AI-driven SIEM that is
open source and affordable
Elastic SIEM is proven in thousands of real-world environments and powered by AI — helping you detect threats faster and scale without overspending.
Guided Demo
Find the threats lurking in your data
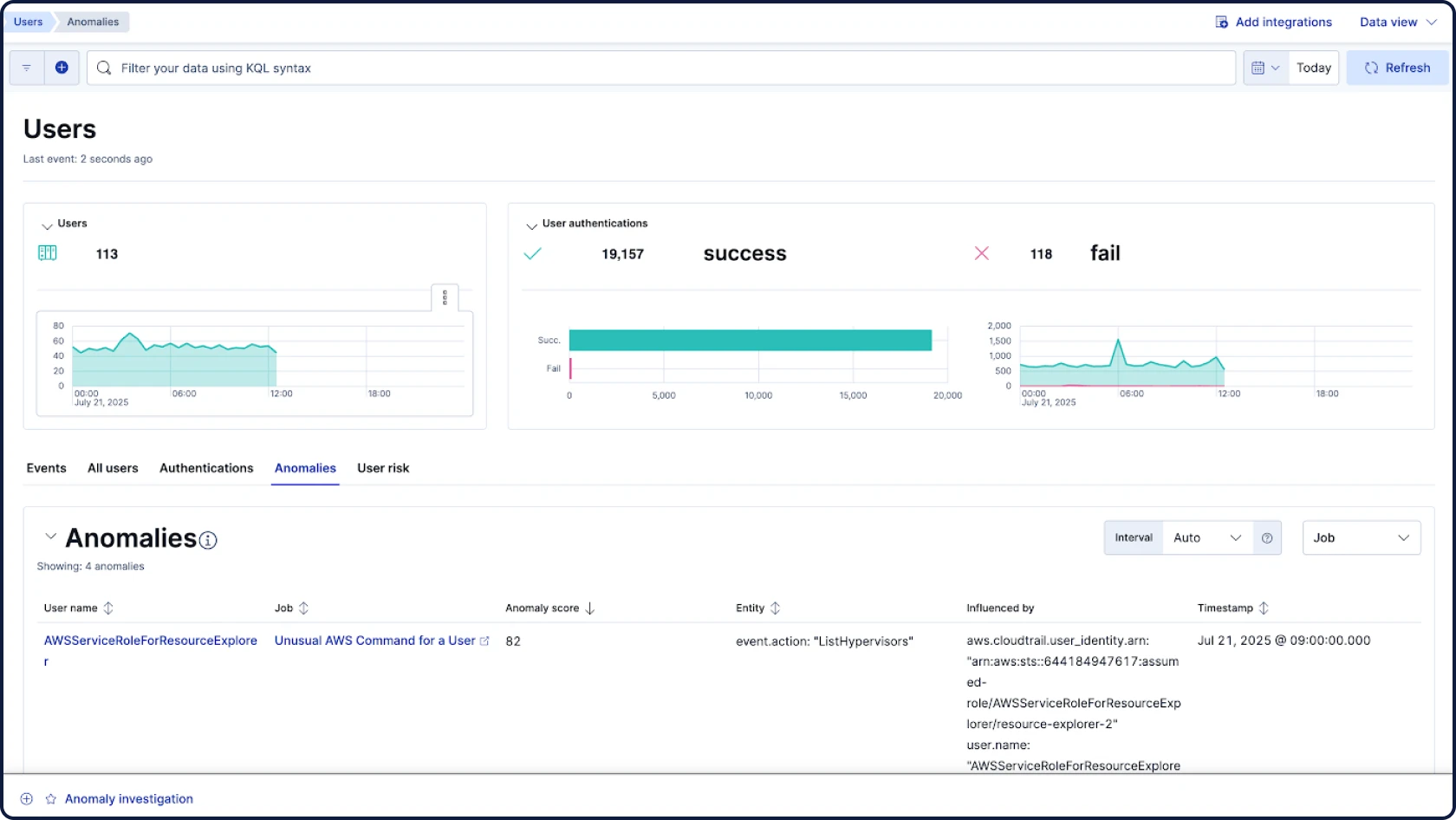
