Shell Evasion: An Insider Threat

Cybersecurity strategies within cloud environments are often seen as a complicated landscape with rapidly developing technologies, architectures, and terms. Simultaneously, there are continuously motivated individuals and groups trying to utilize vulnerabilities for illicit uses such as to increase access to the data, install malware, disrupt services, and more.
More recently, a series of observed threat actors have taken advantage of Shell Evasion tactics to evade detection and target unknowing victims — often to successful outcomes given the lack of visibility most organizations have within their infrastructure.
Shell evasion
Cybercriminals are increasingly using stealthy shells to stay undetected on their victims’ computers. A shell evasion attack technique can be used to install malware on the target device, or circumvent controls within the system by evading the detection of rule-based engines.
The term "shell evasion" covers the different ways that attackers can slip around security controls by using false identities. This includes using social engineering, creating false websites, and hidden passageways outside of any defensive perimeter.
Shell evasion techniques are used primarily to avoid detection by anti-malware or intrusion detection systems. One risk is that an attacker can use shell evasion techniques to slip past defenses undetected and gain access to highly sensitive information.
Shell evasion attacks are a method used by astute adversaries that are attempting to get around computer systems by disguising themselves as benign executables and behaviors. Research has found that some of these attacks have been using malicious shell scripts to bypass anti-malware software and avoid detection.
In shell evasion, programs are often developed to execute commands from within the shell. When executed, another process can be launched in the background without the user's knowledge. This can lead to data tampering and other types of hacking that make it unclear who is behind the attack. The vulnerability of shell evasion is often increased by limitations on what commands can be executed in a restricted mode.
Shell evasion attack vector
There are two main types of threats that can occur with Shell execution. The first is the execution threat, where an attacker forces the victim's system to execute a malicious command or script. The other type is the insider threat, where an authorized user executes a command without realizing it could be malicious or performs an undesired (not a standard use) of the command, leading to an evasion pattern from security monitoring tools.
This blog highlights the use cases of spawning interactive shells from various Linux binaries in evasive manners from regular monitoring, leading to an insider threat pattern. An example insider threat scenario can be described as when an employee has access to systems, programs, or data and maliciously uses these privileged assets. This can include things such as altering records, deleting or modifying files and programs, installing software (which may or may not be malicious, or could be unauthorized software) on the company's systems, bypassing security controls via the shell evasion technique.
Preventing shell evasion
Shell evasion can be easily misunderstood or misinterpreted as a shell vulnerability. In general, a vulnerability can always be prevented when upgraded to the patch version or by removing the use cases of the vulnerable library in the source code. It can also be prevented by temporarily suspending services that use the vulnerable library until a patch has been identified. But an evasion technique will continue to prevail if the use case is being adhered to by the library or system.
The most common scenario of shell evasion is executing a Linux command outside of its expected behavior. Similar to a cpulimit command, which in normal scenarios is used to restrict CPU usage of a particular process, a Linux command is used for spawning an interactive shell with the right usage of the command. Therefore, preventing these use cases is highly unlikely, even with the best practices of secure engineering.
The dimension of detecting Shell evasion takes precedence in such scenarios where prevention lies in a more idealistic way of training engineers with best practices of secure engineering.
Detect shell evasions with Elastic Security 8.2
In Elastic Security 8.2 detection rules, a new category of GTFOBin shell evasion rules has been added to the platform. These rules give cloud users greater visibility in interactive shells being spawned from various Linux libraries. In the current release libraries, such as apt (including apt-get), awk, and its various forms — busybox, MySQL, ssh, and others — Linux libraries have been added to the detection rules to identify any user invoking shell via the shell evasion technique. The detection rules can be customized to fire alerts in a manner suitable for the monitored Linux infrastructure.
On a newly deployed Elastic Cloud environment, navigate to the Elastic Security section and then to the Rules from the left navigation panel. There would be no rules currently in the new environment, like the below screenshot.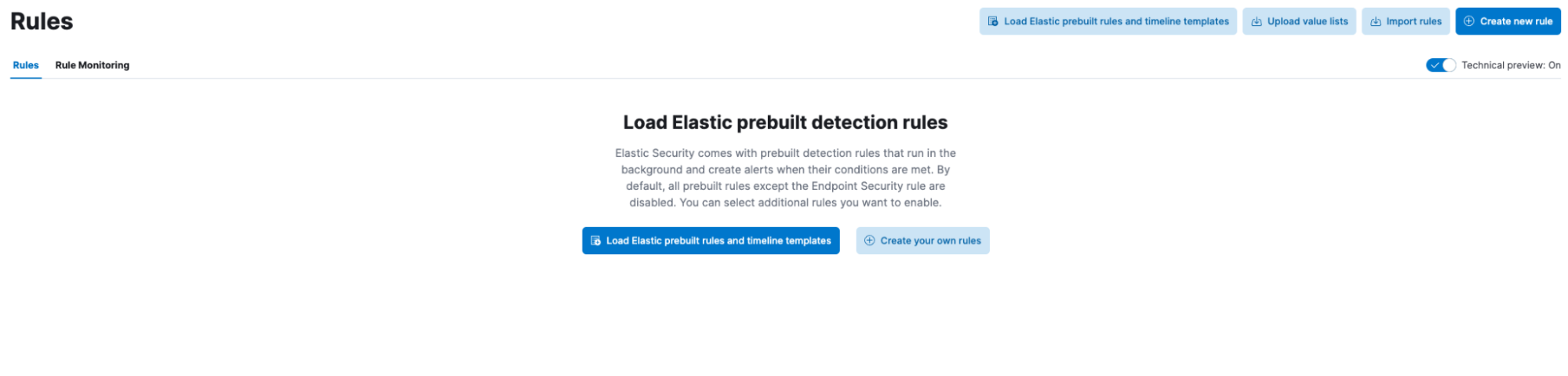
By clicking on the “Load Elastic prebuilt detection rules”, all Elastic configured rules available in this version would be now available for enabling.
