Elastic Global Threat Report Breakdown: Credential Access

Credential Access Breakdown
In the second part of our breaking down the Elastic Global Threat Report series, we’re focusing on the credential access tactic, which was the third-most common category of behavior we observed. Roughly 10% of all techniques we saw involved one form of credential theft or another and dissecting this class of behaviors is helpful both to improve our understanding of threats and to better understand enterprise risks.
For this post, we’ll focus on those techniques valid for on-premise Windows, Linux, and MacOS; a later publication in this series will cover the cloud attack surface.
What can you tell me about credential access?
There are 17 MITRE ATT&CK techniques in this category at the time of this publication, with 28 additional sub-techniques. These capabilities allow credentialed materials like usernames and passwords to be obtained: keys that open the locks on systems and applications.
The process of authentication also allows threats to obtain data, either directly or indirectly. Once you have the ability to log into a targeted resource, for example, you can succeed in stealing data without very much additional work.
Once valid account credentials are stolen, a threat can now masquerade themselves using this stolen persona. When the threat has knowledge about where that persona belongs, they can access systems and applications with much less scrutiny or risk of discovery. When combined with the results of reconnaissance, credential access provides a streamlined path to achieving data theft.
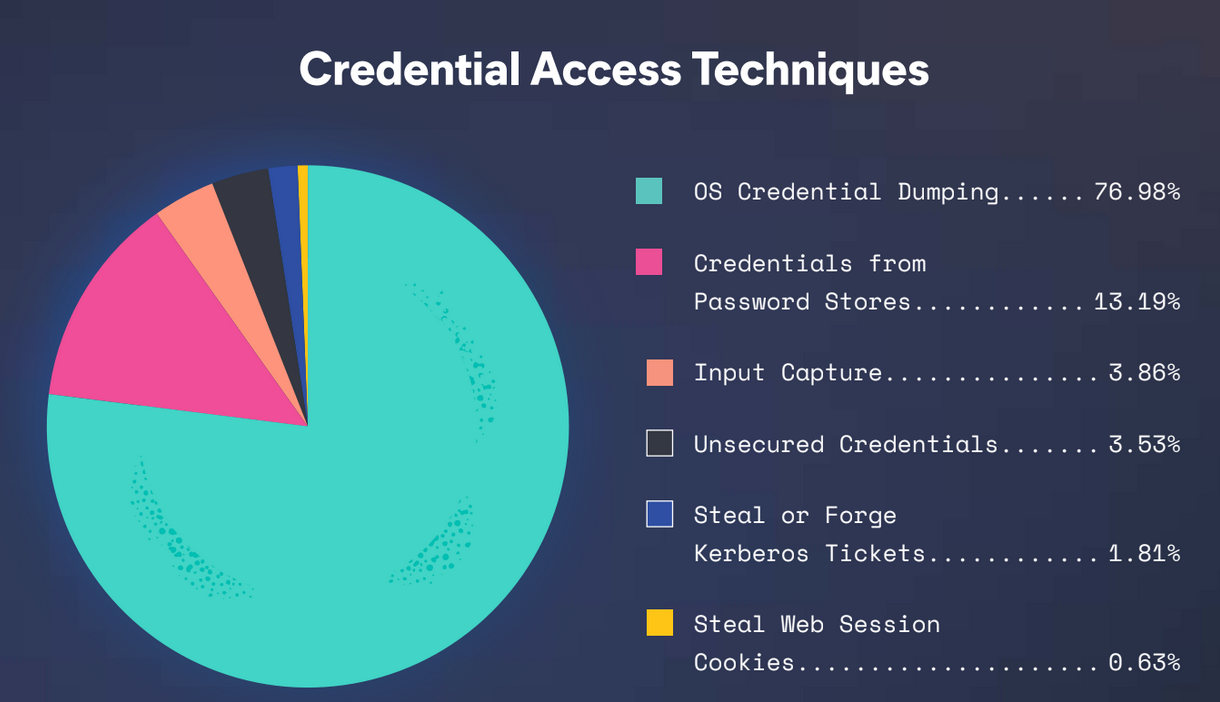
As you can see in the chart borrowed from the 2022 Global Threat Report, the most common method involves OS Credential Dumping, whereby the threat collects targeted credentials directly from the operating system. This method is better illustrated by decomposing the most common applications, as we do in the following chart:
