Elastic and Cmd join forces to help you take command of your cloud workloads
We are excited to announce that Elastic is joining forces with Cmd to accelerate our efforts in Cloud security - specifically in cloud workload runtime security. By integrating the capabilities of Cmd's expertise and product into Elastic Security, we will enable customers to detect, prevent, and respond to attacks on their cloud workloads. Adding to our recent announcement to acquire build.security, this will give customers cloud security protections from build-time, to deployment-time, to runtime.
Cmd is a leader in infrastructure detection and response (IDR), providing deep and performant visibility into cloud workloads using extended Berkeley Packet Filter (eBPF) technology and performing expert detection and prevention on cloud-native data. eBPF has revolutionized how organizations observe and protect cloud workloads. By safely and efficiently running sandboxed programs in the Linux kernel, developers can rapidly innovate and deliver entirely new Observability and Security outcomes to users. This combination is a reflection of our commitment to eBPF and such technologies that enable users to observe and protect modern cloud-native systems in the most frictionless way possible.
Cmd also aligns with Elastic's commitment to delighting the developer and practitioner community. The Cmd product embraces a developer-first approach, delivering experiences that all practitioners, from developers to operations, DevOps, site reliability engineers, and security experts can embrace. We are excited to expand Elastic's portfolio with a shared passion for this community.
Since its inception, Elastic Security has had a clear mission: to protect the world's data and systems from attack. The world's infrastructure is shifting to the cloud, and with this, the need for cloud security is ever increasing. According to the 2021 State of Kubernetes Security report, 94% of organizations admitted to experiencing a security incident involving their Kubernetes or other container environments in the past 12 months, and 55% of organizations reported that security incidents delayed their applications' deployment into production.
Completing the cloud security vision
Only recently, we announced that we are joining forces with build.security to address the needs of continuous cloud-native security, using Open Policy Agent (OPA) to ensure that cloud environments are secure to the policies defined by the business, both at deployment-time and in the future at build-time. By joining forces with Cmd, we are taking a significant step toward fulfilling this vision, and addressing the need for workload runtime security.
We asked co-founder and Chief Security Officer of Cmd, Jake King, to give some background on the company in his own words:
"Cmd was born out of Expa and matured as the brainchild of discussions between Expa General Partner Milun Tesovic and me. Milun and I focused on solving the challenges of addressing Linux observability and security challenges in an efficient way that doesn't bog down production servers and can grow to enterprise scale.
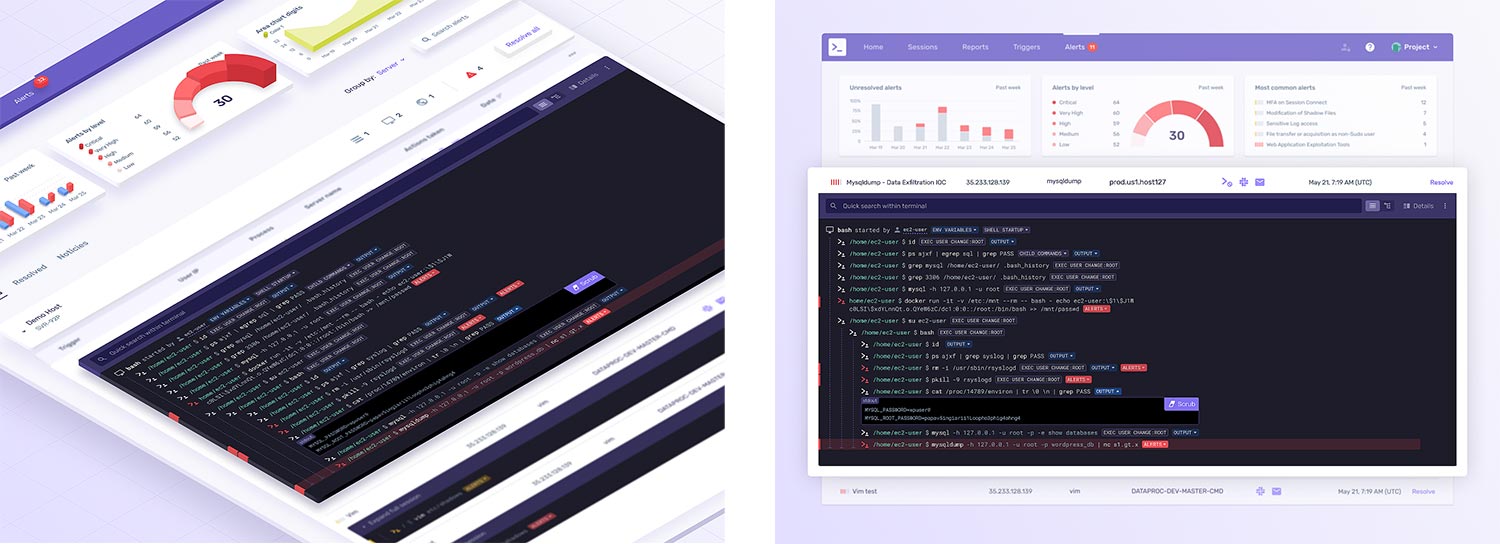
The growing need for IDR is clear. The volume and sophistication of attacks in the cloud continue to rise, and over 90% of this critical infrastructure runs on Linux. Attackers can quickly gain shell access and use native Linux tools to conduct reconnaissance and move laterally from machine to machine. Unfortunately, most security solutions fail to provide visibility and detection for these Linux-specific adversarial techniques. Security teams need detailed and precise Linux telemetry, so they can investigate and respond to these threats quickly and effectively.
