如何使用 Kerberos 确保您 Elasticsearch 集群的安全
希腊神话中的三头猛犬保护您的数据
Elasticsearch 6.4 针对白金级订阅新增了 Kerberos 身份验证支持,在转型为完全 Kerberos 式 Elastic Stack 的道路上迈出了第一步。Kerberos 是一项成熟的技术,能够允许在分布式系统中进行安全身份验证。Kerberos 可让用户通过单点登录方式访问不同服务,无需用户重复提供用户名和密码。本篇博文讲解了如何对 Elasticsearch 进行配置,从而支持对 HTTP 流量进行 Kerberos 身份验证。
部署概述
我们考虑一个简单情境,假设用户 Alice(爱丽丝)拥有一个单节点 Elasticsearch 集群。Alice 已有一个 Kerberos Realm (demo.local),她现在希望通过 Kerberos 身份验证确保 Elasticsearch 集群的安全。Kerberos 身份验证服务器有权对 Realm 内的用户、主机或服务进行身份验证。本文中使用的命令参考了 MIT Kerberos 实施版本。有关更多详情,请参阅 MIT Kerberos 文档。
在这一简单情境中,共有三台主机设备:
- 主机 1 (
kdc.demo.local):这是 Kerberos 密钥分发中心 (KDC),通常包括身份验证服务器和票据授予服务器。 - 主机 2 (
es.demo.local**):**Elasticsearch 单节点集群便位于这里。 - 主机 3 (
client.demo.local**):**Elasticsearch 客户端便位于这里。
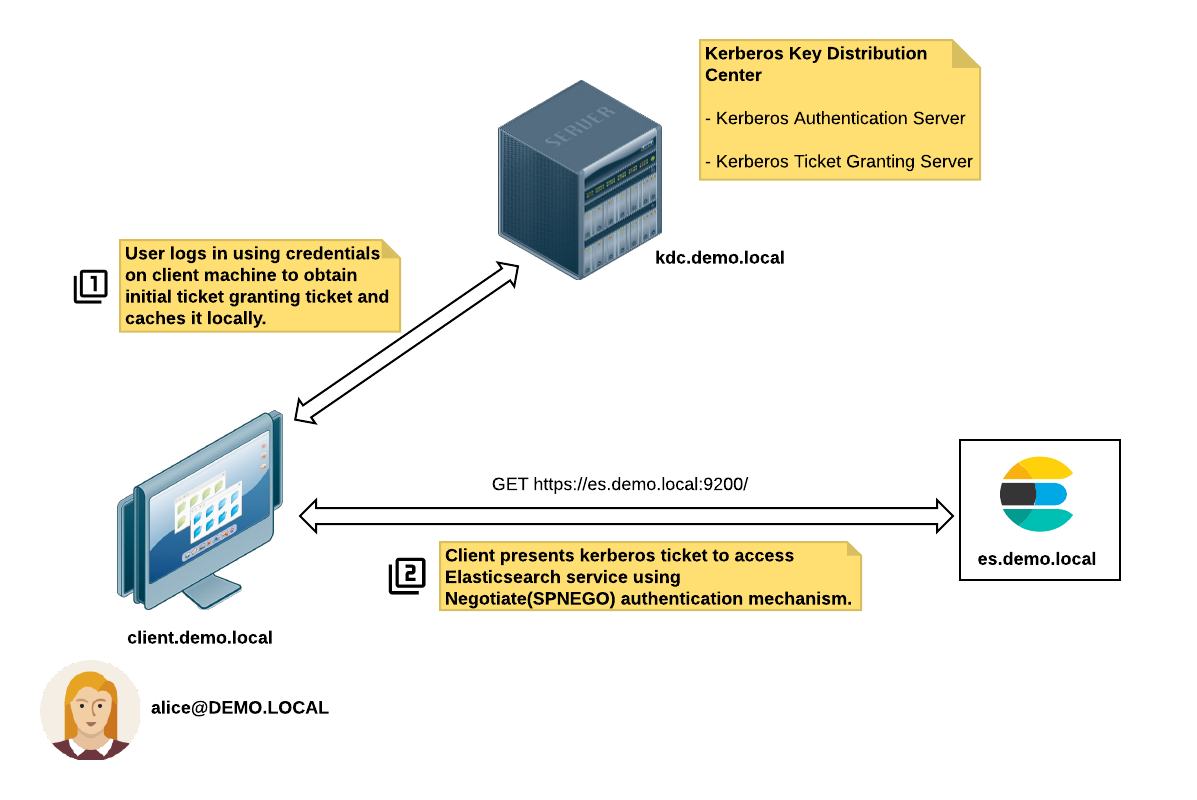
需要完成下列步骤,才能成功完成 Kerberos 身份验证:
1.Alice (alice@DEMO.LOCAL) 使用她自己的凭据登录客户端设备 (client.demo.local)。
2.客户端设备申请从 KDC 服务器 (kdc.demo.local) 获得“授予票据的票据”(TGT)。
3.客户端访问 Elasticsearch 服务 https://es.demo.local:9200,随后会返回一条包括 HTTP 状态代码 Unauthorized(401) 的响应,并且其中包括 WWW-Authenticate: Negotiate 标头。
4.客户端会为 Elasticsearch 服务主体HTTP/es.demo.local@DEMO.LOCAL 从票据授予服务器 (TGS) 申请一个会话票据。Elasticsearch 服务主体的名称来自访问服务时所用的 URL。
5.客户端将此票据出示给 Elasticsearch 服务进行身份验证。
6.Elasticsearch 服务会验证 Kerberos 票据并授予访问权限(如果票据有效)。
如何配置 Kerberos Realm
如要启用 Elasticsearch Kerberos Realm,您需要拥有 Kerberos 基础架构:
- 域中所有参与设备的时钟已进行同步
- 所有参与设备均有一个有效的 DNS 域
- 一个 KDC 服务器
- 已安装 Kerberos 库和配置文件(例如
kinit、klist)的客户端节点
假设您已拥有 Kerberos 基础架构,您还需要提供下列信息:
- Kerberos 配置文件
krb5.conf--- 此文件包含您的 Kerberos 环境的必要详情,例如默认 Realm、KDC 服务器,以及网络域和 Kerberos Realm 之间的对应关系。在 Linux 系统中,此文件通常位于/etc目录中。应该将 JVM 系统属性java.security.krb5.conf设置为此配置文件的完整路径。JVM 将加载此配置文件,并在必要时用其来寻找所需信息。 - Elasticsearch HTTP 服务
keytab--- 密钥表 (keytab) 是一个存储主体和加密密钥对的文件。Elasticsearch HTTP 服务将会使用此密钥表来验证来自客户端的输入票据。通常服务主体的名称为此格式:HTTP/es.demo.local@DEMO.LOCAL,其中服务类别为HTTP,es.demo.local则是 Elasticsearch 主机完全符合要求的域名,而DEMO.LOCAL则是 Kerberos Realm。需要将此文件放置到 Elasticsearch 配置目录中。由于此文件包含凭据,所以为确保此文件的安全,请仅向运行 Elasticsearch 的用户授予只读权限。Kerberos 系统管理员可为您提供您的服务中所用到的密钥表文件。
有了这两个文件之后,我们现在便可以继续在 Elasticsearch 中配置 Kerberos Realm 了。
1.配置 JVM 选项