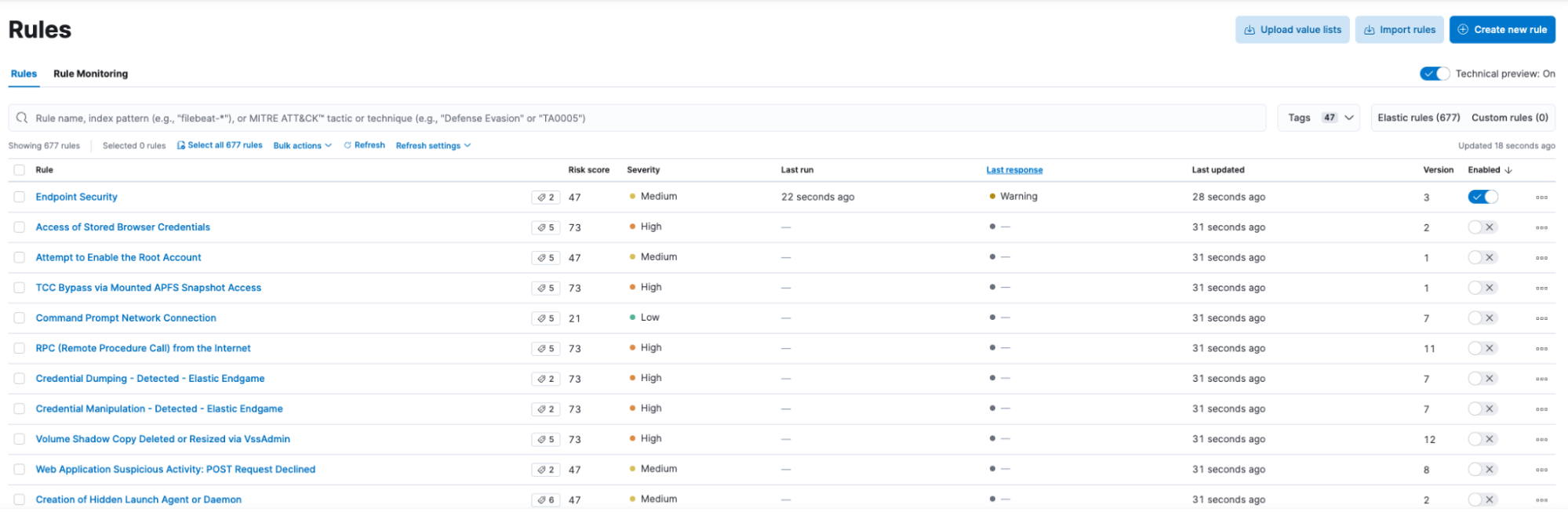
If the Elastic Cloud is a newly deployed environment, we can proceed to add endpoint security to this environment.
Once the endpoint configuration is completed, we can proceed to add hosts.
Enrolling agent is very intuitive and the steps for various OS installations are also provided.
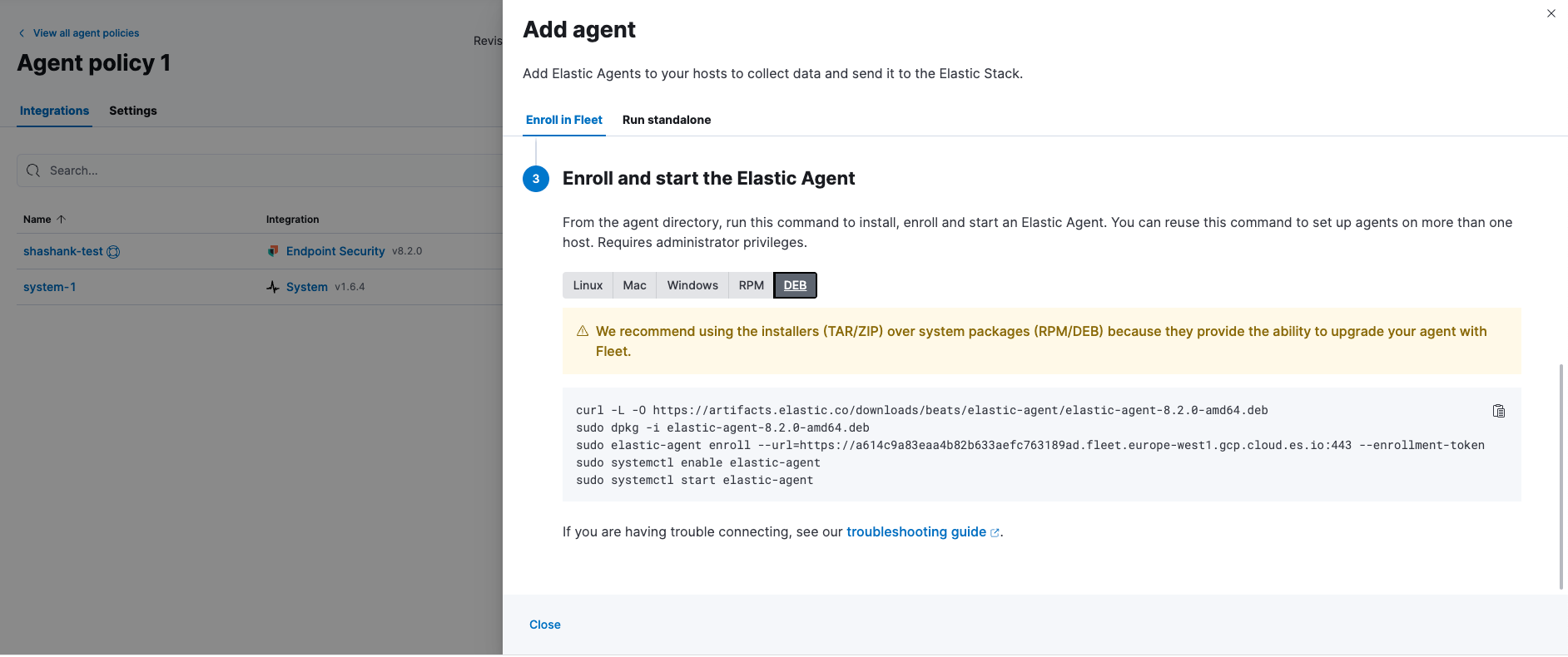
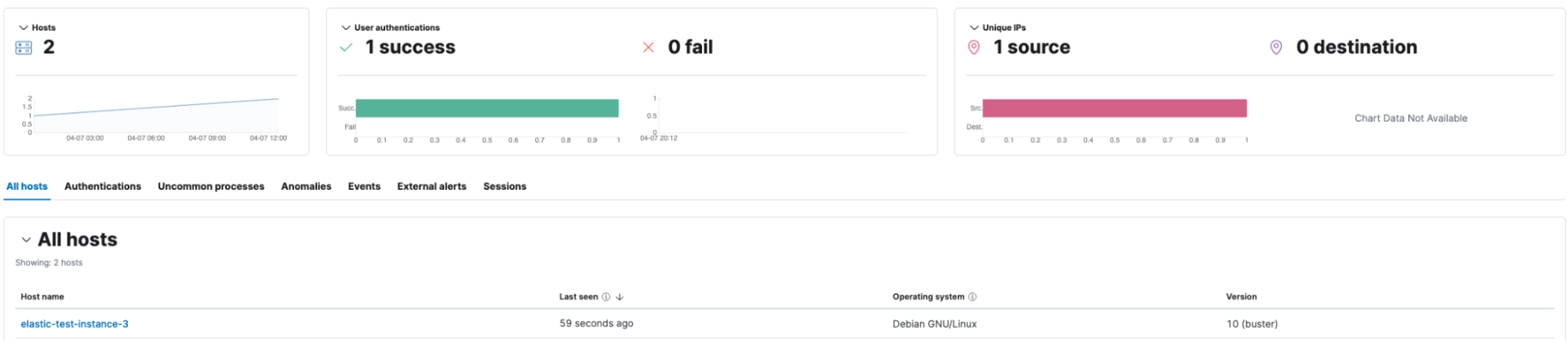
We have now successfully added a host for the environment, enabling shell evasion detection rules.
