


Palo Alto Networks and Elastic
Ingest key data for enterprise-wide analysis.
Solution overview
Palo Alto Networks and Elastic provide an integrated solution for near real-time threat detection, interactive triage and incident investigation, and automated response. Together, the solution helps organizations protect against attacks that can lead to data breaches and other loss or damage.
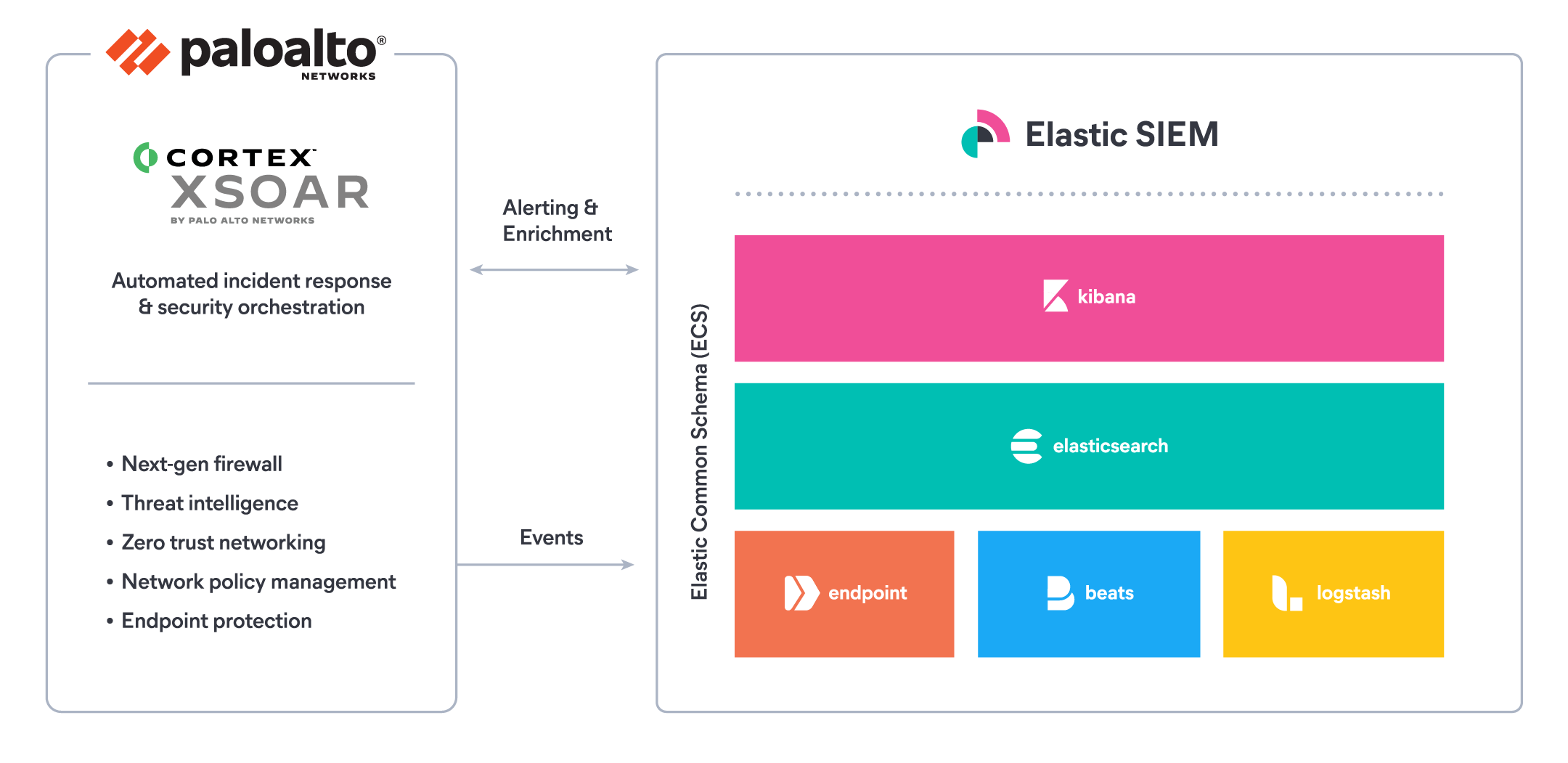
Elastic SIEM leverages the speed, scale, and relevance of Elasticsearch, and provides a curated data integration with Palo Alto Networks logs to enable cross data-source search, analysis, and correlation. Elastic SIEM provides an interactive workspace for analysts to quickly identify suspicious activity, pivot between all data sources, and gather evidence relevant to an incident.