首先,我们需要编辑 JVM 选项文件 (jvm.options),来为 Kerberos 配置文件配置 JVM 系统属性:
# Kerberos configuration
-Djava.security.krb5.conf=/etc/krb5.conf
2.针对 Kerberos 配置 Elasticsearch
接下来,我们需要在 elasticsearch.yml 文件中添加一个 Kerberos Realm:
# Kerberos realm
xpack.security.authc.realms.kerb1:
type: kerberos
order: 1
keytab.path: es.keytab
这会将 Kerberos Realm (kerb1) 的类型配置为 kerberos,将 Realm 顺序配置为 1,并将 keytab.path 配置为指向配置目录中的 Elasticsearch 服务密钥表文件 (es.keytab)。有关更多信息,请参阅配置 Kerberos Realm 文档。
3.重新启动 Elasticsearch
配置完成后,需要重新启动 Elasticsearch 节点。
4.将 Kerberos 用户映射至角色
Kerberos 是一项身份验证协议,但是其并不提供授权详细信息。为完成授权,我们可以使用映射 API 来将用户映射至角色。下面这些代码便会创建一个名为 kerbrolemapping 的角色映射,该映射会将 monitoring_user角色分配给用户 alice@DEMO.LOCAL:
$ curl -u elastic -H "Content-Type: application/json" -XPOST http://es.demo.local:9200/_xpack/security/role_mapping/kerbrolemapping -d
{
"roles" : [ "monitoring_user" ],
"enabled": true,
"rules" : {
"field" : { "username" : "alice@DEMO.LOCAL" }
}
}
有关角色映射的更多详细信息,请参阅我们的相关文档:将用户和群组映射至角色。
噢耶,成功啦!
如要验证是否能够在客户端设备上进行身份验证,我们需要发出一条 kinit 命令以获得一张“授予票据的票据”:
$ kinit alice@DEMO.LOCAL
Password for alice@DEMO.LOCAL:
$ klist
Ticket cache: KEYRING:persistent:1000:krb_ccache_NvNtNgS
Default principal: alice@DEMO.LOCAL
Valid starting Expires Service principal
31/08/18 02:20:07 01/09/18 02:20:04 krbtgt/DEMO.LOCAL@DEMO.LOCAL
Then invoke curl with the negotiate parameter so that Kerberos authentication over HTTP can be performed:
$ curl --negotiate -u : -XGET http://es.demo.local:9200/
然后就大功告成啦!
{
"name" : "Lw7K29R",
"cluster_name" : "elasticsearch",
"cluster_uuid" : "qd3iafXORLy0VCfVD_Hp9w",
"version" : {
"number" : "6.4.0",
"build_flavor" : "default",
"build_type" : "tar",
"build_hash" : "595516e",
"build_date" : "2018-08-17T23:18:47.308994Z",
"build_snapshot" : true,
"lucene_version" : "7.4.0",
"minimum_wire_compatibility_version" : "5.6.0",
"minimum_index_compatibility_version" : "5.0.0"
},
"tagline" : "You Know, for Search"
}
结论
如上面所讲,如果您能访问服务主体密钥表和 Kerberos 配置文件,则配置 Kerberos Realm 是一件很简单的事情;仅需针对 Elasticsearch 编写几行 Kerberos Realm 配置命令即可。在 Elasticsearch 中支持 Kerberos 仅仅是一个开始,我们将会在未来的更新中继续推出针对其他 Elastic Stack 组件的支持,敬请关注!