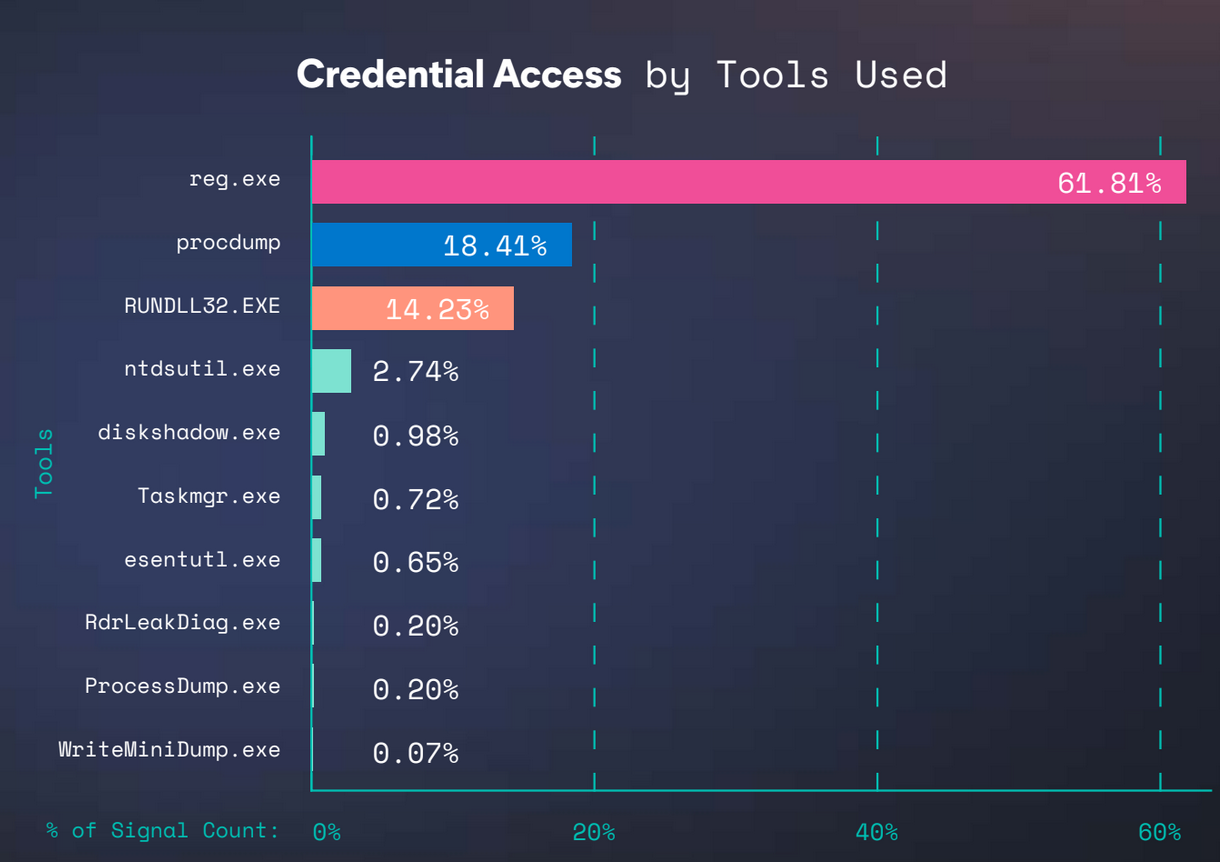
Our Global Threat Report revealed the following breakdown of preferred adversary techniques as observed through Elastic detection and protection rules:
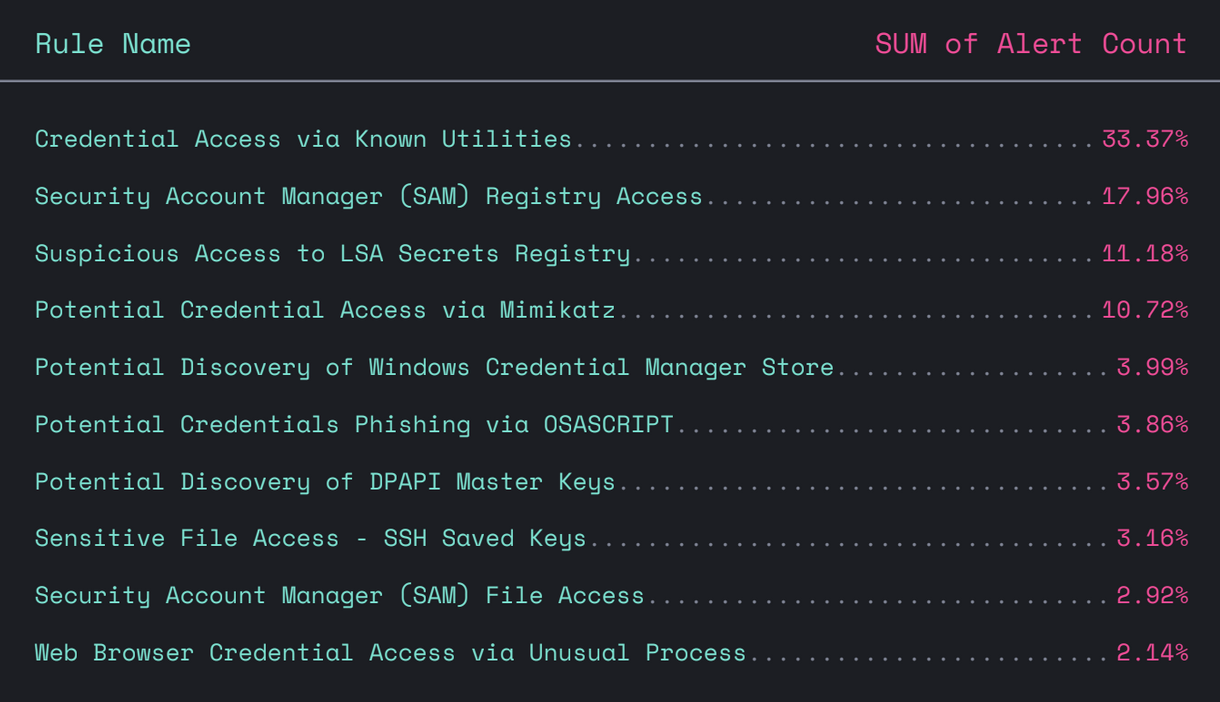
What kinds of credential access were most common?
In 2022, we saw more than 4,500 credential access attempts using the following techniques (all available to the community via the detection-rules or protections-artifacts repositories in compatible rule formats):
- OS Credential Dumping
- Credentials from Password Stores
- Input Capture
- Unsecured Credentials
- Steal or Forge Kerberos Tickets
- Steal Web Session Cookie
OS Credential Dumping came, saw, and conquered
The reg.exe utility, like rundll32.exe and taskmgr.exe, are built into the Windows operating system and users who are local administrators can easily use them to interact with critical files and processes to extract credentials. The concept of “least privilege” can be abstract, but this helps make it more practical: accounts that are not configured to run with only essential privileges make credential access much more likely to occur.
For enterprises who aren’t ready to implement a least privilege model, the next best thing is to consistently monitor the use of OS-native utilities that can be used to steal credentials.
What are the most effective rules for detection?
Elastic has 21 rules for various credential access techniques, and four of those rules were responsible for about 73% of events:
- Credential Access via Known Utilities
- Security Account Manager (SAM) Registry Access
- Suspicious Access to LSA Secrets Registry
- Potential Credential Access via Mimikatz