As sophisticated adversaries gain further traction within cloud ecosystems and the circumvention of traditional Linux sensor technologies grows, eBPF-based technology has become a cornerstone of efficient, safe, and all-encompassing observability for Linux. Cmd has been a leader in eBPF-based security detection, with specific technology aligned with native system process execution and live session observability.
Combining this powerful agent-based technology with the incredible capabilities of the Elastic platform will bring customers unprecedented capabilities for powerful threat detection and prevention while maintaining system performance."
Elastic Security already includes EDR-style kernel-level visibility into Linux systems, as well as powerful Linux protection capabilities like malware prevention, numerous MITRE ATT&CK-mapped advanced Linux rules, and even upcoming features like host isolation of Linux hosts. With the technology and expertise we gain through this teaming with Cmd, we will be able to expand our security capabilities even further for cloud-native application workloads, all implemented using the frictionless approach made possible with eBPF.
The plan
We believe in the force multiplier effect that comes from joining with focused, innovative teams like Cmd. Our intent is to start by working together to integrate Cmd's cloud-native data collection using eBPF directly into Elastic Agent. In parallel, we will integrate Cmd's innovative and practioner-orientated user experience and workflows directly into Kibana. The Cmd team has built many differentiated workflows for DevSecOps users, like the Cmd Session view, that we are excited to integrate into Kibana and make available for all users and use cases.
We are excited that both, existing Elastic customers, as well as existing Cmd customers will benefit from this integration. Existing Elastic customers will get all the cloud-native security capabilities that CMD has built over the past few years. Existing Cmd customers will also benefit from this work because they will be able to take advantage of this more comprehensive, integrated product once the integration is complete.
But this is just the beginning. We asked Cmd CEO Santosh Krishnan to discuss his views on the future of Limitless XDR with IDR capabilities. In his own words -
"We are incredibly excited to join forces with Elastic Security to bring comprehensive cloud runtime security to our customers. Any robust cloud security program starts with a strong analytics foundation - an area in which Elastic Security is a proven leader. Together, we will deliver intuitive investigative workflows on top of that foundation, along with preventive controls, detection and response, to enable customers to quickly find attacks and stop them in their tracks. We look forward to being part of the Elastic team and making this vision a reality."
Continuing to add to the value of resource-based pricing
In 2019, when Elastic joined forces with Endgame we dramatically changed how client endpoint security is priced by removing per-endpoint pricing. We are excited to continue this disruption by adding cloud workloads to the definition of "endpoint".
Two years ago, our founder and CEO, Shay Banon said, "Why should users have to count the number of devices they need to protect? Or choose how many days of threat intelligence data they can afford to retain? We want organizations to have the best protection, use it everywhere, and not be penalized with per-endpoint pricing."
This message resonates even more strongly today with the rapid expansion of containers, pods, virtual instances, and other cloud infrastructure.
Elastic customers pay for resource capacity utilized for any solution they use — Elastic Logs, APM, SIEM, App Search, Site Search, Enterprise Search, and now expanded cloud-native security — with a consistent and transparent pricing framework. This simple pricing model ensures that organizations can capture every bit of value from their data.
With Elastic Security, customers get full protection for as many endpoints as they need, and full data collection and shipping without having to compromise.
In summary
Limitless XDR continues to become...well... even more limitless. First by joining forces with build.security, and now with Cmd, we are making major advances in our cloud-native observability and security capabilities by investing in innovative teams that have built differentiated capabilities leveraging open technologies like OPA and eBPF. Elastic users will see these capabilities added over time into the architecture they already deploy today using the power of the Elastic Stack and Elastic Agent. And, Cmd users will now get access to leading XDR capabilities, including hundreds of stateful detections and machine learning models mapped to MITRE ATT&CK, built-in case workflow, client security on Windows and macOS, and anti-malware prevention on Linux, plus the full breadth of what Elastic has to offer.
Follow us at https://www.elastic.co/security to continue to watch the evolution of Limitless XDR.
###
Forward-Looking Statements
This blog post contains forward-looking statements which include but are not limited to statements about future features and functionality. The release and timing of any features or functionality described in this document remain at Elastic's sole discretion. Any features or functionality not currently available may not be delivered on time or at all.