Recherchez, analysez et agissez avec l'analyse des logs
Les logs sont partout, enregistrent tout, et sont la source de contexte la plus riche. Elastic se démarque grâce à l'IA agentique, transformant les logs désordonnés et non structurés en réponses opérationnelles.
DÉMO GUIDÉE
Des journaux bruts aux vraies réponses
Les logs vous indiquent ce qui s'est passé. Elastic vous aide à comprendre pourquoi.
FONCTIONNALITÉS
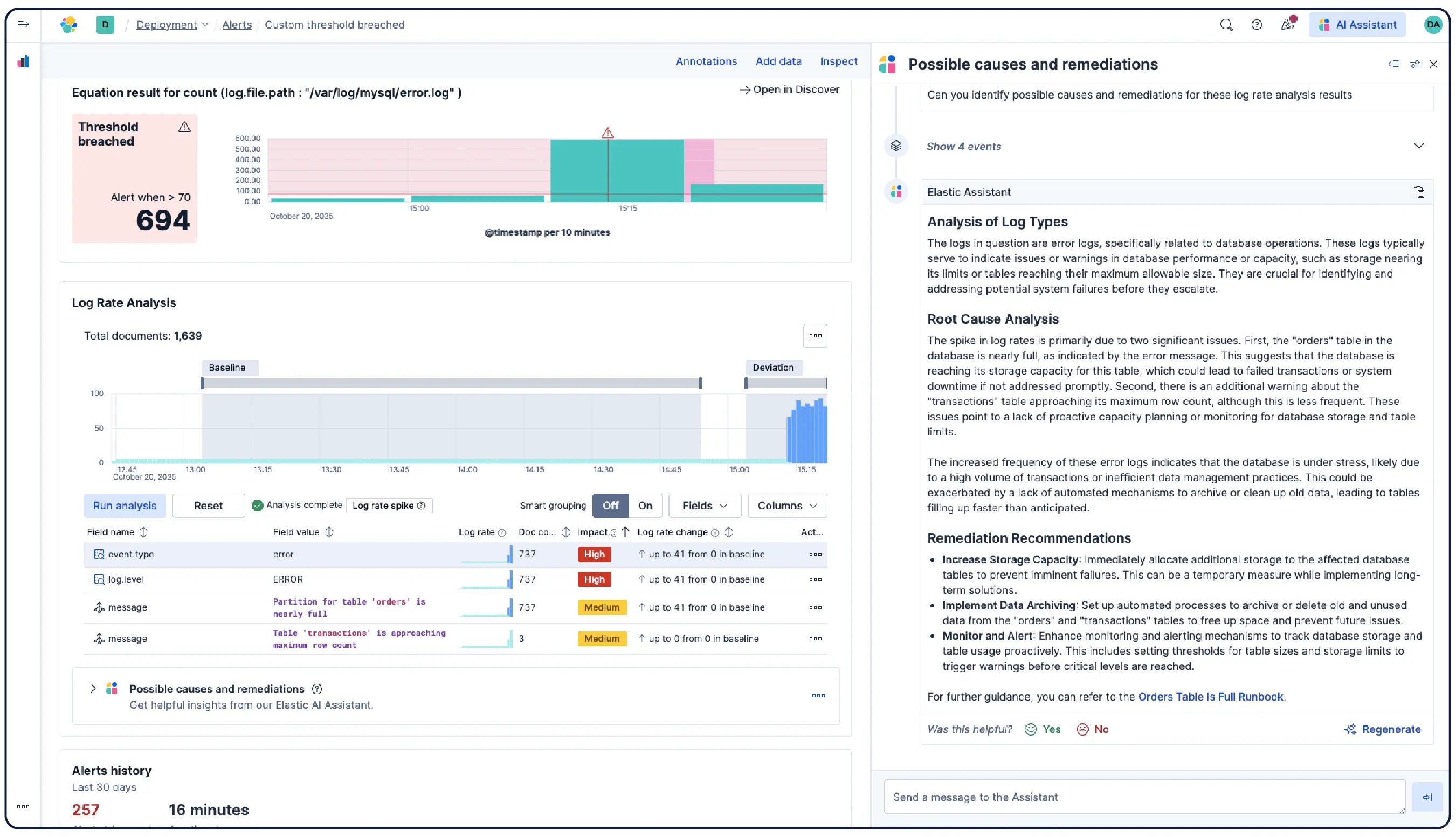
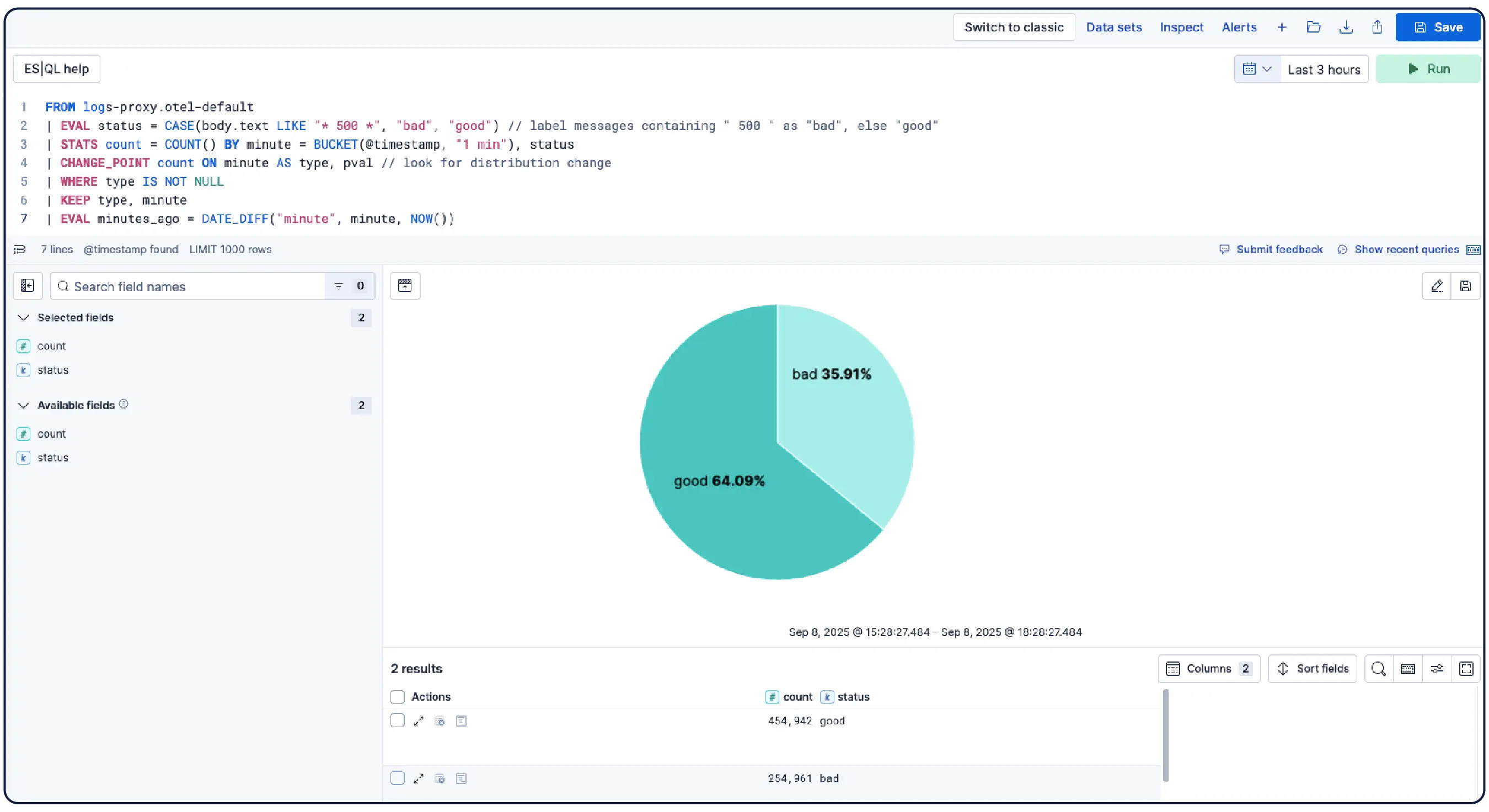
Des milliards de logs, une image claire
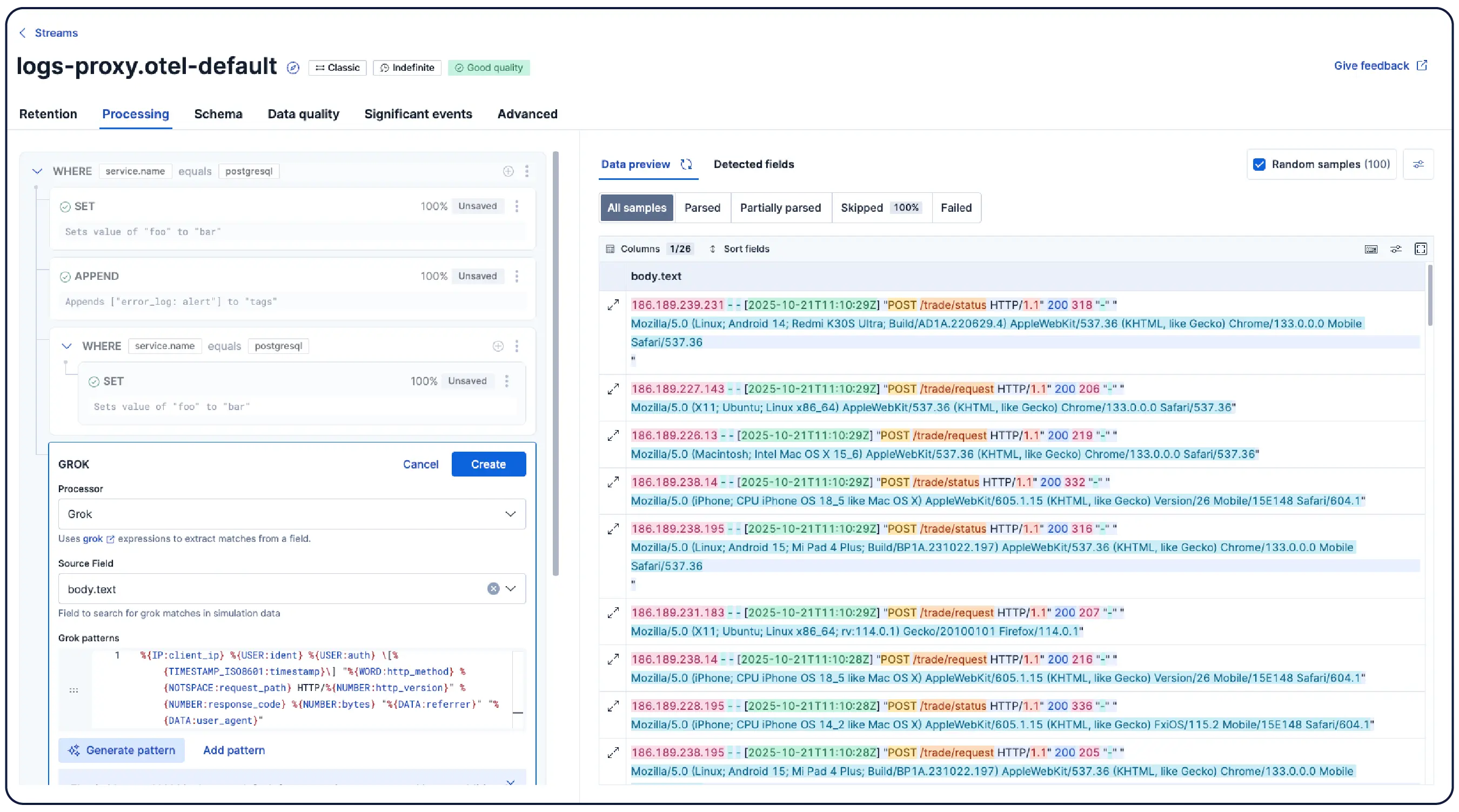
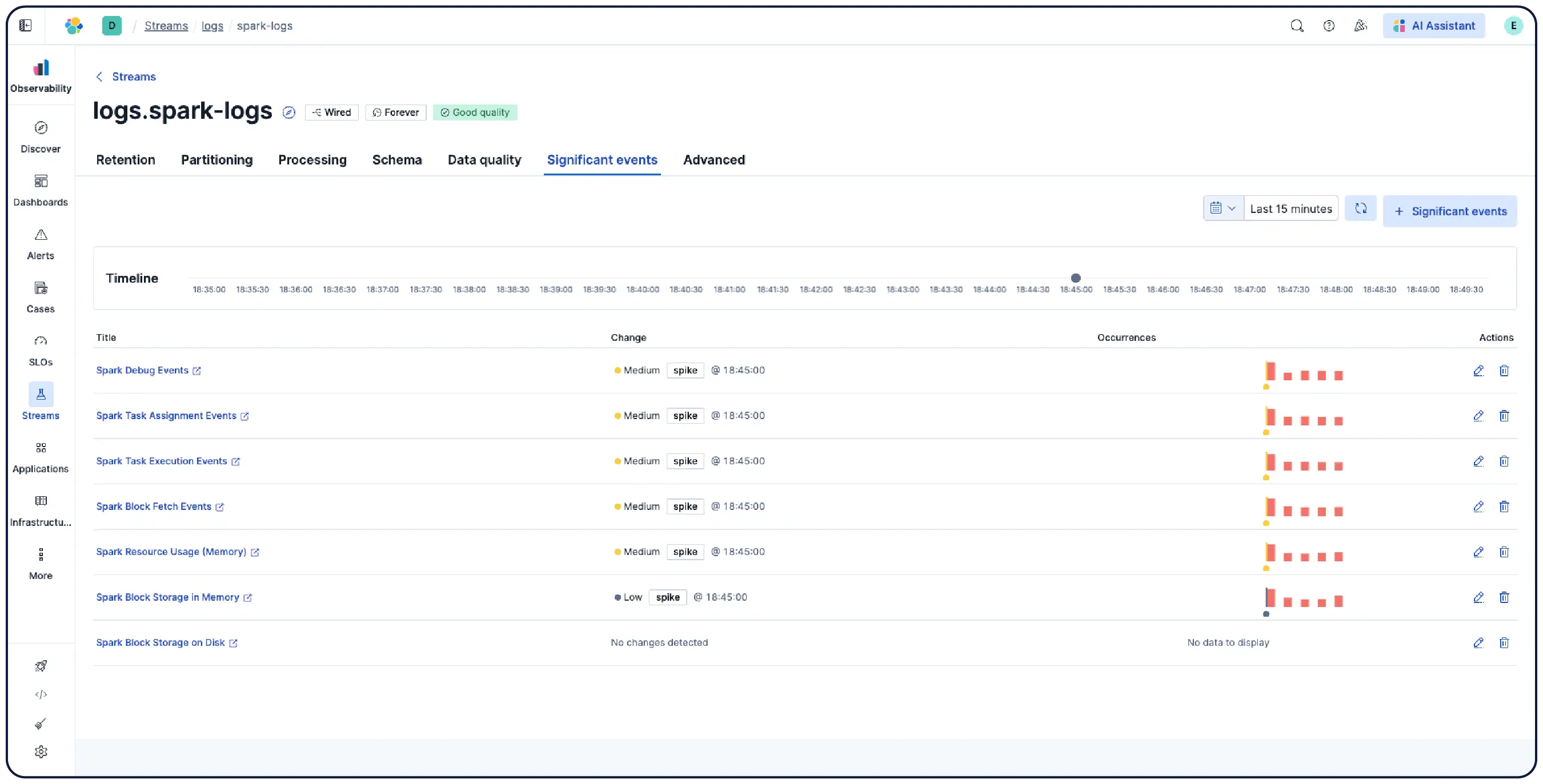
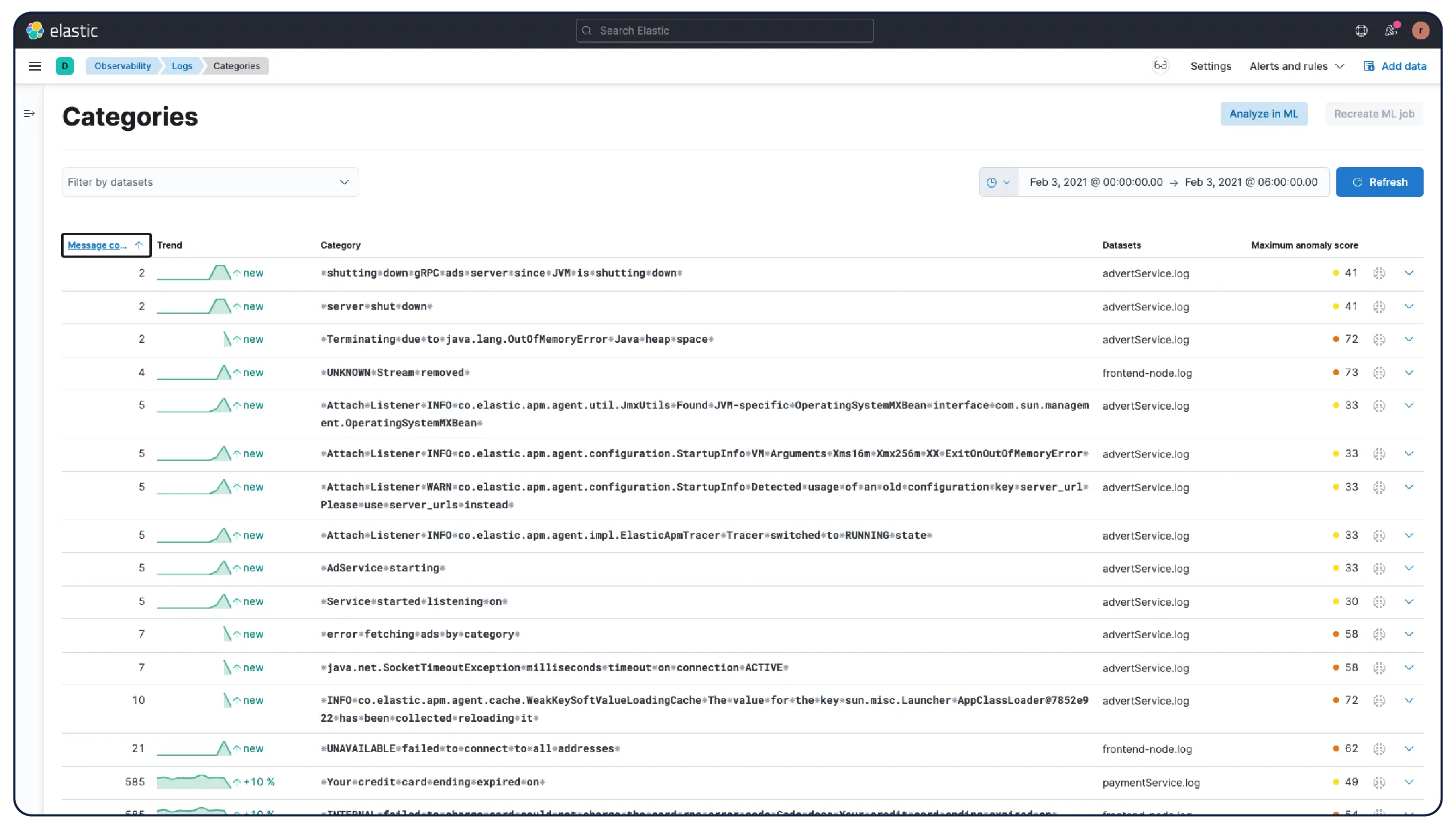
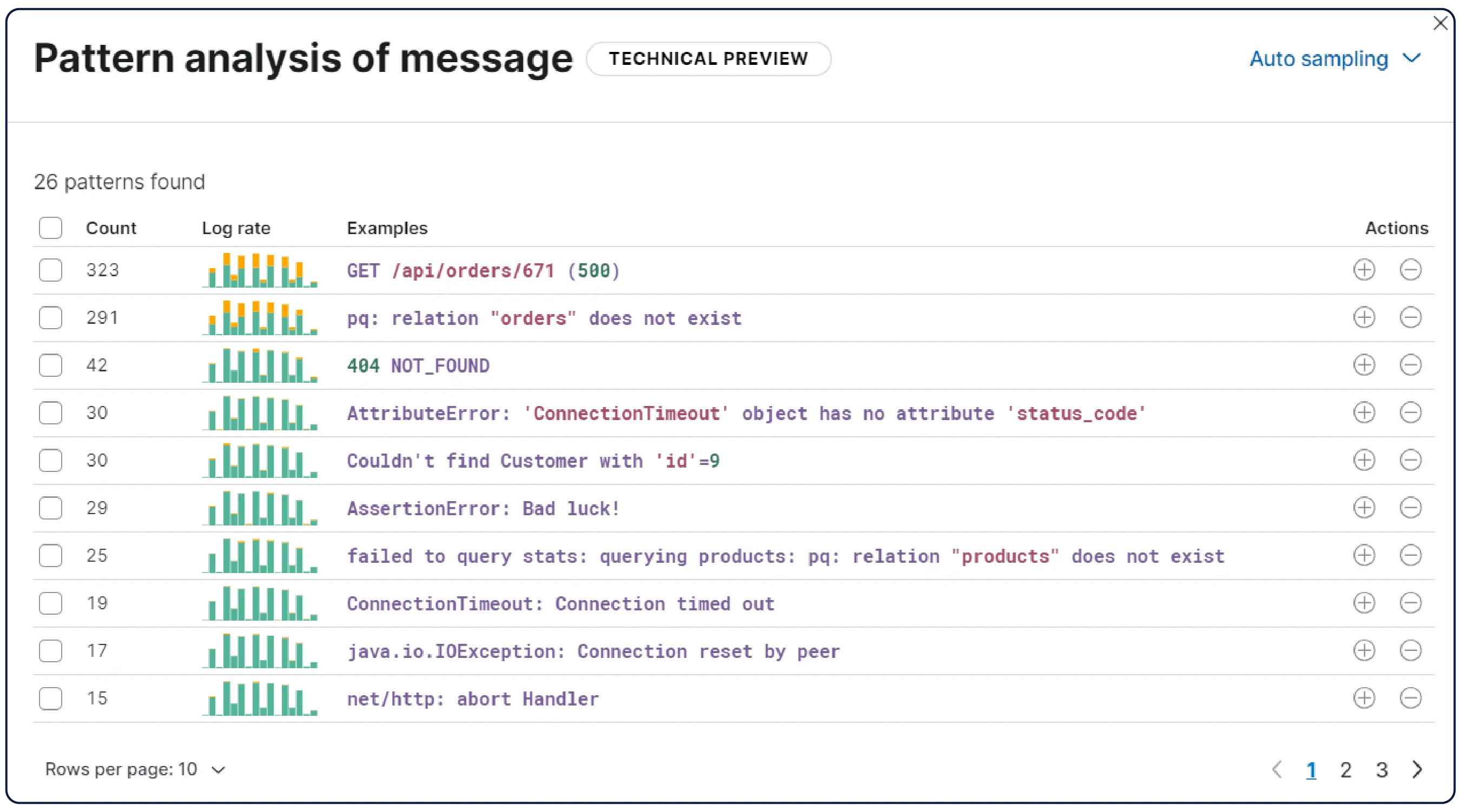
