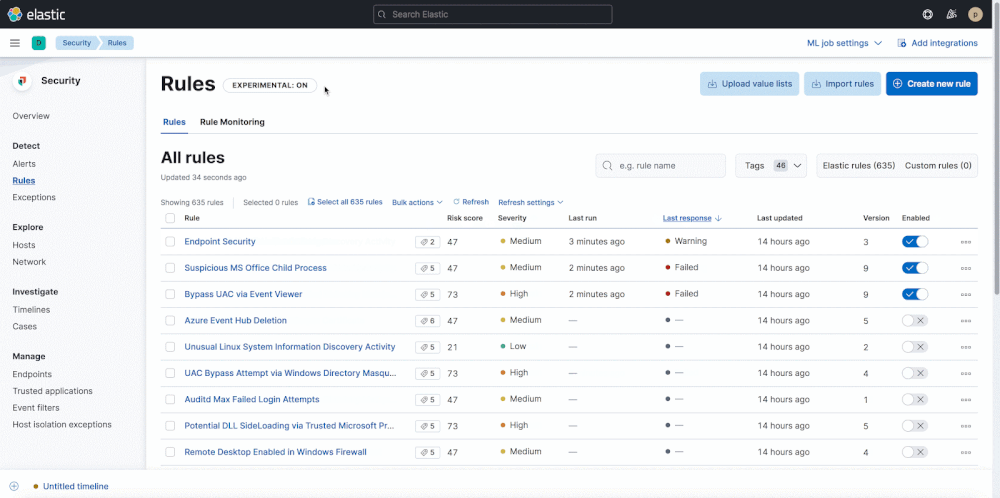
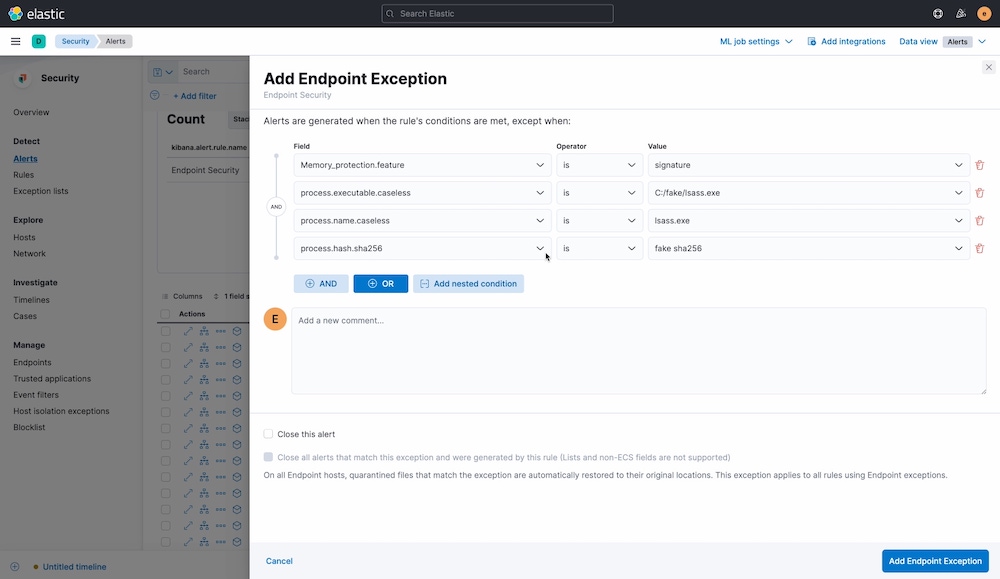
Version 8.1 helps teams avoid alarm fatigue for central and endpoint detections alike by enhancing the alert exceptions UI with at-a-glance visibility into associated conditions.
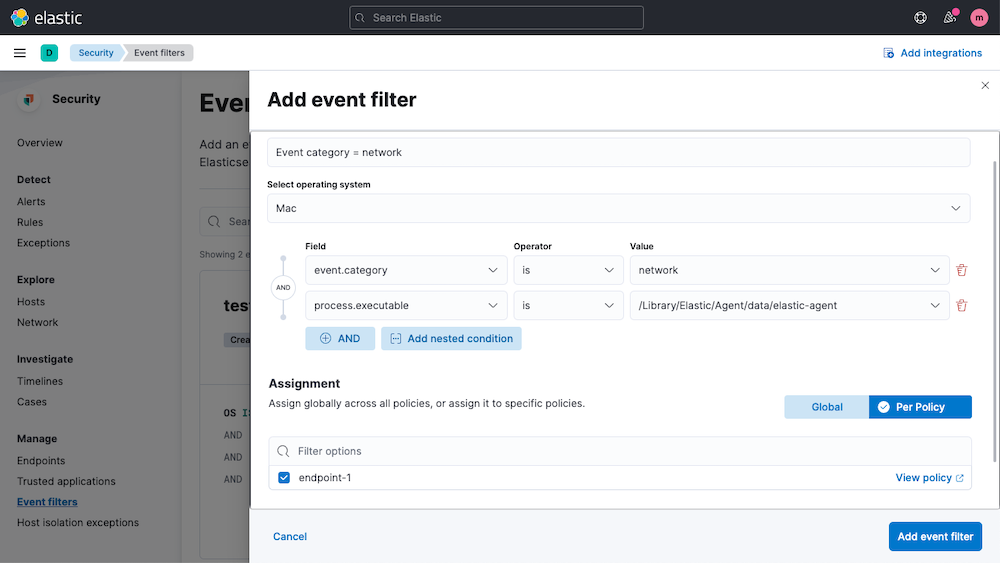
The release enables event filters to be applied per host policy, enhancing control over which events are collected and stored.
Likewise, to preserve visibility into quarantined hosts, IP address exceptions to host isolation controls can now be applied per policy.
Try it out
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. If you’re new to Elastic Cloud, take a look at our Quick Start guides (bite-sized training videos to get you started quickly) or our free fundamentals training courses. You can always get started with a free 14-day trial of Elastic Cloud. Or download the self-managed version of the Elastic Stack for free.
Read about these capabilities and more in the Elastic Security 8.1 release notes, and other Elastic Stack highlights in the Elastic 8.1 announcement post.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.