Note: If there is an existing Elastic Cloud environment, please upgrade to the latest versions and then update the ruleset to the latest version, after these steps we can enable the shell evasion detection rules.
An easy way to look for all shell evasion rules at once is to search via tags, and these rules are bundled under the GTFOBins tag.
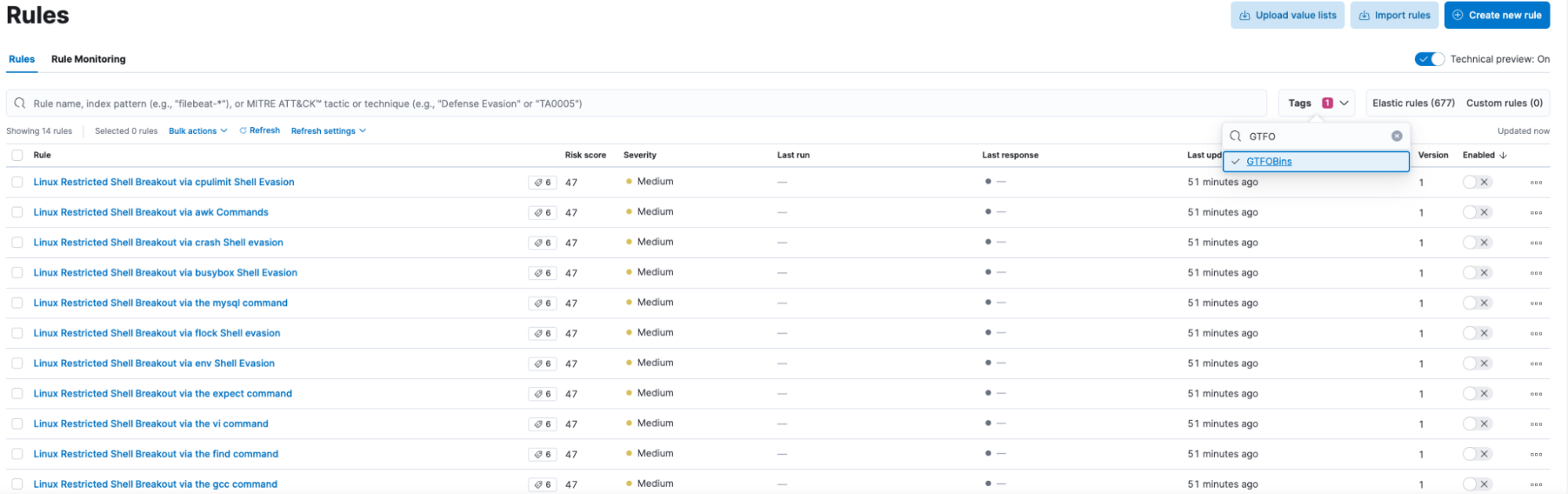
We can bulk enable all the rules at once, or a user can evaluate what suits his infrastructure best and enable only those select rules.
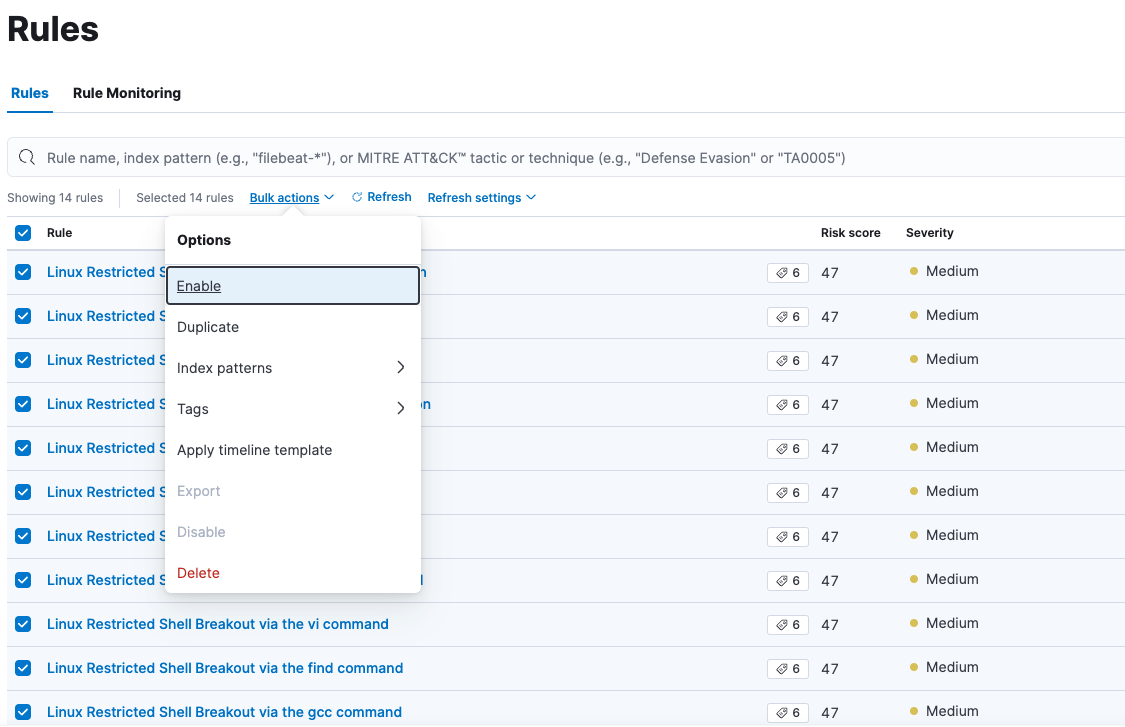
Analyze a sample rule and check the alerting features.