Elastic ingère les logs de n’importe où et les regroupe automatiquement en modèles, met en évidence les anomalies et identifie les pics, afin que vous obteniez des réponses et non une surcharge.
Organisez automatiquement les données en flux logiques, en appliquant des politiques de parsing, de partitionnement, d'extraction de champs et de cycle de vie avec un minimum de configuration manuelle.

Découvrez pourquoi des entreprises comme la vôtre choisissent Elastic Observability
Bénéficiez d'analyses de logs à scaler pour transformer des logs désorganisés en réponses opérationnelles.
Témoignage client

Comcast effectue l’ingestion de 400 téraoctets de données par jour avec Elastic pour monitorer les services et accélérer l’analyse des causes premières, garantissant ainsi une expérience client de premier ordre.
Témoignage client

Discover a réduit les coûts de stockage de 50 % et amélioré les temps de récupération des données en mettant en œuvre une plateforme de logging centralisée avec Elastic.
Témoignage client

Informatica a réduit ses coûts et son MTTR en migrant l'intégralité de sa charge de travail de logging vers Elastic pour plus de 100 applications et plus de 300 clusters Kubernetes.
Rejoignez la discussion
Connectez-vous à la communauté mondiale d'Elastic et participez à des conversations ouvertes et à la collaboration.
Posez des questions, obtenez des réponses et faites entendre votre voix sur notre forum ouvert.














.jpg)