An example of Credential Access via Known Utilities would be the NTDSUtil.exe tool. Active Directory relies on a database (NTDS.dit) which can be accessed offline or in memory to obtain the entire contents of Active Directory, including any configuration settings and credentials stored there.
SAM Registry Access is quite similar and involves various ways of copying various Registry hives for offline credential harvesting. Using an inexpensive physical or virtual machine, an adversary can quickly obtain sensitive credentials for use in a target environment. No special software is needed, reg.exe is all you need and comes on every version of Windows.
Suspicious Access to LSA Secrets Registry is similar, they can be pulled from the HKEY_LOCAL_MACHINE\SECURITY\Policy\Secrets key value from the SECURITY hive.
Potential Credential Access via Mimikatz specifically looks for the Mimikatz tool, which may be the best-known and most feature-rich utility for obtaining credentials. However, enterprises shouldn’t obsess over Mimikatz: there are dozens of tools and scripts capable of achieving the same or similar results.
What next?
Threats can and will target credentials because they offer mobility, access, and the ability to masquerade as high-privilege users that might escape scrutiny. Because the majority of mechanisms are baked into each operating system, adversaries are likely to continue using native capabilities where they can. It would be difficult to frame these as “forecasts” so much as inevitable trends. Enterprises can and should monitor the use of these built-in tools as well as access to registry- and file-based sources of credentials, profiling how specific groups of users commonly interact with them.
If you missed the Elastic Global Threat Report, check it out for trends and correlations, forecasts, and recommendations! Follow Elastic Security Labs for information and resources.