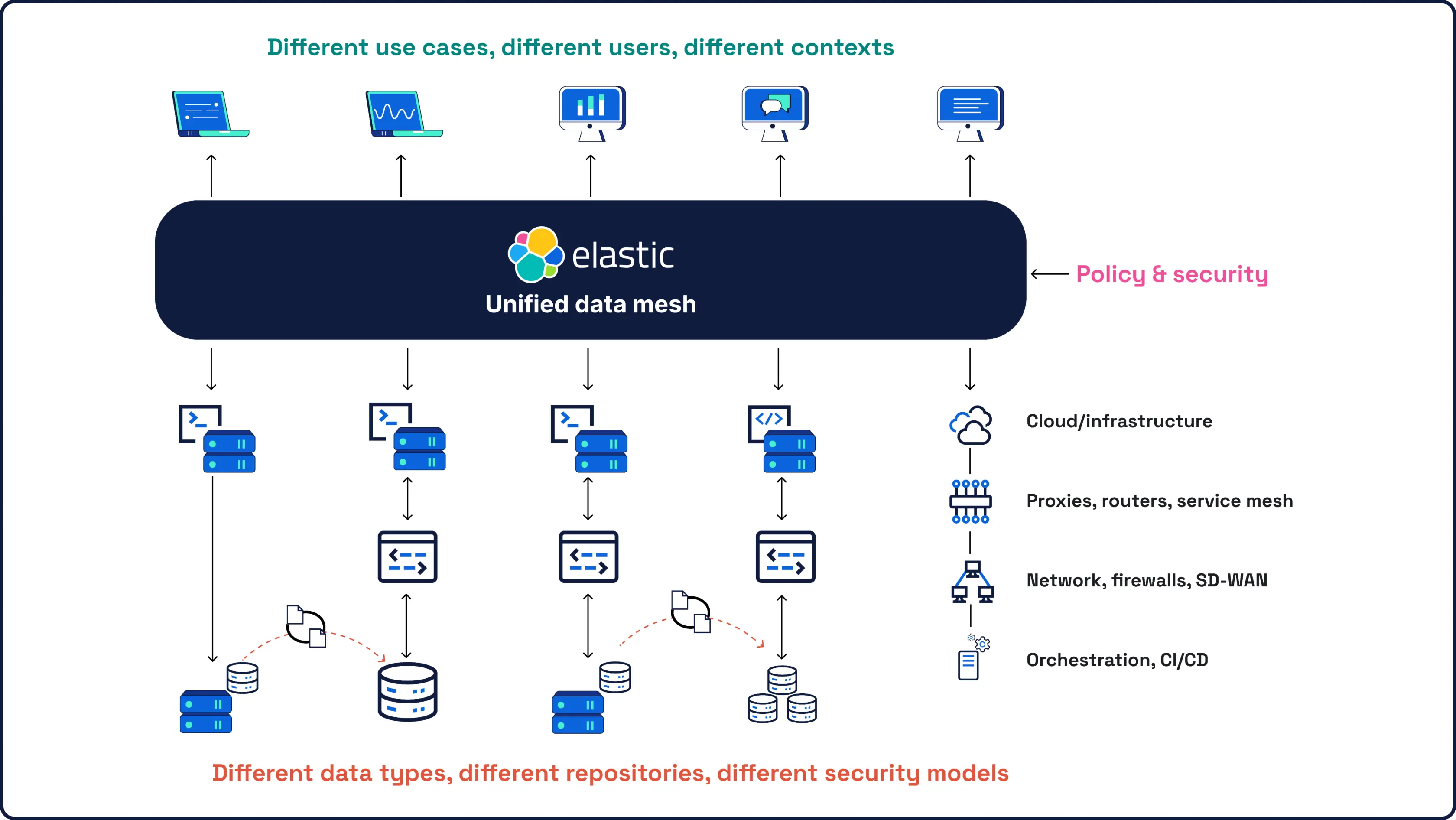
Security starts with data — and data is what we know best. As the company behind Elasticsearch, the world's leading open source search and analytics engine, our SIEM brings powerful, AI-driven detection and investigation to all your security data, at any scale.
