NEW! Elastic Security 8.13: Manage benchmark rules and automated endpoint responses

Elastic Security 8.13 introduces a refined benchmark-rules experience, advanced endpoint response actions, and a suite of enhancements to help users continue to accelerate their security program.
Some of the major features included in this release enable users to:
Quickly navigate to the relevant compliance content with the reorganized benchmark rules.
Tailor compliance visibility to your needs. Enable and disable specific compliance rules to accurately reflect your organization’s cloud security posture.
Proactively respond to threats with more automated endpoint response actions. Automate process termination/suspension to minimize damage and accelerate response.
Elastic Security 8.13 is available now on Elastic Cloud — the only hosted Elasticsearch offering to include all of the new features in this latest release. You can also download the Elastic Stack and our cloud orchestration products, Elastic Cloud Enterprise and Elastic Cloud for Kubernetes, for a self-managed experience
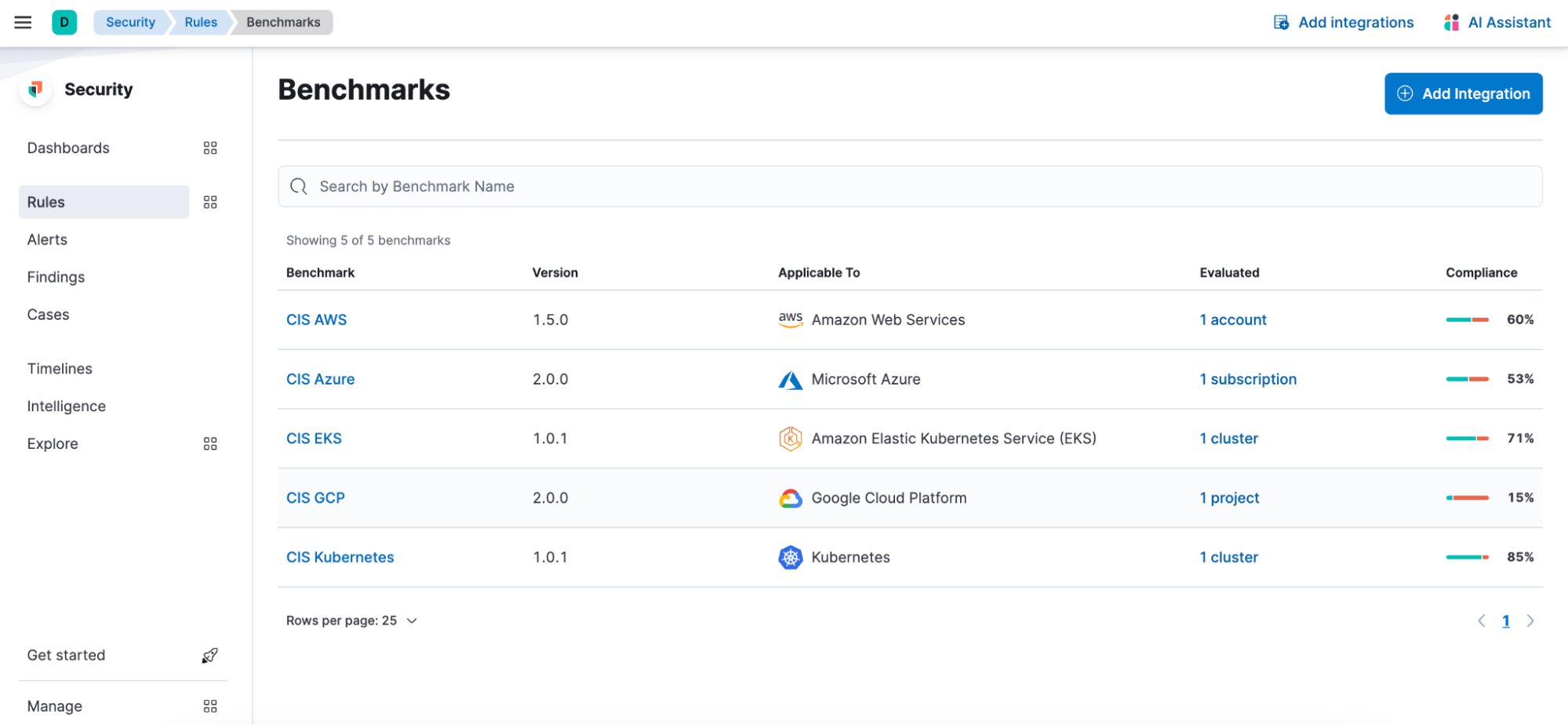
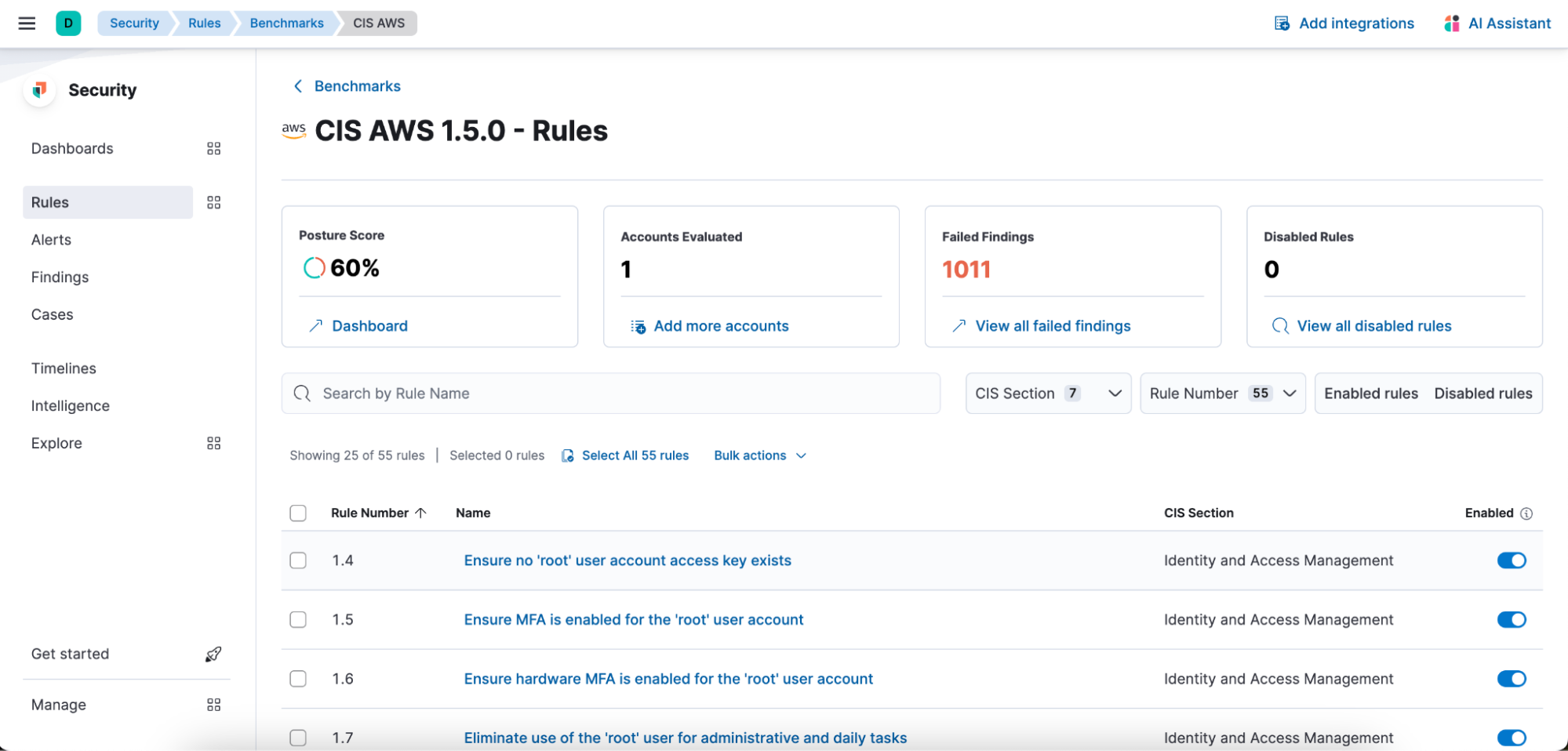
Enhanced CSPM benchmark rules experience
Elevate your security posture through our advanced cloud security posture management (CSPM) benchmark rules. The redesigned page organizes rules by benchmark, expediting decision-making and ensuring a smooth navigation experience. This functionality allows you to tailor your monitoring by enabling or disabling individual rules, providing a customized approach to match your unique environment. This fine-tuning capability enhances your ability to curate a security posture that aligns seamlessly with your specific needs.
Orchestration across endpoints with automated response actions
With the evolving threat landscape and the increasing sophistication of cyber attacks, organizations require proactive security measures. Teams can now configure additional native endpoint response actions via Elastic Defend integration to execute with their detection rules. These actions are automatically executed when a threat is detected. With this update, users can now choose from three powerful response actions to:
-
Kill processes that are associated with a detected threat, effectively stopping the malicious activity
-
Suspend processes that temporarily provide your security team with the opportunity to investigate further before taking further action
-
Isolate hosts from the network, preventing the spread of the threat and protecting other network resources
By allowing users to define endpoint actions with custom detection rules, organizations can proactively protect their networks and respond swiftly to emerging threats. This capability is generally available in 8.13 for every operating system protected by Elastic Defend integration and is accessible via the Elastic Security Enterprise subscription tier for both self-managed and cloud deployments.