Bidirectional integrations between Cortex XSOAR and Elasticsearch enable security operations teams to automate and orchestrate response actions through predefined playbooks — streamlining and standardizing incident response and resolution as well as incident lifecycle management.
Key capabilities
Palo Alto Networks and Elastic help security teams more readily navigate today’s complex threat landscape by providing an integrated solution that’s been proven in large-scale security analytics installations worldwide. By using the two together, you can:
- Ingest Palo Alto Networks PAN-OS firewall logs — normalized through Elastic Common Schema format — into Elastic SIEM using the prebuilt Filebeat Palo Alto Networks module
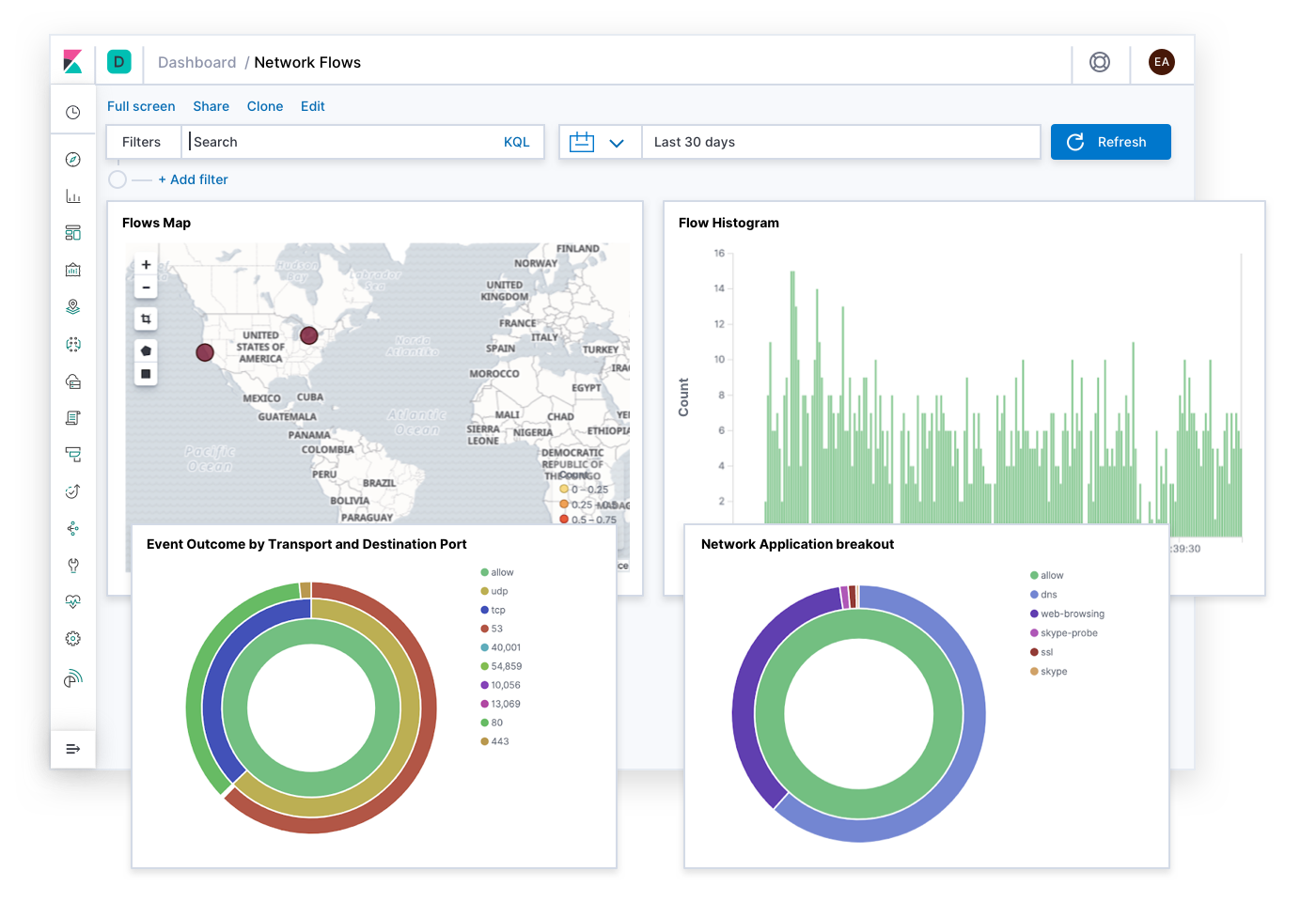
- Visualize, search, and correlate Palo Alto Networks logs with other security-relevant information in Kibana using Elastic SIEM, dashboards, heat maps, geo maps, and infographic displays to enable real-time threat hunting and automated detection
- Apply Elastic alerting and machine learning features to automate threat detection across multiple data sources to reduce false positives, help analysts and operators prioritize, and mitigate alert fatigue
- Elastic SIEM detection alerts can trigger Cortex XSOAR playbooks that orchestrate response actions across the entire stack of products in a single workflow
Use cases
Elastic and Palo Alto Networks work together to fulfill vital use cases.
Insider threat and zero trust: The zero-trust model should be the foundation for conducting operations. Because every network is different, however, it’s important to know exactly where to deploy those zero-trust controls. Elastic can collect logs and netflows, create baselines, and help identify where zero-trust policies would be the most effective. Elastic machine learning features identify anomalies and trigger alerts that admins can then use to automate actions (such as firewall policies) in Demisto.