HUNT & INVESTIGATE
The SIEM for tomorrow's SOC
All your security data, AI, and investigations in one open, extensible, and scalable platform
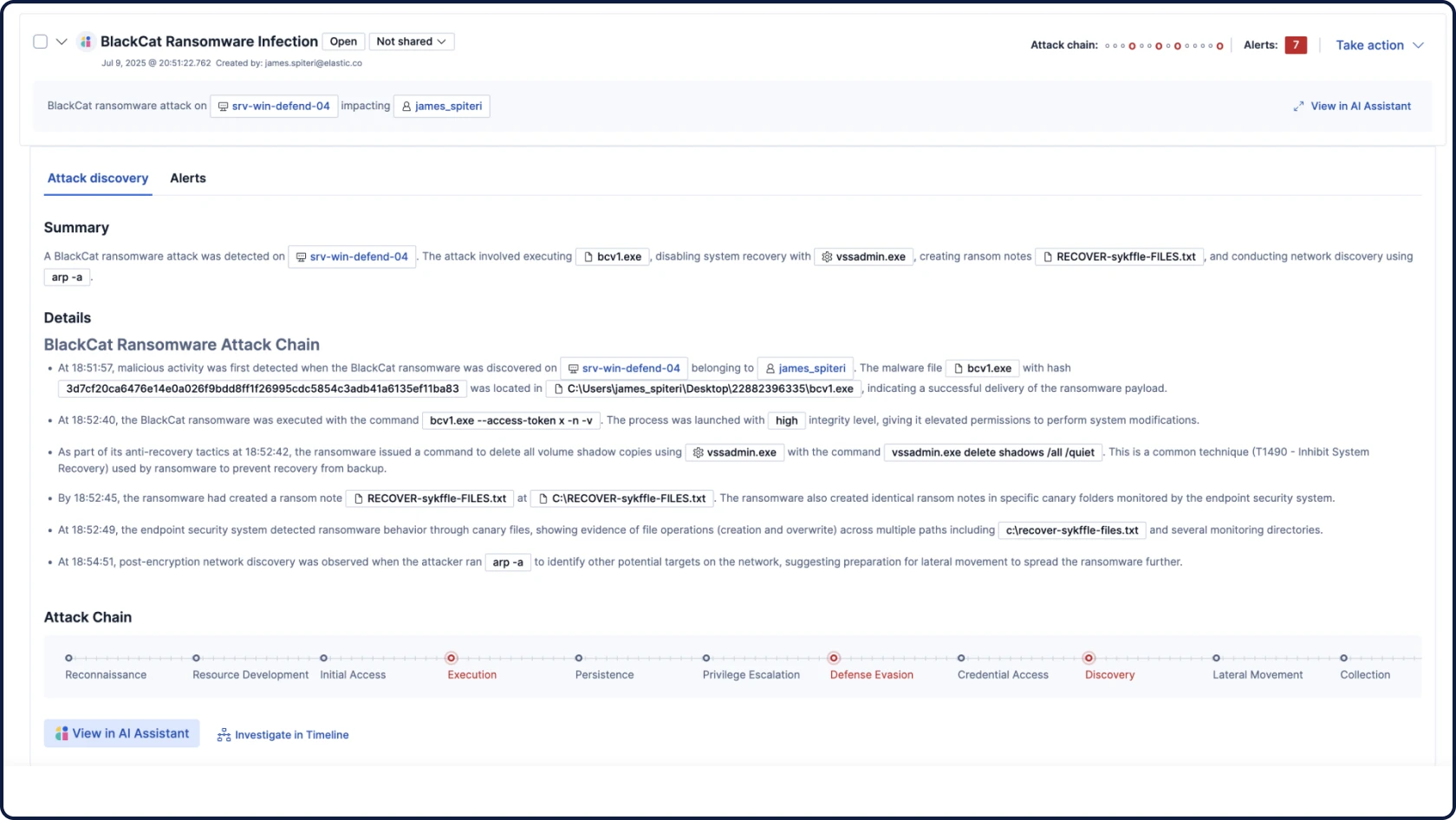
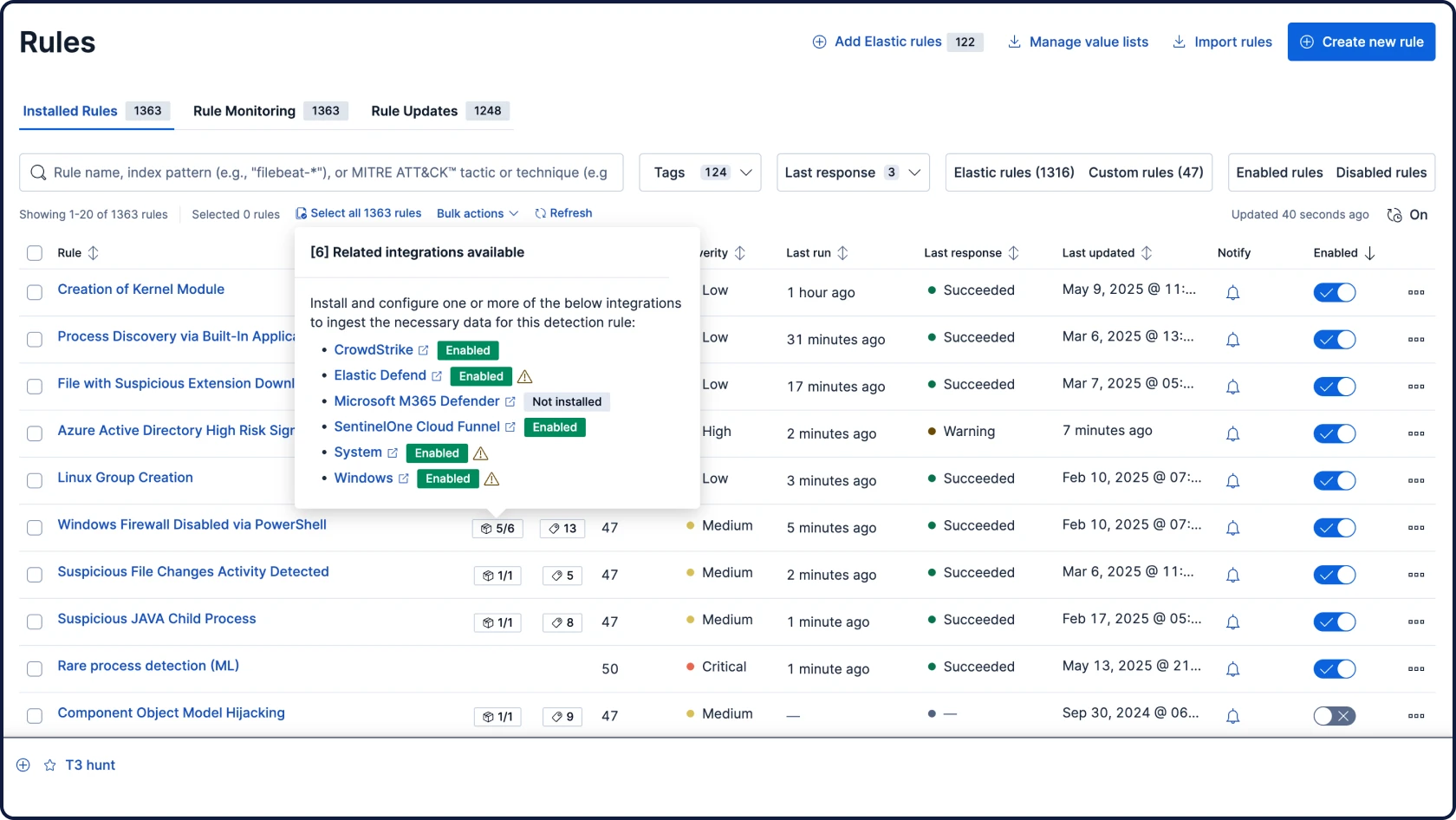
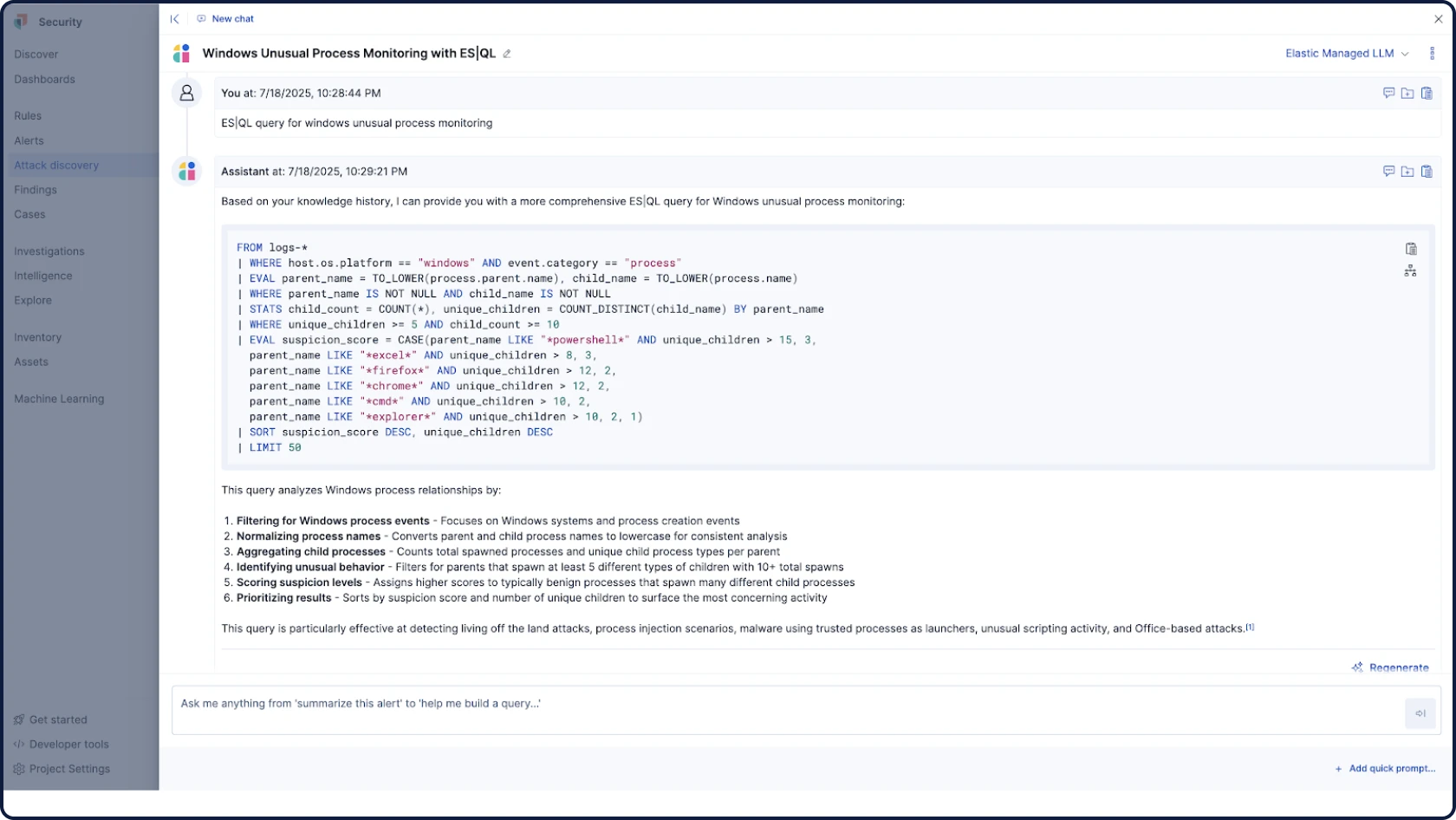
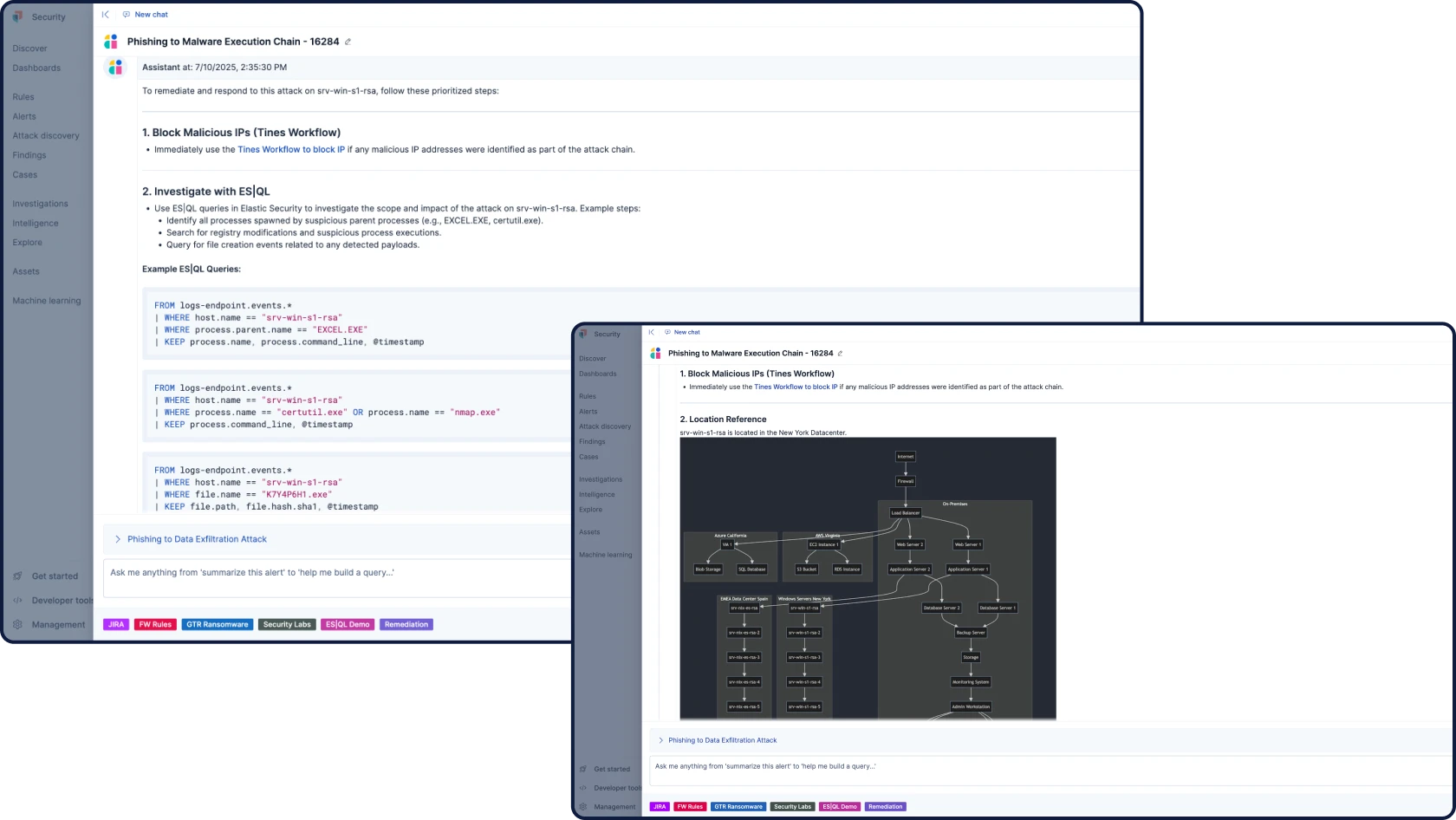
Automate your workflows with grounded, contextual, and transparent AI for security. Attack Discovery identifies real attack behaviors and paths by correlating alerts, while AI Assistant answers questions and guides an analyst’s next steps.

