Elastic Security stops memory and kernel attacks in Round 5 of MITRE Engenuity Evaluations
Elastic's security solution successfully identified and stopped memory-based attacks during MITRE’s annual evaluations with powerful detections and advanced machine learning capabilities.

Want to view the MITRE Engenuity ATT&CK® Eval Round 5 Elastic dashboard? Go here.
MITRE Engenuity is a nonprofit organization that provides adversarial threat intelligence and evaluation services to the security community. The ATT&CK framework is a comprehensive knowledge base of adversary tactics, techniques, and procedures (TTPs). The MITRE Engenuity Evaluations: Enterprise are a series of rigorous, adversarial evaluations that assess the effectiveness of security products against real-world threats.
This year, MITRE Engenuity focused on the Turla malware family — a Russian advanced persistent threat (APT) group that has been active since the early 2000s and has seen heightened activity since 2015. Turla is known for its use of sophisticated TTPs, including fileless malware, living-off-the-land attacks, and custom implants.
Elastic® participated in the MITRE Engenuity ATT&CK Evaluations: Enterprise 2023 and has participated in every evaluation to date. Like previous years, we were evaluated on our ability to detect attacks across a variety of platforms, including Windows and Linux. To see our Round 4 results, check out our blog: Elastic protects against ransomware and Linux threats in MITRE Engenuity Round 4 Evaluation.
How does MITRE Engenuity’s evaluation process work?
MITRE Engenuity’s red team will emulate attacker tradecraft while the vendor provides insight into the protections observed. The detection portion of the evaluation does not permit vendors to configure preventions — vendors can elect to partake in the prevention portion where techniques can be stopped. MITRE Engenuity will also note the type of detection a vendor has along with the data source required for the detection (like “process creation”). The detection categories range from ATT&CK-based alerts (called technique detections) to non-signature, behavior-based detections (usually called general detections). We will break down our results and discuss the type of alerts in each category in the next section.
Round 5 marks the first time that Elastic participated in the prevention portion of the MITRE Engenuity ATT&CK Evaluations. In this test, vendors are permitted to enable prevention technology, unlike the detection portion of the evaluation where MITRE Engenuity appraises a vendor's protection capabilities without preventions. We will discuss our results in the next section.
We deployed all of the Elastic Defend integrations, including detection sensors and protection packages. This not only includes the enhanced visibility into events occurring on Windows, macOS, and Linux operating systems that enables the security analytics and rules highlighted during the evaluation, but also the core protection technology. This technology prevents malware and ransomware from executing and stops advanced threats with malicious behavior, memory threat, and credential hardening protections — all powered by Elastic Security Labs and our global community. All of this was highlighted during the evaluation.
How Elastic Security stopped the attack
So, how did Elastic Security perform in Round 5? Let’s start with a critical piece of the evaluation: how did you stop the attacker? In all but two tests, we were able to stop the attack in the first step, which represented the delivery or initial execution of malware, a necessary prevention to stop the attack before there was any damage or loss. The malicious behavior prevention integration from Elastic Security for Endpoint was at its finest here. Not only does Elastic Security for Endpoint provide malware prevention, but the behavior prevention technology stopped the adversary tradecraft.
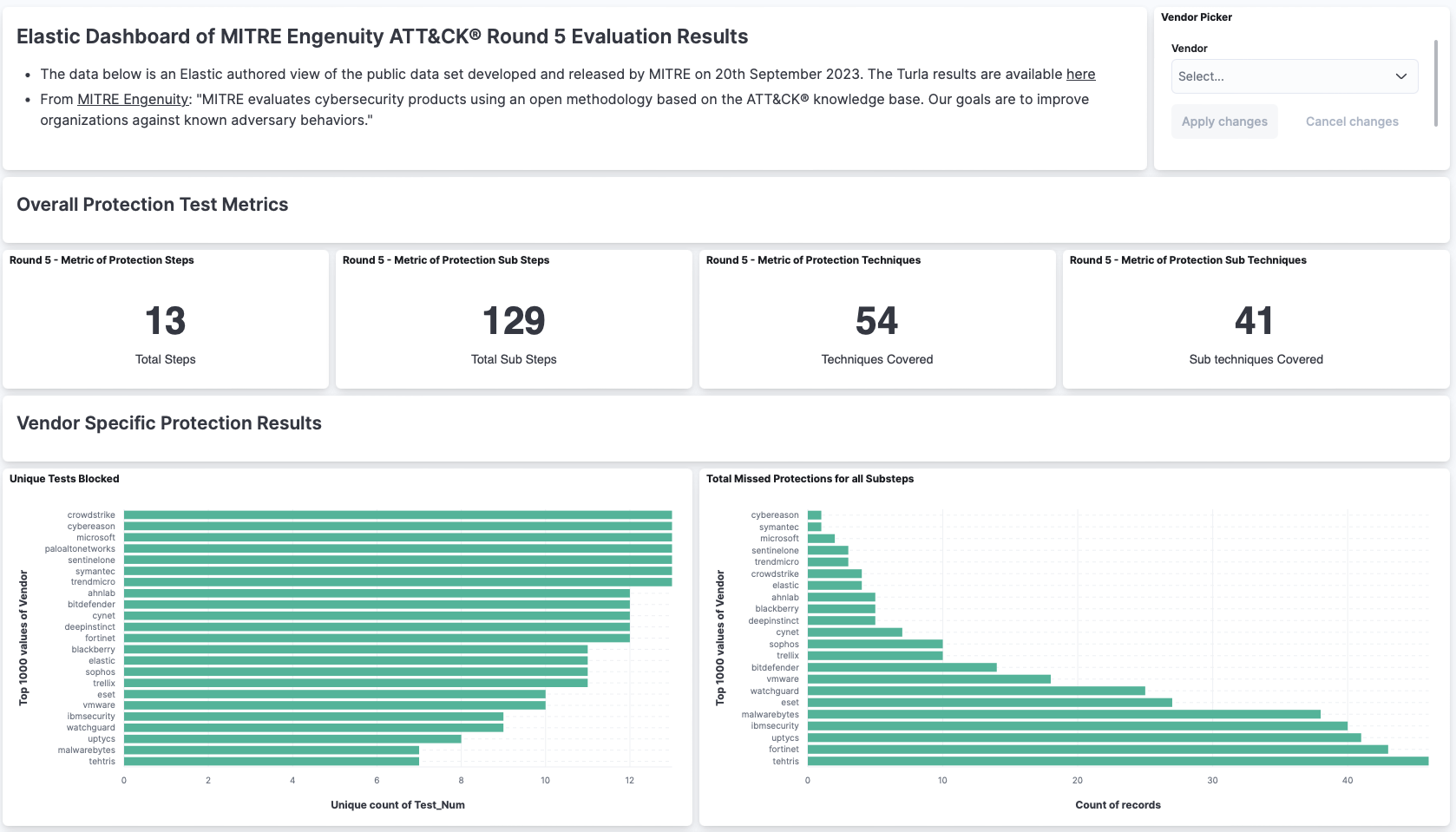
Looking at the detection side of the evaluation, we see more validation of Elastic Security use cases. Here are a few examples:
- Visibility. Utilizing Elastic Security, we collected the core telemetry that empower our prebuilt rules powered by Elastic Security Labs.