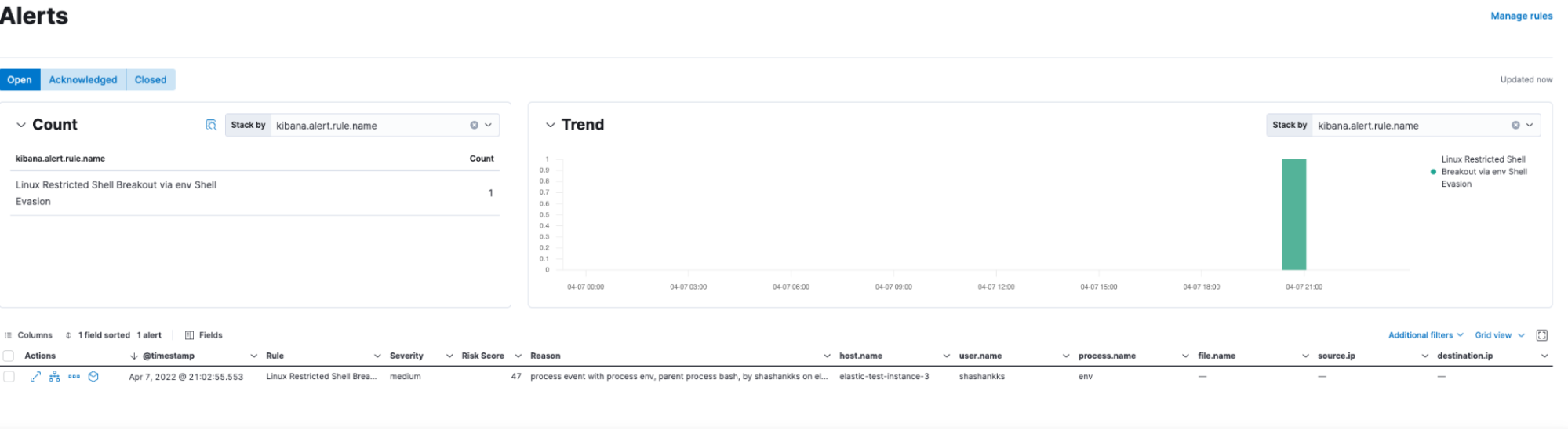
Scenario 1: When a shell has been evoked using the env command, Elastic Security identifies such user activities and alerts the same.
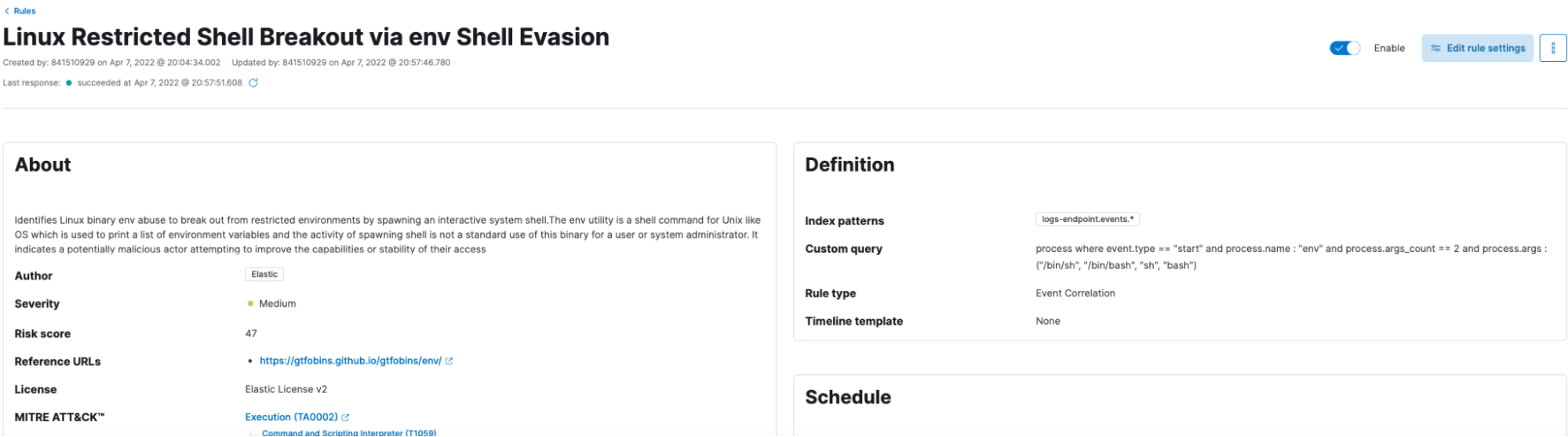