PACKAGING OPTIONS
Adopt it all, or go at your own pace
Our security platform meets you where you are — and takes you where legacy platforms can't.
Elastic Security
Everything you need — SIEM, XDR, cloud security, and integrated AI — in one unified platform. No extra SKUs, no bolt-ons, no compromises. Just a single seamless experience built for the way analysts think, hunt, and respond.
Elastic AI SOC Engine (EASE)
A package of AI capabilities that allows you to adopt Elastic Security on your schedule, without a full rip-and-replace. Bolster your existing SIEM, EDR, and other alerting tools with AI that plugs into your data and workflows — and expand to the full platform when you're ready.
You're in good company
Customer spotlight
 Airtel improves cyber posture with Elastic’s AI capabilities, boosting SOC efficiency by 40% and accelerating investigations by 30%.
Airtel improves cyber posture with Elastic’s AI capabilities, boosting SOC efficiency by 40% and accelerating investigations by 30%.Customer spotlight
 Sierra Nevada Corporation protects its infrastructure, and that of other defense contractors, with Elastic Security.
Sierra Nevada Corporation protects its infrastructure, and that of other defense contractors, with Elastic Security.Customer spotlight
Mimecast centralizes visibility, drives investigations, and cuts critical incidents by 95%, transforming global SecOps.
Join the chat
Connect to Elastic Security's global community — from open conversations and collaboration to hardening our product through our bug bounty program.











.jpg)