- Memory-based protections. During this evaluation, the red team utilized memory and kernel level attacks. Elastic Security’s memory protections not only detected this behavior, but also provided enhanced in-memory visibility to contextualize other alerts.
- Behavior vs. signature detections. Elastic Security has a more behavior approach to detections. This was mentioned earlier in the prevention evaluation, but even in the detection portion of the evaluation we see evidence of this. As some signature based rules led to “technique” detections (a category defined by MITRE Engenuity), the behavior detections were highlighted as “general” and “tactic” based detections. These alerts were powered by machine learning, malicious sequence based rules, Elastic’s behavior protections, and more.
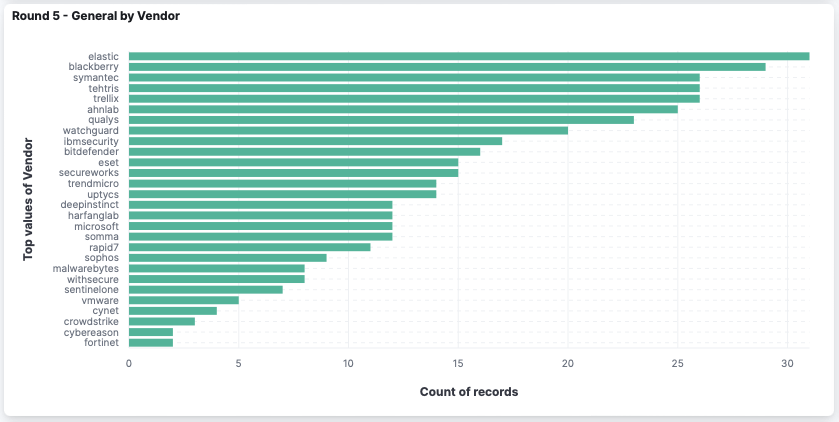
And finally, something not highlighted during this evaluation, as its focus was the detections, was the user experience. Elastic Security’s alert experience provides a streamlined approach to investigating and correlating data. We leaned heavily into our insights to find related alerts and events, providing the necessary contextual information to the analyst. Even without an alert, we utilized visualization capabilities like Analyzer and Session View to correlate events to alerts. And this experience has evolved even further since the evaluation. The next section will dive into the features added since we were evaluated.
Continued progress on prevention and detection capabilities
Elastic Security continues to innovate and improve our security solutions. In the last MITRE Engenuity ATT&CK Evaluation, we were evaluated using Elastic Security 8.7. Since then, we have made a number of improvements in our most recent Elastic Security release, 8.10, which provides enhanced attack prevention and detection capabilities. These improvements include:
- Elastic AI Assistant: The new generative AI sidekick helps analysts triage and investigate suspected attacks faster and more effectively. Synthesize alert details, get suggestions on next steps, automate tasks, and more all within Elastic.
- Reimagined investigations: We have redesigned the investigation experience in Elastic Security to make it faster and more effective to investigate alerts, discard false positives, determine the root cause and scope of attacks, and respond before damage is done.
- MITRE mapped detection rules: We have added a number of new rules to Elastic Security that show the coverage provided by prebuilt and custom rules across inventoried tactics and techniques and help practitioners address gaps using detections from Elastic Security Labs.
- More protections: We have added a number of new protections to Elastic Security to help to prevent a wider range of threats. These protections include file integrity monitoring, process monitoring, and network traffic monitoring.
- Endpoint response actions: We have added a number of new endpoint response actions to Elastic Security for Endpoint. These actions allow you to take automated actions to respond to threats, such as quarantine files, kill processes, and block network connections.
Many thanks, MITRE Engenuity
We would like to thank MITRE Engenuity for the opportunity to participate in the ATT&CK Enterprise Evaluations. We learned a great deal from this experience, and we are committed to continuing to improve our product to help our customers protect themselves from advanced threats. Until next time!
Ready to give Elastic Security a spin? Try it free today!

The views and opinions expressed in this are those of Elastic and do not necessarily reflect the views or positions of any entities they represent.
The release and timing of any features or functionality described in this post remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.