Threat intelligence: Palo Alto Networks provides advanced threat intelligence tools that help identify threats to the network, and Elastic makes it easy to integrate those tools and make them usable in real-time contexts. Feeds ingested via Minemeld, for example, can incorporate AutoFocus tags that are continuously ingested into Elastic SIEM, making them available for near real-time lookup, categorization, and attribution within analysis tools.
IoT and SCADA: Sensor feeds from all types of devices can be ingested into Elastic for analysis and reporting. Anomalies identified by machine learning can trigger alerts to Demisto that perform immediate actions to isolate or control devices in trouble. Practitioners can correlate Zingbox IoT security service analysis with indicators from other enterprise data sources to further validate assessments and even automate response actions like segmentation or quarantine.
NetOps and SIEM: Network data is one of the primary intelligence feeds that cybersecurity teams rely on to monitor and identify threat behaviors — and it’s even more powerful when combined with other indicators. Fine-grained network feeds from the Palo Alto Networks NGFW can be automatically normalized through the Elastic Common Schema and ingested in near real time. Once indexed, they can be correlated with other data sources and then automatically analyzed with tools like unsupervised machine learning to deliver insights and help prioritize responses.
Automated response and orchestration: With 300+ integrated vendor playbooks and counting, Cortex XSOAR is a powerful platform for automating actions in a multivendor environment. The data analytics and insights generated within Elastic can be used to power automatic operations by pushing to Cortex XSOAR, while Cortex XSOAR can leverage Elastic for real-time data access and aggregation.
Learn more
When powerful technologies like Elastic and Palo Alto Networks work together, it's a force multiplier. Take a look at the following technical resources or connect with your local Elastic field team to learn more.
- Documentation on Filebeat module for ingesting PAN data into Elasticsearch
- Webinar on migrating data to Elastic Common Schema (ECS)
- Contact Elastic to explore this integration further