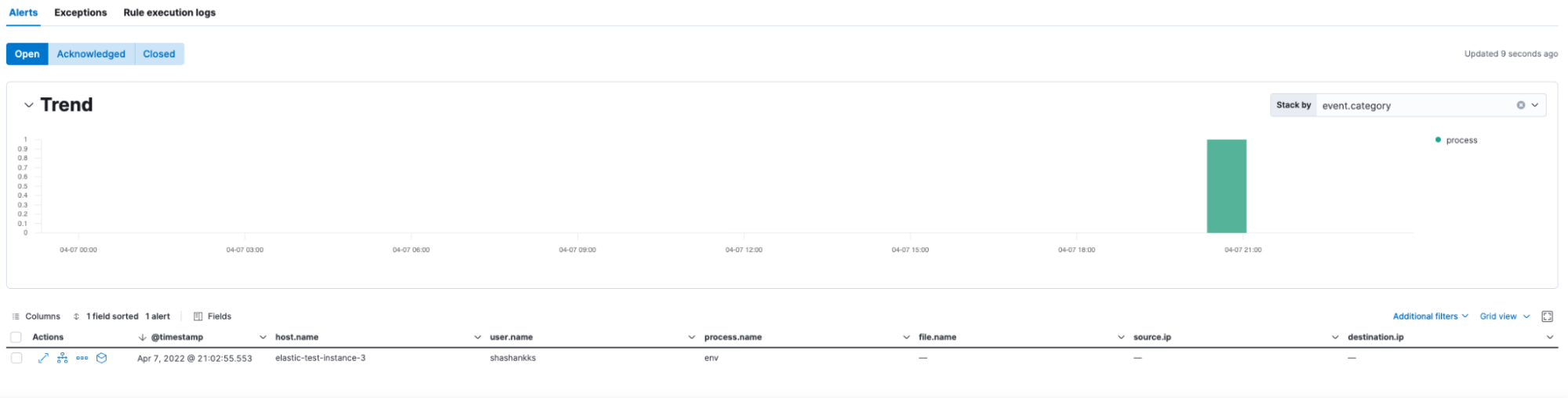
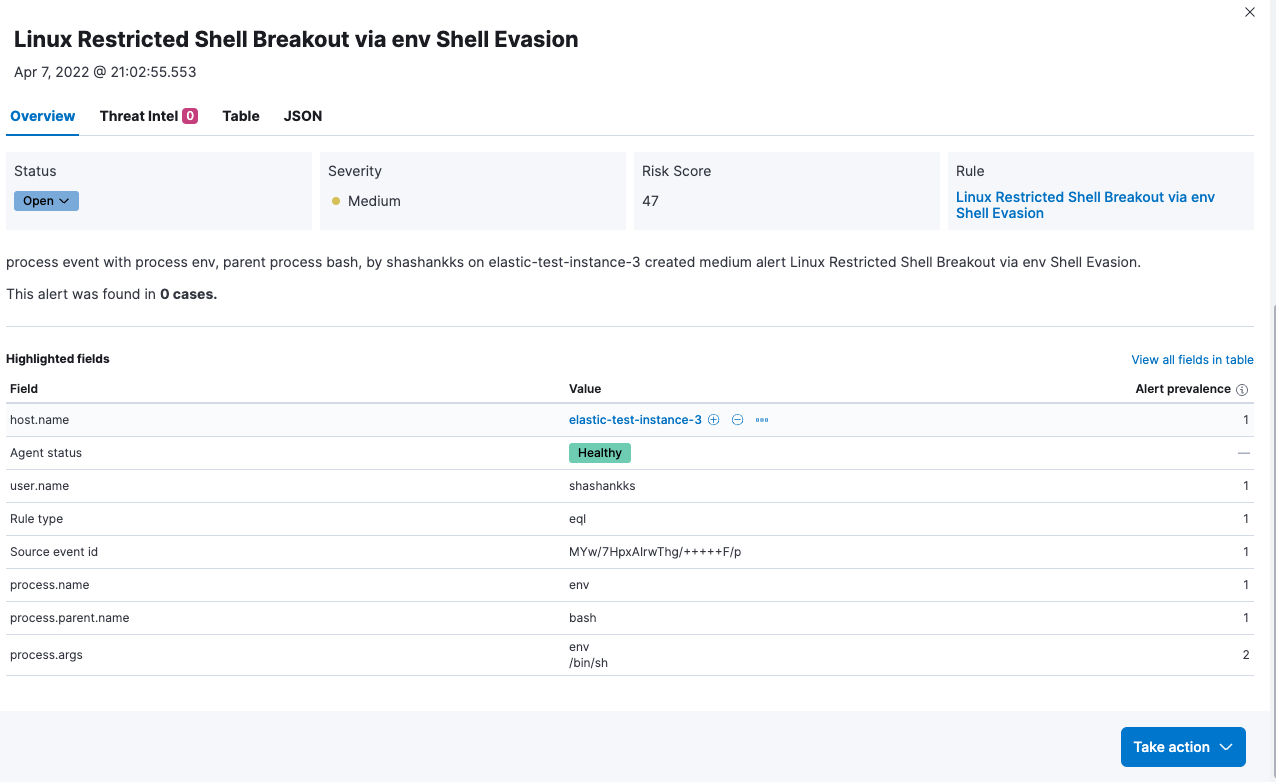
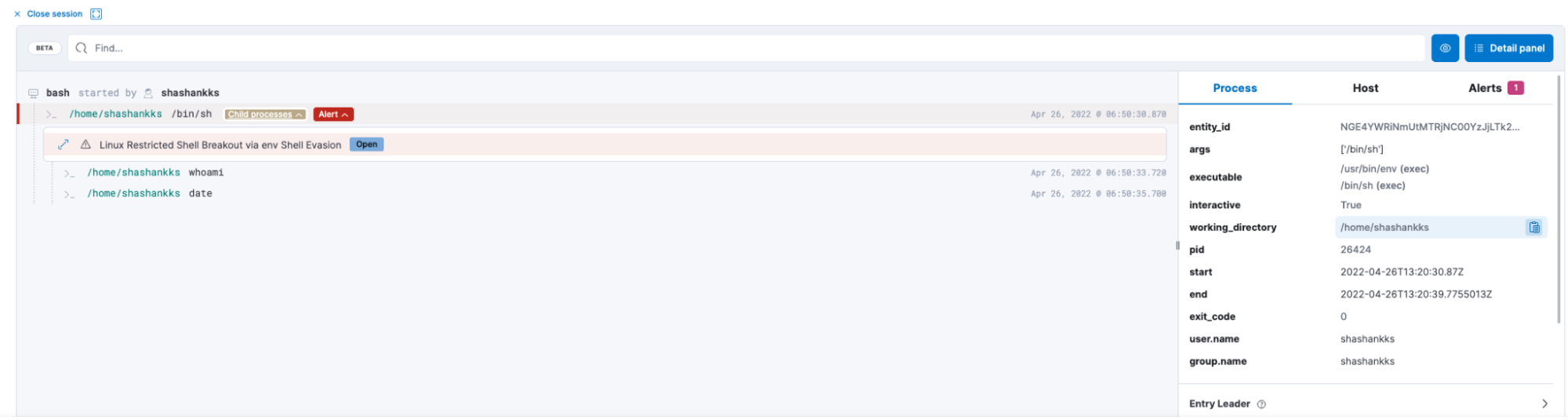
The session view of the of the command execution can be visualized with details.