Additional enhancements
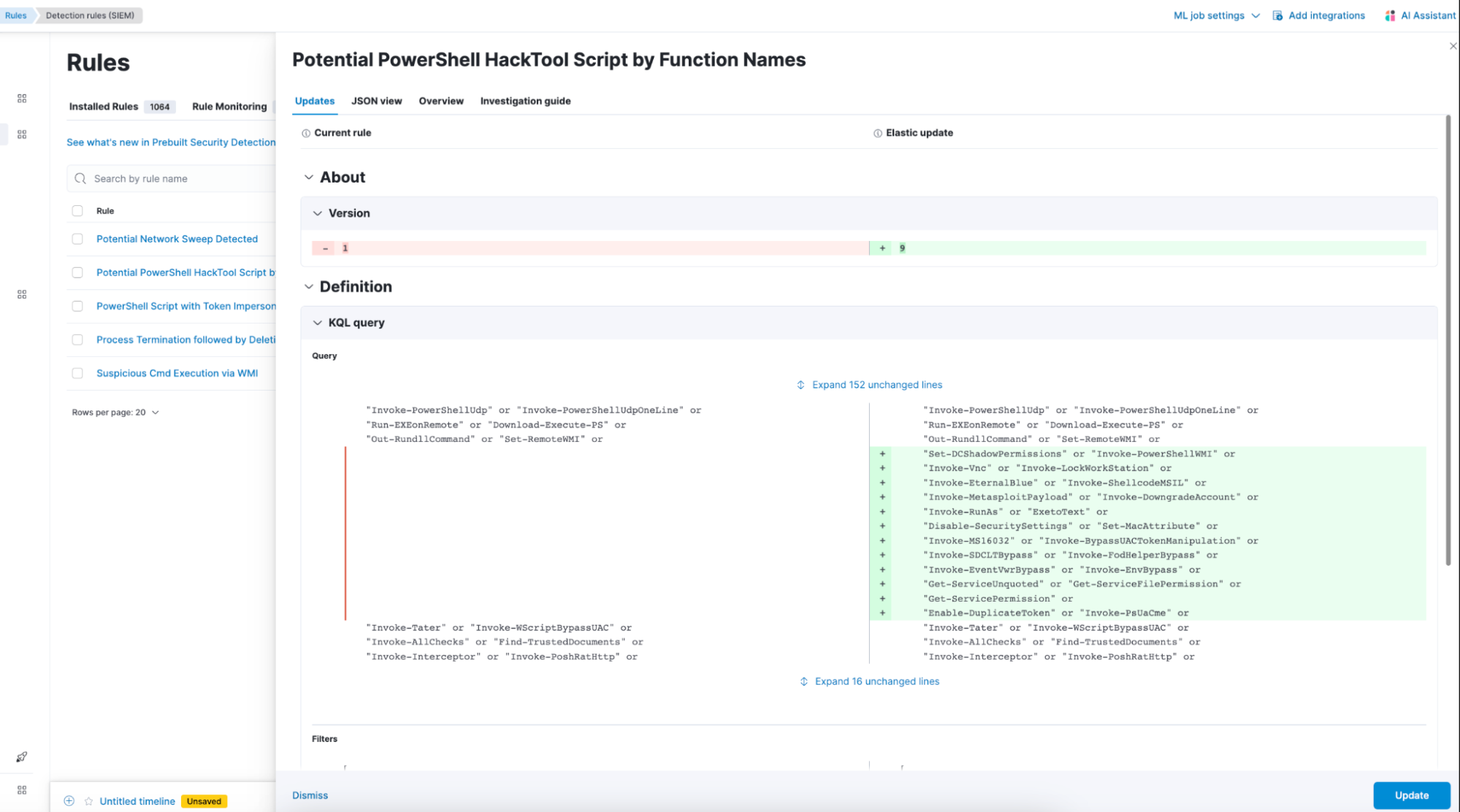
Per-field preview of Elastic Security prebuilt rules updates
Building upon the introduction of the prebuilt rule updates diff interface announced in our 8.12 release, Elastic Security now makes it even simpler to comprehend rule changes with the addition of a per-field comparison feature.
We are constantly monitoring prebuilt detection rules, making refinements to minimize false positives, enhance performance, and broaden coverage. Each out-of-band update brings numerous improvements to multiple prebuilt rules. The per-field diff feature stands as a significant enhancement for users seeking a comprehensive understanding of the impact that incoming rule tunings may have on their detection alerts.
Continued expansion of security integrations
In Elastic Security's commitment to providing seamless data ingestion, version 8.13 sees a continued expansion of our ecosystem with new integrations across threat intelligence, endpoint, and network security. By introducing integrations with CrowdStrike Falcon Intelligence, EclecticIQ, Mandiant Advantage, ThreatConnect, ESET Protect, and Imperva Cloud WAF, our aim is to fortify the security landscape by offering a diverse range of integration options to our users.
Try it out
Read about these capabilities and more in the release notes.
Existing Elastic Cloud customers can access many of these features directly from the Elastic Cloud console. Not taking advantage of Elastic on cloud? Start a free trial.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.