Scenario 2: When a shell has been evoked using the apt command, Elastic Security identifies such user activities and alerts the same.
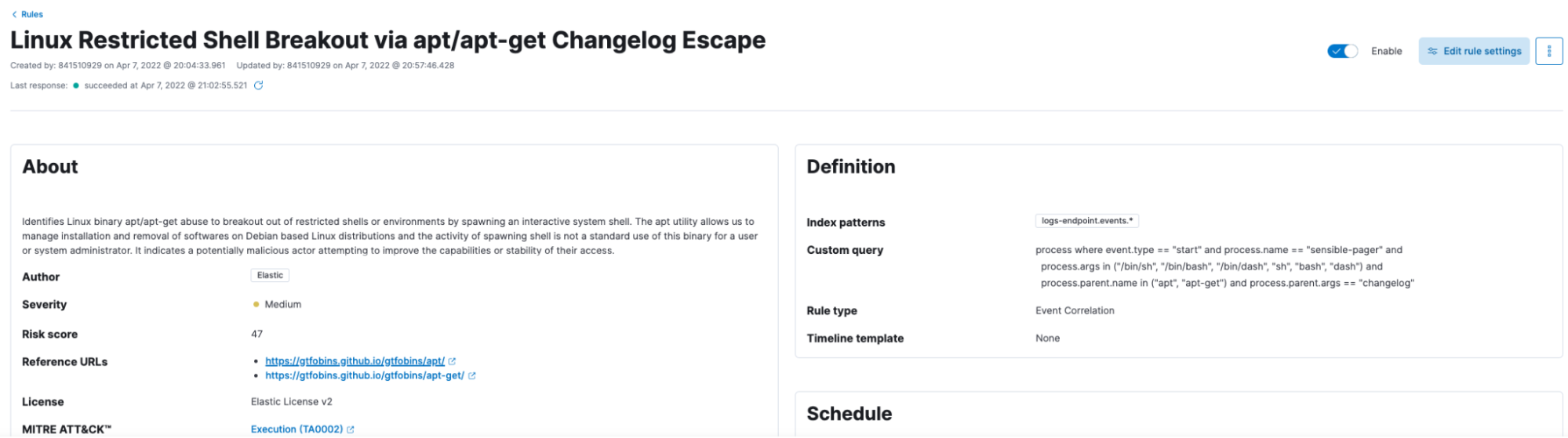
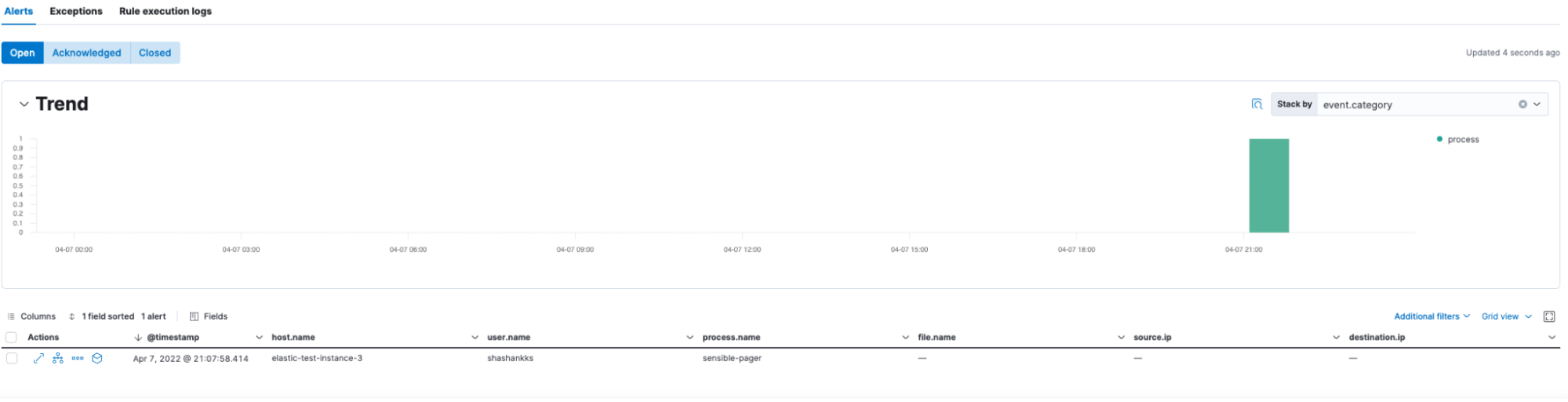
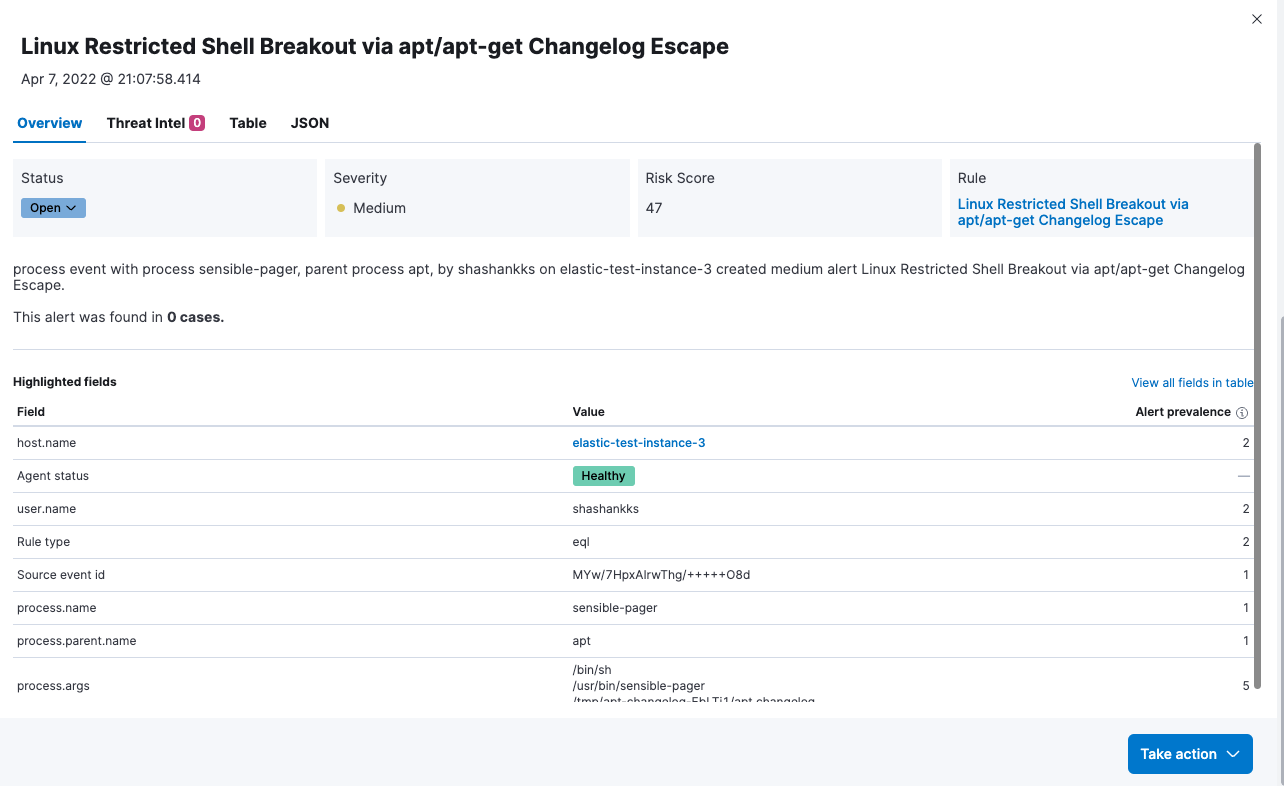
We can investigate the alert in the timeline as well, for additional information.
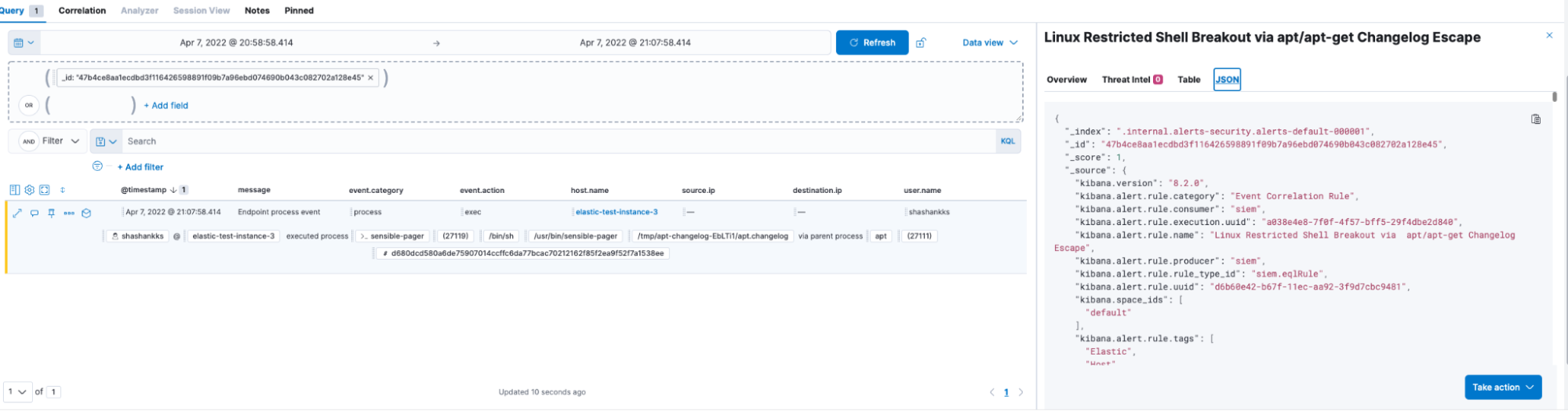
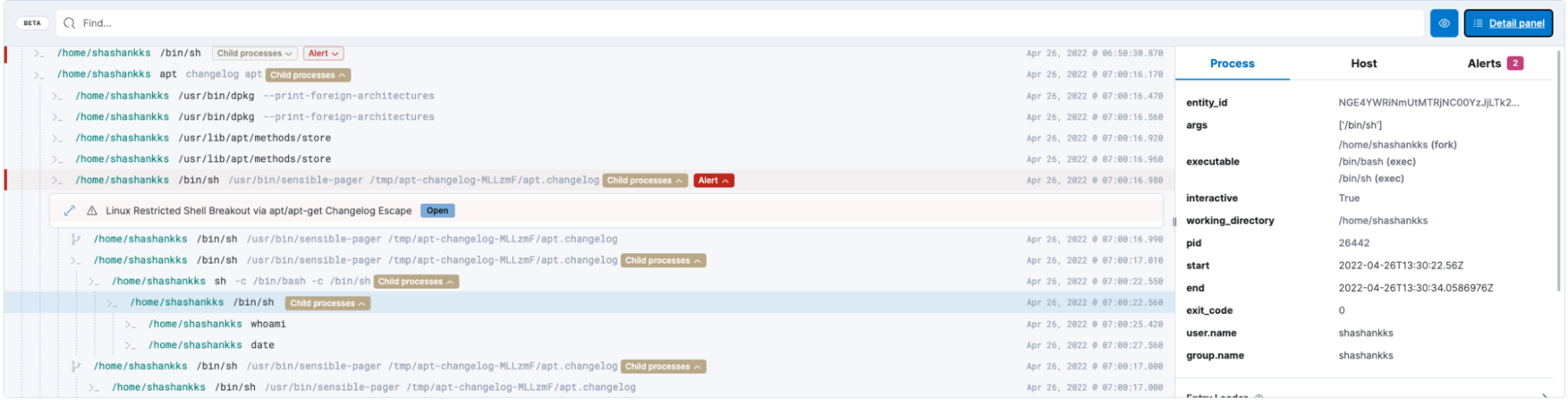
The event can be further analyzed to identify if the user is executing any malicious or unauthorized code in the spawned interactive shell via the evasion technique
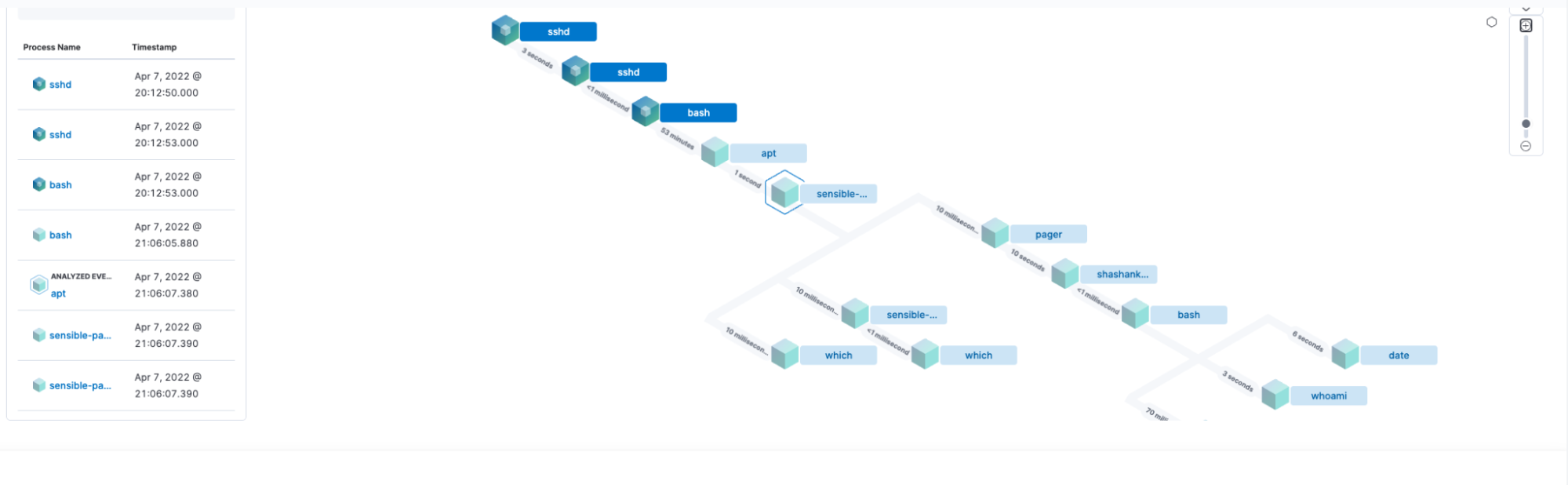
We can see the user has executed the date and whoami commands in the shell.
Similar analysis can be provided by the sessions view.
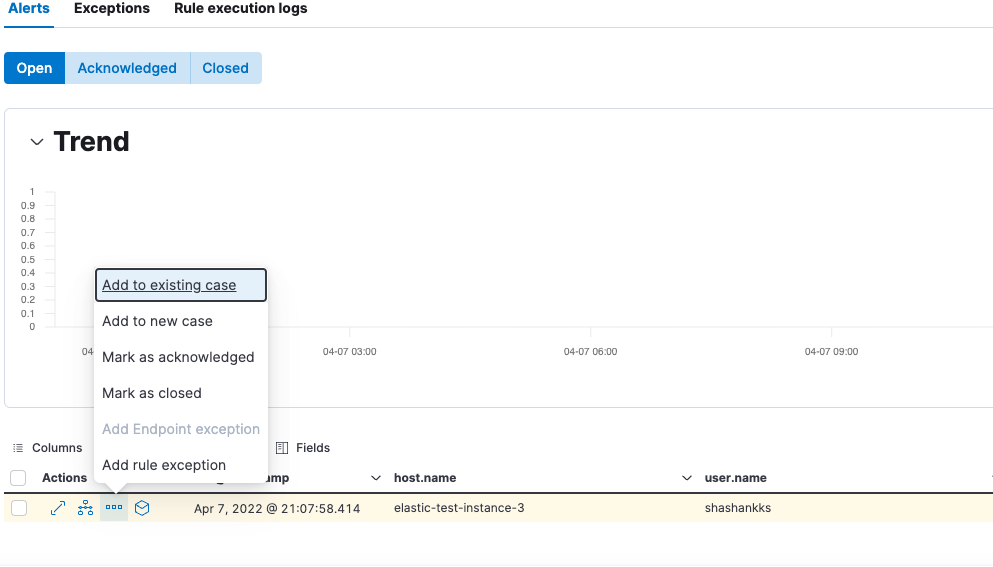
Depending on the outcome of the analysis, we can decide the closure actions for this alert using the ‘more actions’ feature in the post analysis phase.
Cumulative open /acknowledged or closed alerts can also be found in the ‘Alerts” section of the deployment.
MITRE ATT&CK® of Shell Evasion
The Shell evasion technique primarily defines the execution tactic of the adversary. The tactics and techniques details are referenced below.
Tactics
The adversary is trying to run malicious code. |
Techniques / Sub Techniques
Adversaries may abuse command and script interpreters to execute commands, scripts, or binaries. These interfaces and languages provide ways of interacting with computer systems and are a common feature across many different platforms. Most systems come with some built-in command-line interface and scripting capabilities, for example, macOS and Linux distributions include some flavor of Unix Shell while Windows installations include the Windows Command Shell and PowerShell. | ||
Adversaries may abuse Unix shell commands and scripts for execution. Unix shells are the primary command prompt on Linux and macOS systems, though many variations of the Unix shell exist (e.g. sh, bash, zsh, etc.) depending on the specific OS or distribution. Unix shells can control every aspect of a system, with certain commands requiring elevated privileges. |
Closing summary
Cloud infrastructures are often proven to be complex to decipher not because of enormous resources (large nodes), but due to a lack of visibility on what happens in/between those resources. Shell evasion(s) can go unmonitored due to the lack of visibility in the infrastructure without proper monitoring tools to detect and capture these threats.
Elastic Security equips teams with greater visibility to prevent, detect, and respond to all such events at cloud speed and scale — securing business operations with a unified, open platform.
You can always get started with a free 14-day trial of Elastic Cloud. Or download the self-managed version of the Elastic Stack for free.
References:
[1] https://gtfobins.github.io/